Good Laboratory Practices Study Protocols for Effective Research Management
Supplemental materials providing detailed protocols for implementing Good Laboratory Practices (GLP) in research settings. The protocols cover GLP requirements, experimental design, reading regulatory sections, approval processes, amendments, circulation lists, and study plans. These materials aim t
0 views • 22 slides
Update on SWAG Protocols and New NICE TA Progress Report
Kate Gregory leads the SWAG Protocols update for March 2024, with advancements in new protocols and NICE TA updates. A comparison of activities from Oct 2023 to Mar 2024 shows progress in issuing, reviewing, and drafting protocols. The latest NICE TA additions include treatments for advanced cancers
5 views • 13 slides
Understanding Host Bibliographic Records in Alma/Primo VE
Explore the concept of Host Bibliographic Records in the Alma/Primo VE system, which address the issue of linking single items to multiple bibliographic records. Learn how host bibs work, their creation during data migration, implications for library services, and the various types of host bibs used
0 views • 24 slides
Understanding Consistency Protocols in Distributed Systems
Today's lecture covers consistency protocols in distributed systems, focusing on primary-based protocols and replicated-write protocols. These protocols play a crucial role in ensuring consistency across multiple replicas. One example discussed is the Remote-Write Protocol, which enforces strict con
0 views • 35 slides
Oklahoma School Safety Protocols Overview
Overview of the school safety protocols in Oklahoma, which define requirements based on COVID-19 alert levels per capita in each county. The protocols include instructions for different alert levels, mask recommendations, visitor limitations, and activity guidelines. Schools are expected to offer in
0 views • 9 slides
Work Protocols and Safety Measures for Employees Returning to Work
In the wake of the COVID-19 pandemic, these work protocols emphasize roles, responsibilities, and mental wellbeing of employees. Pre-work precautions at home, personal measures, testing procedures, increasing awareness, and safe travel guidelines are highlighted to ensure a secure work environment.
0 views • 16 slides
Unified Volunteering Platform: Host Entity Account Management Training Update
Explore the recent updates in the Unified Volunteering Platform focusing on Host Entity account management training, webinars for UN Host Entities, and the launch of new self-service features. Learn about the roles within Host Entity accounts and the transition to the new system. Contact support for
0 views • 7 slides
Understanding Emergency Conditions in ERCOT Protocols
ERCOT has defined various levels and communication protocols for Emergency Conditions within the electrical grid system. This includes Emergency Notices, Energy Emergency Alerts, operating plans, outage coordination, and requirements related to voltage support for ensuring system safety and reliabil
6 views • 18 slides
Understanding Host-Parasite Relationship in Microbiology
In microbiology, the host-parasite relationship is crucial for understanding diseases caused by pathogens. This lecture covers definitions of terms like pathogenicity, pathogen, disease, resistance, susceptibility, infection, virulence, and transmissibility. It also delves into the division of host
0 views • 16 slides
Understanding Lock-Based Protocols in Database Concurrency Control
Lock-based protocols are essential mechanisms for controlling concurrent access to data items in a database system. This involves granting locks in exclusive (X) or shared (S) modes to ensure data integrity and prevent conflicts. Lock compatibility matrices and locking protocols play a crucial role
2 views • 69 slides
Laboratory Safety Protocols and Pathogen Classification
Scientist must adhere to lab safety protocols including wearing safety gear, proper waste disposal, and handling chemicals carefully. The classification of pathogens varies by country based on WHO guidelines into four risk groups. Understanding these protocols and classifications is crucial for a sa
0 views • 17 slides
Understanding Host Stars and Their Importance in Exoplanet Research
Host stars play a crucial role in determining the physical parameters of planets they host, impacting exoplanet characterization and planet formation understanding. Data from astrometry, photometry, and spectroscopy, combined with stellar evolutionary models, help derive host star properties critica
0 views • 51 slides
SRYA Clinic Soccer Fall 2021 Updates and Protocols
