Virtualization Basics
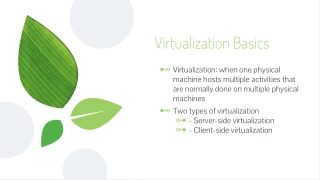
Virtualization and its two types: server-side virtualization, which provides virtual desktops for users, and client-side virtualization, which enables virtual environments for applications on personal computers.
0 views • 10 slides
Cloud Computing and Virtualization
Concepts of cloud computing and virtualization, how they enable efficient use of resources, and their advantages and disadvantages. Explore different types of cloud computing services like IaaS, PaaS, SaaS, and DaaS.
2 views • 14 slides
Modeling and Generation of Realistic Network Activity Using Non-Negative Matrix Factorization
The GHOST project focuses on the challenges of modeling, analyzing, and generating patterns of network activity. By utilizing Non-Negative Matrix Factorization (NMF), realistic network activity patterns can be created and injected into live wireless networks. Understanding and predicting user behavi
4 views • 28 slides
Understanding Isolation and Virtualization in Operating Systems
This text delves into the concepts of isolation and virtualization in operating systems. It covers topics such as virtual memory, virtual machines, containers, and kernel isolation mechanisms like chroot and cgroups. The discussion explores how these techniques provide isolation between processes, c
5 views • 20 slides
Exploring Virtual Machines and Operating Systems in Computer Architecture
Discover the history, benefits, and technologies of virtual machines, along with the implementation methods and hardware features supporting virtualization. Learn about different types of hypervisors and applications for virtualization, and delve into current research areas in virtualization technol
0 views • 49 slides
Understanding Memory Virtualization in Operating Systems
Memory virtualization in operating systems involves mapping guest addresses to host addresses with an added level of indirection managed by the hypervisor. Virtualization extensions in x86 processors enhance efficiency by allowing safe execution of guest code in Ring 0 through supervisor mode. The a
1 views • 28 slides
Network Compression Techniques: Overview and Practical Issues
Various network compression techniques such as network pruning, knowledge distillation, and parameter quantization are discussed in this content. The importance of pruning redundant weights and neurons in over-parameterized networks is highlighted. Practical issues like weight pruning and neuron pru
0 views • 37 slides
1V0-21.20: Associate VMware Data Center Virtualization | Sample Q & A
Click Here---> \/\/bit.ly\/3ShMwk9 <---Get complete detail on 1V0-21.20 exam guide to crack Data Center Virtualization. You can collect all information on 1V0-21.20 tutorial, practice test, books, study material, exam questions, and syllabus. Firm yo
0 views • 17 slides
Network Slicing with OAI 5G CN Workshop Overview
Overview of Network Slicing with OAI 5G CN workshop focusing on the crucial role of network slicing in realizing the service-oriented 5G vision. This workshop covers topics like multiple logical networks creation on shared infrastructure, different types of network slices, preparation and instantiat
1 views • 6 slides
Introduction to Virtualization: Concepts and Evolution
Virtualization allows running multiple operating systems on a single physical system, optimizing hardware usage and enhancing flexibility. It can be achieved through different architectures like Hosted and Bare-Metal, with examples including VMware and Xen. The history of virtualization traces back
0 views • 45 slides
Understanding Snort: An Open-Source Network Intrusion Detection System
Snort is an open-source Network Intrusion Detection System (NIDS) developed by Cisco, capable of analyzing network packets to identify suspicious activities. It can function as a packet sniffer, packet logger, or a full-fledged intrusion prevention system. By monitoring and matching network activity
0 views • 23 slides
Understanding Virtualization in Modern Systems
Virtualization plays a crucial role in modern systems by improving portability, security, and efficient resource utilization. Historical uses, examples like IBM VM/370, and benefits in cloud environments are discussed. The working of virtualization, including naive software interpreters and protecte
1 views • 18 slides
Hardware-Assisted Virtualization: VT-x Overview and Implementation
Explore the key concepts of hardware-assisted virtualization using Intel VT-x technology for CPU virtualization, VMX transitions, and VM control structures. Understand the motivation behind VT-x, CPU virtualization techniques, and the benefits of VT-x in simplifying VMM software. Dive into VMX opera
2 views • 28 slides
Green Computing and Virtualization Technologies in Environmental Conservation
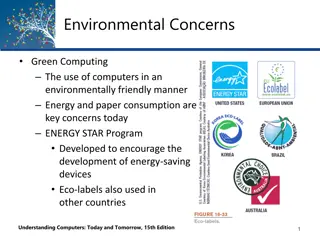
Green computing practices, such as the ENERGY STAR program and eco-labels, address energy and paper consumption concerns in an environmentally friendly way. Virtualization technology helps save money spent on energy, hardware, and maintenance while also benefiting the environment. Portable power dev
