2022 Thales Access Management Index
Thales Access Management Index highlights the current landscape of access security, revealing insights on multi-factor authentication adoption, remote and privileged user access management, VPN usage trends, challenges faced, and preferences towards third-party access management. The report emphasiz
2 views • 9 slides
Personnel Safety Systems and Access Control at CERN Facilities
Personnel Safety Systems at CERN include ODH detection, fire safety measures, and access control to protect personnel from hazards. Various access control layers are implemented to regulate entry to different parts of the facility, ensuring only trained personnel access underground areas. Biometric
0 views • 19 slides
Understanding Narcotic Analgesics and Opiates: History, Mechanisms, and Uses
Delve into the world of narcotic analgesics and opiates, exploring the history of opium poppy, morphine derivatives, opioid compounds, and the pharmacology mechanisms of action. Discover the uses of opiates in analgesia, preanesthetic medication, and more, alongside the endogenous ligands involved.
8 views • 55 slides
Advancements in Chemical Mechanisms for Air Quality Management
Daniel Jacob and team have been enhancing chemical mechanisms in the GEOS-Chem model to support US air quality management. Ongoing work includes developing new mechanisms for aromatic VOCs, tropospheric halogens, mercury redox, adaptive mechanism reduction, machine learning applications, and unifica
0 views • 19 slides
Kinematics of Machines: Instantaneous Center Method for Velocity and Acceleration Analysis
Explore the method of locating instantaneous centers in mechanisms to analyze velocity and acceleration. The content covers examples of pin-jointed four-bar mechanisms and slider-crank mechanisms, providing dimensions and angular velocities calculations. Prof. Divyesh B. Patel from L.E. College, Mor
0 views • 13 slides
Understanding Plasmid Partitioning Mechanisms in Bacteria
The stable maintenance of low-copy-number plasmids in bacteria relies on partition mechanisms that ensure proper positioning during cell division. Different from high-copy-number plasmids, which rely on random diffusion, low-copy-number plasmids require regulated partitioning mechanisms to prevent d
0 views • 14 slides
Port of Stockton Restricted Area Access Control and ID Card Policy
Access to restricted areas at the Port of Stockton facilities requires possession of a TWIC (Transportation Worker Identification Credential). Only authorized personnel, such as employees, contractors, and those with regular access, may receive a Port Access Card after approval by the Facility Secur
0 views • 6 slides
Understanding Metabolic Control Mechanisms in Cellular Regulation
Metabolic control mechanisms play a crucial role in maintaining homeostasis within cells by regulating metabolic pathways. This involves finely adjusting the output of pathways in response to external signals, ensuring the proper flux of metabolites to meet cellular needs. Pacemaker enzymes, such as
1 views • 17 slides
Overview of Organic Reactions and Mechanisms
Organic reactions can be categorized into addition, elimination, and substitution reactions, occurring through either polar or free radical mechanisms. Polar reactions may be electrophilic or nucleophilic, while free radical reactions involve radicals reacting to complete electron octets. Different
2 views • 26 slides
Understanding Prezygotic Reproductive Isolating Mechanisms
Prezygotic reproductive isolating mechanisms prevent mating or fertilization between different species before it can occur. Examples include habitat isolation, behavioral isolation, and temporal isolation. These mechanisms play a significant role in maintaining species integrity and preventing the f
0 views • 4 slides
Fuel Pricing Mechanisms and Regulatory Framework Presentation
This presentation to the Portfolio Committee on Mineral Resources and Energy delves into the Basic Fuel Price (BFP) for liquid fuels, covering global fuel pricing forms, policy positions, key pricing mechanisms, regulatory mandates, and the intricate structure behind fuel prices. It explains how the
2 views • 28 slides
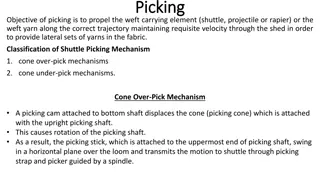
Understanding Shuttle Picking Mechanisms in Weaving
Shuttle picking mechanisms play a crucial role in propelling the weft carrying element to maintain the required trajectory and velocity in fabric weaving. Two common mechanisms are cone over-pick and cone under-pick, each offering unique adjustments for strength and timing. The cone over-pick involv
0 views • 14 slides
Exploring Defense Mechanisms in Personality Structure
In "Understanding Personality Structure in the Clinical Process" by Nancy McWilliams, various defense mechanisms are illustrated through real-life examples. These mechanisms include primitive withdrawal, denial, omnipotent control, idealization and devaluation, and projection with projective identif
1 views • 29 slides
Introduction to Database Security and Countermeasures
Database security is essential to protect data integrity, availability, and confidentiality. Countermeasures such as access control, inference control, flow control, and encryption can safeguard databases against threats. Access control restricts user access, inference control manages statistical da
0 views • 26 slides
Understanding Host Defense Mechanisms Against Infection
Host defense mechanisms safeguard the body from pathogens through various strategies such as intact skin, mucous membranes, nonspecific immune responses like phagocytic cells, and specific immune responses involving antibodies and lymphocytes. Key protective barriers include the skin, eyes, digestiv
3 views • 16 slides
Understanding CBE's Revised IDoW Policy for Regulatory Mechanisms
This presentation by the Council for the Built Environment (CBE) outlines the Identification of Work (IDoW) Policy, elucidating key regulatory mechanisms, acronyms, definitions, and the role of the CBE in implementing and evaluating such mechanisms in the built environment sector. The purpose is to
0 views • 28 slides
Mechanisms of Nutrient Uptake by Microbial Cells
Nutrient uptake by microbial cells involves various transport mechanisms such as passive diffusion, facilitated diffusion, active transport, and group translocation. These mechanisms ensure the specific acquisition of required nutrients by the cell through the selectively permeable plasma membrane.
