Apache MINA: High-performance Network Applications Framework
Apache MINA is a robust framework for building high-performance network applications. With features like non-blocking I/O, event-driven architecture, and enhanced scalability, MINA provides a reliable platform for developing multipurpose infrastructure and networked applications. Its strengths lie i
3 views • 13 slides
Modeling and Generation of Realistic Network Activity Using Non-Negative Matrix Factorization
The GHOST project focuses on the challenges of modeling, analyzing, and generating patterns of network activity. By utilizing Non-Negative Matrix Factorization (NMF), realistic network activity patterns can be created and injected into live wireless networks. Understanding and predicting user behavi
4 views • 28 slides
Automated Anomaly Detection Tool for Network Performance Optimization
Anomaly Detection Tool (ADT) aims to automate the detection of network degradation in a mobile communications network, reducing the time and effort required significantly. By utilizing statistical and machine learning models, ADT can generate anomaly reports efficiently across a large circle network
8 views • 7 slides
Deacon Formation Process in Diocese of Fort Worth Overview
This overview provides insights into the deacon formation and admissions process in the Diocese of Fort Worth. It emphasizes the importance of service, faith, and transformative journey in the formation process, along with stages such as initial inquiry, aspirant stage, candidate stage, ordination t
3 views • 27 slides
Evangelization and Faith Formation: Strengthening Catholic Men's Spiritual Journey
Explore the vital role of evangelization and faith formation in nurturing Catholic men's spirituality. Discover the essence of active relationship with God, ongoing formation in faith, life of prayer, and brotherhood. Learn about key elements like prayer, formation, and fraternity through initiative
1 views • 35 slides
Revolutionizing Network Management with Intent-Based Networking
Explore the concept and benefits of Intent-Based Networking (IBN) in simplifying network configuration and enhancing efficiency. Learn how IBN automates network operations, aligns with business objectives, improves security, and ensures scalability and reliability. Discover the potential of IBN tool
0 views • 14 slides
Formation of Hertwig's Epithelial Root Sheath in Tooth Development
The formation of Hertwig's Epithelial Root Sheath (HERS) is crucial in determining the shape, length, and number of roots in teeth. It initiates the formation of radicular dentin, marking the beginning of root development after enamel and dentin formation. HERS consists of outer and inner enamel epi
0 views • 29 slides
Network Compression Techniques: Overview and Practical Issues
Various network compression techniques such as network pruning, knowledge distillation, and parameter quantization are discussed in this content. The importance of pruning redundant weights and neurons in over-parameterized networks is highlighted. Practical issues like weight pruning and neuron pru
0 views • 37 slides
Evolution of the Ratio Formationis Generalis in Congregational Formation
Evolution and significance of the Ratio Formationis Generalis in Congregational Formation, from its historical development to the need for updates in response to changes in formation programs and Vatican documents. The formation of Units, Conferences, Directories, and Programs based on the Ratio, hi
4 views • 16 slides
Understanding Repair by Connective Tissue in Healing Processes
Healing or repair by connective tissue occurs in response to severe or chronic tissue injuries, leading to the replacement of nonregenerated cells with connective tissue or scar formation. This process involves the induction of fibroblast and endothelial cell proliferation, granulation tissue format
2 views • 26 slides
Major Formation Types of the World by Dr. Zaryab Khalid - BS Botany Semester 7
This presentation by Dr. Zaryab Khalid explores the major formation types of the world in the field of community ecology. It delves into the classification of natural and cultural vegetations, the concept of formation classes and subclasses, and details the six natural formation classes along with e
2 views • 7 slides
Root Development in Tooth Growth Process
Root formation plays a crucial role in the development of teeth, starting after enamel and dentin formation at the cementoenamel junction. Hertwig's epithelial root sheath (HERS) molds the shape of roots, initiating radicular dentin formation. The cervical loop forms an epithelial diaphragm, narrowi
0 views • 23 slides
Network Slicing with OAI 5G CN Workshop Overview
Overview of Network Slicing with OAI 5G CN workshop focusing on the crucial role of network slicing in realizing the service-oriented 5G vision. This workshop covers topics like multiple logical networks creation on shared infrastructure, different types of network slices, preparation and instantiat
1 views • 6 slides
Network Design Challenges and Solutions in Business Data Communications
