Understanding DNA Extraction, Quantitation and Amplification
Learn the fundamentals of DNA extraction, including the two categories of extraction, potential issues, and how to determine the extraction category of your sample.
3 views • 40 slides
Revolutionary Lithium Extraction Technology by SORCIA/IBAT
SORCIA/IBAT's innovative lithium extraction process eliminates the need for chemicals, ensuring efficiency, resource protection, and cost-effectiveness. The modular and mobile plant design allows for rapid deployment with high flexibility, making it a game-changer in the industry. This breakthrough
0 views • 8 slides
Unlocking Solutions: Addressing QuickBooks Company File Incorrect Password Issue
Unlocking Solutions: Addressing QuickBooks Company File Incorrect Password Issues\nQuickBooks, a vital tool for businesses, can encounter password-related hurdles, disrupting workflow. This guide explores causes and solutions to incorrect password issues. Forgotten passwords, user permission errors,
1 views • 5 slides
Understanding DNA Extraction from Strawberries in Molecular Genetics
In this molecular genetics lesson, students explore DNA extraction from strawberries. The content covers the structure of DNA, nucleotides, and the role of DNA in determining genetic information. Students learn about the components of nucleic acids, DNA functions, and the double helix structure of d
1 views • 87 slides
Cybersecurity Best Practices for Password Protection and Incident Response
Enhance your cybersecurity knowledge with insights on password management, cybercriminal tactics, creating strong passwords, and password complexity. Learn how to safeguard your data and prevent cyber threats by implementing strong password rules, multi-factor authentication, and incident response s
2 views • 24 slides
Understanding Device Settings and Strong Passwords for Digital Citizenship
This lesson focuses on understanding device settings and the importance of creating strong passwords for digital citizenship. It covers topics such as changing backgrounds, locking screens, creating strong passwords, common password mistakes to avoid, and tips for password safety. The lesson also in
1 views • 11 slides
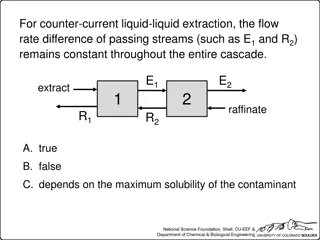
Liquid-Liquid Extraction Techniques and Considerations
Understanding liquid-liquid extraction processes like counter-current and co-current cascades, material balances, and system degrees of freedom. Topics include impact of flow rates, partition coefficients, solvent ratios, and purity on extraction efficiency.
0 views • 14 slides
Strengthen Your Digital Literacy with Strong Password Strategies
Enhance your digital literacy by learning about the importance of strong passwords, strategies for creating secure passwords, and the role of password managers. Explore various resources, videos, and tools to improve your password security and protect your online accounts effectively.
0 views • 5 slides
Promote Feature Adoption with Self-Service Password Reset Posters
Enhance feature adoption of self-service password reset among your employees with these ready-to-use posters. Simply customize and print them to encourage password security awareness in your workplace. Don't risk productivity downtime due to forgotten passwords – empower your team to reset their p
0 views • 13 slides
Extraction Methods in Pesticide Residue Analysis for Food Safety
Extraction methods play a crucial role in separating pesticide residues from food matrices for analysis. Techniques involve using solvents to efficiently remove pesticides without causing chemical changes. The choice of extraction method depends on the substrate type, with liquid and solid substrate
6 views • 25 slides
Slow Extraction Operations at Fermilab Main Injector
Overview of slow extraction operations at Fermilab Main Injector, covering beam transport, low to medium energy user test beams, Drell-Yan experimental beam, and spill procedures. Details on beam targets, production, and observation of high-energy positrons. Also, insights on spill regulation techni
0 views • 12 slides
Enhanced Directional Extraction of Very Cold Neutrons Using Diamond Nanoparticle Reflector
Alexander Nezvanov, a researcher at Frank Laboratory of Neutron Physics, presented a study on enhanced directional extraction of very cold neutrons using a diamond nanoparticle powder reflector. Very cold neutrons (VCN) have unique properties making them ideal for various applications in neutron tec
0 views • 11 slides
Validation Study of Rapeseed Oil Body Extraction Methods
This study explores the validation of two rapeseed oil body extraction methods. It delves into the common uses of rapeseed, the components of oil bodies, and their potential applications in the human food system. The materials and methods section details the extraction processes, including dry and w
2 views • 23 slides
Metal Extraction: Processes and Applications
Metals play a crucial role in various industries, but their extraction from ores is a complex process. Some metals occur naturally in an uncombined form, indicating their low reactivity. Through heat alone, unreactive metals like lead can be separated from their ores. This extraction process involve
2 views • 16 slides
DNA Extraction: A User's Manual for Plant Material
A step-by-step guide on preparing, extracting, and storing DNA from plant material for first-time users, specifically tailored for individuals in botanical fields. The manual covers materials needed, CTAB buffer mixture preparation, leaf material preparation, DNA extraction process, and proper stora
0 views • 8 slides
Safely Logging Password-Derived Measurements for Web Login Systems
Design a secure measurement framework called Gossamer to assess risks associated with password-based measurements for web login systems. Explore ways to differentiate between benign and malicious traffic, and consider adding instrumentation to enhance security. Learn how attackers exploit password-d
0 views • 12 slides
Guide to Logging in and Setting Up Core-CT for the First Time
Accessing Core-CT for the first time involves using your State of Connecticut Employee ID and temporary password. Follow the steps to log in, set up a new password, and establish a forgotten password help feature. This guide provides clear instructions and visuals for each step.