3 views • 15 slides
Understanding Plasmids: DNA Molecules Free of Chromosome
Plasmids are DNA molecules existing free of the chromosome in a cell. They can be circular or linear and carry genes beneficial to the host. Plasmids replicate from unique origins and regulate copy numbers through various mechanisms. Different replication mechanisms, such as theta and RC, are used,
0 views • 31 slides
Enhancing Grievance Mechanisms in EITI: 40th Board Meeting Insights
Explore the presentation of existing grievance mechanisms at the 40th EITI Board Meeting in Berlin. Discussions centered around whether current procedures meet governance requirements and the potential establishment of new mechanisms. Findings highlighted the need for improved clarity, stakeholder u
0 views • 6 slides
Sports-related Injuries and Mechanisms
This content discusses various sports-related injuries and their mechanisms, including shin splints, foot fractures, ankle sprains, and Achilles tendonitis. Each injury is described with its signs and symptoms, along with the mechanisms that caused them. The injuries range from stress fractures in t
1 views • 105 slides
Understanding the Inversion of Mechanisms in Kinematics
Inversion of Mechanisms in Kinematics involves measuring absolute and relative motions in stationary and moving frames, respectively. By fixing different links in a kinematic chain, we can obtain various mechanisms. This process does not alter relative motions but may significantly change absolute m
0 views • 78 slides
Safeguarding Focal Point Training: Enhancing Reporting and Response Mechanisms
This training module focuses on empowering Safeguarding Focal Points (SFPs) to understand and implement community-based feedback and response mechanisms, effectively handle safeguarding complaints, document barriers to reporting, address data protection issues, and ensure inclusive and confidential
0 views • 18 slides
Understanding Authentication Mechanisms and Security Vulnerabilities
Authentication lies at the core of application security, serving as the primary defense against malicious attacks. This article explores various authentication technologies, including HTML forms-based authentication, multi-factor mechanisms, client SSL certificates, and more. It delves into common d
0 views • 70 slides
Open Access at Charles University: Opportunities and Challenges
Charles University is navigating the landscape of open access following the implementation of the Czech National Open Access Strategy. The university is working towards making all research articles and proceeding papers open access, monitoring article processing charges, and promoting open access as
0 views • 24 slides
Understanding Ethernet and Multiple Access Protocols in Computer Networks
Exploring the fundamentals of Ethernet and multiple access protocols in computer networks, this content discusses the two primary categories of multiple access protocols - contention access and controlled access. It delves into topics such as CSMA/CD, LANs, performance of multiple access schemes, ad
0 views • 7 slides
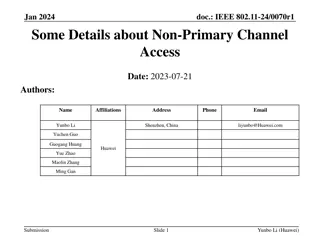
IEEE 802.11-24/0070r1 Presentation on Non-Primary Channel Access
This presentation discusses the concept of using secondary channels for PPDU transmission in IEEE 802.11 networks to improve efficiency in large bandwidth scenarios. It covers topics such as channel access, backoff mechanisms, and channel switching thresholds. Design principles emphasize minimal imp
0 views • 15 slides
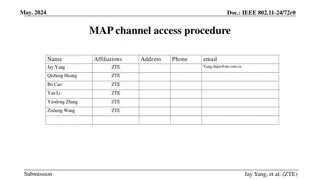
Proposed MAP Channel Access Procedures in IEEE 802.11-24/72r0
In the May 2024 document IEEE 802.11-24/72r0, a uniform MAP coordination framework is discussed, involving procedures like M-AP discovery, coordinated transmissions, and channel access mechanisms. All APs in a coordination group can compete for channel access and share transmission opportunities. Th
0 views • 10 slides
Insights from ASTA.V&F Seed Conference 2015 on Nagoya Protocol & ABS Mechanisms
The ASTA.V&F Seed Conference 2015 shed light on the insufficiencies in the Access and Benefit Sharing (ABS) provisions within the Convention for Biological Diversity (CBD), leading to the necessity of the Nagoya Protocol (NP) in 2010. The NP aims to regulate access to genetic resources and tradition
0 views • 9 slides
Overview of Human Rights Monitoring Mechanisms
Human rights conventions under the United Nations and regional systems have established monitoring mechanisms to ensure compliance. These mechanisms include treaty-based and non-treaty-based approaches, with treaty bodies overseeing the implementation of legally binding instruments. Reporting proced