Issues in designing a Local Area Network (LAN) include needs analysis, technological design, and cost assessment. The traditional approach involves structured systems analysis, but faces challenges due to rapidly changing technology and increasing network traffic. The Building Blocks Approach recomm
1 views • 20 slides
Understanding 5G RAN Network Slicing and Architecture
Explore the intricate world of 5G Radio Access Network (RAN) and Network Slicing, delving into concepts such as SO Service Orchestrator, SDN-C Service Design, and Core Network Elements. Discover the significance of managing and designing mobile slice services, including eMBB, Massive IoT, and Missio
0 views • 26 slides
Understanding Snort: An Open-Source Network Intrusion Detection System
Snort is an open-source Network Intrusion Detection System (NIDS) developed by Cisco, capable of analyzing network packets to identify suspicious activities. It can function as a packet sniffer, packet logger, or a full-fledged intrusion prevention system. By monitoring and matching network activity
0 views • 23 slides
Data Flows and Network Challenges in Particle Physics Infrastructure
This overview delves into the data flows and network challenges faced in particle physics infrastructure, focusing on the JUNO project. It discusses the process of data reception, storage, and replication across various data centers, highlighting the bidirectional nature of data flows. Additionally,
0 views • 24 slides
Progress of Network Architecture Work in FG IMT-2020
In the Network Architecture Group led by Namseok Ko, significant progress has been made in defining the IMT-2020 architecture. The work has involved gap analysis, draft recommendations, and setting framework and requirements. Phase 1 focused on identifying 19 architectural gaps, such as demands for
1 views • 11 slides
Understanding Rocks: Types, Formation, and Properties
Rocks can be classified as metamorphic, igneous, or sedimentary based on their formation processes. Florida's phosphate deposits and pumice formation showcase the diversity of rocks. A scientist's rock cycle model helps predict changes, while pressure on sediments leads to new rock formation. Basalt
1 views • 22 slides
Challenges and Perspectives in Catholic Board Formation
Exploring the essential aspects of board formation in Catholic educational institutions, this content delves into models of formation, institutional needs, perspectives on faith formation, questions for reflection, governance from a mission perspective, and the significance of undertaking board form
1 views • 24 slides
Understanding Interconnection Networks Topology
Exploring the topology of interconnection networks helps determine the arrangement of channels and nodes, impacting network cost, performance, latency, energy consumption, and complexity of implementation. Abstract metrics such as degree, hop count, and network diameter play crucial roles in evaluat
1 views • 56 slides
Transportation Network Modeling and Analysis with C.Coupled SE Platform
This content outlines the features and functionalities of the C.Coupled SE Platform (CSET Platform) developed by the Connetics Transportation Group. It covers aspects such as interface design, inputs merging, purposes, platform development using Cube, TAZs merging, and network attributes. The platfo
0 views • 11 slides
Human Disease Symptom Network: Understanding Disease Relationships Through Symptoms and Genes
The Human Disease Symptom Network (HSDN) is constructed using a large-scale medical bibliographic records database to form a network of human diseases based on symptom similarities. By integrating disease-gene associations and protein-protein interaction data, correlations between symptom similarity
0 views • 37 slides
Introduction to Network Analysis Using .NET
This presentation introduces the concept of network analysis using .NET in the humanities classroom. It provides a template for teaching and adapting network analysis tools for educational purposes. The guide explains the relevance of networks in processing and visualizing data, emphasizing the coll
0 views • 20 slides
Evolution of Compact Star-Forming Galaxies and Quiescent Galaxies
The evolution of galaxies from compact star-forming to quiescent states involves processes such as secular evolution, gas inflows, and star formation quenching. By studying the structural relations and star formation in these galaxies, insights are gained into their transition towards quiescence. Th
0 views • 12 slides
Tactical Formation Maneuvering for T-44C Aircraft
This presentation provides essential knowledge for conducting tactical formation flights in the T-44C aircraft, covering formation types, fundamentals, maneuvers, and division formations. It outlines the importance of formation unity, maneuverability, and coordination, along with considerations like
0 views • 41 slides
Meridian: An SDN Platform for Cloud Network Services
Meridian is an SDN platform developed by Mohammad Banikazemi, David Olshefski, Anees Shaikh, John Tracey, and GuohuiWang at IBM T. J. Watson Research Center. The platform focuses on providing cloud network services efficiently. It encompasses an architecture that enables faster and more convenient n
