Maximizing Impact: The Role of Rich Snippets in SERPs"User Intent
User intent, also known as search intent, refers to the underlying goal or purpose a user has when performing an online search. It goes beyond the literal interpretation of keywords and focuses on understanding why a person is searching. Recognizing and catering to user intent is crucial for creatin
3 views • 10 slides
Operating Systems
An operating system is a crucial program that manages all other programs on a computer. It handles tasks like input recognition, file management, and device control. There are different types of operating systems such as single-user, single-task systems, multi-user, multi-task systems, real-time ope
6 views • 11 slides
The Evolution of Graphical User Interfaces in Computing
Graphical User Interfaces (GUIs) have transformed computing into a more user-friendly and interactive experience, emphasizing the shift from technology-focused to human-centric living. This chapter delves into the various aspects of GUIs, including I/O alternatives, common GUI tasks, programming per
1 views • 32 slides
Understanding Linux User Capabilities and Namespace Management
Linux user namespaces and capabilities play a critical role in managing system security and permissions. Users and groups are assigned unique IDs, and processes are associated with the user's ID. The kernel enforces permission checks based on user IDs and group IDs, allowing root access to bypass ce
0 views • 14 slides
Overview of Vibrio cholerae: Characteristics and Identification
Vibrio cholerae is a gram-negative, curved rod bacterium known for causing cholera. Its distinctive features include polar flagellum motility, oxidase-positive nature, and resistance to inhibitory substances. Various culture media are used for its isolation and growth, such as transport, routine, an
0 views • 8 slides
Decoding the GT Identification Process: Understanding the Numbers
Exploring the intricate world of Gifted and Talented (GT) identification, this insightful guide delves into the significance of 1s and 0s, the criteria for GT scoring, percentile ranks, and the importance of Ability Profiles. Discover the nuances of GT testing, identification, stanines, and more to
1 views • 19 slides
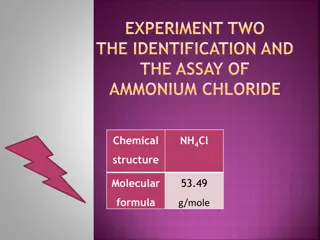
Identification and Assay of Ammonium Chloride: Experiment Insights
Explore the identification and assay process of Ammonium Chloride (NH4Cl), a weak inorganic acid commonly used in various applications. Discover its chemical properties, synthesis, reactivity, identification tests, and details of a titration process using NaOH and phenolphthalein as indicators.
0 views • 16 slides
Understanding Heuristic Evaluation in User Interface Design
Heuristic evaluation is an analytical method where experts evaluate interfaces based on usability principles. This evaluation helps in identifying potential design issues that may impact user satisfaction. The process involves a small group of evaluators reviewing the interface against a set of reco
5 views • 12 slides
Understanding Talent Identification and Selection in Sports
Talent identification in sports involves recognizing and developing the total potential of athletes in various aspects, aiming for long-term growth rather than focusing solely on immediate performance. It focuses on understanding real potential and systematically developing it over time through qual
1 views • 9 slides
Rapid Identification System for Inmate Release
The Rapid Identification System, also called Rapid ID System, provides a quick way to verify an inmate's identity using fingerprints before release from custody. It allows law enforcement agencies, including IPD users under SDSheriff, to log in and access the system. By searching the San Diego AFIS
3 views • 8 slides
Understanding Different Types of Operating Systems
An operating system is the crucial program that manages a computer's resources and acts as an interface between the user and the machine. Various types of operating systems exist, including real-time, multi-user vs. single-user, multi-tasking vs. single-tasking, distributed, and embedded systems. Re
1 views • 11 slides
Understanding LRIT System for Ship Identification and Tracking
LRIT (Long Range Identification and Tracking) system enables global identification and tracking of ships for security purposes. Ships equipped with LRIT system can autonomously transmit ship data to authorized authorities. LRIT system is mandatory for certain types of vessels as per SOLAS convention
0 views • 12 slides
Implementing Alert Messages and User Input Handling in Java
This tutorial guides you through creating alert messages, handling user input, defining functions, calling functions from the `onCreate` method, and creating an XML file for user data entry validation in Java. Learn how to display alerts for empty user credentials and process user actions accordingl
1 views • 6 slides
Language Identification System for DARPA RATS Program Evaluation
