Overview of Food and Beverage Management at President Hotel, Athens
Food and Beverage Management at President Hotel in Athens involves various roles such as F&B Manager, Assistant Manager, Chef, and service staff. The department oversees bars, banquet services, room service, and more. The main duties include HACCP compliance, menu planning, cooperation with other de
0 views • 15 slides
Enhancing Access to Medicines and Health Products through Innovative Approaches
Global Health Centre experts discuss how building access into innovation can ensure better access to medicines, vaccines, and health products. Key ideas include planting seeds for access early in innovation, exploring alternative innovation models, and rethinking the relationship between innovation
4 views • 20 slides
How Does iPad Hire Streamline Guest Check-ins at Seminars?
This PDF, Discover how iPad hire simplifies seminar check-ins, offering efficiency, customization, and real-time updates for a seamless guest experience. Techno Edge Systems LLC offers you a standard services of iPad Hire Dubai. For More info Contact us: 971-54-4653108 Visit us: \/\/ \/ipad-hire-du
4 views • 2 slides
2022 Thales Access Management Index
Thales Access Management Index highlights the current landscape of access security, revealing insights on multi-factor authentication adoption, remote and privileged user access management, VPN usage trends, challenges faced, and preferences towards third-party access management. The report emphasiz
2 views • 9 slides
Write for us free guest post
At GoBookmarking, we offer an open platform for writers to contribute their insights and expertise. Submit a free guest post and share your knowledge on a wide range of topics, including technology, business, fashion, and more. Whether you're a seasoned writer or a newcomer, we welcome your unique p
4 views • 4 slides
Guidelines for Expanded Access to Investigational Drugs and Devices
Providing guidance on types of Expanded Access for drugs, biologics, and devices, this content explains the concept of Expanded Access and the criteria that must be met. It covers different types of Expanded Access for drugs and devices, emphasizing the importance of patient safety and benefit. The
0 views • 10 slides
Personnel Safety Systems and Access Control at CERN Facilities
Personnel Safety Systems at CERN include ODH detection, fire safety measures, and access control to protect personnel from hazards. Various access control layers are implemented to regulate entry to different parts of the facility, ensuring only trained personnel access underground areas. Biometric
0 views • 19 slides
Enhancing SEO Strategies with Diverse Backlink Approaches
Implementing a strategic backlink plan involving Paid Backlinks, Edu-Based Links, Web 3.0 tactics, Google Sites optimization, and Guest Posting can significantly boost website rankings and visibility. Paid backlinks, particularly from Google, play a crucial role in improving link popularity and SEO
0 views • 13 slides
Explore Georgia with BE MY GUEST in Tbilisi and Kakheti
BE MY GUEST in Tbilisi, Georgia, offers travel services at special rates, tours, medical tourism, MICE tour organization, and more. Georgia is a beautiful country with green valleys, old churches, and exciting activities. Discover Tbilisi's landmarks like the Metekhi Bridge, Narikala Fortress, and M
1 views • 16 slides
Understanding Memory Virtualization in Operating Systems
Memory virtualization in operating systems involves mapping guest addresses to host addresses with an added level of indirection managed by the hypervisor. Virtualization extensions in x86 processors enhance efficiency by allowing safe execution of guest code in Ring 0 through supervisor mode. The a
1 views • 28 slides
English for Hotel: Handling Reservations and Guest Requests
Enhance your English language skills for hotel operations through scenarios involving taking reservations, managing guest requests, and coordinating with different hotel departments. Practice key phrases and vocabulary related to room bookings, guest services, and communication protocols in the hosp
0 views • 19 slides
Port of Stockton Restricted Area Access Control and ID Card Policy
Access to restricted areas at the Port of Stockton facilities requires possession of a TWIC (Transportation Worker Identification Credential). Only authorized personnel, such as employees, contractors, and those with regular access, may receive a Port Access Card after approval by the Facility Secur
0 views • 6 slides
Hospitality Industry Benefits From AI-Powered Concierge Mobile Apps
Check out how AI-powered concierge mobile applications are changing the game for the hospitality industry. A helping hand in enhancing guest experience, this app mainly does its bit to help hotels and resorts in increasing the guest experience by str
0 views • 8 slides
Understanding Hotel Classification and Types