Stay updated on the latest news and protocols for the SRYA Clinic Soccer Fall 2021 season. Learn about volunteer positions, contacts, fun facts about the program, COVID-19 updates, and general protocols from Rec & Parks. Ensure the safety and well-being of players, coaches, and families while enjoyi
0 views • 23 slides
State Transportation Department's Stormwater Monitoring Program Overview
This document presents findings and protocols from the National Cooperative Highway Research Program related to stormwater monitoring goals, objectives, and protocols for state departments of transportation. The project team, objectives, and report organization are outlined, aiming to provide guidan
0 views • 32 slides
Animal Use Protocols: Finding the Right Balance
Exploring the analogy between the story of the three bears and animal use protocols, this content delves into the importance of providing just the right amount of information in research protocols. Through examples of intravenous injections in mice, the text emphasizes the necessity of striking the
0 views • 8 slides
Secure Composition of Key Exchange Protocols
Explore the game-based composition approach for key exchange protocols, focusing on ensuring security in compositions with arbitrary tasks and the universal composability of protocols. Delve into the Bellare-Rogaway security model and the details of security games in protocol analysis. Understand ke
0 views • 25 slides
Taming Adaptivity in YOSO Protocols: The Modular Way
Explore the concept of taming adaptivity in YOSO protocols through a modular approach. The research delves into the efficiency, adversary adaptivity, role assignments, and compiler models in synchronous YOSO protocols. The visual presentations illustrate the framework, challenges, and strategies in
0 views • 19 slides
Exploring the Impact of Randomness on Planted 3-Coloring Models
In this study by Uriel Feige and Roee David from the Weizmann Institute, the effect of randomness on planted 3-coloring models is investigated. The research delves into the NP-hard nature of 3-coloring problems, introducing a hosted coloring framework that involves choices like the host graph and th
0 views • 55 slides
Network Routing Algorithms and Protocols Overview
Understanding network routing algorithms and protocols is crucial in the field of networking. This content provides insights into the initialization process, loop prevention mechanisms, and the use of algorithms like OSPF and IS-IS. It also touches on routing protocols such as RIP and EIGRP, explain
0 views • 17 slides
Understanding Mechanisms of Viral Infection and Spread
Viral infection involves a replicative cycle within the host, leading to a range of cellular responses from no apparent effect to disease. Factors such as virulence genes, host characteristics, and viral genome influence the pathogenicity and virulence of a virus. The process includes entry into the
0 views • 16 slides
Understanding Reliable Transport and User Datagram Protocol in Computer Networking
This content covers the concepts of reliable transport in computer networking, including the reliable transport layer protocols like TCP, UDP, and the basics of Domain Name Service (DNS). It explains the layers of the Internet, the functions of each layer, and the differences between TCP and UDP pro
0 views • 28 slides
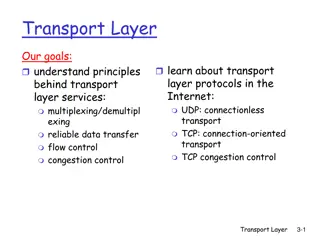
Understanding Internet Transport Layer Services and Protocols
In the realm of networking, exploring the principles of transport layer services is crucial. This involves concepts like multiplexing/demultiplexing, reliable data transfer, flow control, and congestion control, which are facilitated by protocols such as UDP and TCP. The transport layer acts as a br
0 views • 56 slides
Overview of Identification Protocols in CS255 by Dan Boneh
The lecture in CS255 covers various topics related to identification protocols, including signatures from trapdoor functions, certificates, revocation methods, certificate issuance problems, defense mechanisms like certificate transparency (CT), and moving on to protocols. The talk also explores the
0 views • 43 slides
Towards Practical Generic Zero-Knowledge Protocols
Exploring the evolution of zero-knowledge protocols, this presentation by Claudio Orlandi from Aarhus University delves into the concepts of Zero-Knowledge from Garbled Circuits, Privacy-Free Garbled Circuits, and more. The talk discusses efficient methods for proving statements and touches on relat
0 views • 29 slides
Enhancing Accelerator-Host Coherence with Crossing Guard
Explore the need for coherence interfaces in integrating accelerators with host protocols, addressing complexities and safety concerns, emphasizing customizable caches and standardized interfaces for optimal performance and system reliability.