The Patrol Team Language Identification System was developed for DARPA RATS Program to create algorithms and software for speech tasks in noisy environments. The system involved analyzing datasets, implementing subsystems for language identification, and evaluating performance across different langu
0 views • 19 slides
Unsupervised Clickstream Clustering for User Behavior Analysis
Understanding user behavior in online services is crucial for businesses. This research focuses on utilizing clickstream data to identify natural clusters of user behavior and extract meaningful insights at scale. By analyzing detailed user logs, the study aims to reveal hidden patterns in user inte
0 views • 19 slides
Domain-Specific Visual Analytics Systems: Exploring Expert User Insights
This presentation delves into domain-specific visual analytics systems focusing on political simulation, wire fraud detection, bridge maintenance, and more. It emphasizes leveraging user expertise for effective system design and evaluation, highlighting the importance of user insights in data analys
0 views • 27 slides
Efficient User Management System for Health Facilities
Record and manage user details effectively with the new Version 2.0 User Management feature. RNTCP has now registered over 35,000 PHIs, 140,000 Private Health Facilities, 15,000 Private Labs, 31,000 Private Chemists, across 700 Districts and 8,000 TUs in Nikshay. Enhance operations by editing TU pro
0 views • 26 slides
Understanding Agile User Stories in Software Development
Agile user stories play a crucial role in software development by providing short descriptions of features desired by customers in a language they understand. This method allows for agile planning, efficient documentation, and effective communication between development teams and clients. Extracting
0 views • 30 slides
Enhancing User Experience Through Data Trails and Metrics
Andrea Thompson, a Sr. User Experience Manager at The Home Depot, highlights the importance of measuring and analyzing user experience metrics to understand and improve customer interactions. By investigating data trails from various touchpoints, such as customer sign-ups, interactions with associat
0 views • 17 slides
Mineral Identification Challenge for 7th Grade Science Students
Engage in a Mineral Identification Challenge where 7th-grade students will explore various minerals using color, streak, luster, transparency, texture, composition, density, crystal shape, cleavage/fracture, hardness, and special properties. Students will rotate through different stations, perform t
0 views • 11 slides
Livestock Data Management and Recording Guidelines
This documentation outlines the correct procedures for submitting livestock data, including details on birth notifications, calving information, AI processes, calf identification, and more. Topics covered include birth dates, twin identification, AI horn codes, dam and sire identification, calving e
0 views • 11 slides
User Interface Design Principles in Human-Computer Interaction
User interface design principles are crucial in Human-Computer Interaction. This content highlights key principles such as aesthetics, anticipation, autonomy, and color consideration for users with color blindness. It emphasizes the importance of user testing, user autonomy, and providing essential
0 views • 24 slides
Fine-Grained Language Identification Using Multilingual CapsNet Model
This study explores fine-grained language identification through a multilingual CapsNet model, addressing challenges such as short audio snippets, multiple languages, noise, limited training data, and non-class identification. The dataset includes various languages like Arabic, Bengali, Chinese, Eng
0 views • 36 slides
Livestock Identification Methods: Exploring Different Techniques
Explore the importance of livestock identification, methods used, and their significance in various situations. Understand why animals need to be identified, from proof of ownership to disease eradication. Learn about types of identification like branding, ear notching, tattooing, and more, each wit
0 views • 16 slides
Understanding Remote Identification of Unmanned Aircraft: Compliance Methods
The Final Rule on Remote Identification of Unmanned Aircraft introduces compliance methods for the model aircraft community to fly safely in national airspace. Explore the three ways to comply, including Standard Remote ID, Broadcast Modules, and FAA Recognized Identification Areas. Learn about regi
0 views • 11 slides
Understanding Interaction Design in Human-Computer Interaction
Interaction design focuses on creating interactive products that are easy, effective, and enjoyable to use. It aims to reduce negative user experiences while enhancing positive ones. Designing interactive products requires understanding user activities, interfaces, and device arrangements to support
0 views • 11 slides
Understanding Structural Identification in Vector Autoregressions
Explore the algebra of identification problems in VARs, including Cholesky factorization, timing restrictions, long-run impact restrictions, sign restrictions, and identification through heteroskedasticity. Discover why structural identification is crucial for policy design, economic modeling, and u