Hotel classification and types cover various aspects such as facilities, services, amenities, guest types, and factors influencing hotel classification. From resort hotels to airport hotels and city center accommodations, each hotel type serves different purposes and caters to diverse guest preferen
0 views • 44 slides
Introduction to Database Security and Countermeasures
Database security is essential to protect data integrity, availability, and confidentiality. Countermeasures such as access control, inference control, flow control, and encryption can safeguard databases against threats. Access control restricts user access, inference control manages statistical da
0 views • 26 slides
O3 Access Control Solution Overview
O3 Access Control Solution offers unique selling points like single-seat management software, role-based permissions, customizable user information, and more. The system includes a compact controller with multi-format reader support and BACnet Access objects. It integrates with other O3 modules for
0 views • 10 slides
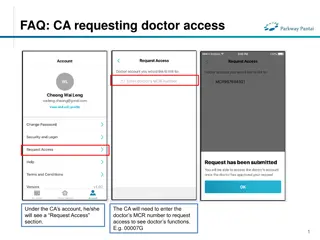
FAQs for Doctor and Clinical Assistant (CA) Account Access Management
Learn how CAs can request access to doctors' functions by entering the MCR number, how doctors can grant or remove CA access, and how CAs can manage access to multiple doctors. The process includes requesting, approving, and unlinking accounts, ensuring efficient and secure access management in a cl
0 views • 4 slides
Importance of Housekeeping Management in Hotels
Housekeeping management plays a crucial role in maintaining a hotel's reputation for cleanliness and quality. The housekeeping department ensures clean rooms, common areas, and overall appearance, contributing significantly to the guest experience. Without a strong housekeeping staff, the hotel's im
0 views • 75 slides
EventsHQ Virtual Event Registration: User Access and Setup Guide
This comprehensive guide provides step-by-step instructions on setting up virtual event registration using EventsHQ. It covers how users can access event details, join the event, and includes best practices for sharing access links. Learn how to utilize the Virtual Event Details feature, send remind
1 views • 19 slides
Accessible Voting System for Californians with Disabilities
Learn about the Remote Accessible Vote-by-Mail System in California, designed to empower voters with disabilities to securely access, mark, and return their ballots from any computer with internet access. Find out who is eligible to use the system, how to access and return the ballot, and the steps
0 views • 23 slides
Dell Networking Solutions for BYOD and Guest Access Projects
Dell offers end-to-end solutions for Bring-Your-Own-Device (BYOD) and guest access projects, enabling secure employee access and controlled connectivity for visitors. The framework includes mobility business models, device security, network protection, and scalability. Dell supports customers in imp
0 views • 11 slides
Role-based Access Control Policies and Security Properties Overview
This content provides an overview of Role-based Access Control (RBAC) policies, Administrative RBAC (ARBAC) systems, and security properties in the context of access control in large organizations. It discusses the implementation of RBAC in various software systems, the assignment and revocation of
0 views • 18 slides
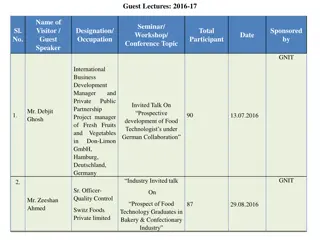
Guest Lectures and Seminars on Food Technology and Processing Industry
The document provides a detailed overview of various guest lectures, seminars, workshops, and conferences conducted at GNIT focusing on food technology, processing industry trends, and collaborations with international experts. Topics include cheese and alcoholic beverage manufacturing, sustainable
0 views • 20 slides
Open Access at Charles University: Opportunities and Challenges
Charles University is navigating the landscape of open access following the implementation of the Czech National Open Access Strategy. The university is working towards making all research articles and proceeding papers open access, monitoring article processing charges, and promoting open access as
0 views • 24 slides
Snowsports Program at Scotch: Handbook, Training, and Guest Speaker
Embark on a thrilling adventure with the Snowsports program at Scotch featuring dryland training, winter sport camps, cross country skiing, and guest speakers like Al Guss, a former Winter Olympic ski team member. Explore opportunities for beginners and intermediate skiers, with a focus on interscho
0 views • 20 slides
Efficient Hotel Reservation Procedures for Guest Satisfaction
Taking reservations accurately is crucial for hotel efficiency and guest satisfaction. This guide covers aspects like checking availability, handling special requests, policies, and confirmation procedures to ensure a smooth reservation process. By implementing clear reservation procedures, hotels c
0 views • 23 slides
Understanding Filesystem Security Principles and Access Control
Learn about filesystem security, general principles, discretionary access control (DAC), closed vs. open policy, closed policy with negative authorizations, and access control entries and lists. Discover how files and folders are managed, the role of access control lists (ACLs), and the different le