0 views • 5 slides
Understanding Market Trends for Storage Virtualization
NEC conducted research to analyze market trends and needs for storage virtualization, focusing on HYDRAstor advantages over competitors. Key findings include the preference for VMware vSphere, top challenges with current storage solutions, and recommendations to address concerns and highlight benefi
0 views • 24 slides
Optical SDN/NFV User Guide for Network Control & Management
Explore the comprehensive user guide for Optical Software-Defined Networking (SDN) and Network Functions Virtualization (NFV) at the University of Arizona. Learn about the SDN controller interfaces, network monitoring, traffic engineering databases, and more. Discover the capabilities of the Northbo
0 views • 13 slides
Transportation Network Modeling and Analysis with C.Coupled SE Platform
This content outlines the features and functionalities of the C.Coupled SE Platform (CSET Platform) developed by the Connetics Transportation Group. It covers aspects such as interface design, inputs merging, purposes, platform development using Cube, TAZs merging, and network attributes. The platfo
0 views • 11 slides
Zorua: A Holistic Resource Virtualization in GPUs Approach
This paper presents Zorua, a holistic resource virtualization framework for GPUs that aims to reduce the dependence on programmer-specific resource usage, enhance resource efficiency in optimized code, and improve programming ease and performance portability. It addresses key issues such as static a
0 views • 43 slides
Practical Implementation of Embedded Shadow Page Tables for Cross-ISA System Virtual Machines
This research focuses on the practical implementation and efficient management of embedded shadow page tables for cross-ISA system virtual machines. It discusses the framework, evaluation, and conclusions regarding system virtualization, particularly addressing memory virtualization overhead and opt
0 views • 33 slides
SQL Server Polybase: Data Virtualization Overview
Learn about SQL Server Polybase, a data virtualization feature that allows distributed query processing and data virtualization across various sources such as HDFS, Cosmos DB, and more. Discover how to use Polybase to build a data hub within SQL Server, enabling efficient query performance and analy
0 views • 20 slides
Meridian: An SDN Platform for Cloud Network Services
Meridian is an SDN platform developed by Mohammad Banikazemi, David Olshefski, Anees Shaikh, John Tracey, and GuohuiWang at IBM T. J. Watson Research Center. The platform focuses on providing cloud network services efficiently. It encompasses an architecture that enables faster and more convenient n
0 views • 21 slides
Multi-phase System Call Filtering for Container Security Enhancement
This tutorial discusses the importance of multi-phase system call filtering for reducing the attack surface of containers. It covers the benefits of containerization, OS virtualization, and the differences between OS and hardware virtualization. The tutorial emphasizes the need to reduce the kernel
0 views • 32 slides
Understanding Memory Management in Operating Systems
Dive into the core concepts of memory management in operating systems, covering address spaces, virtualization, processes and threads, memory multiplexing, binding of instructions and data, and multi-step program processing. Explore the importance of protection, isolation, sharing, and virtualizatio
0 views • 44 slides
Comprehensive Guide to Virtualization Infrastructure Administration
Explore the world of virtualization infrastructure administration, covering resources such as CPU, memory, storage, and network I/O. Learn about resource management, CPU scheduling, memory efficiency, and virtual memory management in virtualized environments. Dive into topics like vCPU mapping, prop
0 views • 10 slides
Networking Solutions for Server Virtualization Challenges
This presentation discusses the challenges server virtualization technologies bring to data center networks. It demonstrates a standards-based approach to enhance the experience and economics in a virtualized environment. Topics include market drivers, limitations of legacy networks, simplification
0 views • 33 slides
Maximizing Your Computer's Performance with Virtualization Software
Enhance your computer's capabilities by utilizing virtualization software like VirtualBox, VMWare, and Parallels to run virtual machines efficiently. Seamlessly operate multiple operating systems on a host OS, boost resource utilization, and achieve smooth file sharing and program installations. Div
0 views • 27 slides
Efficient Memory Virtualization: Reducing Dimensionality of Nested Page Walks
TLB misses in virtual machines can lead to high overheads with hardware-virtualized MMU. This paper proposes segmentation techniques to bypass paging and optimize memory virtualization, achieving near-native performance or better. Overheads of virtualizing memory are analyzed, highlighting the impac
