Data Cleaning
Data cleaning is the process of fixing or removing incorrect, duplicate, or incomplete data within a dataset. It improves data quality, ensuring accurate and reliable information for decision-making. Learn why data cleaning is necessary and the essential reasons to clean your data.
4 views • 35 slides
How to Consolidate EasyChair Accounts
Learn how to merge two EasyChair accounts and consolidate them into one for the AMS Annual & WMC Conferences. Follow the steps outlined to ensure a smooth transition and avoid having duplicate accounts. Images included for visual guidance.
0 views • 8 slides
What is Email Marketing?
Email marketing is a cornerstone of digital marketing, leveraging targeted email communication to engage subscribers and drive desired outcomes. By crafting compelling content, personalized messages, and strategic segmentation, businesses can cultivate meaningful relationships with their audience. B
1 views • 7 slides
Lubbock Retail Integration Task Force – LRITF
The Lubbock Retail Integration Task Force (LRITF) discussed various topics including customer choice enrollment, Winter Storm Uri securitization, distribution loss factors, and updates on duplicate addresses and various other updates. The completed action items Q&A provided insight into transitionin
0 views • 11 slides
Enterprise Marketing Management (EMM) Capabilities for Effective Email Campaigns
Enterprise Marketing Management (EMM) offers a comprehensive suite of tools for tracking marketing expenditure, ROI, and lead performance. With capabilities ranging from Marketing Activity Codes (MAC) for tracking sources to customizable email templates and delivery reports, EMM streamlines the proc
0 views • 8 slides
Efficient Biofilm Removal Products for Cleaner and Safer Environments
When it comes to maintaining cleanliness in demanding environments, using the right biofilm removal products is crucial. \n\nChemical Essentials' F919SC Biofilm Remover and Heavy Duty Degreaser stands out as a powerful solution designed to tackle eve
5 views • 5 slides
Efficient Record-Keeping System for Needle Stick Injuries
Streamline your needle stick and sharp object injury reporting process with EPINET for Microsoft Access. Learn how to enter new incident records, avoid duplicate IDs, input dates accurately, and utilize handy tips for efficient data entry. Ensure completeness of information to enhance infection prev
0 views • 35 slides
Mail Server Basics from a Linux Operating System Perspective
Dive into the essentials of mail servers, exploring the key components of an email system, such as email clients and servers. Learn how email clients work, the functions they offer, and the role of email servers in managing and routing messages to ensure delivery over the Internet.
0 views • 25 slides
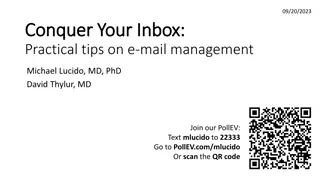
Mastering Email Management: Practical Tips for Efficiency
Learn how to conquer your email inbox with practical tips from Michael Lucido, MD, PhD, and David Thylur, MD. This seminar aims to improve your email culture, personalize management strategies, and enhance Outlook skills for increased efficiency. Discover how to shift to a compassionate email cultur
0 views • 18 slides
Efficient Slide Presentation Tips & Resource Utilization
Utilize the Duplicate Slide function when starting a new presentation instead of editing existing templates directly. Refer to the proper process for seamless layout and design preservation. For any inquiries, contact caesomc@uga.edu.
0 views • 13 slides
Internet Mail Architecture Components
The Internet mail architecture consists of key components including Message User Agents (MUA), Mail Submission Agent (MSA), Message Transfer Agent (MTA), Mail Delivery Agent (MDA), and Message Store (MS). These components work together to facilitate the sending, receiving, and storing of email messa
6 views • 4 slides
Mastering Email Communication: Layouts, Etiquette, and Best Practices
Dive into the world of email communication with this comprehensive guide covering email layouts, etiquette tips, common purposes, and general email format. Learn how to effectively structure your emails, address recipients, and maintain professionalism in your online correspondence.
