Understanding Vulnerability: Meaning, Types, and Factors affecting Vulnerability
This article explores the concept of vulnerability, including its meaning, types (physical and social), and factors that contribute to vulnerability. It discusses the impact of hazardous events on communities, infrastructure, and the environment, and highlights the importance of awareness and prepar
26 views • 31 slides
Understanding Risk Management in Environmental Geography and Disaster Management
Risk management in environmental geography and disaster management involves assessing the potential losses from hazards, evaluating vulnerability and exposure, and implementing strategies to mitigate risks. It includes calculating risk, dealing with risk through acceptance, avoidance, reduction, or
1 views • 10 slides
Understanding Vulnerability Mapping (VM) for Ensuring Free and Fair Elections
This PowerPoint presentation delves into the concept of vulnerability mapping (VM) in the context of election planning, emphasizing the role of District Electoral Officers (DEOs/ROs) in controlling the entire VM process. It outlines pre-poll and poll-day responsibilities, as well as post-poll action
2 views • 36 slides
Comprehensive Guide to Vulnerability Mapping in Election Planning
Explore the significance of Vulnerability Mapping (VM) in empowering vulnerable voters, understand the concept, role of DEO/RO, and the objective of identifying and addressing voter vulnerability. The presentation emphasizes pre-poll and post-poll actions, remedial measures, and timelines, providing
3 views • 42 slides
Vulnerability Mapping (VM).Guidance Plan
Vulnerability Mapping (VM) is crucial in empowering vulnerable voters by identifying and addressing potential threats to their exercise of franchise. This guide explains the concept of vulnerability mapping, its role in ensuring free and fair elections, and the responsibilities of election officials
2 views • 42 slides
REACH Pathway Mapping Toolkit
Explore the REACH Pathway Mapping Toolkit to analyze credentials in pathways, labor market outcomes, work-based learning, and holistic support to identify gaps and needs for improved guidance. Learn about different mapping examples and types to enhance educational pathways effectively.
0 views • 19 slides
Understanding Telecom Security Testing: Vulnerability Assessment & Remediation
Telecom security testing is crucial for safeguarding infrastructure against hacks. Learn about vulnerability assessment, common weaknesses, types of vulnerabilities, severity scoring, and automated tools like Nessus and Nexpose. Explore network, web application, and host-based vulnerability testing
0 views • 18 slides
Understanding Relational Database Design and Mapping Techniques
Explore the process of mapping Entity-Relationship (ER) and Enhanced Entity-Relationship (EER) models to relational databases. Learn about relational model concepts, mapping algorithms, and the goals and steps involved in the mapping process. Discover how to preserve information, maintain constraint
1 views • 42 slides
Leveraging Artifact Dependency Graphs for Software Vulnerability Detection
Explore how LLVM-GitBOM utilizes artifact dependency graphs to detect vulnerabilities in software dependencies. The presentation covers the overview of GitBOM, CVE detection, supply chain vulnerabilities, and the importance of precise build tools in vulnerability scanning. Learn about utilizing gito
0 views • 34 slides
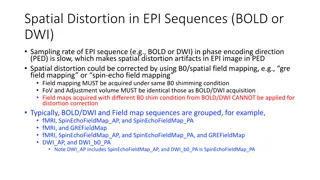
Spatial Distortion Correction in EPI Sequences: Field Mapping Examples
Spatial distortion artifacts in EPI sequences (BOLD or DWI) due to slow sampling rates in the phase encoding direction can be corrected using B0/spatial field mapping techniques. This correction requires obtaining field maps under the same B0 shimming conditions and with identical FoV and adjustment
0 views • 4 slides
Creating a Curriculum Map for Competency-Based Education
This presentation aims to guide faculty and staff in competency-based curriculum mapping at the program level. It covers the definition of curriculum mapping, a recommended framework, steps for identifying program competencies, developing a matrix, and mapping courses to competencies. Utilize this r
0 views • 11 slides
Understanding Customer Interactions Through Journey Mapping
Customer journey mapping and empathy mapping are essential tools for businesses to comprehend typical customer interactions, decisions, and emotions throughout the product acquisition cycle. By creating representative personas and empathy maps, teams can gain deeper insights into customer needs and
1 views • 12 slides
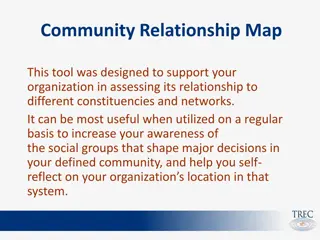
Community Relationship Mapping Tool for Organizational Assessment
Designed to support organizations in assessing relationships with various constituencies and networks, the Community Relationship Mapping Tool increases awareness of social groups influencing decisions in a community. Regular use enhances self-reflection on an organization's position in the system,
1 views • 12 slides
Understanding the Vulnerability Index for Small Island Developing States
This article discusses the concept of vulnerability in the context of countries, focusing on Small Island Developing States (SIDS). It explores the differences between vulnerability and poverty, the history of vulnerability index development from SIDS to Least Developed Countries (LDCs), and critiqu
8 views • 44 slides
Integrated Vulnerability Assessment and Human Security for Sustainable Livelihoods in the Solomon Islands
