Why Simplified Data Manipulation is the Future of BI Dashboard Software
Discover why simplified data manipulation is revolutionizing BI dashboard software. As businesses strive for real-time insights and data-driven decisions, the need for intuitive and efficient BI tools becomes paramount.
3 views • 6 slides
Simplified Data Manipulation and Cleaning Without Coding
To fully experience and leverage the potential of your data, complex coding is not always the best bet. Business users and analysts can increase their productivity by leaving everyday challenges at bay. Our latest blog explores how no-code Business Intelligence tools are revolutionizing data manipul
3 views • 6 slides
Insights into "The Tempest": Power, Manipulation, and Restoration
In Act III of "The Tempest," themes of power, manipulation, and restoration unfold. Ferdinand's labor for Miranda symbolizes love's easing of difficulties. Prospero orchestrates magic and illusion to ensure Miranda and Ferdinand fall in love. Stephano's drunken power play highlights selfish motives
0 views • 13 slides
Analyzing Iago's Manipulation in Othello Act 2 Scene 3
Explore the intricate dynamics between Iago and Cassio in Act 2 Scene 3 of Othello. Dive into the themes of manipulation, loyalty, and deception as Iago orchestrates his plans while examining Cassio's susceptibility to Iago's ploys. Uncover the layers of dramatic irony, thematic contrasts, and chara
3 views • 8 slides
Genetic Engineering: Techniques, Models, and Applications in Microbial Biotechnology and Plant Genetics
This document explores genetic manipulation, gene manipulation techniques, gene transfer techniques, applications in synthetic and developmental biology, genetically modified organisms/plants, plant tissue culture, micropropagation of plants, genetics in evolution, and genetics in crop improvement m
1 views • 5 slides
Arrays as Pointers: Fundamentals of Computing
Explore the concept of using arrays as pointers in the context of computing. Learn how to create array of char pointers to store multiple strings, access elements in arrays of pointers, and understand the rules for accessing individual elements. Discover the nuances of pointer manipulation and array
1 views • 10 slides
How Advanced Data Manipulation Techniques Are Transforming UK Businesses
Gain insight into the ways that cutting-edge data manipulation techniques are reshaping the UK corporate landscape with more improved decision-making, effectiveness in operations, and greater client customisation. With the use of real-world examples
1 views • 9 slides
Genetic Manipulation in Environmental Biotechnology
Genetic manipulation strategies in environmental biotechnology involve techniques like gene splicing and molecular cloning to modify genes directly. These methods have various applications such as isolating genes, producing specific molecules, improving biochemical production, creating organisms wit
1 views • 20 slides
Enhancing Crop Yield and Quality Through Genetic Manipulation
This chapter explores methods to improve crop productivity and quality through genetic enhancements such as increasing yield and improving plant material quality. It discusses factors influencing crop productivity, such as solar radiation and photosynthetic efficiency, and factors determining crop q
2 views • 19 slides
Ethical Considerations in Manipulated Photography for Media
Ethical control in photojournalism involves capturing non-fiction events without manipulation, but some control over the image is acceptable within ethical bounds. However, moving into manipulated images for non-news events requires a different approach, involving subject and scene manipulation for
1 views • 28 slides
How Advanced Algorithms Are Reshaping Data Manipulation
Explore the transformative impact of advanced algorithms on data manipulation in our latest feature. This insightful exploration delves into the sophisticated technologies revolutionizing business analytics and understanding what is data manipulation
0 views • 7 slides
Analyzing the Impact of Glucose on Students' Listening Span
Research presented by Dr. Christine Malone explores how drinking glucose can enhance listening span in students who miss breakfast. The study investigates if the experiment qualifies as a true experiment by analyzing key features like manipulation, measurement, comparison, and control. Internal vali
1 views • 12 slides
APL - A Functional Language with Array Paradigms
APL, named after the book "A Programming Language Paradigms," is a functional language with a focus on array manipulation. Developed in the 1960s by Kenneth E. Iverson, it has had a significant impact on the development of spreadsheets and computer math packages. APL operates with chains of monadic
0 views • 11 slides
Basin Manipulation Simulation Analysis Tool Overview
Basin Manipulation Simulation Analysis Tool provides a comprehensive solution for managing and analyzing basin data, including tasks like basin manipulation, simulation analysis, case management, and defining simulation time steps. The tool allows for easy data entry, visualization of simulation res
4 views • 17 slides
Insights into Animal Farm: A Narrative of Betrayal and Manipulation
The narrative of Animal Farm encapsulates the evolution from an idealistic society to a manipulative regime, illustrating themes of betrayal, rule violations, manipulation, leadership exaggeration, harsh penalties, rumor spreading, forced labor, and emotional suppression within a communist-socialist
1 views • 10 slides
Mastering Algebraic Manipulation: Simplifying and Solving Equations
Understanding the fundamental concepts of algebraic manipulation, including the four arithmetic functions and reduction techniques to find unknown variables like x and y. Learn how to isolate variables by applying arithmetic operations step by step, even in more complex expressions, by following spe
1 views • 8 slides
Frame Pointer Attacks and Exploit Development with pwntools
Explore the concepts of frame pointer attacks, LD_PRELOAD usage, and exploit development with pwntools library. Discover how to spawn a shell using LD_PRELOAD or a constructor, along with the limitations and challenges associated with command-line exploitation.