0 views • 19 slides
DNA Extraction from Fruit Lab: Strawberry Extraction Method
Explore the fascinating process of breaking cell barriers and extracting DNA from strawberry cells. This comprehensive lab guide provides detailed instructions on how to extract DNA using simple materials like strawberries, plastic bags, ethanol, liquid detergent, and more. From mashing the fruit to
1 views • 11 slides
Unconventional Gas Extraction: Balancing Industry and Environmental Concerns
Study the implications of unconventional gas extraction on health, quality of life, and the global energy context. Explore the impacts of technologies like shale gas fracking and coal bed methane on climate change, energy supplies, and economic sustainability. Consider the risks posed by water-inten
0 views • 39 slides
Extraction in Orthodontics and Dentofacial Orthopedics: Comprehensive Overview
Painless extraction of teeth is crucial in orthodontic treatment for achieving normal occlusion and creating space in the dental arch. Historical background traces the evolution of extraction in orthodontics. The need for extraction is determined by factors like arch length-tooth material ratio, int
0 views • 38 slides
Automated Information Extraction for Decision Making in Data
Processing unstructured data from sources like news, blogs, and papers is a challenge due to the volume of digital data. The Dutch-Belgian Database Day 2013 discusses event extraction as a solution using natural language processing and statistics. Event extraction can benefit systems in personalized
0 views • 20 slides
Enhancing Open Information Extraction with Focused Entailment Graphs
Explore how Focused Entailment Graphs improve Open Information Extraction (Open IE) by structuring propositions and their entailment relations. These graphs help consolidate natural language expressions like "relieve headache" and "treat headache" to organize data hierarchically for better understan
0 views • 52 slides
Overview of Tooth Extraction and Contraindications: Dr. Mohammed Alaraji
Tooth extraction is a common procedure performed by dentists, with severe caries and periodontal disease being primary indications. Dr. Mohammed Alaraji discusses the importance of extraction methods and contraindications for the procedure in this informative presentation.
