Access to the Results of International Publicly Funded R&D for Health Emergencies
Discussion paper on IP and access to publicly funded research results in health emergencies presented by WIPO, focusing on the role of the public sector in driving health emergency R&D, access conditions for international projects, and growing capacity in LMICs. Key points include leveraging public
0 views • 26 slides
Enhancing Access to Medicines and Health Products through Innovative Approaches
Global Health Centre experts discuss how building access into innovation can ensure better access to medicines, vaccines, and health products. Key ideas include planting seeds for access early in innovation, exploring alternative innovation models, and rethinking the relationship between innovation
4 views • 20 slides
Unlocking Mini Grids for Sustainable Development in Papua New Guinea: Business Models & Challenges
Papua New Guinea has ambitious targets for electricity access, electrification, and climate action. The government aims to achieve universal electricity access by 2050, with specific goals to increase access rates and renewable energy penetration. Initiatives like the Rural Electrification Program f
3 views • 27 slides
2022 Thales Access Management Index
Thales Access Management Index highlights the current landscape of access security, revealing insights on multi-factor authentication adoption, remote and privileged user access management, VPN usage trends, challenges faced, and preferences towards third-party access management. The report emphasiz
2 views • 9 slides
Guidelines for Expanded Access to Investigational Drugs and Devices
Providing guidance on types of Expanded Access for drugs, biologics, and devices, this content explains the concept of Expanded Access and the criteria that must be met. It covers different types of Expanded Access for drugs and devices, emphasizing the importance of patient safety and benefit. The
0 views • 10 slides
Personnel Safety Systems and Access Control at CERN Facilities
Personnel Safety Systems at CERN include ODH detection, fire safety measures, and access control to protect personnel from hazards. Various access control layers are implemented to regulate entry to different parts of the facility, ensuring only trained personnel access underground areas. Biometric
0 views • 19 slides
Proposal for Random Access Efficiency Enhancement in IEEE 802.11be Networks
This document presents a proposal for enhancing random access efficiency in IEEE 802.11be networks through a Random-Access NFRP (RA-NFRP) principle. The proposal addresses the challenges of low efficiency in the current UORA procedure and introduces modifications based on the 802.11ax standard to im
5 views • 16 slides
Patient Access to Medical Records: Legal Framework and Key Principles
Patients have the right to access their medical records under the 1998 Data Protection Act and 1990 Access to Health Records Act. Dr. Chris Webb explains the key principles governing patients' access to their own health information, emphasizing the importance of legal compliance and patient empowerm
1 views • 88 slides
Port of Stockton Restricted Area Access Control and ID Card Policy
Access to restricted areas at the Port of Stockton facilities requires possession of a TWIC (Transportation Worker Identification Credential). Only authorized personnel, such as employees, contractors, and those with regular access, may receive a Port Access Card after approval by the Facility Secur
0 views • 6 slides
Microsoft Access: A Comprehensive Overview
Microsoft Access is a powerful Database Management System (DBMS) that integrates the relational Microsoft Jet Database Engine with a user-friendly graphical interface. It is a key component of the Microsoft Office suite, offering tools for database creation, data input, querying, and report generati
0 views • 18 slides
Proposal to Add National Security and Emergency Preparedness Priority Access Feature in IEEE 802.11be Amendment
The document proposes integrating the National Security and Emergency Preparedness (NSEP) priority access feature into the IEEE 802.11be standard to ensure seamless NSEP service experience, particularly in Wi-Fi networks used as last-mile access. The NSEP priority feature at the MAC layer is indepen
0 views • 12 slides
Introduction to Database Security and Countermeasures
Database security is essential to protect data integrity, availability, and confidentiality. Countermeasures such as access control, inference control, flow control, and encryption can safeguard databases against threats. Access control restricts user access, inference control manages statistical da
0 views • 26 slides
National Labor Mapping Application User Roles and Access Overview
