Phishing and Social Media Scam Protection | Scam Killnet Switch
The best online parental control tool is Scam Killnet Switch; protect your family against phishing and social media scams. Watch out for your family members while they play around on the internet. Your online interactions are kept safe by our cutting-edge technology, which recognises and stops harmf
3 views • 2 slides
State of Oregon Phishing Awareness Program Implementation Overview
The State of Oregon has launched a comprehensive Phishing Awareness Program to educate and protect employees against phishing attacks. The program includes phishing simulations, security culture surveys, and clear steps for handling suspicious emails. Various phases have been implemented to ensure a
0 views • 10 slides
Oregon Phishing Awareness Program: Implementation and Strategy
The State of Oregon's Phishing Awareness Program involves a structured approach to combat phishing attacks. It includes various phases such as pilot programs, monthly phishing simulations, and employee engagement strategies. The program aims to educate staff at all levels on identifying and reportin
1 views • 10 slides
Understanding Investigations in Science
Investigating in science involves various approaches beyond fair tests, such as pattern-seeking, exploring, and modeling. Not all scientists rely on fair tests, as observational methods are also commonly used. The scientific method consists of steps like stating the aim, observing, forming hypothese
1 views • 20 slides
Phriendly Phishing Training Solutions Overview
Phriendly Phishing offers security awareness and phishing simulation training solutions to organizations in Australia and New Zealand. Their training covers topics like phishing, spear-phishing, ransomware, malware, and scams, focusing on empowering employees to detect and prevent cyber threats effe
6 views • 42 slides
Understanding Modern Phishing Techniques and Evilginx Framework
Explore the evolution of phishing from its inception to modern-day strategies like Evilginx, a man-in-the-middle attack framework. Learn about the effectiveness of phishing, its impact on financial losses, and how Evilginx bypasses multi-factor authentication to capture sensitive information. Dive i
7 views • 30 slides
Understanding Phishing Attacks: Risks, Prevention, and Awareness
Phishing attacks are prevalent cybercrimes where attackers deceive individuals into divulging sensitive information or engaging in harmful actions. These attacks can happen through various channels such as emails, texts, or websites. The perpetrators aim to manipulate emotions like curiosity, greed,
1 views • 47 slides
Insurance Investigations: Handling Privilege, Coverage, and Disclosure
Explore the nuances of responding to insurance investigations in this 90-minute interactive webinar. Learn how to cooperate effectively while protecting privilege, coverage, and confidential information. Gain valuable insights on preventing insurer abuse, misuse, and disclosure, as well as safeguard
0 views • 52 slides
Environmental Investigations Unit of Houston Police Department
Environmental Investigations Unit of the Houston Police Department is responsible for investigating crimes with environmental impact in the city, such as water pollution, hazardous waste dumping, air pollution, and illegal dumping. They work on large-scale investigations involving releases of hazard
0 views • 6 slides
Protect Yourself from Phishing Scams: Essential Tips to Stay Safe Online
Phishing is a serious threat that can lead to identity theft and financial loss. Learn what phishing is, how it works, and crucial tips to prevent falling victim to such scams. Stay informed about the latest phishing techniques, think before clicking on unfamiliar links, use anti-phishing tools, ver
0 views • 8 slides
Understanding Cyber Crime: Risks and Prevention Measures
Cyber crime, including hacking, phishing, and pharming, poses a significant threat in today's digital world. Learn about the types of hackers and how to tackle phishing and pharming attacks effectively. By following security measures such as avoiding sharing sensitive information and updating anti-p
4 views • 18 slides
Environmental Investigations Unit of Houston Police Department
The Environmental Investigations Unit of the Houston Police Department is responsible for investigating crimes with an environmental connection in the city. From water pollution to hazardous waste dumping, the unit handles a wide range of cases, focusing on criminal investigations and coordinating s
0 views • 6 slides