0 views • 30 slides
Analysis of Lady Macbeth's Manipulation in Shakespeare's Macbeth
In a pivotal moment in Macbeth, Lady Macbeth's manipulation of her husband is showcased when she calls upon supernatural forces to overcome his kindness and convince him to kill Duncan. This extract is crucial in introducing Lady Macbeth's character and power dynamics within the play, particularly h
3 views • 49 slides
Investigating Performance Bottlenecks in Smart Pointer Management
Investigation into performance issues caused by smart pointer manipulation, focusing on the use of boost
0 views • 8 slides
Introduction to Data Manipulation in R with dplyr
Explore the essential functions of dplyr for data manipulation in R, focusing on key operations like selecting variables, filtering observations, rearranging rows, summarizing data, adding new variables, and grouping operations. Discover the basic structure of dplyr code to efficiently manipulate an
1 views • 21 slides
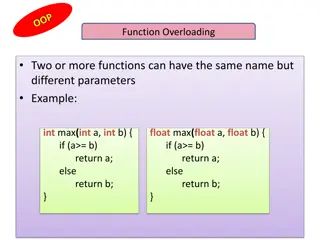
Function Overloading and this Pointer in C++
Explore the concept of function overloading in C++, allowing multiple functions with the same name but different parameters. Learn about the this pointer in object-oriented programming, which holds the memory address of the current object using a function. See examples of how to implement these conc
0 views • 13 slides
High Brightness Electron Beams: Beam Manipulation and Acceleration Using Dielectric-Lined Waveguides
This presentation discusses the manipulation and acceleration of electron beams through the use of dielectric-lined waveguides. It delves into motivations for accelerators, beam-driven acceleration, wakefields, transformer ratio, and the search for continuous smooth shapes in beam technologies. Vari
2 views • 30 slides
Database Language and Interfaces Overview
A database management system (DBMS) requires appropriate languages and interfaces to handle queries and updates for data manipulation and control. This includes Data Definition Language (DDL), Data Manipulation Language (DML), Data Control Language (DCL), and Transaction Control Language (TCL). Each
1 views • 12 slides
Mastering Advanced R with Tidyverse for Efficient Data Analysis
Unlock the power of Advanced R with Tidyverse through in-depth exploration of functions, operators, data manipulation, and efficient coding techniques. Dive into Tidyverse packages like tibble, readr, and dplyr to streamline data storage, reading, and manipulation. Learn to work with RStudio Project
2 views • 90 slides
Effective S106 Process Management in Local Authority: Insights from Stephen Pointer, Harborough District Council
Explore the expertise of Stephen Pointer, Strategic Planning and Housing Manager at Harborough District Council, in managing an effective Section 106 (S106) process. Discover his role, responsibilities, and experiences in navigating the complexities of national and district contexts, community inter
0 views • 19 slides
How to Lie with Statistics: Uncovering Deceptive Data Manipulation
Explore the deceptive world of statistics and how they can be used to mislead. Learn about the marriage of math, science, and art in making sense of data. Discover examples of biased sampling leading to inaccurate predictions, as showcased in the 1936 election attempt by The Literary Digest Magazine
2 views • 46 slides
Code Pointer Integrity Team Overview
Code Pointer Integrity Team, consisting of Po-Jen Lai, Timmy Lin, Chun-Yu Hsiung, and Hung-Lin Wu, under the instruction of Scott Mahlke, is focused on understanding control flow hijack, memory control, and protection mechanisms. They explore new approaches to enhance code safety while minimizing ov
0 views • 25 slides
Automatic Generation of Research Highlights from Scientific Abstracts
Huge growth in scientific publications has made it challenging for researchers to keep up with new research. This project focuses on automatically constructing research highlights from paper abstracts using deep learning models. The system employs sequence-to-sequence models with attention and point
0 views • 9 slides
Storage and Manipulation of Liquefied Gases with Dewars and Cryostats