0 views • 21 slides
Enhancing Network Security with Software-Defined Snort and OpenFlow
Explore the implementation of Snort, Barnyard, and PulledPork within a Software-Defined Network framework using OpenFlow technology. Learn how these tools enhance network security through intrusion detection engines, rule management, and network traffic control mechanisms. Dive into the architecture
0 views • 15 slides
Understanding Network Metrics Through Centrality Analysis
This presentation introduces network metrics as tools to describe network characteristics and answer important questions. Using centrality metrics as an example, participants learn how to identify the most important nodes in a network based on different criteria such as degree centrality and closene
0 views • 15 slides
Implications of Star Formation in the Central Parsec of Our Galaxy with Subaru Observations
Researchers presented implications of star formation in the central parsec of our Galaxy using Subaru observations at the 2014 Subaru Users Meeting. The study focused on the supermassive black hole Sgr A* and the challenges posed by conditions in the Galactic Center for star formation. Various scena
0 views • 30 slides
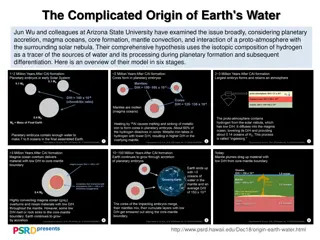
The Complicated Formation of Earth's Water: A Detailed Overview
Jun Wu and colleagues at Arizona State University have developed a comprehensive model to explain the origin of Earth's water through stages such as planetary accretion, core formation, and interactions with the solar nebula. By tracing the isotopic composition of hydrogen, they explore how water so
0 views • 7 slides
Understanding Network Analysis: Whole Networks vs. Ego Networks
Explore the differences between Whole Networks and Ego Networks in social network analysis. Whole Networks provide comprehensive information about all nodes and links, enabling the computation of network-level statistics. On the other hand, Ego Networks focus on a sample of nodes, limiting the abili
0 views • 31 slides
Understanding Exponential Random Graph Models (ERGMs) in Social Network Analysis
Exponential Random Graph Models (ERGMs) play a crucial role in predicting network ties in social networks by accounting for network dependence and incorporating both exogenous and endogenous variables. These models allow for testing multiple theories and competitive explanations for network formatio
0 views • 66 slides
Understanding Network Interference in CS590B/690B Lecture
Delve into the realm of network interference through the CS590B/690B lecture with Phillipa Gill at UMass Amherst. Explore topics such as Internet routing, timing attacks, BGP hijacks, Tor network functionality, relay selection, collusion scenarios, use of guards, web site fingerprinting attacks, tra
0 views • 11 slides
Contribution of HALA Network to ATM Community and SESAR 2020: Achievements and Future Directions
HALA network has been instrumental in fostering research and innovation in the field of automation for ATM systems, providing a platform for knowledge dissemination, collaboration, and advancement. The network has facilitated exploratory research, encouraged young scientists' participation, and crea
0 views • 12 slides
Network Function Virtualization (NFV) Overview
Network Function Virtualization (NFV) focuses on virtualizing network functions to improve efficiency and reduce costs in network infrastructure. The lecture discusses key readings, devices that compose a network, specialization of devices, benefits of one-device-does-anything approach, and the goal
0 views • 21 slides
Enhancing Network Stability with Network Monitoring Systems
Network monitoring is crucial for efficient management and proactive issue detection in a network environment. Factors influencing an effective network system include choosing the best OEM, SLA agreements, and selecting a reliable System Integrator. Reactive monitoring can lead to financial losses a
0 views • 12 slides
Understanding Standard Molar Enthalpies of Formation
Formation reactions involve substances being created from elements in their standard states, with the enthalpy change known as the standard molar enthalpy of formation (Hf). This enthalpy represents the energy released or absorbed when one mole of a compound is formed from its elements in their stan
0 views • 13 slides
Accelerating Systemic Change Network Inaugural Workshop Summary
The Accelerating Systemic Change Network held its inaugural workshop at Howard Hughes Medical Institute in July 2016 to address the lack of coordination in improving higher education. With a vision to become a professional hub for change researchers in STEM education, the network aims to enhance ind
0 views • 5 slides
University Network Section Overview July 2015 - March 2016
The presentation covers the network team structure, team members, objectives, goals, report outline, network statistics, accomplishments, and future plans of the university network section from July 2015 to March 2016. It highlights efforts to provide stable internet and intranet services, restructu
0 views • 16 slides