Understanding Malicious Attacks, Threats, and Vulnerabilities in IT Security
Malicious attacks, threats, and vulnerabilities in IT systems pose significant risks and damages. This chapter explores the types of attacks, tools used, security breaches, and measures to protect against cyber threats. Learn how security professionals safeguard organizations from malicious attacks
0 views • 24 slides
Understanding Typosquatting in Language-Based Package Ecosystems
Typosquatting in language-based package ecosystems refers to the malicious practice of registering domain names that are similar to popular packages or libraries with the intention of tricking developers into downloading malware or compromised software. This threat vector is a serious issue as it ca
0 views • 23 slides
Understanding Half-Life in Physics
Half-life is a key concept in physics, particularly in radioactive decay. It is the time taken for the activity of a radioactive source to decrease to half of its original value. This can be determined experimentally through measuring counts per minute and graphing the data. Additionally, half-life
2 views • 11 slides
Influence of Solar Activity and Orbital Motion on Terrestrial Atmosphere
Solar magnetic field reversal, wavelet spectral analysis, and proxies for solar activity index are discussed in relation to the joint effects of solar activity and solar orbital motion on the Earth's atmosphere. The study highlights the impact of solar cycles on terrestrial climate dynamics and temp
6 views • 16 slides
Modeling and Generation of Realistic Network Activity Using Non-Negative Matrix Factorization
The GHOST project focuses on the challenges of modeling, analyzing, and generating patterns of network activity. By utilizing Non-Negative Matrix Factorization (NMF), realistic network activity patterns can be created and injected into live wireless networks. Understanding and predicting user behavi
4 views • 28 slides
Understanding Activity, Pay, and Special Codes in API Terminology
Dive into the terminology surrounding Activity Codes, Pay Codes, and Special Codes within the realm of APIs. Explore how these codes represent different aspects of scheduling, productivity, and payroll management. Gain insights into the distinctions between Activity Codes and Pay Codes, their implic
5 views • 8 slides
Exploring the Health Benefits of Exercise and Physical Activity at www.aber.ac.uk/ibers/
Delve into the relationship between physical activity, fitness, and mortality through insightful studies such as the Harvard Alumni Health Study and research by Paffenbarger et al. Discover the impact of exercise on reducing the risk of dying and improving overall health. Explore early work in sport
0 views • 12 slides
Understanding Density of Materials Activity
Density is defined as the mass per unit volume of a material. In this activity, students learn to measure and calculate the density of solid objects or liquids using the density equation. They also explore the concept of density through practical examples and self-assessment tasks. Additionally, the
0 views • 16 slides
Understanding Water Activity and Mass Transfer in Food Engineering
Water activity (aw) plays a crucial role in microbial activity, chemical and physical changes in foods, and the dehydration process. Maintaining water activity below specific levels can prevent microbiological spoilage and deterioration reactions, while also affecting texture, aroma, and overall qua
0 views • 11 slides
Interactive Mystery Chart Activity for Math Classroom
Engage your students with an interactive mystery chart activity to enhance their math skills. Utilize various sets of slides based on your class's needs, including options for distance learning. Use clues to deduce the number of dice in a glass, fostering estimation skills and logical thinking. The
0 views • 19 slides
Gel Electrophoresis DNA Extension Activity in Modern Biology Lab
This lab activity uses agarose gel electrophoresis to determine the length of an unknown DNA fragment by comparing it to known DNA fragment lengths. The process involves gel preparation, loading samples, electrophoresis, staining, de-staining, and measurement of DNA bands. The activity was produced
0 views • 7 slides
Interactive Football Top Trumps Game Activity for Year 3 Students
Engage Year 3 students in a fun and educational activity centered around designing and playing Top Trumps cards featuring famous footballers from Euro 2016. Students will research player statistics, create cards, establish rules, and play the game with classmates to enhance literacy and numeracy ski
0 views • 7 slides
Factors Affecting Enzyme Activity and Catalysis
Enzyme activity is influenced by various factors such as enzyme concentration, temperature, pH, substrate concentration, inhibitors, activators, and physical agents. The rate of enzyme-catalyzed reactions is directly proportional to enzyme concentration, and temperature plays a significant role with
0 views • 23 slides
Understanding Peroxidase Enzyme Activity in Biological Samples
Demonstrating the enzyme activity of peroxidase, an enzyme that plays a crucial role in breaking down hydrogen peroxide in various organisms. Learn about the differences between peroxidase and catalase, the calculation of enzyme activity, and the significance of extinction coefficient in enzyme assa
0 views • 8 slides
Understanding Article 6.2 Activity Cycle in Paris Agreement
Exploring the operationalization of Article 6.2 of the Paris Agreement through a private training series, this program focuses on capacity building for implementation and covers key aspects like the activity cycle, authorization processes, roles of governments, and project-level requirements. It del
0 views • 29 slides
Investigating Amylase Activity in Starch Digestion
An investigation on amylase activity involving the digestion of starch was conducted, with methods for controlling temperature, calculating digestion rates, and improving data precision discussed. The effects of temperature on enzymatic activity and precision enhancement techniques were explored.