Storage and manipulation of liquefied gases involve using specialized equipment like Dewars and Cryostats to minimize heat transfer and maintain low temperatures. Dewars, invented by James Dewar, are double-walled vacuum vessels designed to store liquefied gases with minimal losses. The use of vacuu
2 views • 11 slides
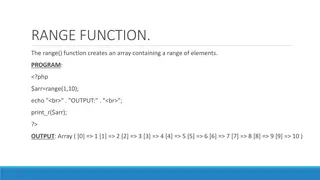
PHP Array Manipulation Functions Overview
The PHP code snippets demonstrate the use of various array manipulation functions like range(), min(), max(), array_slice(), adding/removing array elements, and array_unique(). These functions allow for creating ranges of elements, finding the minimum and maximum values in an array, extracting selec
2 views • 11 slides
Direct Manipulation in HCI
In this lecture, learn about the concept of direct manipulation in Human-Computer Interaction (HCI), including its benefits, drawbacks, and related terms such as engagement, distance, semantic, and articulatory distances. Explore the evolution of GUIs and interaction styles, and compare edge maps an
1 views • 24 slides
String Manipulation and Palindrome-Anagram Exercises
Explore exercises on string manipulation, counting characters in a sentence, creating a diamond-shaped array based on a string's characters, checking palindrome strings, and detecting anagrams. Practice coding skills with these engaging challenges.
0 views • 5 slides
Data Manipulation Using MarcEdit for ANBD Preparation
Explore in-depth data manipulation techniques with MarcEdit to prepare your data for the ANBD. Learn how to work with Regular Expression Language, extract and manipulate data effectively, and utilize MarcEdit's global editing functions. Dive into examples and gain insights into using regular express
1 views • 30 slides
Narcissistic Abuse: The Insidious Manipulation of Victims
Narcissistic abuse is a form of severe psychological and emotional manipulation that targets a victim's spirit and identity. The abuser employs tactics such as lying, manipulation, denial of reality, and control. This abuse is often invisible and devastating, characterized by a lack of empathy and a
1 views • 15 slides
Robot Learning for Manipulation: Challenges and Opportunities
A review of robot learning for manipulation presents key motivations, concepts, and formalization of learning tasks. It covers various aspects such as manipulations as physical systems, task decompositions, object-centric generalization, and learning object and environment representations.
0 views • 19 slides
Pointers in C: A Beginner's Guide
Delve into the world of pointers in C with this comprehensive guide covering topics such as the address operator, pass by copy versus pass by reference, pointer usage, NULL pointers, pointer allocation, and practical experiments to enhance your understanding. Learn about the fundamentals of pointers
0 views • 22 slides
Ethical Analysis of Manipulation in Organ Allocation System
This resource tackles the issue of manipulation in organ transplant waitlist priority through unnecessary medical interventions. It highlights the ethical concerns, potential harms, and ways to mitigate this manipulation, urging adherence to systemic safeguards and ethical clinical practice.
2 views • 9 slides
Smart Pointers in C++ - Bonus Lecture CSE390c Spring 2022
Explore the concept and benefits of smart pointers in C++ as a solution to managing heap-allocated memory more effectively. Learn about avoiding memory leaks and errors when handling pointers through smart pointer implementation. Dive into a Toy Smart Pointer example using a custom class template.
0 views • 36 slides
Innovative Multicellular Computing Circuits for Genetic Manipulation
Cells are utilized as computational devices in a innovative approach for genetic manipulation. Various logic gates and promoters are combined to achieve complex circuit behavior without the need for genetic manipulation. Advantages include a wide dynamic range and low variability, but with the drawb
2 views • 10 slides
Microprocessor & Micrcontroller
The 8085 microprocessor architecture involves key components like register array, ALU, program counter, stack pointer, address latch, and more. Learn about the functionality and importance of each unit in data manipulation and communication. Dive into the details of general-purpose registers, data s
5 views • 17 slides