Apache MINA: High-performance Network Applications Framework
Apache MINA is a robust framework for building high-performance network applications. With features like non-blocking I/O, event-driven architecture, and enhanced scalability, MINA provides a reliable platform for developing multipurpose infrastructure and networked applications. Its strengths lie i
3 views • 13 slides
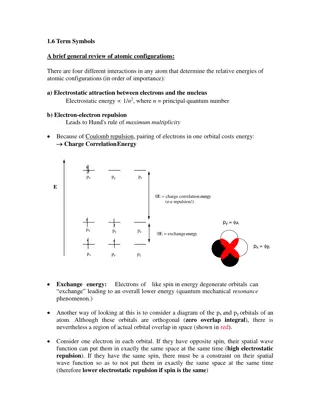
Understanding Atomic Configurations and Term Symbols
The energy of atomic configurations is determined by electrostatic attraction between electrons and the nucleus, electron-electron repulsion, spin-orbit coupling, and spin-spin interactions. Term symbols in electronic spectroscopy specify atomic states using quantum numbers. Hund's rule and the Paul
8 views • 12 slides
Modeling and Generation of Realistic Network Activity Using Non-Negative Matrix Factorization
The GHOST project focuses on the challenges of modeling, analyzing, and generating patterns of network activity. By utilizing Non-Negative Matrix Factorization (NMF), realistic network activity patterns can be created and injected into live wireless networks. Understanding and predicting user behavi
4 views • 28 slides
Automated Anomaly Detection Tool for Network Performance Optimization
Anomaly Detection Tool (ADT) aims to automate the detection of network degradation in a mobile communications network, reducing the time and effort required significantly. By utilizing statistical and machine learning models, ADT can generate anomaly reports efficiently across a large circle network
8 views • 7 slides
Revolutionizing Network Management with Intent-Based Networking
Explore the concept and benefits of Intent-Based Networking (IBN) in simplifying network configuration and enhancing efficiency. Learn how IBN automates network operations, aligns with business objectives, improves security, and ensures scalability and reliability. Discover the potential of IBN tool
0 views • 14 slides
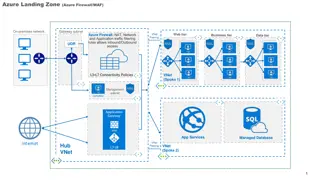
Azure Network Architecture Deployment Overview
An in-depth look at Azure network architectures, including landing zone configurations with Azure Firewall and WAF, deployment to primary Azure regions, hub and spoke models, network virtual appliances (NVAs), VPN tunnels, DMZ setups, and more. This comprehensive guide covers various network compone
3 views • 7 slides
Network Compression Techniques: Overview and Practical Issues
Various network compression techniques such as network pruning, knowledge distillation, and parameter quantization are discussed in this content. The importance of pruning redundant weights and neurons in over-parameterized networks is highlighted. Practical issues like weight pruning and neuron pru
0 views • 37 slides
Network Slicing with OAI 5G CN Workshop Overview
Overview of Network Slicing with OAI 5G CN workshop focusing on the crucial role of network slicing in realizing the service-oriented 5G vision. This workshop covers topics like multiple logical networks creation on shared infrastructure, different types of network slices, preparation and instantiat
1 views • 6 slides
Network Design Challenges and Solutions in Business Data Communications
Issues in designing a Local Area Network (LAN) include needs analysis, technological design, and cost assessment. The traditional approach involves structured systems analysis, but faces challenges due to rapidly changing technology and increasing network traffic. The Building Blocks Approach recomm
1 views • 20 slides
Discussion on Multi-PUSCH Configuration for UTO-UCI Content Moderator at Ericsson
This discussion encompasses the configuration and implications of the Multi-PUSCH setup based on agreed parameters within the UTO-UCI content moderation context at Ericsson. It delves into varying configurations, potential impacts, and considerations for effective utilization. The slides provide ins
0 views • 17 slides
Understanding 5G RAN Network Slicing and Architecture
Explore the intricate world of 5G Radio Access Network (RAN) and Network Slicing, delving into concepts such as SO Service Orchestrator, SDN-C Service Design, and Core Network Elements. Discover the significance of managing and designing mobile slice services, including eMBB, Massive IoT, and Missio
0 views • 26 slides
Understanding Snort: An Open-Source Network Intrusion Detection System
Snort is an open-source Network Intrusion Detection System (NIDS) developed by Cisco, capable of analyzing network packets to identify suspicious activities. It can function as a packet sniffer, packet logger, or a full-fledged intrusion prevention system. By monitoring and matching network activity
0 views • 23 slides
Electronic Meeting Agenda: UE PC2 for NR Inter-Band CA and SUL Configurations
The document relates to the upcoming electronic meeting of 3GPP TSG-RAN WG4, focusing on UE power class 2 for NR inter-band Carrier Aggregation and supplemental uplink configurations. It includes background contributions, identified issues, and options for SAR schemes addressing duty cycle based sol
5 views • 5 slides
