System Modeling and Simulation Course Overview
This course covers the basics of systems modeling, discrete-event simulation, and computer systems performance evaluation. Topics include Monte Carlo simulation, probability models, simulation output analysis, queueing theory, and more. Professor Carey Williamson leads the course with a focus on pra
4 views • 21 slides
Overview of Army Modeling and Simulation Office
The U.S. Army Modeling and Simulation Office (AMSO) serves as the lead activity in developing strategy and policy for the Army Modeling and Simulation Enterprise. It focuses on effective governance, resource management, coordination across various community areas, and training the Army Analysis, Mod
1 views • 8 slides
Simulation-Based Training for Diabetes Care in Nursing
This simulation program, SCENS, focuses on enhancing nursing skills in managing diabetes-related complications such as hyper/hypoglycemia. The learning objectives include assessment, safe care provision, insulin administration, and effective communication. The simulation addresses the significant im
0 views • 17 slides
Colorado Alliance of Research Libraries: MARC Record Matching System Overview
Designed and hosted by the Colorado Alliance of Research Libraries, the Gold Rush Analytics Technical Overview showcases a cost-effective system utilizing open-source software with tailored solutions. The Matching MARC section details the methodology for matching records, emphasizing the pre-built m
1 views • 10 slides
How to Check a Simulation Study: Methods and Considerations
Simulation studies are often used to evaluate statistical methods and study power, but they can sometimes produce misleading results. This work discusses strategies to assess and improve the quality of simulation studies, drawing on experiences and considerations outlined in relevant literature. A s
0 views • 31 slides
Understanding Monte Carlo Transport Simulation
Monte Carlo simulation is a stochastic technique that uses random numbers and probability statistics to investigate and solve problems. In the context of transport simulation, a Monte Carlo program simulates the passage of particles through matter, involving geometry, transport, visualization, detec
0 views • 11 slides
System Modeling and Simulation Overview
This content provides insights into CPSC 531: System Modeling and Simulation course, covering topics such as performance evaluation, simulation modeling, and terminology in system modeling. It emphasizes the importance of developing simulation programs, advantages of simulation, and key concepts lik
0 views • 28 slides
Entity Resolution Problem in Customer Data Matching
The challenge of entity resolution, especially in the context of matching customer data between companies, is addressed in this content. The scenario involves accurately identifying which records correspond to the same individuals despite potential variations or errors in the data. Strategies such a
1 views • 56 slides
Basin Manipulation Simulation Analysis Tool Overview
Basin Manipulation Simulation Analysis Tool provides a comprehensive solution for managing and analyzing basin data, including tasks like basin manipulation, simulation analysis, case management, and defining simulation time steps. The tool allows for easy data entry, visualization of simulation res
2 views • 17 slides
Engaging English Lesson for Second Graders - Alphabet Learning and Word Matching
Engage young learners in an interactive English lesson focusing on alphabet recognition and word-object matching. The Head Teacher leads students at Jagotpur Government Primary School through fun activities like singing the alphabet song, identifying objects by initial sounds, and matching words wit
0 views • 16 slides
Enhancing Long-Term Fostering Matching Process for Social Care Teams
This presentation outlines the long-term fostering matching process in March 2023 by South Gloucestershire Council. It emphasizes the importance of understanding and following the process for Service Managers, Team Managers, and new starters in Social Care. The responsibilities of staff in ensuring
3 views • 19 slides
Classroom Connectivity Initiative in Texas: E-rate and State Matching Fund Process
The Classroom Connectivity Initiative in Texas outlines how E-rate and State Matching funds work to make telecommunications and information services more affordable for schools and libraries. With federal E-rate discounts ranging from 20% to 90%, and state matching funds providing dollar-for-dollar
0 views • 9 slides
Achieving Impedance Matching for TRF79xxA Single Receive Channel Using L Network: Calculations and Simulation
This content discusses the process of achieving impedance matching for a single receive channel in TRF79xxA devices, which operate with a 50-ohm antenna. The calculations involve determining the Q values of the legs, calculating reactances, and deriving the required values for L and C components. Si
1 views • 19 slides
Simulation Training in Education: Enhancing Learning Through Hands-On Simulation
