Discover the Hidden Gems of Puerto Rico with a Kayaking Tour
Embark on an extraordinary adventure with \"Discover the Hidden Gems of Puerto Rico with a Kayaking Tour.\" Explore secret coves, pristine lagoons, and remote islands, all while paddling through crystal-clear waters. From bioluminescent bays to cultural expeditions, unlock the island's treasures on
2 views • 22 slides
Understanding Hidden Harm: Impact of Substance Misuse on Young People
The Norfolk Drug and Alcohol partnership aims to address the hidden harm caused by substance misuse, specifically focusing on young people affected by someone else's drug or alcohol problems. The project seeks to bring statistics to life, raise awareness, and encourage support for those experiencing
4 views • 29 slides
Recognizing Hidden Bias in the Workplace
In the workplace, hidden bias, also known as implicit bias, can significantly impact hiring, employment decisions, and overall workplace dynamics. Deloitte's 2019 State of Inclusion Survey revealed that a substantial percentage of workers experienced bias at least monthly. Hidden biases can be based
3 views • 18 slides
Understanding Modes of Communication and Verbal Messages
Communication occurs through verbal and nonverbal modes, with messages having denotative and connotative meanings. Verbal messages vary in directness, affecting the effectiveness of communication. Indirect messages offer advantages such as politeness and avoiding offense, but can also lead to misund
0 views • 64 slides
Heartwarming Messages of Thanks and Support from the Community
Heartfelt messages of gratitude and appreciation are shared by various organizations and community members for the efforts of frontline workers during challenging times. The messages highlight the unity, support, and resilience within the community as they come together to ensure the well-being and
0 views • 8 slides
Understanding the Importance of Nonverbal Communication in Communication Skills
Nonverbal communication plays a crucial role in conveying messages and signals through platforms like eye contact, facial expressions, gestures, posture, and spatial distance. It includes appearance, body language, silence, time, and space. This form of communication can significantly impact the rec
0 views • 16 slides
Introduction to Public Key Cryptography
Public key cryptography, exemplified by algorithms like Diffie-Hellman and RSA, revolutionizes secure communication by allowing users to encrypt messages with public keys known to all and decrypt them with private keys known only to the intended recipient. This advanced encryption method ensures sec
1 views • 44 slides
The Hidden Messages in Water: Power of Positivity
Encountering overwhelming situations is common, but maintaining a positive attitude can be transformative. "The Hidden Messages in Water" explores how positivity affects water crystals, emphasizing the impact of words. Discover the unique connection between positivity and well-being, as seen through
1 views • 16 slides
Pictur.e.Reveal.Game - Answer Questions and Uncover Hidden Picture
Dive into the Pictur.e.Reveal.Game where you answer questions related to Franklin D. Roosevelt, the Great Depression, and the New Deal to reveal a hidden picture. Test your knowledge and uncover historical facts as you progress through the questions and reveal the hidden image piece by piece.
1 views • 22 slides
Comprehensive Guide to Automated Export System (AES) Response Messages
Explore a detailed guide on Automated Export System (AES) response messages, covering topics such as common response messages, fatal errors, compliance alerts, and proper actions for different scenarios. Gain insights into ensuring compliance, resolving errors, and understanding the ITN issuance pro
1 views • 29 slides
Enhancing User Productivity with Outlook Actionable Messages
Explore how to develop and deploy Outlook Actionable Messages to optimize user productivity. Join Julie Turner, a seasoned professional developer, in learning about connectors, message creation, API endpoints, security, and more, to create targeted and interactive messages within Outlook. Get a hand
0 views • 18 slides
Introduction to Cryptography, Cryptanalysis, and Cryptology
Cryptography involves protecting information by encrypting and decrypting data, while cryptanalysis focuses on breaking encryption methods to access hidden messages. Cryptology encompasses both cryptography and cryptanalysis. Encryption encodes messages to prevent unauthorized access, while decrypti