Data Flows and Network Challenges in Particle Physics Infrastructure
This overview delves into the data flows and network challenges faced in particle physics infrastructure, focusing on the JUNO project. It discusses the process of data reception, storage, and replication across various data centers, highlighting the bidirectional nature of data flows. Additionally,
0 views • 24 slides
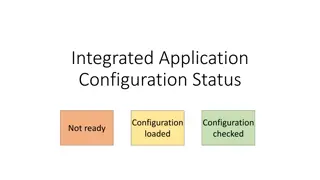
Configurations and Tests Overview in Integrated Applications
This content provides an overview of various configurations and tests in integrated applications, covering aspects such as status, loaded configurations, readiness checks, server tests for HV and LV systems, as well as client-server interactions. It details the different components involved and thei
0 views • 5 slides
Emerging Trends in Network Design and Verification
Explore the evolution of network design from manual configurations to custom networks and software-defined solutions. Discover the challenges facing current networks and the potential for optimizing network performance through innovative approaches like P4 and SDNs. Delve into the intersection of di
0 views • 45 slides
Abstracting Queues in the UApi for Improved Network Performance
Abstracting queues in the UApi is crucial for enabling more efficient traffic steering and management in network devices. The proposal aims to enhance the handling of queues by hiding or exposing them to user space, allowing for better scalability and flexibility in network configurations.
4 views • 8 slides
Understanding Static Routing in Network Infrastructure Workshops
Explore the concepts of static routing in networking workshops, covering Unix and Cisco network interface configurations, static routes, default routes, and advantages and disadvantages of static routing. Learn about IP routing configuration, assignment of IPv4 addresses, and FreeBSD network interfa
4 views • 37 slides
Transportation Network Modeling and Analysis with C.Coupled SE Platform
This content outlines the features and functionalities of the C.Coupled SE Platform (CSET Platform) developed by the Connetics Transportation Group. It covers aspects such as interface design, inputs merging, purposes, platform development using Cube, TAZs merging, and network attributes. The platfo
0 views • 11 slides
Understanding Horizontal and Backbone Cabling in Network Architecture
Explore the fundamentals of horizontal and backbone cabling in network architecture. Learn about their segments, configurations, and types. Discover how horizontal cabling connects devices to outlets and back to the telecommunications room, while backbone cabling links multiple buildings or sections
2 views • 18 slides
Hardware Configurations for Project Cysera by Zoebir Bong
This document outlines proposed hardware configurations for Project Cysera drafted by Zoebir Bong. It includes options from Dell and Lenovo servers with both remote and local data storage solutions. Each configuration specifies server models, network switches, processors, memory, storage drives, net
0 views • 8 slides
Comparison of New and Old Cave Configurations in Neutron Ball Testing
This content discusses the comparison between the new and old cave configurations in the Neutron Ball testing part II. It showcases images and descriptions of the different cave configurations, highlighting the progress in research at the Cyclotron Institute. The Neutron Ball's functionality and tes
0 views • 14 slides
Meridian: An SDN Platform for Cloud Network Services
Meridian is an SDN platform developed by Mohammad Banikazemi, David Olshefski, Anees Shaikh, John Tracey, and GuohuiWang at IBM T. J. Watson Research Center. The platform focuses on providing cloud network services efficiently. It encompasses an architecture that enables faster and more convenient n
0 views • 21 slides
Fundamentals of Computer Networks
Explore the essentials of computer networks, covering topics such as DHCP, NAT, IPv6, server operations, and IP address allocation. Understand how DHCP servers control IP address pools and provide network configurations to clients. Learn about address leases for dynamic allocation and how DHCP clien
0 views • 35 slides
Understanding Electron Configurations and the Periodic Table in Chemistry
Explore the world of electron configurations in atoms, subshells, and electron arrangement using the periodic table. Learn about the organization of electrons in subshells, different ways to represent electron arrangements, and how to determine electron configurations based on the periodic table. Di
0 views • 12 slides
Nonstationary Configurations of a Spherically Symmetric Scalar Field
Action and stress-energy tensor, Einstein-Klein-Gordon equations, and method for constructing nonstationary configurations of a spherically symmetric scalar field are discussed in this study. The behavior of the characteristic function allows interpretations such as black holes, wormholes, or naked
0 views • 14 slides
Understanding Network Analysis: Whole Networks vs. Ego Networks