The approach to the Solomon Islands Integrated Vulnerability Assessment (SIIVA) and the Integrated Vulnerability and Adaptation Assessment (IVA) are key methodologies to assess climate change risks and prepare nations for adaptation. The objectives include informing national climate change policies,
0 views • 21 slides
Understanding Genetic Markers in Molecular Mapping
Genetic markers play a crucial role in gene mapping within molecular biotechnology. They are fragments of DNA associated with specific genomic locations, aiding in identifying DNA sequences and analyzing genetic variation. Various types of genetic markers such as RFLP, SSR, and SNP offer insights in
1 views • 26 slides
Understanding Value Stream Mapping in Toyota Production Systems
Value Stream Mapping is a powerful tool used by Industrial Engineers to visualize processes, identify areas of improvement, and enhance efficiency. This method involves numbering steps, naming each one, indicating paths with arrows, flagging problem areas with stars, and brainstorming solutions. Var
1 views • 7 slides
Economic Vulnerability Premium for SIDS - Webinar Insights
Presentation outlines applying Economic Vulnerability Index (EVI) for an Economic Vulnerability Premium in Small Island Developing States (SIDS) during ADF 13 cycle. Details ADF grants availability, grant allocation framework, performance-based allocation system, and modifications needed for SIDS.
0 views • 14 slides
Mapping Robot using ROS, Lidar with Raspberry Pi & MATLAB
Turtle.bot is a popular product for home service robots, utilizing SLAM and navigation technologies. It features gyro, Kinect sensors, Lidar, and a laptop for mapping. The robot localizes and navigates using ROS in Raspberry Pi connected with MATLAB. ROS (Robot Operating System) is a set of software
0 views • 17 slides
National Labor Mapping Application User Roles and Access Overview
This detailed overview outlines the implementation plan, user roles, and access benefits of the National Labor Mapping Application. Users are assigned specific roles with established access through domain usernames, enhancing security measures. Different user roles such as VISN Coordinators, Site Te
0 views • 14 slides
Mapping Methodology for Establishing ESCO Relations
Learn how to set up teams, collect resources, compare classifications, and establish mapping relations for ESCO implementation projects. Get insights on using computer-assisted suggestions, updating mapping tables, and selecting mapping projects. Explore techniques for navigating classifications, br
0 views • 21 slides
Gender Considerations in Climate Vulnerability and Risk Assessments for Agriculture
This training workshop explores the intersection of gender, climate vulnerability, and risk assessments in adaptation planning for the agriculture sectors. It delves into how women and men may experience climate change effects differently and discusses ways to ensure gender considerations are includ
0 views • 6 slides
Exploring Texture Mapping in Computer Graphics
Delve into the world of texture mapping as a solution to the smoothness of polygons in computer graphics. Learn how to create textured scenes using techniques such as bump mapping and environmental mapping. Discover the process of representing textures, working with curved surfaces, and mapping onto
2 views • 24 slides
Understanding Vulnerability and Capacity Issues in Civil Courts
Exploring vulnerability and capacity issues in civil courts, this content delves into the importance of addressing vulnerabilities of parties and witnesses for ensuring fair participation and quality evidence in legal proceedings. Topics covered include factors contributing to vulnerability, the rol
0 views • 21 slides
Innovative LiDAR Cave Mapper for Cavers
Develop a portable and cost-effective LiDAR cave mapper to assist freelance cavers in mapping caves efficiently. The project aims to create a device that is affordable, DIY-style, and open-source, making cave mapping more accessible and accurate. The team from FAMU-FSU College of Engineering strives
0 views • 22 slides
Atlantic Seabed Mapping Workshop Summary
Workshop held in Dublin Castle on Dec 2, 2014, discussed current and future plans for seabed mapping in the Atlantic. Key topics included navigational charting, initiatives by various organizations, challenges of disjointed mapping efforts, and proposed actions to address issues. Recommendations inc
1 views • 5 slides
Coastal Vulnerability Assessment of Curacao, Netherlands Antilles
Conduct a comprehensive Coastal Vulnerability Audit of Curacao, Netherlands Antilles, using the Coastal Vulnerability Audit Tool (CVAT) to assess physical, human, and engineering infrastructure systems, as well as vulnerability, planning, and resiliency action plans. Consider factors such as climati
0 views • 10 slides
Reimagining Vulnerability: Rethinking the Body and Human Dignity
The notion of vulnerability is explored within the framework of the human body and dignity, challenging traditional concepts of autonomy and independence. Scholars like Martha Nussbaum and Fineman provide insights on the universal nature of vulnerability and advocate for a shift towards recognizing
0 views • 21 slides
Understanding Risks and Vulnerability in Risk Assessment
This module focuses on understanding risks, vulnerability, and conducting risk assessments in disaster risk management. It covers terminologies such as threats, hazards, vulnerability, and exposure, essential for prioritizing risks and initiating risk reduction measures.