0 views • 63 slides
IEEE 802.11-20/1317r1 EHT-SIG Proposal Discussion
The document discusses EHT-SIG for single-user and sounding NDP in IEEE 802.11-20/1317r1, focusing on overflow bits, user fields, CRC, and tail formats. It covers the format details, subfields, and overhead compared to HE sounding, proposing specific bit allocations for different elements. The EHT-S
0 views • 16 slides
Understanding Minerals: Properties and Identification
Minerals are naturally occurring solid inorganic substances with definite compositions and structures. They are classified based on physical and chemical properties. This content discusses the definition of minerals, the conditions that classify gold as a mineral, distinguishing mineral characterist
0 views • 29 slides
Performance Studies of dRICH Detector at ePIC Experiment
The Electron-Ion Collider ePIC experiment focuses on the performance studies of the dRICH detector for particle identification crucial in various physics channels. The detector features aerogel optimization, SiPM sensors, and test-beam analyses. Key capabilities include different techniques for part
0 views • 28 slides
Fundamentals of Marketing: Product Identification and Branding Insights
Explore the essential concepts of marketing including the marketing mix, product identification methodology, and the significance of branding in differentiating products. Learn about the 4Ps of marketing mix - Product, Price, Place, and Promotion, and how branding plays a crucial role in establishin
0 views • 15 slides
Six Step Approach to Problem Identification in Medical Curriculum Development
In this comprehensive guide on curriculum development for medical education, the focus is on identifying and addressing key problems in the curriculum design. The six-step approach outlined covers problem identification, needs assessment, goal setting, educational strategies, implementation, and eva
0 views • 12 slides
Administrator Deletes User - User Management System Storyboard
An administrator navigates through a user list, selects a user for deletion, confirms the action, and successfully removes the user from the system. The process involves interacting with user details, confirming the deletion, and updating the user list accordingly in a structured manner.
0 views • 4 slides
Importance of Verification for Patient Identification & Blood Product Labeling in Medical Procedures
This educational program emphasizes the crucial role of verifying patient identification and blood product labeling in medical settings. It covers the significance of accurate verification, policy expectations, and the process for ensuring patient safety during blood product administration. The prog
1 views • 30 slides
User Interface vs User Experience: Understanding the Essentials
Exploring the distinctions between User Interface (UI) and User Experience (UX) in human-computer interaction design. UI focuses on the space of interaction between humans and machines, while UX encompasses users' behavior, attitude, and emotions towards a product or service. The goal is to create i
0 views • 63 slides
Advanced Techniques for User Identification in Transportation Using GPS and Accelerometer Data
This research focuses on transportation mode recognition and user identification by analyzing GPS and accelerometer data. The study involves data collection from varying conditions with over 500 trips and 150 hours of data, processed using spatio-temporal techniques. Features such as mean, deviation
0 views • 33 slides
Understanding NOAA's User Needs Identification Strategies
NOAA employs various user needs identification strategies, including user interviews, diary studies, persona building, task analysis, journey mapping, and more. By observing users, their environment, and asking the right questions, NOAA can uncover real needs effectively.
0 views • 13 slides
Understanding Context Switching and User-Kernel Interaction in Operating Systems
Context switching in operating systems involves a seamless transition between user-level threads without the kernel's awareness. User-level code manages register state and stack pointers, while user-kernel mode switching requires changing processor privilege levels and agreement on information excha
0 views • 25 slides
Behavioral Modeling Approach Across Social Media Sites
This paper explores a behavioral modeling approach for connecting users across social media sites, aiming to identify individuals based on their shared information and unique behavioral patterns. It addresses the importance of verifying ages online and presents a methodology called MOBIUS for user i
0 views • 29 slides
Tracking and Identifying People with Millimeter Wave Radar
This study presents a human tracking and identification system using mmWave radar technology, offering high precision and the ability to conceal behind materials. The system achieved a median tracking accuracy of 0.16m and an identification accuracy of 89% for 12 individuals. Unlike traditional meth
0 views • 12 slides