0 views • 12 slides
Insights on the Hidden Color Component in Nuclear Physics
Introduction to the hidden color component in nuclear physics, discussing its definition, physical effects, and multiquark states like tetraquarks, pentaquarks, and dibaryons. Various models and ongoing debates on the role of hidden colors in multi-quark systems are explored. The concept of colorles
1 views • 42 slides
Emergency Warning System: Important Messages Sent Directly to Mobile Telephones
The Emergency Warning System sends critical messages directly to mobile phones to ensure public safety. Users will receive alerts with vibrating, siren-like sounds and text messages informing them of any ongoing situation and necessary actions. A test is scheduled for Wednesday, 14th June at 12:00 t
0 views • 5 slides
Understanding Micro-Inequities in the Workplace
Exploring the concept of micro-inequities, this presentation delves into the subtle messages that devalue individuals, discussing their impact, forms, communication role, and conversion into positive affirmations. Highlighted are the reasons for learning about micro-inequities, emphasizing diversity
1 views • 17 slides
Understanding Micromessaging: Hidden Impact of Subtle Behaviors
Micromessaging refers to the subtle, semi-conscious messages we send through our behaviors, both verbal and physical, that influence our interactions with others. These messages, categorized as micro-affirmations and micro-inequities, can have a significant impact on individuals. The concept delves
1 views • 17 slides
Challenging Convictions: Hidden Failures and Bayesian Analysis
Delve into the intriguing concept of hidden failure states impacting model confidence, as explored in the article by Lachlan J. Gunn and team. Through Bayesian analysis, the article uncovers how overwhelming evidence may fail to persuade, introducing terms like Verschlimmbesserung. Case studies invo
0 views • 13 slides
Positive Messages for Encouragement and Growth
Empower yourself with inspirational messages about resilience, courage, kindness, and self-improvement. Encouraging individuals to bounce back from setbacks, be brave, make mistakes, and nurture a growth mindset. Remind yourself that smiling, apologizing, and facing challenges head-on are essential
0 views • 39 slides
Mastering Data-Driven Messages for Effective Communication
Unlock the power of data-driven messages to create impactful communication outcomes. Learn how to craft messages that inspire action and drive results through compelling storytelling. Explore the key elements of a message platform and harness the importance of data in shaping your message strategy f
0 views • 59 slides
Co-created Messages & Trusted Messengers for COVID-19 Vaccine Acceptance in Northern Nigeria
Dr. Chizoba Wonodi is evaluating the use of co-created messages and trusted messengers to improve COVID-19 vaccine acceptance in Northern Nigeria. Vaccine hesitancy due to conspiracy theories and safety concerns remains a challenge. TM-COVAC study aims to design targeted messages using human-centere
0 views • 8 slides
Understanding SMTP - Simple Mail Transfer Protocol
SMTP (Simple Mail Transfer Protocol) is a fundamental component of the application layer in computer networks. It is used for sending electronic mail messages between servers and user agents. The process involves user agents composing messages, connecting to mail servers, and transferring messages o
0 views • 29 slides
Inspirational Images and Messages from Harlem
Explore a collection of images and messages showcasing the beauty and community spirit of Harlem. From the historic Elmendorf Reformed Church to expressions of teamwork and hard work, these visuals reflect a culture of giving back and unity in the neighborhood. Feel inspired by the messages of hope,
0 views • 7 slides
Reported Conversations and Text Messages Example
This content highlights examples of reported speech in text messages, featuring various emotional expressions and conversations between two individuals. The provided text messages show dialogues involving feelings, requests, and decisions, which can serve as a practice exercise for reporting convers
0 views • 6 slides
Effective Strategies for Media Interactions: Tips, Key Messages, and More
Discover tips for interacting with print and television media, key messages about ACMS, and strategies for reinforcing mission and values. Learn how to handle interviews, turn questions towards key messages, and work effectively with reporters to create compelling news angles.
