Adaptive Tree-based Convergecast Protocol
Adaptive tree-based protocol for managing overlay networks in heterogeneous networks. It proposes improvements to the existing Tree-Based Convergecast Routing (TBCR) protocol by considering additional parameters such as RTT, power consumption, link stability, and link mobility to optimize routing de
32 views • 12 slides
Understanding Transfer Pricing in Organizational Decision Making
Explore the concept of transfer pricing in organizational decision-making, including factors affecting transfer prices, objectives of transfer pricing, and how it influences the autonomy and profitability of responsibility centers. Learn about different bases for setting transfer prices and examples
0 views • 13 slides
Introduction to SFTP & PGP Encryption for Secure Data Transfer
Discover how to ensure reliable data transfer, make informed decisions, and gain a strategic advantage through the use of Secure File Transfer Protocol (SFTP) and Pretty Good Privacy (PGP) encryption. The session includes demonstrations on PGP encryption and SFTP access, along with insights on setti
1 views • 22 slides
Understanding OSI Model and TCP/IP Protocol Suite
Explore the concept of layering in data communication, comparing the OSI model and TCP/IP protocol suite. Learn about protocol layers, protocol hierarchies, and the functionality of each layer in these models. Discover the interrelationships between layers and the evolution from OSI to TCP/IP.
5 views • 57 slides
Doctrine of Election under Section 35 of the Transfer of Property Act, 1882
The doctrine of election under Section 35 of the Transfer of Property Act, 1882 deals with situations where a person professes to transfer property he does not own, and the owner must elect to confirm or dissent. If the transfer is gratuitous and the transferor is unable to make a fresh transfer, th
5 views • 17 slides
Introduction to Unix-like Systems and Shell Interaction
Unix-like systems, such as Linux, Android, iOS, and macOS, are prevalent in various devices. The Unix shell acts as an intermediary between users and the operating system, allowing for program execution and process management. Secure Shell (SSH) and X Window System enable remote machine connections
4 views • 19 slides
London Homeless Coalition (LHC) Death Communication Protocol
In 2014, the Memorial Committee of the London Homeless Coalition (LHC) established the Death Communication Protocol to acknowledge, share, and address the loss of individuals experiencing homelessness. The protocol aims to inform partnering organizations of confirmed or unconfirmed deaths, support g
0 views • 12 slides
Update on Forward Capacity Auction 18 Transmission Transfer Capabilities
This update covers the progress and developments surrounding the Forward Capacity Auction 18 (FCA 18) transmission transfer capabilities, Capacity Zone Development, and ongoing analyses in New England's power system. The ISO-NE has been actively reviewing interface transfer capabilities, discussing
1 views • 25 slides
Understanding Mobile Computing and TCP/IP Protocol Suite
Mobile computing is crucial for continuous internet connectivity regardless of physical location. The TCP/IP protocol suite, consisting of Transmission Control Protocol (TCP) and Internet Protocol (IP), forms the backbone of internet infrastructure. IP addressing and mobility challenges are addresse
1 views • 51 slides
Understanding OSI Model and TCP/IP Protocol Suite in Computer Networking
This chapter explores the OSI model and TCP/IP protocol suite, delving into protocol layers, addressing mechanisms, and network components. It highlights the interface between layers, functions of each layer in the OSI model, and compares TCP/IP protocol suite layers with OSI model layers. The discu
0 views • 30 slides
MAAP Protocol Overview in IEEE 1722: Address Acquisition and Message Format
The MAAP (Multicast Address Acquisition Protocol) is defined in IEEE 1722 for time-sensitive applications in bridged local area networks. It involves acquiring multicast addresses through claiming, probing, and defending messages. MAAP enables dynamic allocation of addresses and defending against co
1 views • 8 slides
IEEE 802.11-20/1761r1 Ranging Protocol for 11bd
This document outlines the ranging protocol proposed for IEEE 802.11-20/1761r1, focusing on RTT-based ranging leveraging multi-channel operation. By integrating the 11az ranging protocol, it enables flexible and low-overhead application in 11bd for improved accuracy in ITS bands. The protocol includ
1 views • 13 slides
Understanding Transfer of Learning: Types and Examples
Transfer of learning refers to the carry-over of habits, knowledge, or skills from one area to another. This process influences performance in various situations, as seen in positive and negative transfer examples. Various definitions and types of transfer learning are explored in this special lectu
0 views • 21 slides
Understanding Heat Transfer in Engineering Applications
