Universal Two-Qubit Computational Register for Trapped Ion Quantum Processors
Universal two-qubit computational register for trapped ion quantum processors, including state preparation, gates, and benchmarking. The experimental setup and results are discussed.
0 views • 14 slides
Towards Single-Event Upset Detection in Hardware Secure RISC-V Processors
This research focuses on detecting single-event upsets (SEUs) in hardware-secure RISC-V processors in radiation environments, such as high-energy physics and space applications. Motivated by the potential data errors, unpredictable behavior, or crashes caused by SEUs, the study explores fault inject
4 views • 17 slides
Understanding Secure Act 2.0 Key Provisions
In a detailed report by Dee Spivey and Angie Zouhar, key provisions of SECURE Act 2.0 are outlined, including changes in retirement plans like RMD age increase, employee certification of hardship withdrawals, and more. Secure 1.0 and Secure 2.0 differences, effective dates, and necessary actions for
5 views • 12 slides
Understanding Superscalar Processors in Processor Design
Explore the concept of superscalar processors in processor design, including the ability to execute instructions independently and concurrently. Learn about the difference between superscalar and superpipelined approaches, instruction-level parallelism, and the limitations and design issues involved
0 views • 55 slides
Understanding Computer Architecture: A Comprehensive Overview by Prof. Dr. Nizamettin AYDIN
Explore the realm of computer architecture through the expertise of Prof. Dr. Nizamettin AYDIN, covering topics like RISC characteristics, major advances in computers, comparison of processors, and the driving force for CISC. Delve into the evolution of processors, register optimization, and the tra
0 views • 42 slides
Understanding Multicore Processors: Hardware and Software Perspectives
This chapter delves into the realm of multicore processors, shedding light on both hardware and software performance issues associated with these advanced computing systems. Readers will gain insights into the evolving landscape of multicore organization, spanning embedded systems to mainframes. The
1 views • 36 slides
Introduction to SFTP & PGP Encryption for Secure Data Transfer
Discover how to ensure reliable data transfer, make informed decisions, and gain a strategic advantage through the use of Secure File Transfer Protocol (SFTP) and Pretty Good Privacy (PGP) encryption. The session includes demonstrations on PGP encryption and SFTP access, along with insights on setti
1 views • 22 slides
Introduction to Intel Assembly Language for x86 Processors
Intel Assembly Language is a low-level programming language designed for Intel 8086 processors and their successors. It features a CISC instruction set, special purpose registers, memory-register operations, and various addressing modes. The language employs mnemonics to represent instructions, with
2 views • 12 slides
Ensuring Secure Testing Environments in Oregon Education System
Oregon's Statewide Assessment System (OSAS) emphasizes the critical need for secure testing environments to maintain the validity and accuracy of assessment data. This includes handling secure printed test materials, identifying and preventing improprieties, and reporting any irregularities. From ma
2 views • 20 slides
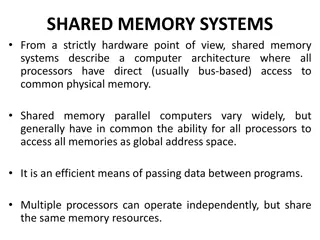
Understanding Shared Memory Systems in Computer Architecture
Shared memory systems in computer architecture allow all processors to have direct access to common physical memory, enabling efficient data sharing and communication among processors. These systems consist of a global address space accessible by all processors, facilitating parallel processing but
1 views • 19 slides
Understanding Computer System Architectures
Computer systems can be categorized into single-processor and multiprocessor systems. Single-processor systems have one main CPU but may also contain special-purpose processors. Multiprocessor systems have multiple processors that share resources, offering advantages like increased throughput, econo
2 views • 25 slides
Understanding System Management Mode (SMM) in x86 Processors
System Management Mode (SMM) is a highly privileged mode in x86 processors that provides an isolated environment for critical system operations like power management and hardware control. When the processor enters SMM, it suspends all other tasks and runs proprietary OEM code. Protecting SMM is cruc
1 views • 26 slides
PowerPC Architecture Overview and Evolution
PowerPC is a RISC instruction set architecture developed by IBM in collaboration with Apple and Motorola in the early 1990s. It is based on IBM's POWER architecture, offering both 32-bit and 64-bit processors popular in embedded systems. The architecture emphasizes a reduced set of pipelined instruc
2 views • 13 slides
Contrasting RISC and CISC Architectures
Contrasting RISC (Reduced Instruction Set Computing) and CISC (Complex Instruction Set Computing) architectures, the images and descriptions elaborate on their advantages and disadvantages, with a focus on multiplying two numbers in memory using a CISC approach. CISC processors aim to complete tasks