1 views • 56 slides
Understanding Ethernet and Multiple Access Protocols in Computer Networks
Exploring the fundamentals of Ethernet and multiple access protocols in computer networks, this content discusses the two primary categories of multiple access protocols - contention access and controlled access. It delves into topics such as CSMA/CD, LANs, performance of multiple access schemes, ad
0 views • 7 slides
Understanding Shared Memory, Distributed Memory, and Hybrid Distributed-Shared Memory
Shared memory systems allow multiple processors to access the same memory resources, with changes made by one processor visible to all others. This concept is categorized into Uniform Memory Access (UMA) and Non-Uniform Memory Access (NUMA) architectures. UMA provides equal access times to memory, w
0 views • 22 slides
Housekeeper Job Description at Sparkl Resorts
Hourly, nonexempt housekeeping position at Sparkl Resorts responsible for maintaining guestrooms to high standards of cleanliness. Duties include daily cleaning tasks, prioritizing workload, and ensuring guest satisfaction. Qualifications include physical ability, flexibility, guest service orientat
0 views • 27 slides
Understanding Access Changes and Community Relations at Fermilab
Access to Fermilab has become more complicated due to changing DOE guidance and security posture. Efforts are being made to streamline access while addressing security gaps. Public access to outdoor areas of the Fermilab campus is still encouraged, but communication regarding access changes needs im
0 views • 12 slides
Understanding Computer System Protection and Security
Mechanisms like protection and security ensure controlled access to a computer system's resources and prevent malicious activities. Protection involves defining access control levels through models, policies, and mechanisms. Security focuses on user authentication to safeguard stored information. Di
0 views • 25 slides
Understanding Access to ITU Information and Documents
Exploring the concept of access in the work of a dedicated group, this content delves into the types of information that could or should be made available to the public, along with considerations on when access should be provided. It highlights the varying stages of information dissemination, discus
0 views • 8 slides
Harvard Chan School 2021 Yearly Access Review Process
The Harvard Chan School conducts its annual Yearly Access Review (YAR) process to review user access to various financial systems. The process involves assessing permissions, levels of access, and organizational details for each team member. Instructions are provided on reviewing worksheets, adding
0 views • 19 slides
Understanding Security Access in PeopleSoft Finance
Explore the various levels of security access in PeopleSoft Finance, from basic entry access to transaction entry, approvals, and procurement processes. Learn how to request individual and department security access and find relevant forms on the financial services website. Discover the different ty
0 views • 11 slides
Proxy Access to Medications Implementation Stages
This document outlines the implementation stages for proxy access to medications. It covers agreements with healthcare providers, prerequisites including compliance and data sharing agreements, and systems configuration for access to medical records. The stages include setting up access for care pro
0 views • 7 slides
CSUEB Academic Access Enhancement and Excellence Fee Proposal
The CSUEB Academic Access Enhancement and Excellence Fee Proposal aims to enhance the academic environment, reduce student costs, and provide equal access to educational materials. Components include an Academic Access Enhancement fund, e-textbooks program, and provision of tablets/netbooks to all i
0 views • 23 slides
Sungarden Terrace Compassionate Assisted Living, Memory, and Respite Care in Lemon Grove
Respite care is an effective service that welcomes a guest resident to stay temporarily at Sungarden Terrace. Although this time can be beneficial for the caregiver, our guest often expresses interest in making the short-term visit, permanent. Meetin
0 views • 6 slides
Responsibilities of a NAPS Branch President
The role of a NAPS Branch President involves leading by example, directing and controlling meetings, setting agendas, introducing guest speakers with proper background information, and ensuring adherence to organizational rules and orders. The President must be familiar with the constitution, bylaws
0 views • 26 slides
Enhancing Data Visualization Community Engagement through Viz and Tell Sessions
This resource outlines a model for building a critical community focused on data visualization, offering Viz and Tell/Coffee Break sessions to encourage engagement and learning. Topics covered include visualization instruction, tools, ethics, data journalism, and more. The model emphasizes open disc
0 views • 6 slides