Addressing 5G Signaling Protocol Vulnerabilities
The 8th meeting of the Communications Security, Reliability, and Interoperability Council to discuss and address security vulnerabilities in the newly adopted 5G signaling protocol, HTTP/2. Learn about potential risks, recommended safeguards, and the prevention of these vulnerabilities in the upcomi
3 views • 85 slides
Understanding Manufacturing Readiness Levels (MRLs) in Defense Technology
Manufacturing Readiness Levels (MRLs) are a vital tool in assessing the manufacturing maturity and associated risks of technology and products in defense acquisitions. They provide decision-makers with a common understanding of the maturity levels to support informed decisions throughout the acquisi
1 views • 12 slides
Army Rapid Capabilities and Critical Technologies Office Symposium 2023
LTG Robert A. Rasch, Jr., U.S. Army Director of Hypersonics, Directed Energy, Space, and Rapid Acquisition, presented updates on various defense projects at the Space and Missile Defense Symposium 2023. Topics included the Long Range Hypersonic Weapon program, Mid-Range Capability development, and D
5 views • 11 slides
Understanding Manufacturing Readiness Levels (MRLs) in Defense Acquisition
The Joint Defense Manufacturing Technology Panel (JDMTP) establishes Manufacturing Readiness Levels (MRLs) as a risk identification tool for assessing the manufacturing maturity, risks, and capabilities related to defense technology production. MRLs provide decision-makers with a common understandin
2 views • 14 slides
Future of Radiological and Nuclear Defense Programs and Capabilities
The Radiological and Nuclear Defense Capability Development Directorate discusses the responsibility for modernizing and procuring defense capabilities in the face of radiological and nuclear threats. The Department of Defense outlines strategic priorities to ensure the ability to survive and prevai
1 views • 10 slides
Understanding Vulnerabilities of Individuals with Autism in Disciplinary Hearings and Employment Tribunals
People with autism may face vulnerabilities in disciplinary proceedings and employment tribunals due to impaired theory of mind, communication difficulties, insistence on sameness, stereotyped behaviors, and sensory sensitivities. These challenges can lead to misunderstandings, difficulties in copin
0 views • 10 slides
Transforming NLP for Defense Personnel Analytics: ADVANA Cloud-Based Platform
Defense Personnel Analytics Center (DPAC) is enhancing their NLP capabilities by implementing a transformer-based platform on the Department of Defense's cloud system ADVANA. The platform focuses on topic modeling and sentiment analysis of open-ended survey responses from various DoD populations. Le
0 views • 13 slides
Essential Self Defense Tips and Techniques for Personal Safety
Explore the world of self-defense with insights from BJJ Black Belt Alex Vamos. Learn about physical and mental self-defense, enhancing awareness, important skills to master, assessing safety in hangout spots, and trusting your instincts to stay safe from potential threats.
3 views • 24 slides
Graduate School Defense Committee Guidelines
Comprehensive guidelines for thesis/dissertation defense committees at The Graduate School, SUNY ESF. Includes details on committee structure, purpose of defense, roles of members, scheduling, and more.
1 views • 15 slides
Understanding Unsoundness of Mind as a Defense in Law
The concept of unsoundness of mind as a defense in law is explored through principles of criminal liability and historical legal perspectives. The defense under Section 84 of the Indian Penal Code provides immunity for acts committed by individuals incapable of understanding the nature of their acti
1 views • 20 slides
Defense Presentation of "TITLE OF DISSERTATION" by Doctoral Candidate
This presentation features the defense process of a dissertation by a doctoral candidate, covering aspects such as the problem statement, theoretical framework, research questions, methodology, and findings. The defense includes committee introductions, dissertation presentation, audience questions,
0 views • 12 slides
Understanding Buffer Overflow Vulnerabilities in Programming
Buffer overflow vulnerabilities pose serious security threats by allowing attackers to execute arbitrary code on victim machines. This issue arises from overwriting memory in a way that manipulates the program's behavior. Learn about the dangers of buffer overflow bugs, how they can be exploited, an
2 views • 33 slides
Software Security Principles and Practices: Enhancing Program Code Security
Understanding and addressing critical web application security flaws like unvalidated input, cross-site scripting, buffer overflow, injection flaws, and improper error handling is crucial in enhancing the security of program code. The NIST report NISTIR 8151 provides valuable recommendations to redu
2 views • 44 slides
Understanding Computer Security and Software Vulnerabilities
Computer security, also known as cybersecurity or IT security, encompasses the protection of information systems from theft and damage. This overview delves into software security, control-flow attacks, memory vulnerabilities, and the historical impact of events like the Morris Worm. Various aspects
0 views • 53 slides
Understanding the Good Faith Personnel Action Defense in Workers' Compensation Cases
Exploring the application of the good faith personnel action defense in workers' compensation cases, examining relevant case law, factors for consideration by medical-legal evaluators and judges, and the Rolda v. Pitney Bowes, Inc. decision that established the analytical framework for this defense.