0 views • 31 slides
Interactive Password Security Activity for Children
This presentation recaps the importance of strong passwords, techniques for creating them, and the significance of two-factor authentication. The lesson notes guide discussions on creating secure passwords using the "three random words" method and avoiding personal details. The interactive game "Gue
0 views • 4 slides
Zero-Shot Relation Extraction Based on Contrast Learning
This paper presents a zero-shot relation extraction approach based on contrast learning, aiming to improve the efficiency of relation extraction tasks. The methodology involves utilizing a knowledge graph to extract relational triplets and leveraging zero-shot learning to automate the process. The s
0 views • 21 slides
Best Practices for Secure Password Storage - OWASP Foundation Guidelines
Learn about secure password storage techniques recommended by OWASP Foundation, including adding salt, slowing down hashing functions, using HMAC isolation, and imposing difficult verification processes on attackers. Remember to use proper encoding, avoid limiting password types or lengths unreasona
0 views • 10 slides
Techniques and Tools for Offline Password Cracking
Explore the world of offline password cracking techniques using tools like John the Ripper. Learn about the motivation behind cracking user account passwords, gaining root privilege, and compromising vulnerable systems to obtain password hashes for further exploitation. Enhance your understanding of
0 views • 15 slides
Understanding Fine-Grained Password Policies in Active Directory
Explore the intricacies of Fine-Grained Password Policies (FGPP) in Active Directory, covering topics such as domain account policies, policy recovery methods, interpreting pwdProperties attribute, and implementing PSOs for granular password settings. Delve into the nuances of password complexity, h
0 views • 11 slides
Understanding Caffeine Extraction from Tea Leaves
Caffeine, a widely consumed alkaloid, is extracted from tea leaves using organic chemistry techniques. This process involves liquid-liquid extraction to isolate the caffeine from the mixture of substances. The efficiency of extraction relies on the solubility of the target compound in a chosen solve
0 views • 17 slides
Overview of Mu2e Slow Extraction Workshop at Fermilab by Vladimir Nagaslaev
This content discusses the Mu2e project at Fermilab, focusing on slow extraction techniques for beam delivery. It covers beam facilities, characteristics of Muon Campus, design requirements, beam losses, new MARS simulations, and losses in the extraction beam line. Details include beam kinetics, spi
0 views • 17 slides
Solid Phase Extraction Optimization Experiment for Research Use Only
This experiment involves optimizing solid-phase extraction using Agilent Bond Elut C18 cartridges for research purposes. The procedure includes preparing standard solutions, conditioning cartridges, loading samples, washing, and analyzing by HPLC to determine recoveries. The goal is to optimize extr
0 views • 12 slides
Understanding DNA Extraction Process: Steps and Importance
DNA extraction is a crucial process in molecular biology that involves separating DNA from cellular components. The process includes steps like lysis, precipitation, and purification to obtain pure DNA samples. Careful handling and proper labeling of samples are essential to prevent contamination. T
0 views • 10 slides
Biochemical Methodology 530 - Lactate Dehydrogenase Extraction and Purification Experiment
This course focuses on the extraction and purification of lactate dehydrogenase (LDH) using a series of procedures involving tissue preparation, centrifugation, and ammonium sulfate precipitation. The methodology includes detailed steps from preparing the extraction buffer to isolating LDH in differ
0 views • 10 slides
Gold Extraction Methods and Characteristics Explained
Gold extraction involves various methods such as hard rock mining, panning, sluicing, and cyanidation. Gold is known for its density, malleability, conductivity, and durability, making it ideal for jewelry, dentistry, and technology. Different types of gold ores exist, including native gold and ores
0 views • 12 slides
Understanding Password Security: Techniques and Best Practices
Delve into the world of password security with this comprehensive guide, covering topics such as password gathering, cracking strategies, tools, types of passwords, hashes, salting, better hashes, and hash identification. Learn how to enhance security measures and protect against malicious attacks.
0 views • 20 slides
Protecting Password Identifiers in IEEE 802.11-21
This submission addresses the need for safeguarding password identifiers in SAE to ensure privacy and prevent attackers from constructing personally identifiable information. The document presents two potential solutions, ultimately recommending the use of symmetric cryptography for efficient protec
0 views • 11 slides
Understanding Password Guessability Metrics in Real-World Security
Delve into the realm of password guessability metrics to enhance password security. Explore how measuring guessability aids in eliminating weak passwords, aiding users in creating stronger ones, and assessing security against various cracking algorithms. Uncover the significance of statistical and p
0 views • 27 slides
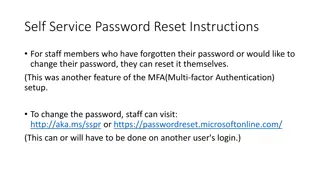
Self-Service Password Reset Instructions for Staff Members
Staff members can easily reset or change their password through self-service options using Multi-Factor Authentication. They can visit the provided links, verify their identity through email and phone number, and reset their password securely. Follow the step-by-step guide for a hassle-free password
0 views • 4 slides
Guide to Logging into Your Chromebook
This step-by-step guide provides instructions on how to log into your Chromebook using either your student ID and password or a QR code. Simply open the lid, press the power button, select "Next," and then proceed to log in with your credentials. For password login, enter your student ID and the def
0 views • 6 slides
Enhancing Wi-Fi Security with User-Friendly WPA3 Passwords
Proposal to enhance Wi-Fi security by incorporating password and password identifier hashes in the SAE commit exchange, enabling devices to hint to access points which password will be used. This approach aims to improve network efficiency and user experience while addressing privacy concerns associ
0 views • 8 slides