This detailed overview outlines the implementation plan, user roles, and access benefits of the National Labor Mapping Application. Users are assigned specific roles with established access through domain usernames, enhancing security measures. Different user roles such as VISN Coordinators, Site Te
0 views • 14 slides
O3 Access Control Solution Overview
O3 Access Control Solution offers unique selling points like single-seat management software, role-based permissions, customizable user information, and more. The system includes a compact controller with multi-format reader support and BACnet Access objects. It integrates with other O3 modules for
0 views • 10 slides
FCCLA and Access from AT&T Program Partnership
FCCLA has partnered with Access from AT&T to provide low-cost wireline home Internet service to qualifying households with at least one resident participating in the U.S. Supplemental Nutrition Assistance Program (SNAP) in AT&T's service area. The program aims to make Internet access more accessible
0 views • 12 slides
Information Commissioner's Briefing at Royal Hamilton Amateur Dinghy Club
The Information Commissioner's Briefing held at Royal Hamilton Amateur Dinghy Club covered topics related to the Public Access to Information Act in Bermuda. The briefing emphasized the rights of Bermudians and residents to access public records, the role of the Information Commissioner in promoting
0 views • 51 slides
Enhancing Broadband Access in Educational Settings: E-Rate Program Initiatives
The 6th Report and Order from Fall 2010 outlines significant developments in the E-Rate Program, focusing on improving broadband access for schools and libraries. Key points include the eligibility of leased dark fiber, funding adjustments, and pilot programs for wireless access. The report undersco
0 views • 47 slides
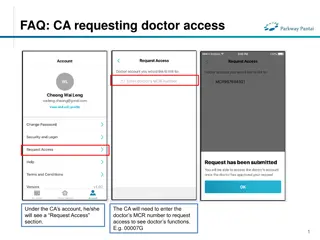
FAQs for Doctor and Clinical Assistant (CA) Account Access Management
Learn how CAs can request access to doctors' functions by entering the MCR number, how doctors can grant or remove CA access, and how CAs can manage access to multiple doctors. The process includes requesting, approving, and unlinking accounts, ensuring efficient and secure access management in a cl
0 views • 4 slides
EventsHQ Virtual Event Registration: User Access and Setup Guide
This comprehensive guide provides step-by-step instructions on setting up virtual event registration using EventsHQ. It covers how users can access event details, join the event, and includes best practices for sharing access links. Learn how to utilize the Virtual Event Details feature, send remind
1 views • 19 slides
Exploring Plate Tectonics and Earth's Structure for 5th Grade Science
Delve into the world of plate tectonics with a focus on Earth's layers, crust, mantle, and core. Understand how tectonic plates move and learn about continental drift and the concept of Pangea. Explore evidence of Pangea, sea floor spreading, and the fascinating geological processes that shape our p
0 views • 23 slides
Accessible Voting System for Californians with Disabilities
Learn about the Remote Accessible Vote-by-Mail System in California, designed to empower voters with disabilities to securely access, mark, and return their ballots from any computer with internet access. Find out who is eligible to use the system, how to access and return the ballot, and the steps
0 views • 23 slides
Dell Networking Solutions for BYOD and Guest Access Projects
Dell offers end-to-end solutions for Bring-Your-Own-Device (BYOD) and guest access projects, enabling secure employee access and controlled connectivity for visitors. The framework includes mobility business models, device security, network protection, and scalability. Dell supports customers in imp
0 views • 11 slides
Step-by-Step Guide to Using secure.colostate.edu NetConnect
Accessing secure.colostate.edu NetConnect is crucial for connecting securely to Colostate's network. Follow these steps: Use your web browser to login, allow Juniper Network installation, access Secure.Colostate.edu, connect behind the firewall, and utilize Pangea for file access. Obtain the Pangea
0 views • 8 slides
Role-based Access Control Policies and Security Properties Overview
This content provides an overview of Role-based Access Control (RBAC) policies, Administrative RBAC (ARBAC) systems, and security properties in the context of access control in large organizations. It discusses the implementation of RBAC in various software systems, the assignment and revocation of
0 views • 18 slides
Journey Through Earth's Formation and Evolution
Explore the origins of the Earth through the Big Bang Theory, Nebula Theory, Iron Catastrophe, and Formation of the Moon. Learn about Earth's layers, Pangea supercontinent, and the fascinating processes that shaped our planet over billions of years.