Hands-on simulation training in education provides students with valuable learning experiences by increasing self-reported knowledge and technical proficiency. Simulations help improve students' knowledge, experience, and comfort with challenging procedures in a lower-risk environment, leading to en
0 views • 13 slides
Understanding Computer Simulation and Modeling Tools
Computer simulation and modeling is essential for conducting studies in various fields. Selecting the right simulation language or package is crucial for accurate results. This involves considering the characteristics of the language, such as random number generation, process transformers, list proc
0 views • 7 slides
Challenges in Data Integration: Heterogeneity and Solutions
Data integration faces challenges such as value heterogeneity, instance heterogeneity, and structure heterogeneity. Existing solutions assume independence of data sources and utilize methods like data fusion, truth discovery, string matching, object matching, schema matching, and model management. T
0 views • 5 slides
Advanced Beam Dynamics and Machine Protection in High-Energy Linacs
Overview of recent talks and discussions at LCWS 2014 in Belgrade, Serbia, focusing on machine protection, simulation codes, instrumentation, and system tests. Topics include beam-loss monitors, dark current measurements, simulation code developments, and beam dynamics studies in linacs. Key speaker
0 views • 12 slides
Enhancing Matching Gift Strategies for Nonprofits
Explore a comprehensive roadmap for maximizing matching gift opportunities provided by Double the Donation. This presentation covers important steps such as determining donor information, evaluating revenue, and setting timelines for success. Learn how to identify responsible departments and individ
0 views • 10 slides
Enhancing Healthcare Simulation Through Constructive Feedback
Explore the principles and benefits of healthcare simulation, focusing on formative evaluation and constructive feedback to improve learning outcomes. Delve into the role of formative assessment tools, TeamSTEPPS model, and Mayo High Performance Teamwork Scale in simulation scenarios. Discover the s
0 views • 37 slides
Beam Polarization Simulation Study for CEPC
Simulation study on beam polarization for the Circular Electron Positron Collider (CEPC) using the PTC Poly- morphic Tracking Code. The study includes orbital and spin tracking, equilibrium polarization calculation, and Monte-Carlo simulation of depolarization rate. Comparison with other Monte-Carlo
0 views • 20 slides
Gender Wage Gap Among Those Born in 1958: A Matching Estimator Approach
Examining the gender wage gap among individuals born in 1958 using a matching estimator approach reveals significant patterns over the life course. The study explores drawbacks in parametric estimation, the impact of conditioning on various variables, and contrasts with existing literature findings,
0 views • 18 slides
New Pattern Matching Algorithms for Network Security Applications by Liu Yang
Discusses new pattern matching algorithms for network security applications, focusing on intrusion detection systems (IDS) and the use of signatures and regular expressions to detect malicious patterns in network traffic. Explores the ideal and reality of pattern matching, time-space tradeoffs, and
0 views • 57 slides
Introduction to VLSI CAD and Discrete-Event Simulation at Tufts University
This course introduces students to event-oriented simulation, building virtual models, and validating designs through simulation. It covers the importance of simulation in testing and refining designs before implementation. Examples include simulating VLSI networks and exploring the use of discrete-
0 views • 32 slides
Graph Pattern Matching Challenges and Solutions
Graph pattern matching in social networks presents challenges such as costly queries, excessive results, and query focus issues. The complexity of top-k and diversified pattern matching problems requires heuristic algorithms for efficient solutions. Finding best candidates for project roles involves
0 views • 19 slides
Understanding Matching Keys in Database Systems
Matching keys play a crucial role in identifying the same real-world entities in database systems. They specify which attributes to compare and how to compare them, helping minimize redundancy and improve data accuracy. This summary discusses relative candidate keys, minimal matching keys, and relia
0 views • 13 slides
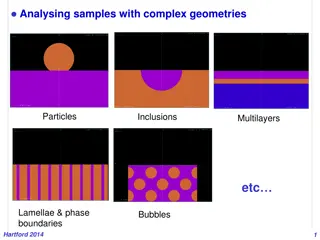
Advanced Simulation Techniques for Analyzing Samples with Complex Geometries
Explore the capabilities of PENELOPE simulation software for analyzing samples with intricate structures like particles, inclusions, multilayers, lamellae, and phase boundaries. The software facilitates detailed investigations of material composition and electron-photon transport in diverse geometri
0 views • 28 slides
Stable Matching Problem and Gale-Shapley Algorithm Overview
The content provides information on the stable matching problem and the Gale-Shapley algorithm. It covers the definition of stable matching, the workings of the Gale-Shapley algorithm, tips for algorithm implementation, and common questions related to the topic. The content also includes a summary o