0 views • 48 slides
Understanding Virtualization: Hardware Abstraction and Hypervisor Concepts
Dive into the world of virtualization with a focus on hardware abstraction and hypervisor technology. Explore the definitions and examples of hardware virtualization, hypervisors, and hardware abstraction, shedding light on how they enable multiple operating systems to coexist on a single physical m
0 views • 21 slides
Understanding Virtualization and System Virtualization in Operating Systems
Virtualization in operating systems plays a crucial role in creating virtual versions of resources like CPU, containers, and virtual machines. It involves techniques like isolating containers and utilizing hypervisors to manage hardware for system virtualization. Hypervisors come in different types,
0 views • 20 slides
Elastic Security Virtualization with vNIDS
Explore the concept of Elastic Security through Safe and Efficient Virtualization of Network Intrusion Detection Systems using vNIDS. This study delves into the challenges of traditional NIDSes, the requirements for virtualized environments, traffic volume variations, new trends in network function
0 views • 36 slides
Hardware-Assisted Page Walks for Virtualized Systems
Virtualization in cloud computing and server consolidation relies on hardware-assisted page walks for address translation in virtualized systems. This involves two-level address translations to ensure isolated address spaces for each virtual machine, utilizing multi-level page tables to manage memor
0 views • 32 slides
Comprehensive Guide to Virtualization Infrastructure Administration by Jakub Yaghob
Dive into the world of virtualization infrastructure administration with a focus on VMware vSphere and Microsoft Hyper-V. Explore courses, resources, feature comparisons, pricing details, and network setup in virtual laboratories. Understand the physical infrastructure applications, operating system
0 views • 14 slides
Understanding CPU Virtualization and System Virtualization
Virtualization involves creating virtual versions of systems, such as virtual memory and virtual machines, to optimize resources and support multiple operating systems. Hypervisors are essential for managing hardware and creating isolated environments. Different types of hypervisors exist, with the
0 views • 16 slides
Exploring Network Slicing in Future 5G Networks
The research delves into the design of a 5G-ready architecture known as NFV-based Network Store, aiming to serve as a digital distribution platform for 5G applications. By focusing on network slicing and programmability, the architecture enhances resource efficiency and agility in deploying software
0 views • 17 slides
Understanding Containers and Virtualization in Cloud Computing
Containers play a crucial role in virtualization by providing isolated environments for processes, addressing issues like dependency conflicts and system configurations. The concept is not new, with Windows NT kernel supporting various types of applications, including legacy Windows and DOS POSIX. M
0 views • 38 slides
Network Function Virtualization (NFV) Overview
Network Function Virtualization (NFV) focuses on virtualizing network functions to improve efficiency and reduce costs in network infrastructure. The lecture discusses key readings, devices that compose a network, specialization of devices, benefits of one-device-does-anything approach, and the goal
0 views • 21 slides
Enhancing Network Stability with Network Monitoring Systems
Network monitoring is crucial for efficient management and proactive issue detection in a network environment. Factors influencing an effective network system include choosing the best OEM, SLA agreements, and selecting a reliable System Integrator. Reactive monitoring can lead to financial losses a
0 views • 12 slides
Evolving Computer Communication and Networks: P2P Networking, Media Streaming, CDN
Delve into the continuously evolving landscape of computer communication and networks, focusing on P2P networking, media streaming, and CDN technologies. Explore topics such as overlays, P2P applications, multimedia streaming advancements, and the interplay between internet, data processing, and dis
0 views • 63 slides
Enhancing Cloud Profits with Parallels Dynamic Infrastructure and OpenStack
Parallels offers a dynamic infrastructure enabled for over 400 services, including APS, containers, hosted desktops, and automation for cloud profit. Their cloud server and storage solutions optimize virtual environments for high performance and scalability, while their virtualization technologies p
0 views • 13 slides
Understanding CPU Virtualization and Execution Control in Operating Systems
Explore the concepts of CPU virtualization, direct execution, and control mechanisms in operating systems illustrated through a series of descriptive images. Learn about efficient CPU virtualization techniques, managing restricted operations, system calls, and a limited direct execution protocol for
0 views • 18 slides