Phishing Survival Guide: Educating Children and Parents
Empower children to identify and respond to phishing attacks with this comprehensive phishing survival guide. The guide includes learning outcomes, lesson notes, and instructions to create an engaging pocket guide for parents. Learn how to report suspicious emails, handle suspicious links, and prote
0 views • 4 slides
Understanding Phishing: Types, Risks, and Prevention Strategies
Phishing is a prevalent cyber threat that aims to deceive individuals into divulging sensitive information. This detailed guide covers different types of phishing attacks, their objectives, and effective prevention measures. It highlights how phishing emails target users through fear, urgency, rewar
0 views • 17 slides
Child Placing Agencies and Child Caring Institutions Overview
Explore the procedures and protocols followed by Special Investigations and Regular Investigations units when dealing with allegations of maltreatment in Child Placing Agencies (CPA) and Child Caring Institutions (CCI). Learn about the different types of investigations and how cases are handled base
1 views • 16 slides
Advanced Financial Crime Investigations and Anti-Money Laundering Overview
Explore the world of advanced financial crime investigations, anti-money laundering, and the importance of estimating financial reporting errors. Delve into the role of internal audit and investigations, understand the significance of changes in accounting estimates, and learn why estimation is vita
0 views • 63 slides
Best Practices for Conducting Effective Investigations
Understanding the purpose, principles, and process of investigations is crucial for conducting fair and well-managed inquiries. Learn about the impact of improper investigations and follow a structured approach encompassing appointment of an investigating manager, defining scope, planning, evidence
0 views • 41 slides
How to Protect Your Cryptocurrencies from DeFi Phishing Scams
Learn how to protect your cryptocurrencies from DeFi phishing scams in this comprehensive guide. Understand the common tactics scammers use and discover practical strategies to safeguard your assets. From recognizing suspicious links to using secure
1 views • 4 slides
A Rare Case of Ascites in a 22-Year-Old Female: Clinical Presentation and Investigations
A 22-year-old female presented with abdominal distension and pain. Her medical history, family history, and personal habits were reviewed. Examination revealed mild hepatomegaly and shifting dullness. Lab investigations showed normal values with no signs of infection. Ascitic fluid analysis indicate
1 views • 20 slides
Understanding Offsite Investigations in CSA's National Safety Interventions
Offsite Investigations are part of CSA's safety tools, conducted remotely to ensure carrier compliance. Safety Investigators review online documents to diagnose issues and provide corrective actions. Failure to comply may result in penalties or onsite investigations. Offsite Investigations have show
0 views • 7 slides
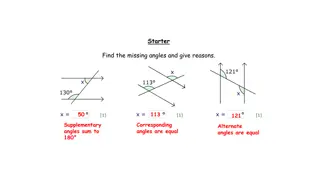
Geometry Investigations and Theorems
Explore various circle theorems and investigations involving angles, tangents, radii, and circumferences. Discover the relationships between angles at the center and circumference, the properties of tangents, and the angle measurements within a circle. Engage in investigations to understand the sign
6 views • 26 slides
Phishing Survival Guide: How to Recognize and Respond to Suspicious Emails
Learn how to spot a phishing email and what steps to take if you receive one or fall victim to a phishing scam. Find out how to identify suspicious links, recognize phishing attempts, and protect yourself from giving out personal information or losing money. Stay informed and secure in the digital a
2 views • 5 slides
Essential Cybersecurity Practices for Safe Online Activities
Phishing attacks come in various forms such as common phishing, spear phishing, whaling, smishing, and vishing. It's crucial to be cautious when connecting to Wi-Fi networks, secure your passwords, and follow safe web browsing practices to protect your personal information online.
4 views • 5 slides
Rapid Investigation Service Overview
The Wessex RIS is a new cancer referral pathway aimed at patients with concerning non-specific symptoms. Working in partnership with acute trusts in Wessex, the service provides timely investigations to exclude cancer in such patients. Established as part of the National Rapid Diagnostic Centre proj
0 views • 15 slides
Staying Safe Online_ How to Avoid Phishing Scams?