0 views • 35 slides
Secure Computation Techniques in RAM Models with Efficient Automation
Explore the automation of efficient RAM-model secure computation techniques, including examples such as secure binary search. Discover how traditional solutions using circuit abstractions can be improved for sub-linear time computation through methods like Oblivious RAM. Learn about techniques such
0 views • 37 slides
Understanding ARM RISC Design Philosophy and Its Impact
Delve into the world of ARM processors, exploring the RISC design philosophy that underpins their efficiency and widespread application. Learn about key principles, compare RISC with CISC, and discover how ARM's simplicity, orthogonality, and efficient architecture contribute to its dominance in mob
0 views • 12 slides
Design and Implementation of Shifters in ALU for Single-Cycle Processors
The detailed discussion covers the construction of a multifunction Arithmetic Logic Unit (ALU) for computer processors, specifically focusing on the design and implementation of shifters. Shift operations such as SLL, SRL, SRA, and ROR are explained, with insights into shifting processes and data ex
0 views • 5 slides
Tamper-Evident Pairing (TEP) Protocol for Secure Wireless Pairing Without Passwords
This article discusses the challenges of traditional secure wireless pairing methods that rely on password validation and proposes the Tamper-Evident Pairing (TEP) protocol as a secure in-band solution to protect against Man-in-the-Middle (MITM) attacks. TEP eliminates the need for out-of-band chann
1 views • 40 slides
Actively Secure Arithmetic Computation and VOLE Study
Exploring actively secure arithmetic computation and VOLE with constant computational overhead at Tel Aviv University. Understanding how functions are represented in secure computation using arithmetic circuits over boolean circuits. Efficiently evaluating arithmetic circuits over large finite field
0 views • 36 slides
k-Ary Search on Modern Processors
The presentation discusses the importance of searching operations in computer science, focusing on different types of searches such as point queries, nearest-neighbor key queries, and range queries. It explores search algorithms including linear search, hash-based search, tree-based search, and sort
0 views • 18 slides
Enhancing I/O Performance on SMT Processors in Cloud Environments
Improving I/O performance and efficiency on Simultaneous Multi-Threading (SMT) processors in virtualized clouds is crucial for maximizing system throughput and resource utilization. The vSMT-IO approach focuses on efficiently scheduling I/O workloads on SMT CPUs by making them "dormant" on hardware
0 views • 31 slides
Accessing and Utilizing CPCSSN Secure Research Environment (SRE)
Learn how to access the CPCSSN Secure Research Environment (SRE) for secure data analysis. Follow steps such as setting up VPN, accessing SQL databases, and establishing ODBC connections for statistical analysis using tools like SAS, R, SPSS, or Stata. Enhance your research capabilities within a sec
0 views • 12 slides
Dynamic Load Balancing on Graphics Processors: A Detailed Study
In this comprehensive study by Daniel Cederman and Philippas Tsigas from Chalmers University of Technology, the focus is on dynamic load balancing on graphics processors. The research delves into the motivation, methods, experimental evaluations, and conclusions related to this critical area. It cov
0 views • 57 slides
Enhancing Animal Telemetry Data Systems for Secure Collaboration
Wide spectrum of animal telemetry data collection protocols and platforms require enhanced data stewardship options for secure sharing before public release. The need for a more granular understanding of available data and structured systems integration is crucial. Initial workflow involves providin
0 views • 4 slides
Scaling Multi-Core Network Processors Without the Reordering Bottleneck
This study discusses the challenges in packet ordering within parallel network processors and proposes solutions to reduce reordering delay. Various approaches such as static mapping, single SN approach, and per-flow sequencing are explored to optimize processing efficiency in multi-core NP architec
0 views • 22 slides
STM32WB BLE Secure Connections Overview
This detailed content provides insights into the secure connections in STM32WB BLE devices, covering aspects such as BLE security methods, encryption techniques, pairing processes, key distribution, and security modes and levels. It emphasizes the use of Long Term Keys (LTK), Diffie-Hellman key exch
0 views • 12 slides
Understanding Secure Electronic Transactions (SET)
Secure Electronic Transactions (SET) is an encryption and security specification designed to protect credit card transactions on the Internet. SET provides a secure way to utilize existing credit card payment infrastructure on open networks, such as the Internet, involving participants like clients,
1 views • 6 slides