0 views • 55 slides
Enhancing Server State Detection in OpenStack for Immediate Host Fault Reporting
This blueprint proposes the development of a new API in Nova to promptly update the server state in OpenStack when a host fault occurs. The intention is to ensure reliability and real-time updates of server and host states for Telco-grade VIM, allowing users to take necessary actions swiftly in case
0 views • 5 slides
Understanding Radiation Pressure Confinement in Quasars and Their Host Galaxies
Jonathan Stern's research explores the implications of radiation pressure confinement on the interaction between quasars and their host galaxies, focusing on photo-ionized gas systems. Through modeling and analyzing various properties of these systems, the study offers insights into quasar feedback
0 views • 35 slides
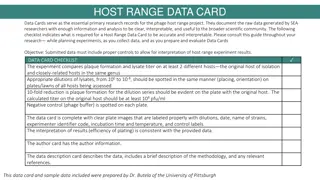
Guidelines for Host Range Data Card Creation in Phage Research
Essential checklist for creating accurate and interpretable Host Range Data Cards in phage host range projects, detailing required experiment components, controls, data documentation, and analysis. The provided checklist ensures the inclusion of necessary information and proper formatting for clear
0 views • 6 slides
Wireless Sensor Networks: Medium Access Protocols Overview
This collection of images presents key concepts in wireless sensor networks, focusing on medium access protocols, the ISO/OSI reference model, types of conflict resolution, contention-free protocols, Bitmap protocol, ALOHA algorithm, and its analysis and efficiency. Various protocols and algorithms
0 views • 83 slides
Understanding the Complexities of Parasite Life Cycles and Host Interactions
Parasites exhibit diverse life cycles and behaviors, with cycles ranging from domestic to sylvatic environments. Factors influencing parasite diseases include host specificity, immunity, and host-parasite interactions. Parasitism can alter host behavior, impacting ecological dynamics. Immunology pla
0 views • 9 slides
Green Protocols for Greener Arbitrations
The Green Protocols introduced by AtLAS aim to guide the arbitration community in committing to environmentally sustainable practices. These protocols suggest ways to reduce carbon emissions, energy consumption, waste generation, and unnecessary travel by utilizing electronic communication, video co
0 views • 14 slides
Comprehensive Guide to Hacking Techniques & Intrusion Detection
Dive into the world of hacking techniques, intrusion detection, and network protocols with expert Ali Al-Shemery. Learn about host discovery, port scanning, packet crafting, and more using tools like Nmap. Explore the importance of network protocols like TCP, UDP, ICMP, and ARP. Discover the art of
0 views • 50 slides
Understanding Ethernet and Multiple Access Protocols in Computer Networks
Exploring the fundamentals of Ethernet and multiple access protocols in computer networks, this content discusses the two primary categories of multiple access protocols - contention access and controlled access. It delves into topics such as CSMA/CD, LANs, performance of multiple access schemes, ad
0 views • 7 slides
Scalable Identity and Key Management for Publish-Subscribe Protocols
This research by Prashant Anantharaman from Dartmouth College focuses on scalable identity and key management for publish-subscribe protocols in Energy Delivery Systems. It discusses the architecture, goals, assumptions, and implementation results in the context of PKI vs. Macaroons protocols. The w
0 views • 37 slides
Life Cycle of Ascaris lumbricoides in Human Host
Ascaris lumbricoides, commonly known as roundworm, is a human parasite found in the intestine. The life cycle involves copulation, egg development, and infection of a new host through ingestion of eggs. It does not require an intermediate host. The larval stages undergo migration within the body. Th
0 views • 14 slides
Comprehensive Examination Questions on Data Management Systems and Security Protocols
This content covers a range of topics related to data management systems, including two-phase locking and two-phase commit protocols, Bayou system with vector clocks and causality, digital signatures and certificates in protocols, and authentication protocols. Questions include scenarios and concept
0 views • 6 slides
Understanding Parasitology: The Study of Organisms Living on or within Hosts
Parasitology is the study of parasites, which are organisms that live on or within a host and derive nutrients from them without benefiting the host. Parasites can be classified as ectoparasites or endoparasites based on their location in or on the host. Hosts play a crucial role in the life cycle o
0 views • 23 slides
Improved Merlin-Arthur Protocols for Fine-Grained Complexity Problems
The text discusses Merlin-Arthur proof systems and protocols for central problems in fine-grained complexity, particularly focusing on the time complexity, completeness, and soundness of these protocols. It also touches on recent interest in these protocols and presents new results in areas such as
0 views • 16 slides
Quantum Distributed Proofs for Replicated Data
This research explores Quantum Distributed Computing protocols for tasks like leader election, Byzantine agreement, and more. It introduces Quantum dMA protocols for verifying equality of replicated data on a network without shared randomness. The study discusses the need for efficient protocols wit
0 views • 28 slides
Terrestrial File Transfer Concept: Design Goals and Protocols
This document discusses the concept of terrestrial file transfer as presented in a series of slides from an ESA event in Noordwijkerhout, The Netherlands. It covers the purpose, design goals, protocols, and transport protocols involved in exchanging files between agencies for mission design, operati
0 views • 20 slides