0 views • 28 slides
Cryptography in the Bounded Storage Model: Revisited - Eurocrypt 2023
Cryptography researchers revisit the Bounded Storage Model (BSM) to enhance security in transmitting messages while considering limited storage capacities. The BSM restricts adversaries to limited storage, enabling unconditional security. The model aims to address challenges in message transmission
0 views • 16 slides
Optimization Strategies for MPI-Interoperable Active Messages
The study delves into optimization strategies for MPI-interoperable active messages, focusing on data-intensive applications like graph algorithms and sequence assembly. It explores message passing models in MPI, past work on MPI-interoperable and generalized active messages, and how MPI-interoperab
0 views • 20 slides
Community Health & Wellness Messages from University of Hawai'i CHL Program
Community messages promoting healthy habits, such as encouraging kids to drink more water with fun flavors and keeping cool water readily available. Multiple messages shared by Dr. Rachel Novotny from the University of Hawai'i and the College of Tropical Agriculture and Human Resources. Contact info
0 views • 26 slides
Deanonymization of TOR HTTP Hidden Services - Techniques and Defense
This detailed content delves into the deanonymization of TOR HTTP hidden services, discussing known techniques, downgrading the protocol, and potential fixes. It covers the concept of hidden services, key certificate risks, search methods, and Gzip compression vulnerabilities. The author, a security
0 views • 32 slides
COVID-19 Vaccination Programme for Childbearing Women - Educational Slides and Key Messages
This presentation focuses on the COVID-19 vaccination programme for childbearing women, providing information on learning objectives, key messages, and current vaccination programmes for pregnant and breastfeeding women. It discusses the understanding of COVID-19 symptoms, the importance of vaccinat
0 views • 24 slides
Deconstructing Media Messages: Key Concepts and Techniques
In media literacy, deconstructing media messages involves closely examining and dissecting TV shows, newspapers, movies, advertisements, etc., to understand their creators' intentions, biases, and hidden meanings. Key concepts include analyzing the source, text, subtext, audience, and persuasion tec
0 views • 19 slides
Messages of Hope and Faith Through Images
These images convey messages of hope, faith, and assurance of victory through challenging times. They depict themes of freedom, joy, safety, and the presence of Beloved Jesus. The visuals inspire courage, faith, and a sense of assurance that one is never alone, accompanied by powerful messages of lo
0 views • 10 slides
Working with SMS Messaging in Android Applications
Explore how to send and receive SMS messages programmatically within your Android application. Learn about utilizing the built-in Messaging application, sending SMS messages using Intents, and managing SMS messaging capabilities programmatically without user intervention. Discover techniques for sen
1 views • 29 slides
Understanding Allegory: Unveiling Hidden Meanings in Literature
Delve into the world of allegory and uncover the hidden depths within stories, poems, and pictures. Learn to differentiate between literal and allegorical meanings, exploring how authors convey deeper messages through symbolic representations. Discover the power of allegory in conveying moral, polit
0 views • 8 slides
Embracing Growth Mindset and Hidden Messages in Visual Communication
Explore the concept of growth mindset versus fixed mindset, highlighting the importance of challenges, effort, and learning from criticism. Discover hidden messages in logos, such as the subtle arrow in the FedEx logo, and how they influence perception and communication.
0 views • 28 slides
Understanding Semantic Aspects of Interpretation
Explore the semantic structure of oral messages, distinctions between meaning, sense, and semantics in linguistics, and the role of context in interpreting linguistic units. Discover how interpreters render sense in speech acts, the proposition as a picture of the world, and the components of verbal
0 views • 36 slides
Fun Spy Challenges for Beavers - Crack the Codes!
Dive into exciting spy missions with a group of clever beavers! Decode secret messages using various encryption techniques such as switching codes, letter grouping, Pig Pen cipher, Morse code, and Caesar cipher. Test your spy skills as you unravel each challenge to reveal hidden messages. Unleash yo
0 views • 6 slides
Effective Communication with APRS via Emails and Text Messages
Discover how to utilize APRS for seamless communication through emails and text messages. Learn about sending and receiving messages, establishing accounts, confirming deliveries, and more using this innovative technology. Enhance your communication capabilities with APRS today!
0 views • 15 slides
Understanding the Core Teachings of the Three Angels' Messages
Delve into the profound significance of the Three Angels' Messages as a foundational aspect of Seventh-day Adventist beliefs. Explore the theological and personal implications of these messages on individual spiritual growth and the broader Adventist community. Gain insights into the core doctrinal
0 views • 40 slides
TYPES OF REASONING DEDUCTION AND INDUCTION
Reasoning involves a connected sequence of thoughts leading to a conclusion. Deductive reasoning moves from general to specific, identifying assumptions and hidden premises. Categorical syllogisms demonstrate valid and sound argument structures, while real-life arguments may require uncovering assum
0 views • 21 slides
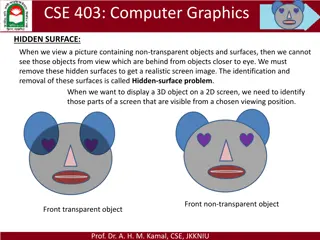
Hidden Surface Removal in Computer Graphics
In computer graphics, the hidden-surface problem refers to identifying and removing surfaces that are not visible in a given view to create a realistic screen image. Different methods like Depth Buffer (Z-Buffer) and Scan-Line are used to address this issue by determining the closest visible surface
0 views • 14 slides