An Open-Source SPDM Implementation for Secure Device Communication
This article introduces an open-source SPDM (Secure Protocol and Data Model) implementation for secure device communication, developed by Jiewen Yao and Xiaoyu Ruan, Principal Engineers at Intel. SPDM aims to enhance device security through protocols for device authentication, session key establishm
0 views • 29 slides
Exploring Secure Care Services in Scotland
Delve into the world of secure care services in Scotland, focusing on achievements, challenges, and opportunities in providing youth justice. Learn about trends in secure care, reduction in costs, reasons for referrals, and evidence-based programs like DBT in Glasgow. Gain insights from industry lea
0 views • 77 slides
- Understanding Exceptions in Modern High-Performance Processors
- Overview of exceptions in pipeline processors, including conditions halting normal operation, handling techniques, and example scenarios triggering exception detection during fetch and memory stages. Emphasis on maintaining exception ordering and performance analysis in out-of-order execution proc
0 views • 28 slides
Understanding Interrupt Processing Sequence in X86 Processors
X86 processors have 256 software interrupts, functioning similarly to a CALL instruction. When an INT n instruction is executed, the processor follows a sequence involving pushing the flag register, clearing flags, finding the correct ISR address, and transferring CPU control. Special interrupts lik
0 views • 10 slides
Understanding Shared Memory, Distributed Memory, and Hybrid Distributed-Shared Memory
Shared memory systems allow multiple processors to access the same memory resources, with changes made by one processor visible to all others. This concept is categorized into Uniform Memory Access (UMA) and Non-Uniform Memory Access (NUMA) architectures. UMA provides equal access times to memory, w
0 views • 22 slides
Should Ghana Provide Discounts on Cocoa Beans for Local Processors? A Case Study
Ghana's cocoa sector plays a significant role in the country's economy, yet less than 25% of cocoa beans are processed locally, limiting its market share. This case study explores the impact of local processing on Ghana's cocoa industry and discusses the dilemma of value addition. The question of wh
0 views • 14 slides
Understanding Shared Memory Coherence, Synchronization, and Consistency in Embedded Computer Architecture
This content delves into the complexities of shared memory architecture in embedded computer systems, addressing key issues such as coherence, synchronization, and memory consistency. It explains how cache coherence ensures the most recent data is accessed by all processors, and discusses methods li
0 views • 47 slides
Constructive Computer Architecture: Multistage Pipelined Processors
Explore the concepts of multistage pipelined processors and modular refinement in computer architecture as discussed by Arvind and his team at the Computer Science & Artificial Intelligence Lab, Massachusetts Institute of Technology. The content delves into the design and implementation of a 3-stage
0 views • 28 slides
Data Hazards in Pipelined Processors: Understanding and Mitigation
Explore the concept of data hazards in pipelined processors, focusing on read-after-write (RAW) hazards and their impact on pipeline performance. Learn strategies to mitigate data hazards, such as using a scoreboard to track instructions and stall the Fetch stage when necessary. Discover how adjusti
0 views • 23 slides
Understanding Instruction Flow Techniques in High-IPC Processors
Explore the intricate processes involved in optimizing instruction flow within high-IPC processors, tackling challenges such as control dependences, branch speculation, and branch direction prediction. Learn about the goals, impediments, branch types, and implementations that shape the efficient exe
0 views • 80 slides
Leveraging Graphics Processors for Accelerating Sonar Imaging via Backpropagation
Utilizing graphics processors to enhance synthetic aperture sonar imaging through backpropagation is a key focus in high-performance embedded computing workshops. The backpropagation process involves transmitting sonar pulses, capturing returns, and reconstructing images based on recorded samples. T
0 views • 18 slides
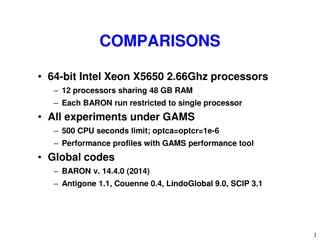
Performance Comparison of Optimization Solvers on Intel Xeon X5650 Processors
Experiment results comparing the performance of optimization solvers (BARON, Antigone, LindoGlobal, SCIP, Couenne) on Intel Xeon X5650 2.66Ghz processors with 48GB RAM. The study includes 369 NLPs from various libraries and an aggregate analysis of 1740 NLPs and MINLPs. Performance profiles generate
0 views • 6 slides
Flynn's Taxonomy: Classification of Computer Architectures
Michael Flynn's 1966 classification divides computer architectures into SISD, SIMD, MISD, and MIMD based on the number of instruction streams and data streams. SISD corresponds to traditional single-processor systems, SIMD involves multiple processors handling different data streams, MISD has multip
0 views • 10 slides