0 views • 24 slides
Power Mapping: A Visual Tool for Advocates to Influence Change
Power mapping is a visual tool used by advocates to identify key individuals to target in order to effect change. It involves mapping the community around an issue or campaign, identifying decision-makers, adversaries, and influential stakeholders. By following important steps and asking relevant qu
0 views • 10 slides
Gamifying Vulnerability Reporting for Coordinated Disclosure at Microsoft Security Response Center
Christa Anderson, a Senior Security Program Manager at Microsoft's Security Response Center, discusses the importance of gamifying vulnerability report data to encourage coordinated disclosure. The MSRC Top 100, announced at Black Hat USA, plays a crucial role in the public credit strategy by recogn
0 views • 13 slides
GEBCO Technical Sub-Commission on Ocean Mapping (TSCOM) Overview
Technical Sub-Commission on Ocean Mapping (TSCOM) is a key component of the GEBCO program, established in 2006 to provide expertise in seafloor mapping and discuss emerging technologies. TSCOM serves as an authoritative source for bathymetric and hydrographic data and offers ongoing advice to associ
0 views • 12 slides
Virtual Network Mapping: A Graph Pattern Matching Approach
Virtual Network Mapping (VNM) involves deploying virtual network requests in data center networks in response to real-time demands. It facilitates the deployment of virtual networks on physical machines by mapping virtual nodes and links onto substrate nodes and paths, ensuring constraints are met.
0 views • 15 slides
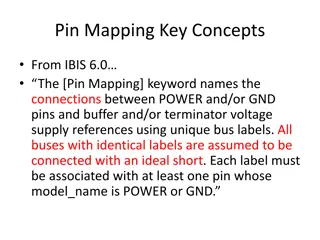
Understanding Pin Mapping and Interconnect in IBIS 6.0
Pin Mapping in IBIS 6.0 defines the connections between POWER/GND pins and buffer/terminator voltage supplies using unique bus labels. Interconnects between VDD pins and buffer supply terminals are crucial, with all pins associated with a named supply being shorted together. Draft 9 Interconnects an
0 views • 6 slides
Understanding Mercator Mapping: A Key Tool for Information System Management
Mercator is a web application designed for managing the mapping of an organization's information system, allowing for a comprehensive representation of its components and connections with the outside world. Mapping is crucial for controlling, protecting, and defending the information system, as well
0 views • 21 slides
Enhancing Nuclear Security Through Creative Vulnerability Assessment
Creative and effective vulnerability assessment and testing are essential in nuclear security to identify weaknesses and improve defense systems against intelligent adversaries. The need for in-depth assessment and realistic testing is emphasized to uncover vulnerabilities that adversaries may explo
0 views • 8 slides
Enhancing Curriculum Development through Mapping for Schools
Curriculum mapping in schools involves using electronic tools to input, track, and analyze data related to curriculum, enabling stakeholders to meet standards, align content, collect real-time data on instruction, and reflect on practices for continuous improvement. Software programs like Rubicon At
1 views • 15 slides
Understanding Vulnerability in Research Populations
Vulnerability in research populations refers to being exposed to harm without the ability to protect oneself adequately. Factors contributing to vulnerability include intrinsic limitations like decision-making capacity and situational influences such as political or economic circumstances. Different
0 views • 22 slides
Importance of Maps and GIS in Census Mapping: A Case Study from Nepal
Census mapping plays a crucial role in ensuring accurate population counts and territorial delineation. This case study from Nepal highlights the significance of Geographic Information Systems (GIS) in producing high-quality maps for census operations, data collection, analysis, and dissemination. T
0 views • 12 slides
Exploring Vulnerability and Power Dynamics in Imperial Rome: Phaedrus' Perspective
Delve into the intricate relationship between constructions of vulnerability in imperial Latin texts and the material reality of vulnerability in ancient Rome. Discover how cultural perceptions of male citizen invulnerability rely on affirming vulnerability in others. Uncover the strengths of vulner
0 views • 10 slides