Understanding Data Breach Causes in Education
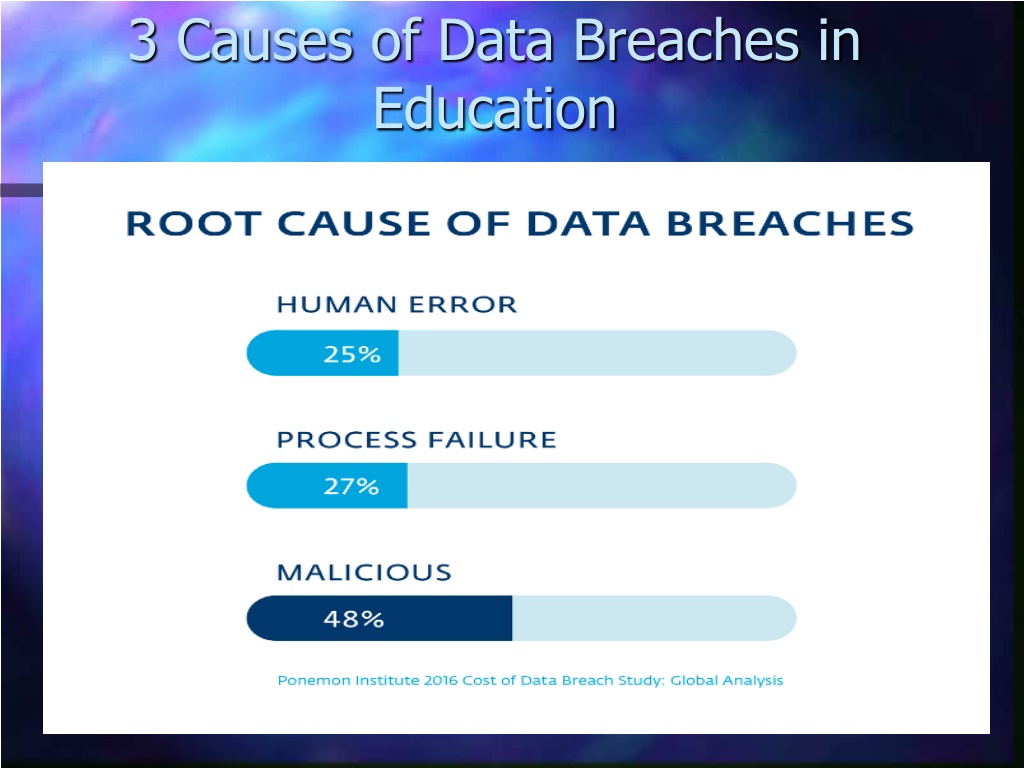
Data breaches in education are often caused by human errors, process failures, and malicious breaches. Human errors include leaving computers unlocked, sharing passwords, and carelessly discarding sensitive information. Process failures involve not keeping software up-to-date, lack of security policies, and insufficient security measures. Malicious breaches include malware, hacking attempts, and social engineering tactics. Implementing layered security measures, such as perimeter security, network security, and user awareness training, is crucial to prevent data breaches in educational institutions.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. Download presentation by click this link. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
E N D
Presentation Transcript
3 Causes of Data Breaches in Education
Human Error Defined Leaving a computer unlocked & unattended Writing passwords on sticky notes Sharing passwords Lost or stolen portable devices o Laptop, iPad, iPhone, iWatch Carelessly discarding sensitive information o Not shredding documents containing PII o Makes you vulnerable to dumpster diving
Process Failure Defined Failing to keep patches up-to-date Failing to keep virus definitions up-to-date Not properly implementing security products Insufficient account security policies No password expiration dates Not enforcing principal of least privilege Not having a layered security approach Need perimeter, network, end-point, & data security solutions working together
Malicious Breaches Defined Malware (60%) o Viruses (Trojans, Worms) o Ransomware variants (i.e. locky) o Spam emails w/ link to attached payload Hacking attempts (22%) o From guessing/stealing weak or default passwords Social Engineering (18%) o Phishing emails o Phone phreaking o F2F spoofing or sleight of hand
Can U Say Layered Security?!?! Perimeter security o Firewall & VPN (close to EOL need upgrades) Network security o Switches (in process of replacing EOL switches) o IDS/IPS system (Forcepoint in procurement now) Email security o Barracuda Spam Firewall (not keeping up need replacement)
Can U Say Layered Security?!?! End-point security o FDE & Lo Jack on laptops (investigating options) o NextGen desktop protection (investigating options) Data security o Employ DLP technology (will have capability with Forcepoint) o Re-examine privileged accounts & enforce concept of least-privilege User awareness training o Anti-phishing & spam training o Should use professional training software with user progress tracking capabilities (investigating options)
Top Holiday Phishing Scams Fake Purchase Invoices
Top Holiday Phishing Scams Shipping Status Malware Messages
Top Holiday Phishing Scams Email Deal Advertisements
Top Holiday Phishing Scams Inspect Links & URL s More Closely!
Top Holiday Phishing Scams Keep A Close Eye On Your Accounts!
Some Other Safeguards Don t use public computers or WiFi for online shopping Don t respond to popup ads Don t save your credit card info online Use complex/long account passwords Don t walk around the mall with Bluetooth turned on & use an RFID wallet to protect your credit cards