0 views • 41 slides
Customize Your PAC Handbook for an Effective Parent Advisory Council
Customize this template PAC Handbook for your school by saving a duplicate copy, renaming it, and tailoring it to your PAC's needs. The handbook includes guidance on where to find existing PAC information and specific details on school operations. Explore various sections to streamline your role wit
0 views • 18 slides
Professionalism and Communication in the Digital Age
This presentation delves into the nuances of professionalism and effective communication in today's digital world, emphasizing the importance of email and social media etiquette. It explores topics such as managing perceptions, the myth of casual email, the value of business email, and the essential
0 views • 24 slides
UNDERSTANDING EMAIL,SPF,DKM,AND DMARC
Email infrastructure involves protocols like SPF, DKIM, DMARC, and SMTP to ensure secure and reliable communication. SMTP is used to transport emails between servers, while MTA acts as the mail transport agent. Understanding these components is crucial for effective email communication and troublesh
5 views • 14 slides
Essential Email Writing Guidelines and Etiquette
Understanding the importance of email writing, this guide covers the functions, advantages, and pitfalls of using emails. It delves into the reasons for the popularity of emails, common mistakes to avoid, and key principles for composing effective emails. Additionally, it provides insights into emai
0 views • 8 slides
Implementing Provisions of Agriculture Improvement Act of 2018: National Accuracy Clearinghouse Efforts
Efforts are underway to implement sections of the 2018 Agriculture Improvement Act related to the National Accuracy Clearinghouse (NAC) to prevent duplicate issuance of SNAP benefits across states. The NAC rule requires states to report recipient information, screen applicants against the NAC, and t
0 views • 8 slides
Insights on Lord Ganesh: Symbolism and Significance
Lord Ganesh, the remover of obstacles, holds significant attributes like his elephant face, one tusk, protruding belly, and more. Learn about the rituals, prayers, and festivals dedicated to this revered deity.
0 views • 9 slides
Mastering Email Management: Tips, Statistics, and Best Practices
Explore key insights and strategies for effective email management in the digital age. Discover email statistics, protocol etiquette, inbox management techniques, and insights on popular email platforms like Gmail. From understanding email distributions to implementing rules and filters, enhance you
0 views • 7 slides
Mastering Email Communication for Effective Interactions
Enhance your email communication skills by understanding the nuances of emotional intelligence, proper email etiquette, and effective email format. Learn how to craft compelling subject lines, avoid common email pitfalls, and tailor your tone based on recipients. Discover strategies for improved ema
0 views • 16 slides
Innovative Gadgets from AliExpress: Unbox & Explore New Tech Marvels
Uncover the latest innovative gadgets from AliExpress in a thrilling unboxing experience. From a mini microscope with impressive magnification to a revolutionary rivet adapter for power drills, discover cutting-edge devices like a flame torch for everyday use, staple-less paper binding solution, and
0 views • 6 slides
Email Campaigns in Internet Marketing
Email campaigns have transformed communication by allowing easy distribution of messages and documents worldwide within seconds. They can take various forms like direct emails, newsletters, and press releases. This chapter explores different types of email campaigns, including direct mail vs. direct
0 views • 25 slides
Mastering Email Communication in the Workplace
Dive into the intricacies of email communication in the workplace with insights on when to send emails, email etiquette, and valuable tips for composing effective professional emails. Understand the role of email in modern organizations, learn the do's and don'ts of email messaging, and enhance your
0 views • 32 slides
Email Technologies and Infrastructure
Explore the intricacies of email technologies, infrastructure, and architecture, including the format of HTTP messages, the role of proxy servers, creating web servers, and key components of email systems like user agents, mail servers, and SMTP protocol. Delve into email protocols like SMTP, POP3,
0 views • 38 slides
Email Security and Encryption Technologies Overview
Email security is crucial in today's digital world. This content discusses various email security measures, including PGP and S/MIME systems, and their utilization in business and personal communications. It also explores the history of PGP encryption, the role of Philip R. Zimmermann, and the chara
0 views • 10 slides
TrustVare Email Duplicate Remover Software For OST, PST, MSG, EML, and MBOX.