0 views • 23 slides
Improved Truthful Mechanisms for Subadditive Combinatorial Auctions
This research paper discusses strategies to maximize welfare in combinatorial auctions. It explores mechanisms for handling strategic bidders with private valuations, aiming to design truthful and optimal welfare mechanisms while considering polytime constraints. The study presents advancements in a
0 views • 19 slides
Understanding Computer System Protection and Security
Mechanisms like protection and security ensure controlled access to a computer system's resources and prevent malicious activities. Protection involves defining access control levels through models, policies, and mechanisms. Security focuses on user authentication to safeguard stored information. Di
0 views • 25 slides
Harvard Chan School 2021 Yearly Access Review Process
The Harvard Chan School conducts its annual Yearly Access Review (YAR) process to review user access to various financial systems. The process involves assessing permissions, levels of access, and organizational details for each team member. Instructions are provided on reviewing worksheets, adding
0 views • 19 slides
Understanding Security Access in PeopleSoft Finance
Explore the various levels of security access in PeopleSoft Finance, from basic entry access to transaction entry, approvals, and procurement processes. Learn how to request individual and department security access and find relevant forms on the financial services website. Discover the different ty
0 views • 11 slides
Understanding Carnegie Mellon's Protection and Security Concepts
Carnegie Mellon University emphasizes the importance of protection and security in operating systems. Protection involves preventing unauthorized access by users, while security focuses on external threats and authenticating system users. The goals of protection include preventing access violations
0 views • 37 slides
Facilitating Development of Innovative Drug Formulations and Delivery Mechanisms: The Role of Medicines Patent Pool
The presentation by Charles Gore, Executive Director of Medicines Patent Pool, at IAS 2019 discussed how the MPP works to ensure future access to innovative drug formulations and delivery mechanisms. The MPP model involves negotiating public health-driven licenses with patent holders, sublicensing t
0 views • 16 slides
Understanding Biomarkers and Toxicity Mechanisms: Overview of Mechanisms in Targeting Biological Macromolecules
This overview delves into different categorizations of mechanisms of action (MoA) based on target molecules, interaction types, and steric specificity. It explores non-specific and specific mechanisms, along with possible categorizations involving membrane toxicity, reactive toxicity, and species-sp
0 views • 8 slides
Understanding Coping Skills and Defense Mechanisms
Coping mechanisms and defense mechanisms are strategies individuals use to manage stress and emotions. Coping mechanisms help people adjust to difficult events while maintaining emotional well-being, whereas defense mechanisms operate at an unconscious level and can change internal psychological sta
0 views • 18 slides
Database Access Control & Privacy: A Common Ground Explored
Exploring the intersection of database access control and data privacy, this paper delves into the implications of data privacy concerns on Database Management Systems (DBMS). It discusses the need for more than just access control mechanisms and highlights the evolving landscape of data publishing,
0 views • 29 slides
Defense Mechanisms in Psychology: Understanding Repression, Displacement, Intellectualization, Rationalization
Defense mechanisms play a crucial role in how individuals cope with stress and anxiety. This text delves into key defense mechanisms such as repression, displacement, intellectualization, and rationalization. These mechanisms help individuals manage unacceptable thoughts, feelings, and impulses by r
0 views • 11 slides
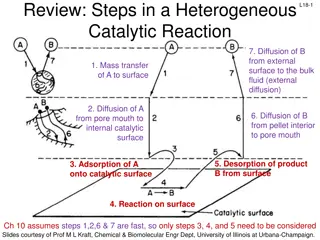
Understanding Steps in Heterogeneous Catalytic Reactions and Adsorption Mechanisms
This review discusses the steps involved in a heterogeneous catalytic reaction, focusing on diffusion, mass transfer, adsorption, and desorption processes. It details the site balance, surface reaction mechanisms, and desorption steps, providing insights into the complexities of catalytic processes.
0 views • 17 slides