This content covers various aspects of heat transfer in engineering, including calculations for thermal resistances, heat transfer between different surfaces and mediums, and practical applications such as heat transfer in pipes, plates, and spheres. It also includes review questions involving heat
0 views • 8 slides
Understanding EIGRP: A Comprehensive Overview
Enhanced Interior Gateway Routing Protocol (EIGRP) is a dynamic routing protocol providing various advantages to network administrators. It is a classless routing protocol supporting VLSM and is considered an Interior Gateway Protocol (IGP). EIGRP uses advanced distance vector routing and is known f
1 views • 5 slides
Understanding SFTP Server Functionality with ACS 5.x by Mohammad Azharuddin AAA Team
SFTP (SSH File Transfer Protocol) is a secure network protocol for file access, transfer, and management over reliable data streams. It enhances security by extending the SSH protocol and can be implemented using a reliable 8-bit byte stream protocol. SFTP commands are sent as 4 ASCII letters follow
4 views • 23 slides
Enhanced Family Court Police Disclosure Protocol for 2024
The 2024 Family Court Police Disclosure Protocol addresses key issues identified in the 2013 protocol, emphasizing timely and proportionate requests for material. Changes include a new checklist for the judiciary, guidance notes, and revised processes for litigants in person. The protocol provides c
1 views • 19 slides
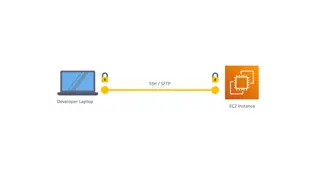
Development Process Using SSH, SFTP, EC2 Instances, and Autoscaling Groups
Exploring the development workflow involving SSH, SFTP, EC2 instances, and Autoscaling Groups for code merging, building, and releasing applications in the cloud environment using technologies like Amazon Elastic Container Service (ECS). The images provide insights into setting up developer laptops,
0 views • 5 slides
Essential Elements of Clinical Trial Protocols
Understanding the key components of a clinical trial research protocol is essential for conducting successful studies. This includes identifying session objectives, discussing trial protocol contents, exploring observational study elements, and learning about reporting guidelines. Study objectives f
1 views • 25 slides
Ohio Department of Higher Education and Transfer Initiatives
Ohio Department of Higher Education focuses on transfer initiatives like Transfer Guarantees, Advanced Placement, CLEP Credits, Guaranteed Transfer Pathways, and more to help Ohioans achieve postsecondary credentials by 2025. They offer Transfer Modules, Transfer Assurance Guides, and Career-Technic
0 views • 20 slides
Understanding File Transfer Protocols in Networking
Explore the fundamental concepts of File Transfer Protocol (FTP) in networking, covering its architecture, operation, commands, security considerations, and a comparison with Secure File Transfer Protocol (SFTP). Gain insights into how FTP enables the transfer of files between client and server, inc
0 views • 33 slides
Understanding C++ File I/O Operations
Learn about C++ file I/O operations, including input/output instructions, file handling with ifstream and ofstream, opening multiple files, checking end of file, and a review of the file I/O process. Discover how to write to an ASCII file and read data from it in C++ programming. Practice with examp
0 views • 47 slides
Fundamentals of Mass Transfer: Lecture Highlights with Dr. Alaa D. Jawad AL-Bayati
This content covers the basics of mass transfer, including the definition, types, properties used for mass transfer, mass transfer rate, Fick's law, and factors influencing transfer rate in chemical reactions. Dr. Alaa D. Jawad AL-Bayati provides insights into the mechanisms and processes involved i
0 views • 9 slides
Transfer Reform and Common Course Numbering Initiatives in California Higher Education
The Transfer Reform initiatives, including AB 928 and AB 1111, aim to improve student transfer achievement and streamline the transfer process in California's higher education system. AB 928 focuses on establishing a single lower-division general education pathway while AB 1111 implements a common c
0 views • 7 slides
Sync HotStuff: Practical Synchronous State Machine Replication
Sync HotStuff is a practical synchronous protocol that tolerates Byzantine replicas and handles weaker synchrony models. It overcomes issues of requiring a large number of rounds and lock-step execution. The protocol ensures safety by committing blocks and guarantees liveness by continuing to commit
0 views • 15 slides
Understanding File Transfer Protocols: FTP, SSH, SFTP, and Email Systems
This content delves into the intricacies of file transfer protocols such as FTP, SSH, and SFTP, along with components of email systems. It explains how FTP works, its security implications, and the evolution towards more secure protocols like SFTP. Additionally, it provides insights into FTP impleme
0 views • 40 slides
Understanding the Key Dimensions of SSH Research Societal Impact
Exploring pathways to societal impact through SSH research, this presentation delves into the mechanisms and processes that lead to impactful interactions with society. It challenges the focus on physical outputs and emphasizes the importance of studying the ways in which SSH researchers engage with