Using the TrustVare Email Duplicate Remover Software, you can simultaneously remove numerous emails in various formats. Bulk duplicate emails from OST, PST, MSG, EML, EMLX, MBOX, and NSF files can be easily deleted with this software. A free trial ve
5 views • 8 slides
Mastering Email Etiquette for Business Success
Enhance your professional image by mastering email etiquette. Learn how to represent your company well, write effective emails, use proper subject lines, address recipients professionally, and avoid common mistakes. Understand the importance of email security and when not to use email for sensitive
1 views • 32 slides
Identifying Redundancies in Fork-Based Development
Explore the challenges of redundant development in fork-based projects, such as duplicate pull requests, un-merged commits, and redundant feature implementations. Discover the impact of these redundancies on project maintenance, developer motivation, and overall efficiency. Learn about tools and str
0 views • 50 slides
The Fascinating Story of Lord Ganesh: Birth, Appearance, and Roles
Discover the intriguing tale of Lord Ganesh, the Elephant God in Hindu mythology. Born from Parvati's bath residue, Ganesh faced unique challenges and was blessed by Shiva with extraordinary powers. With a unique appearance and a role as the remover of obstacles and God of Good Luck, Ganesh holds a
0 views • 17 slides
Effective Email Strategies: Taming the Tiger
Strategies for managing email effectively are discussed in "Taming the Tiger: Strategies for Effective Use of Email," featuring insights from Elaine Shuck and Janine Lim. Tips include organizing emails into folders, using filters for newsletters and social media, and unsubscribing from listservs to
0 views • 25 slides
Deliverability and IP Warming in Email Marketing
Explore the concepts of deliverability and IP warming to improve your email marketing strategy. Learn about the importance of sender reputation, key factors affecting email delivery, and the methodology for warming up IP addresses. Discover how to establish a positive sender reputation and navigate
0 views • 15 slides
Four List Cleaning Methods Related to Reachability to Improve Email Reachability – Benchmark Email
Bulk Mail Masters specializes in efficient, high-impact bulk email marketing services. We help businesses grow by delivering personalized email campaigns at scale, boosting engagement, conversions, and brand visibility. Reach your audience with preci
0 views • 7 slides
Four List Cleaning Methods Related to Reachability to Improve Email Reachability – Benchmark Email
Bulk Mail Masters specializes in efficient, high-impact bulk email marketing services. We help businesses grow by delivering personalized email campaigns at scale, boosting engagement, conversions, and brand visibility. Reach your audience with preci
0 views • 7 slides
Four List Cleaning Methods Related to Reachability to Improve Email Reachability – Benchmark Email
Bulk Mail Masters specializes in efficient, high-impact bulk email marketing services. We help businesses grow by delivering personalized email campaigns at scale, boosting engagement, conversions, and brand visibility. Reach your audience with preci
0 views • 7 slides
Office 365 Email & Security Workshop Highlights
Office 365 Email & Security workshop was held with presenters Jason Hetterle, Steve Garcia, and Joseph Andreason covering topics like security awareness, self-service password reset, Office 365 webmail features, and more. The agenda included discussions on security measures, a case study on an anato
0 views • 9 slides
AI-Powered Tools Offered by MaxStudio.ai
https:\/\/www.maxstudio.ai\/object-remover\r\nMaxStudio.ai stands out due to its comprehensive suite of AI tools, each crafted to address specific editing needs. Below is an overview of its key offerings:\\n\\n1. AI Background Replacer\\nWhether you\\u2019re looking to add a professional backdrop fo
3 views • 5 slides
How to Choose the Perfect Makeup Remover Balm for Your Skin Type
A makeup remover balm has become a favorite among skincare enthusiasts due to its efficiency and skin-friendly properties. Unlike harsh cleansers, a cleansing balm not only removes makeup but also nourishes the skin, leaving it soft and refreshed.\n
0 views • 6 slides
Challenges of Running an Email Campaign Without DMARC (1)
Secure Your Email Campaigns Today\nDon\u2019t let the absence of a DMARC record hinder your email marketing efforts. Take control of your domain\u2019s security, enhance email deliverability, and safeguard your brand from fraud.\nSet up your DMARC re
2 views • 2 slides
Cleansing Makeup Remover BalmTips for Effective Use and Maximum Skincare Benefits
Makeup removal is a vital step in any skincare routine, and using the right products can make all the difference in maintaining healthy and glowing skin. One of the most effective ways to remove makeup without stripping the skin is by using a cleansi
0 views • 5 slides
Manage Duplicate Emails from MBOX with TrustVare MBOX Duplicate Remover Software
TrustVare MBOX Duplicate Remover Software is the best solution for removing multiple duplicate emails from MBOX files without a single error. This application can support various email clients like Thunderbird, Apple Mail, Eudora, Entourage, SeaMonke
1 views • 11 slides