1 views • 36 slides
Overview of Global Farmed Salmon and Organic Production
The data showcases the production figures for global farmed salmon across various countries, with Norway leading the production, followed by Chile, Scotland, and others. Additionally, insights into the growing organic salmon production, vulnerabilities in the sector, and details on organic mussels p
0 views • 9 slides
Analysis of file:// Vulnerabilities in Android Browser Apps
The study delves into file:// vulnerabilities in Android browser apps, uncovering risks posed by the file:// URI scheme. It highlights how file:// requests can breach app data isolation, potentially compromising sensitive files. The research presents a unified attack model, FileCross automated testi
0 views • 22 slides
The Parasomnia Defense: Unusual Mental Health Defense in State v. Joseph A. Mitchell Case
The case of State v. Joseph A. Mitchell involves shocking events where Mitchell killed his son, attacked his daughter, and attempted suicide. The defense presented focuses on parasomnia, indicating Mitchell had no memory of the events due to a sleep disorder. Bizarre and odd facts, including Mitchel
4 views • 44 slides
Automated Detection of SSL Vulnerabilities in Applications
This research introduces SSLint, a systematic approach and automated tool for detecting incorrect SSL API usage vulnerabilities in applications. By analyzing millions of lines of code, the tool discovered previously unknown SSL/TLS vulnerable apps. The study addresses the motivation, problem stateme
0 views • 29 slides
Server-Side Technologies and Security Vulnerabilities in Mobile Services
This content delves into server-side technologies such as SQL, SOAP, JSON, and ReST used in mobile services, highlighting vulnerabilities that expose sensitive data. It emphasizes the importance of general web service security guidelines and discusses attacks against XML-based web services, outlinin
0 views • 52 slides
Understanding Blockchain Vulnerabilities to Quantum Attacks
Explore the vulnerabilities of blockchains to quantum attacks and the potential impact of quantum devices on blockchain technologies. Learn about key concepts such as blockchain basics, proof-of-work, quantum computing, quantum computing algorithms, and vulnerabilities like ECDSA and peer-to-peer ne
0 views • 23 slides
Understanding Security Threats and Vulnerabilities in Computer Systems
In computer security, threats exploit vulnerabilities to breach security and cause harm. Vulnerabilities arise from system weaknesses, attacker access, and capability. Threats include spoofing, data tampering, repudiation, information disclosure, denial of service, and elevation of privilege. Catego
0 views • 13 slides
Understanding Authentication Mechanisms and Security Vulnerabilities
Authentication lies at the core of application security, serving as the primary defense against malicious attacks. This article explores various authentication technologies, including HTML forms-based authentication, multi-factor mechanisms, client SSL certificates, and more. It delves into common d
0 views • 70 slides
Crafting Persuasive Defense Theories for Trial Success
Explore the art and science of cross-examination, theory development, and defense strategies in trial storytelling. Learn the essential components of a compelling defense theory, emphasizing factual, legal, and emotional aspects. Discover examples illustrating effective defense strategies for presen
0 views • 35 slides
Understanding the Importance of OWASP Dependency-Check Project
Explore the significance of OWASP Dependency-Check in managing software dependencies and mitigating known vulnerabilities in applications. Learn about the risks associated with using components with vulnerabilities and the challenges of patching programs. Discover how OWASP Dependency-Check provides
1 views • 26 slides
Data Disaggregation Taskforce: Assessment and Recommendations on Vulnerabilities
The Data Disaggregation Taskforce is conducting an assessment of current practices across sectors, assessing 10 sectors/clusters, 15 categories of affected populations, and identifying vulnerabilities in 17 categories. The Taskforce is working on harmonizing categories and finalizing recommendations
0 views • 6 slides
Cache-Based Attack and Defense on ARM Platform - Doctoral Dissertation Thesis Defense
Recent research efforts have focused on securing ARM platforms due to their prevalence in the market. The study delves into cache-based security threats and defenses on ARM architecture, emphasizing the risks posed by side-channel attacks on the Last-Level Cache. It discusses the effectiveness of si
0 views • 44 slides
Understanding Spectre and Meltdown Security Vulnerabilities