0 views • 47 slides
Supporting Healthy Aging Through Physical Activity: Workshop Highlights
Explore the insights from an online workshop focusing on supporting healthy aging through physical activity for older adults. The workshop covers topics such as increasing awareness of the importance of physical activity, incorporating activities into daily routines, setting goals, and sustaining pr
0 views • 23 slides
Efficient Malicious URL Detection with Bloom Filters
Google's Chrome team faces the challenge of detecting malicious URLs without heavy memory usage. Universal hashing and Bloom Filters are discussed as innovative solutions to address this issue efficiently and effectively, illustrating how K-independent hash functions can improve detection accuracy w
0 views • 19 slides
Exploring the Malicious Use of Artificial Intelligence and its Security Risks
Delve into the realm of artificial intelligence and uncover the potential risks associated with its malicious applications, including AI safety concerns and security vulnerabilities. Discover common threat factors and security domains that play a vital role in combating these challenges.
0 views • 30 slides
Understanding Typosquatting in Language-Based Package Ecosystems
Typosquatting in language-based package ecosystems involves malicious actors registering similar-sounding domain names to legitimate ones to deceive users into downloading malware or visiting malicious sites. This practice poses a significant threat as users may unknowingly install compromised packa
0 views • 23 slides
Understanding Malicious Software and Its Impact on Computer Systems
Malicious software, commonly known as malware, poses a serious threat to computer systems by exploiting vulnerabilities. This content covers various terminologies, categories, and types of malware, including viruses, worms, rootkits, spyware, and adware. It also delves into how malware can cause dam
0 views • 16 slides
Investigating Computational Intelligence: Reading What Machines Think at University of Rome Tor Vergata
Researchers at University of Rome Tor Vergata are delving into the intriguing realm of understanding and predicting human brain activity by observing cognitive tasks using computational machines. Their motivation lies in bridging the complexity of computers with the mysteries of the human brain, aim
0 views • 20 slides
Adherence to 2008 Physical Activity Guidelines & Mortality Study
This study explores the association between adherence to the 2008 Physical Activity Guidelines for Americans and all-cause mortality. It analyzes data from the NHIS and NDI to assess the risks associated with aerobic and muscle-strengthening activities. The primary objective is to evaluate mortality
0 views • 29 slides
DNS Forensics & Protection: Analyzing and Securing Network Traffic
DNS Forensics involves using DNS traffic to analyze network health, detect anomalous behavior, and combat malicious activities. By understanding DNS activity on systems and implementing defense strategies, users and network providers can enhance security and privacy.
0 views • 16 slides
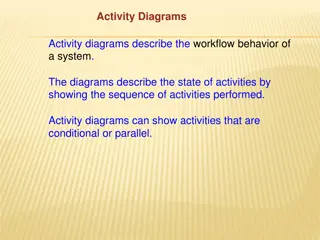
Understanding Activity Diagrams and State Chart Diagrams
Activity diagrams describe the workflow behavior of a system by showing the sequence of activities performed, including conditional and parallel activities. Elements such as Initial Activity, Symbol Activity, Decisions, Signals, Concurrent Activities, and Final Activity are depicted in these diagram
0 views • 10 slides
The Evolution of Cheerleading: From Yelling to Intense Physical Activity
Cheerleading ranges from yelling to intense physical activity, incorporating tumbling, dance, jumps, cheers, and stunting to motivate sports teams and entertain audiences. Originating in the United States, it has evolved from an all-male activity to a predominantly female sport with some co-ed teams
0 views • 9 slides
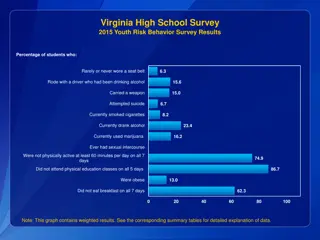
Virginia High School Survey 2015 Youth Risk Behavior Results
The Virginia High School Survey 2015 presented data on various risky behaviors among students, including seat belt usage, alcohol and drug consumption, weapon carrying, suicide attempts, physical activity, sexual activity, and more. The results are divided into percentages of students engaging in th
0 views • 4 slides
Interim Report of Harefield DCD Heart Transplant Programme Clinical Activity
The interim report highlights the clinical activity of the Harefield DCD Heart Transplant Programme, showcasing the feasibility of DCD heart transplantation using various methods. The report discusses donor/recipient risk profiles, feedback from medical teams, and the potential impact on national tr