0 views • 16 slides
Understanding Stable Matching and Secretary Problem in Algorithms
This tutorial explores stable matching and the secretary problem in the context of algorithm design and analysis. It covers concepts such as perfect matching in bipartite graphs, preference lists, blocking pairs, and the existence and methods of finding stable matchings. The content delves into scen
0 views • 30 slides
Simulation Design for Authentic Learning and Assessment at ACU
Simulation design for authentic learning and assessment is a crucial aspect of education, particularly in the healthcare field. At the Australian Catholic University (ACU), simulation plays a significant role in providing students with authentic experiences that bridge the gap between theory and pra
0 views • 18 slides
The Right Way to Code Simulation Studies in Stata
Simulation studies in Stata involve using (pseudo) random numbers to generate data from a distribution for studying statistical methods. This process helps to evaluate different scenarios and understand the properties of statistical techniques. Key components like ADEMP (Aims, Data-generating mechan
1 views • 18 slides
Simulation Results for LC-Optimized PHY Proposal in July 2019
The document presents simulation results for an LC-optimized PHY proposal for TGbb based on G.9991 PHY. It includes details on the simulation setup, frame detection results, header modulation, coding simulation results, payload modulation, and coding simulation results. The setup involved various re
0 views • 18 slides
Fundamentals of Computer Vision and Image Processing
Fundamentals of computer vision cover topics such as light, geometry, matching, and more. It delves into how images are recorded, how to relate world and image coordinates, measuring similarity between regions, aligning points/patches, and grouping elements together. Understanding concepts like shad
0 views • 29 slides
Thermoelectric Module with PID Control Simulation
This simulation showcases a lumped thermoelectric module with PID control. The model evaluates the performance of a thermoelectric element in a nonisothermal fluid flow around a heat sink. A stationary simulation assesses the module's capabilities, followed by a transient simulation with a PID contr
0 views • 7 slides
Defense Modeling and Simulation Coordination Office Overview
The Defense Modeling and Simulation Coordination Office (DND/CAF MSCO) is responsible for managing contractors, policies, and strategic activities related to modeling and simulation within the Canadian Armed Forces. The office focuses on supporting various organizations and enhancing capabilities th
0 views • 6 slides
Understanding Stable Matching and Orderly Markets in Various Allocation Systems
Exploring the concept of stable matching and orderly markets in different allocation systems such as medical residencies, law clerk placements, and college admissions. From theory to practice, the history of the National Residency Matching Program (NRMP) to centralized clearinghouses, the importance
0 views • 36 slides
Aerodynamic Simulation of MARINTEK Braceless Semisubmersible: Insights and Tools
Explore the aerodynamic simulation of the MARINTEK Braceless Semisubmersible through advanced techniques and tools. Discover the unique aerodynamic actuator, simulation models, and tools used in the research conducted by Gordon Stewart, a post-doctoral researcher at NTNU. Gain insights into the expe
0 views • 16 slides
Specialization in International Business Communication (SIBC)
Specialization in International Business Communication (SIBC) offered by the Department of Business Communication focuses on the critical role of communication in various business settings, emphasizing skills in language usage, communicative competence, and strategic language application. The progra
0 views • 11 slides
Comparison of GLM-16 and GLM-17 with WWLLN Strokes
The report by Robert Holzworth and Michael McCarthy discusses the comparison of GLM-16 and GLM-17 with WWLLN strokes, highlighting areas of agreement and disagreement. Methods for matching GLM and WWLLN events are explored, focusing on time and distance considerations. The analysis shows that NOAA-1
0 views • 16 slides
Enhancing OpenStreetMap with Crowdsourced Turning Restrictions
Abundance of GPS tracking data has led to significant research on map-matching algorithms and identifying turning restrictions. This study focuses on inferring turning restrictions for OpenStreetMap data by utilizing historic map-matching results effectively. Understanding and implementing turning r
0 views • 25 slides
Understanding Simulation Types for Ecosystem Modeling
Exploring different simulation types such as continuous and discrete event simulations for modeling complex systems like ecosystems. Detailed discussion on creating an ecosystem simulation with fish and bears on a grid, showcasing actions like breeding, moving, eating, and dying. Overview of a World
0 views • 31 slides