Spectre and Meltdown are two critical security vulnerabilities that exploit microarchitectural features to gain unauthorized access to memory. These vulnerabilities enable attackers to read memory that should be inaccessible, targeting branch prediction and exception handling mechanisms. Side channe
0 views • 19 slides
20th Annual Space and Missile Defense Symposium Agenda
The agenda outlines the schedule for the 20th Annual Space and Missile Defense Symposium held at the Von Braun Center in Huntsville, Alabama. It includes sessions with prominent speakers such as General John Hyten, General Lori Robinson, and Secretary of Defense James Mattis, covering topics like sp
0 views • 4 slides
Understanding Cloud Security Threats and Vulnerabilities
Explore the world of cloud security through the eyes of Dr. Liang Zhao, focusing on mobile security, WLAN security, and cloud threats. Learn about threat modeling, mitigating cloud vulnerabilities, and common threats such as data leakage, insecure interfaces, and more. Discover practical threat anal
0 views • 18 slides
Understanding Network Security Vulnerabilities and Attacks
Explore the world of network security vulnerabilities and attacks, including Denial-of-Service (DoS) and Distributed-Denial-of-Service (D-DoS), security flaws in the TCP/IP protocol suite, ICMP attacks, routing attacks, and TCP attacks. Learn about common security vulnerabilities such as address spo
0 views • 36 slides
Understanding Web Application Vulnerabilities in Information Warfare
Web application vulnerabilities such as Cross-Site Scripting, SQL Injection, and Broken Authentication pose significant risks in information warfare. Current solutions include Black-Box Security Testing and XSS Analyzers, but they have limitations like static verification and dependence on security
0 views • 21 slides
Understanding Programming Language Vulnerabilities and ISO/IEC/SC22/WG23
Explore the history and evolution of ISO/IEC/SC22/WG23 focusing on programming language vulnerabilities, led by Stephen Michell. Learn about the formation in 2006, publications, identified vulnerabilities, and the upcoming Edition 3 outlook with language-specific annexes. Discover comparisons with A
0 views • 15 slides
Basic Web Security Model for Secure Electronic Commerce
This presentation covers the basic web security model for secure electronic commerce, focusing on vulnerabilities such as XSS and SQL injection. It discusses the decline in web vulnerabilities since 2009 and explores reported web vulnerabilities. The course theme includes topics like web application
0 views • 38 slides
Sustainable Procurement Practices in Defense Department
Sustainable procurement practices play a crucial role in the Defense Department, focusing on reducing emissions, enhancing eco-labeling, and promoting administrative cooperation. Initiatives such as reciprocal defense procurement agreements and memoranda of understanding with qualifying countries co
0 views • 85 slides
Understanding Spectre and Meltdown Security Flaws
Recent security vulnerabilities named Spectre and Meltdown have surfaced in the realm of computer architecture and hardware implementation. These flaws allow attackers to access sensitive data through covert channels utilizing speculative execution mechanisms. The vulnerabilities exploit the perform
0 views • 12 slides
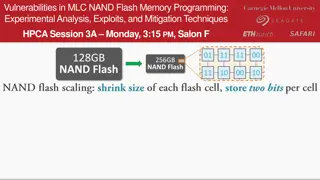
Experimental Analysis of Vulnerabilities in MLC NAND Flash Memory Programming
This session at HPCA explores the experimental analysis, exploits, and mitigation techniques related to vulnerabilities in MLC NAND flash memory programming. The presentation delves into the risks associated with NAND flash memory, such as data corruption and errors during read operations. It discus
0 views • 10 slides
Defense Cost Reporting and Systems Overview
Defense Cost Analysis and Reporting Systems (CSDR) provide the cost community with essential data for developing independent cost estimates within major defense acquisition programs. The Defense Automated Cost Information Management System (DACIMS) offers instant access to historical cost informatio
0 views • 19 slides
Understanding the Impact of Section 889 on Defense Industrial Base
Section 889, passed as part of the 2019 NDAA, restricts the US government from contracting with entities using certain telecommunications and video surveillance equipment. It aims to strengthen the defense supply chain by prohibiting direct procurement or contracts with entities utilizing covered eq
0 views • 17 slides
Defense Outlook Unveiling Growth Potential and Forecasted Outlook for 2023-2033
The global defense outlook showcases the defense budget of 30 countries for the period 2023-2033. The cumulative defense budget is valued to be $29,031.67 billion for the period 2023-2033.\n\nRead Report Overview: \/\/bisresearch.com\/industry-report
1 views • 3 slides