Explore the differences between Whole Networks and Ego Networks in social network analysis. Whole Networks provide comprehensive information about all nodes and links, enabling the computation of network-level statistics. On the other hand, Ego Networks focus on a sample of nodes, limiting the abili
0 views • 31 slides
Overview of Magnet Configurations at GSI Helmholtzzentrum GmbH
This document provides detailed information on the magnet configurations at GSI Helmholtzzentrum GmbH, focusing on multiplet designs, magnetic field simulations, quadrupoles, sextupoles, and steering dipoles. It covers the general design of SC multiplets, requirements on axis and angles, and specifi
2 views • 17 slides
Understanding Network Security Vulnerabilities and Attacks
Explore the world of network security vulnerabilities and attacks, including Denial-of-Service (DoS) and Distributed-Denial-of-Service (D-DoS), security flaws in the TCP/IP protocol suite, ICMP attacks, routing attacks, and TCP attacks. Learn about common security vulnerabilities such as address spo
0 views • 36 slides
Understanding Electronic Configurations Through Simplified Assignments
Exploring electron configurations and orbital regions using simplified notations colored in on Periodic Charts. Descriptions and visual aids for Carbon, Fluorine, and excited state of Fluorine. Learn to assign s, p, d, and f electron neighborhoods without memorization through a fun song. Includes te
0 views • 14 slides
Maximizing Network Performance: Tips and Considerations
Learn how to troubleshoot network performance issues effectively by understanding user expectations, tuning host specifications, optimizing PCI configurations, managing storage subsystem factors, and other critical considerations for enhancing network performance.
0 views • 25 slides
MOIMS Protocol Viewpoint for SEA Reference Architecture Updates
This content describes the MOIMS Protocol Viewpoint inputs to the SEA Reference Architecture updates by Roger Thompson from ESA SAWG. It includes details about the graphical conventions, data store elements, organizational domains, network layers, communications protocols, and space communications c
0 views • 21 slides
Network Function Virtualization (NFV) Overview
Network Function Virtualization (NFV) focuses on virtualizing network functions to improve efficiency and reduce costs in network infrastructure. The lecture discusses key readings, devices that compose a network, specialization of devices, benefits of one-device-does-anything approach, and the goal
0 views • 21 slides
Enhancing Network Stability with Network Monitoring Systems
Network monitoring is crucial for efficient management and proactive issue detection in a network environment. Factors influencing an effective network system include choosing the best OEM, SLA agreements, and selecting a reliable System Integrator. Reactive monitoring can lead to financial losses a
0 views • 12 slides
Local Network and File Sharing Workshop Overview
Exploring the concepts of local area networks (LANs), intranets, and practical aspects of sharing files and printers on a network. The workshop delves into the structure of the University of Alkafeel network, including hotspot settings and ad hoc network configurations. Learn about USB printer shari
0 views • 30 slides
DC Motor Control Techniques and Configurations
This chapter delves into various aspects of PWM and DC motor control, exploring characteristics of selected DC motors, rotation mechanisms, H-bridge configurations for motor direction control, logic configurations for motor operation, bidirectional motor control using an L298 chip, pulse width modul
0 views • 27 slides
Traffic Routing and Game Theory in Network Design
Explore the intersection of traffic routing and game theory in network design scenarios. Delve into concepts like Atomic Congestion Games, Potential Function, Price of Anarchy and Stability, Nash Equilibrium, Braess's Paradox, and the pursuit of Pure Strategy Nash Equilibriums in traffic routing gam
0 views • 16 slides
Network Configuration Complexity and Verification Tools
The content discusses the challenges of managing complex router configurations involving multiple routing protocols, metrics, and filters. It highlights the importance of using network verification tools to proactively detect errors and policy violations. Various tools such as Tiramisu, Minesweeper,
0 views • 26 slides
Accelerating Systemic Change Network Inaugural Workshop Summary
The Accelerating Systemic Change Network held its inaugural workshop at Howard Hughes Medical Institute in July 2016 to address the lack of coordination in improving higher education. With a vision to become a professional hub for change researchers in STEM education, the network aims to enhance ind
0 views • 5 slides
University Network Section Overview July 2015 - March 2016
The presentation covers the network team structure, team members, objectives, goals, report outline, network statistics, accomplishments, and future plans of the university network section from July 2015 to March 2016. It highlights efforts to provide stable internet and intranet services, restructu
0 views • 16 slides