0 views • 20 slides
Understanding Asynchronous Transfer Mode (ATM) in Data and Computer Communications
Asynchronous Transfer Mode (ATM) is a packet transfer technology that supports multiple logical connections over a single physical interface. It uses fixed-sized packets called cells for data transfer. ATM bears similarities to packet switching and offers streamlined packet transfer with minimal err
0 views • 46 slides
Understanding I2C Bus Interface and Protocol
I2C, short for Inter-Integrated Circuit, is a serial protocol with a two-wire interface designed by Philips. It allows communication between master and slave devices using start and stop conditions. Each slave device has a unique address, and data transfer occurs in serial 8-bit packets at varying s
0 views • 11 slides
Understanding Protocol Deviations in Clinical Trials
Protocol deviations are expected occurrences in clinical trials that may arise from site or participant actions. It is crucial for research teams to identify, report, and learn from these deviations to ensure the integrity and safety of the study. Mechanisms for identifying and reporting deviations,
0 views • 16 slides
Understanding OSI Model and TCP/IP Protocol Suite in Computer Networking
This content delves into the OSI model and TCP/IP protocol suite, highlighting the protocol layers, addressing mechanisms, and communication scenarios. It explores the functions of each layer, the interface between layers, and compares the TCP/IP layers with the OSI model. Through examples and illus
0 views • 46 slides
Fast File Clone in ZFS Design Proposal Overview
This document details a proposal for implementing fast file clone functionality in ZFS, allowing for nearly instant file copying through referencing. The motivation behind this proposal includes support for VMware VAAI, NAS Full File Clone, and Fast File Clone to save memory and disk space. The prop
0 views • 29 slides
Setting Up Ignite-UX Server and Client with NFSv4 and SSH Tunnel on HP-UX 11iv3
Learn how to configure an Ignite-UX server and client on HP-UX 11iv3 using NFSv4 with an SSH tunnel for a secure environment. This presentation covers the setup process, equipment requirements, and the benefits of using NFSv4 in disaster recovery scenarios.
0 views • 28 slides
Seeking a General-Purpose CCSDS Link Layer Protocol: Next-Generation Data Link Protocol (NGDLP)
This document discusses the proposed Universal Frame Format for a next-generation data link protocol, focusing on major questions about transfer frames, Protocol Link Transmission Unit (PLTU), and Universal Transfer Frame Structure. It explores topics such as frame formats, telemetry transfer frames
0 views • 24 slides
NT Awake Proning Protocol for Non-Intubated Patients
This protocol outlines the benefits and procedure for prone positioning in non-intubated patients experiencing mild to moderate hypoxemia. It highlights patient eligibility criteria, equipment required, and considerations for nursing care. The protocol emphasizes improving oxygenation by promoting a
0 views • 11 slides
Understanding Electron-Phonon Interaction and Peierls Instability in Polyacetylene using SSH Model
Explore the concepts of electron-phonon interaction, Peierls instability, and the SSH model in the context of Polyacetylene. Dive into the Born-Oppenheimer approximation, electron band properties, and density of states, unraveling the fascinating world of molecular dynamics and energy calculations.
0 views • 16 slides
Understanding File Input/Output (I/O) in C++
File Input/Output (I/O) is an essential concept in C++ programming, allowing for interaction with files stored on secondary storage devices. This involves steps like including the fstream header file, declaring file stream variables, associating them with input/output sources, opening the file, perf
0 views • 19 slides
Terrestrial File Transfer Concept: Design Goals and Protocols
This document discusses the concept of terrestrial file transfer as presented in a series of slides from an ESA event in Noordwijkerhout, The Netherlands. It covers the purpose, design goals, protocols, and transport protocols involved in exchanging files between agencies for mission design, operati
0 views • 20 slides
Understanding File Systems: File Naming, Extensions, and Structure
File systems and commands play a crucial role in managing information on disks while shielding users from the complexities of storage mechanisms. This article delves into the rules of file naming, distinctions between upper and lower case letters, file extensions indicating file types, and the under
0 views • 85 slides
Sequential File Maintenance and Organisation Process
In sequential file maintenance, the master records are updated and written to a new file in sequence after processing transaction records. This process continues until all relevant master records are updated, resulting in a new file with unchanged and updated records. Additional steps involve file s
0 views • 7 slides