0 views • 7 slides
Detecting Drive-By Attacks: Analysis of Malicious Javascript in Big Data Environments
Cybersecurity researcher Andrei Bozeanu delves into the complex world of polymorphic viruses, heuristic analysis, and the similarities between polymorphic viruses and malicious Javascript. Discover how these threats operate and evade detection, highlighting the importance of understanding malware be
0 views • 48 slides
Understanding Malware: Types, Symptoms, and Countermeasures
Malware is malicious software that can alter computer settings, behavior, files, services, ports, and speed. Sources of malware include insufficient security, honeypot websites, free downloads, torrents, pop-ups, emails, and infected media. Symptoms of malware include unusual computer behavior, slow
0 views • 9 slides
Advances in Authenticated Garbling for Secure 2PC
The research discusses advancements in authenticated garbling for achieving constant-round malicious secure 2PC using garbled circuits. It emphasizes the utilization of correlated randomness setup and efficient LPN-style assumptions to enhance communication efficiency significantly. Various techniqu
0 views • 30 slides
Understanding Factors Affecting Enzyme Activity in Biochemistry
Enzyme assays measure substrate conversion to product under varying conditions like cofactors, pH, and temperature. Enzyme velocity represents the rate of a catalyzed reaction, typically reported as V0. Enzyme activity is expressed as mol of substrate transformed per minute, with enzyme unit and kat
0 views • 18 slides
Understanding Malicious Software in Computer Security
In "Computer Security: Principles and Practice," the chapter on Malicious Software covers various types of malware such as viruses, adware, worms, and rootkits. It defines malware, Trojan horses, and other related terms like backdoors, keyloggers, and spyware. The chapter also discusses advanced thr
0 views • 49 slides
Understanding Malicious Software in Data Security
Malicious software, or malware, poses a threat to the confidentiality, integrity, and availability of data within systems. It can be parasitic or independent, with examples like viruses, worms, Trojan horses, and e-mail viruses. Understanding the different types of malware and their modes of operati
0 views • 5 slides
Buffer Overflow Attack and Vulnerable Programs
Understanding buffer overflow attacks and vulnerable programs, the consequences of such attacks, how to run malicious code, and the setup required for exploiting vulnerabilities in program memory stack layouts. Learn about creating malicious inputs (bad files), finding offsets, and addressing shellc
0 views • 36 slides
Exploring Java Sandbox Flexibility and Usage
The research delves into evaluating the flexibility and practical usage of the Java sandbox in dealing with Java applications. It highlights the importance of investigating how security tools are utilized, aiming to enhance security mechanisms and differentiate between malicious and benign code. The
0 views • 28 slides
Understanding Malware: Types, Risks, and Prevention
Malware, short for malicious software, is designed to disrupt, damage, or gain unauthorized access to computer systems. Malware includes viruses, worms, trojans, ransomware, adware, spyware, rootkits, keyloggers, and more. They can be spread through various means like malicious links, untrusted down
0 views • 15 slides
Understanding Malicious Software: Classification and Payload Actions
Malicious software, or malware, can be broadly classified based on how it spreads and the actions it performs once on a target system. This classification includes distinctions between viruses, worms, trojans, botnets, and blended attacks. The payload actions of malware can range from file corruptio
0 views • 44 slides
Activity Leader Guidelines for Volunteers
Welcome to the role of a leader, driver, or bus captain! As a leader, it is essential to familiarize yourself with the provided leader packets, understand the details of the activity, and prioritize safety. Taking pride in being a leader, owning the activity before the event, ensuring your packet is
0 views • 25 slides
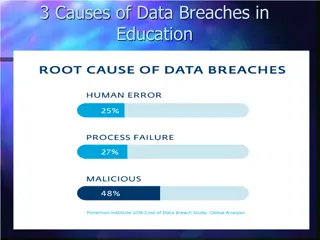
Understanding Data Breach Causes in Education
Data breaches in education are often caused by human errors, process failures, and malicious breaches. Human errors include leaving computers unlocked, sharing passwords, and carelessly discarding sensitive information. Process failures involve not keeping software up-to-date, lack of security polic
0 views • 15 slides