0 views • 7 slides
Open Access at Charles University: Opportunities and Challenges
Charles University is navigating the landscape of open access following the implementation of the Czech National Open Access Strategy. The university is working towards making all research articles and proceeding papers open access, monitoring article processing charges, and promoting open access as
0 views • 24 slides
Understanding Filesystem Security Principles and Access Control
Learn about filesystem security, general principles, discretionary access control (DAC), closed vs. open policy, closed policy with negative authorizations, and access control entries and lists. Discover how files and folders are managed, the role of access control lists (ACLs), and the different le
1 views • 56 slides
Journey Through Earth's Physical Geography: A Living Planet
Explore the intricate layers of the Earth, from the core made of iron and nickel to the diverse environments of the lithosphere, hydrosphere, atmosphere, and biosphere. Learn about continental drift and the formation of the supercontinent Pangea in this fascinating overview of our dynamic planet.
0 views • 7 slides
Understanding Ethernet and Multiple Access Protocols in Computer Networks
Exploring the fundamentals of Ethernet and multiple access protocols in computer networks, this content discusses the two primary categories of multiple access protocols - contention access and controlled access. It delves into topics such as CSMA/CD, LANs, performance of multiple access schemes, ad
0 views • 7 slides
Understanding Shared Memory, Distributed Memory, and Hybrid Distributed-Shared Memory
Shared memory systems allow multiple processors to access the same memory resources, with changes made by one processor visible to all others. This concept is categorized into Uniform Memory Access (UMA) and Non-Uniform Memory Access (NUMA) architectures. UMA provides equal access times to memory, w
0 views • 22 slides
Understanding Access Changes and Community Relations at Fermilab
Access to Fermilab has become more complicated due to changing DOE guidance and security posture. Efforts are being made to streamline access while addressing security gaps. Public access to outdoor areas of the Fermilab campus is still encouraged, but communication regarding access changes needs im
0 views • 12 slides
Understanding Computer System Protection and Security
Mechanisms like protection and security ensure controlled access to a computer system's resources and prevent malicious activities. Protection involves defining access control levels through models, policies, and mechanisms. Security focuses on user authentication to safeguard stored information. Di
0 views • 25 slides
Understanding Access to ITU Information and Documents
Exploring the concept of access in the work of a dedicated group, this content delves into the types of information that could or should be made available to the public, along with considerations on when access should be provided. It highlights the varying stages of information dissemination, discus
0 views • 8 slides
Harvard Chan School 2021 Yearly Access Review Process
The Harvard Chan School conducts its annual Yearly Access Review (YAR) process to review user access to various financial systems. The process involves assessing permissions, levels of access, and organizational details for each team member. Instructions are provided on reviewing worksheets, adding
0 views • 19 slides
Understanding Security Access in PeopleSoft Finance
Explore the various levels of security access in PeopleSoft Finance, from basic entry access to transaction entry, approvals, and procurement processes. Learn how to request individual and department security access and find relevant forms on the financial services website. Discover the different ty
0 views • 11 slides
Proxy Access to Medications Implementation Stages
This document outlines the implementation stages for proxy access to medications. It covers agreements with healthcare providers, prerequisites including compliance and data sharing agreements, and systems configuration for access to medical records. The stages include setting up access for care pro
0 views • 7 slides
CSUEB Academic Access Enhancement and Excellence Fee Proposal
The CSUEB Academic Access Enhancement and Excellence Fee Proposal aims to enhance the academic environment, reduce student costs, and provide equal access to educational materials. Components include an Academic Access Enhancement fund, e-textbooks program, and provision of tablets/netbooks to all i
0 views • 23 slides
Publishing Requirements and Challenges in Horizon Europe
The publication landscape under Horizon Europe presents challenges regarding compliance with publishing fee eligibility for hybrid journals and embargoes for open access. Hybrid journals feature subscription-based and open access parts, while open access journals require authors to pay open access f
0 views • 6 slides
Best Practices for Transradial Angiography and Intervention
This update highlights best practices for transradial angiography and intervention, including topics such as ultrasound guidance for transradial access, ulnar artery access recommendations, and future study opportunities. The importance of developing proficiency with ultrasound guidance, utilizing r
0 views • 15 slides
Evolution of Access Management in the 21st Century: RA21 Initiative
RA21, a joint initiative of STM Publishers and NISO, addresses the challenges of IP-based access management in the digital age. It aims to enhance user experience by optimizing access protocols across different stakeholder groups. The evolution from print to digital formats has led to the need for n
0 views • 12 slides