Learn simple tips to protect yourself from phishing scams and keep your online accounts secure. Stay safe online today!\n
2 views • 5 slides
ReBIT Operational Excellence Webinar Series: Anti-Phishing Campaign
The ReBIT Operational Excellence Webinar Series features the Anti-Phishing Campaign, aiming to enhance cybersecurity postures in the industry through DMARC implementation and threat intelligence sharing. The webinar covers topics such as phishing mitigation strategies, DMARC technical details, and c
0 views • 10 slides
Effective Accident Investigations for Safety in the Workplace
Understanding the importance of accident investigations and their objectives is crucial for workplace safety. This content covers the definition of accidents, accident investigation objectives, the purpose behind investigations, and who typically conducts them. It emphasizes the need for thorough in
0 views • 34 slides
Understanding Phishing, Viruses, and Online Security
The internet can be a dangerous place with threats like viruses, worms, Trojan horses, and phishing scams. Learn how to protect yourself against these cyber threats and secure your personal information online. Be vigilant against email phishing schemes and follow tips to avoid falling victim to onli
0 views • 16 slides
Watch Out for Online Scams and Phishing Attempts
Be cautious of clickbait, loot boxes, and phishing schemes online. Stay alert for misleading titles and lookalike websites. Protect your accounts by avoiding suspicious links and always purchase from official websites. Remember: if it seems too good to be true, it probably is.
0 views • 9 slides
Protect Yourself from Phishing Scams: Key Tips for Members
Phishing is a deceitful attempt by fraudsters to extract personal information from individuals, often through emails pretending to be from trusted sources like credit unions. The scammers aim to trick you into divulging sensitive details like passwords or account information. Learn how to recognize
0 views • 11 slides
Secure Online Behavior: Learn to Identify and Protect Against Cyber Threats
Enhance your knowledge on appropriate cyber behavior and how to identify phishing emails, handle phishing attempts, recognize phony phone calls, protect personal information, and more. Understand the risks and consequences of mishandling cyber threats to safeguard your online presence.
0 views • 4 slides
Protect Yourself from Online Scams: Tips and Examples
Learn about scams, identity theft, and phishing schemes, along with ways to safeguard your personal and financial information online. Discover common tricks used by scammers and how to spot and avoid falling victim to online fraud. Explore examples of phishing emails and strategies to protect yourse
0 views • 13 slides
Practical Considerations for Interacting with Criminal Authorities During Internal Investigations
This content discusses the legal obligations and privacy issues involved when interacting with criminal authorities during internal investigations. It covers topics such as revealing information, privacy concerns with devices, documenting investigations, and standard procedures for requesting inform
0 views • 12 slides
Cyber Security Awareness and Best Practices
Enhance your cyber security knowledge with terminology like Social Engineering and Spear Phishing, and learn about common cybercrime activities such as phishing and ransomware attacks. Stay informed to protect yourself and your organization from malicious threats.
0 views • 26 slides
Cybersecurity Awareness: Phishing Investigations Practitioner Notes and Game Instructions
This content focuses on teaching children to identify phishing tactics used by individuals and organizations through activities and lesson notes. It emphasizes recognizing scam attempts, understanding safe online practices, and evaluating suspicious messages. The interactive game instructions instru
0 views • 4 slides
Learn How to Identify Genuine Emails and Avoid Phishing Attempts
Understanding how to spot phishing emails is crucial for maintaining email security. This activity presents various email examples for evaluation – distinguishing between genuine communications and potential phishing attempts. By honing this skill, individuals can protect themselves from online sc
0 views • 9 slides
Innovative Phishing-Resistant Cardholder Authentication and Payment Confirmation Method
Introducing a method for cardholder authentication and secure payment confirmation that is phishing-resistant, requires no interaction with the issuing bank at transaction time, and provides merchants with a non-repudiable cryptographic signature on transactions. This innovative approach leverages t
0 views • 8 slides
Direct Payments & Social Care Investigations Workshop Overview
Explore the key areas covered in the Direct Payments & Social Care Investigations Workshop, focusing on Direct Payments, social care fraud, applications, counter-fraud work, investigations, and overcoming cultural resistance. Delve into the risks associated with social care fraud and learn about the
0 views • 28 slides
Protecting Your Data_ Tips for Preventing Phishing Attacks
Learn practical tips to protect your data and avoid phishing scams. Stay safe online with easy-to-follow advice to prevent cyber threats.
2 views • 7 slides
Understanding Network Breaches: Methods and Mitigation
Discover how networks are breached through phishing, exposed services, and publicly available exploits as explained by a security consultant. Learn about phishing techniques, externally exposed services vulnerabilities, and common exploits used to gain unauthorized access. Explore ways to mitigate t
0 views • 22 slides