HOPWA: Pre-submittal Conference
The HOPWA program is the only federal initiative dedicated to addressing the housing needs of individuals living with HIV/AIDS. It provides support for eligible activities such as supportive services, housing information, and operational expenses. Client eligibility criteria include a medical diagno
0 views • 13 slides
Maximizing Impact: The Role of Rich Snippets in SERPs"User Intent
User intent, also known as search intent, refers to the underlying goal or purpose a user has when performing an online search. It goes beyond the literal interpretation of keywords and focuses on understanding why a person is searching. Recognizing and catering to user intent is crucial for creatin
3 views • 10 slides
Special Education Circuit Breaker Program Overview FY2024
The Special Education Circuit Breaker Program for FY2024 provides financial assistance to public school districts for high-cost special education services. The program includes Relief Claims and Year-End Claims cycles, with legal references for reimbursement guidelines. Reserve Relief funds are avai
1 views • 27 slides
Software-defined Networking Market
Software-defined Networking Market by Offering, Model (API SDN, Overlay SDN, Open SDN), Application (Control Flow, Packet Forwarding, Security Flow Open Flow Switch), End User (Data Centers, Enterprises), and Geography - Global Forecast to 2031
1 views • 4 slides
Multimat-2 Experiment: Advancements in HL-LHC Collimator Technologies
The Multimat-2 experiment conducted by Jorge Guardia Valenzuela and the team at CERN focused on testing prototypes of HL-LHC collimators, including materials and coatings, to improve the robustness and performance under extreme conditions. The goals included deriving strength models, exploring failu
0 views • 13 slides
Understanding Software-Defined Radio (SDR) with GNU Radio Introduction
Software-defined radio (SDR) revolutionizes radio technology by enabling flexible software-based solutions that can alter transmitter parameters without hardware changes. The SDR tiers defined by the SDR Forum provide evolving capabilities in terms of flexibility, transitioning from hardware-control
4 views • 54 slides
Operating Systems
An operating system is a crucial program that manages all other programs on a computer. It handles tasks like input recognition, file management, and device control. There are different types of operating systems such as single-user, single-task systems, multi-user, multi-task systems, real-time ope
6 views • 11 slides
Software-defined Networking Market
Meticulous Research\u00ae\u2014a leading global market research company, published a research report titled, \u2018Software-defined Networking Market by Offering, Model (API SDN, Overlay SDN, Open SDN), Application (Control Flow, Packet Forwarding, Security Flow Open Flow Switch), End User (Data Cen
6 views • 3 slides
Understanding Audiometric Worksheets: Frequency Mapping for Hearing Thresholds
Explore how audiometric worksheets represent hearing thresholds across frequencies, including patient details, equipment used, test results, and more. Learn about different audiogram forms, symbols used, and how to assess hearing loss type, degree, and laterality. Gain insights into interpreting aud
0 views • 58 slides
Impact of COVID-19 on the Software-Defined Wide Area Network Market
Software-Defined Wide Area Network (SD-WAN) Market by Component, Organization Size, Deployment Mode, End User (Communication Service Providers, Data Centers, and Enterprises), and Geography\u2014Global Forecast to 2029\n
0 views • 6 slides
The Evolution of Graphical User Interfaces in Computing
Graphical User Interfaces (GUIs) have transformed computing into a more user-friendly and interactive experience, emphasizing the shift from technology-focused to human-centric living. This chapter delves into the various aspects of GUIs, including I/O alternatives, common GUI tasks, programming per
1 views • 32 slides
Understanding Linux User Capabilities and Namespace Management
Linux user namespaces and capabilities play a critical role in managing system security and permissions. Users and groups are assigned unique IDs, and processes are associated with the user's ID. The kernel enforces permission checks based on user IDs and group IDs, allowing root access to bypass ce
0 views • 14 slides
Introduction to IEEE 802.11-20 EHT PPE Thresholds Field
IEEE 802.11-20 standard defines the Nominal Packet Padding values and Pre-FEC Padding Factors for PE fields in 11ax. The selection of Nominal Packet Padding values is crucial and can be determined using specific methods, including PPE Thresholds Present subfield. The PPE Thresholds field contains in
0 views • 14 slides
University Procurement Overview August 2020
This detailed document covers various aspects of procurement in the University of Strathclyde, including legislation, EU procurement principles, Scottish procurement context, thresholds, procedures, and risks associated with non-compliance. It emphasizes adherence to EU principles, different spend t
0 views • 37 slides
New Jersey State Library Directors Training: Purchasing Basics and Bid Thresholds
Explore the essential topics covered in the New Jersey State Library Directors Training on Purchasing Basics, including bid threshold exceptions, local public contract laws, Qualified Purchasing Agent certification requirements, and the importance of not dividing contracts to bypass bid thresholds.
0 views • 28 slides
Academic Senate Resolutions and Low-Cost Thresholds in Higher Education
The Academic Senate addresses the adoption of open educational resources (OER) and low-cost materials to support academic freedom and compliance with legislative requirements. The resolution discusses the definition of low-cost resources and the variability among California Community Colleges in set
2 views • 9 slides
Understanding Purchasing Rules and Thresholds in Government Contracts
Buying in the public sector differs from the private sector due to policies dictating purchases. General rules on thresholds prevent dividing purchases to meet discretionary buying limits. Proper documentation is required for orders ranging from $1-$10,000 to over $35,000. New York State's preferred
1 views • 17 slides
Understanding Heuristic Evaluation in User Interface Design
Heuristic evaluation is an analytical method where experts evaluate interfaces based on usability principles. This evaluation helps in identifying potential design issues that may impact user satisfaction. The process involves a small group of evaluators reviewing the interface against a set of reco
5 views • 12 slides
Understanding Different Types of Operating Systems
An operating system is the crucial program that manages a computer's resources and acts as an interface between the user and the machine. Various types of operating systems exist, including real-time, multi-user vs. single-user, multi-tasking vs. single-tasking, distributed, and embedded systems. Re
1 views • 11 slides
SSO Solution Using OAuth and OpenID Connect for Defense Logistics Agency
This document outlines a Single Sign-On (SSO) solution utilizing OAuth and OpenID Connect for the Defense Logistics Agency's America’s Combat Logistics Support Agency. OAuth allows for token-based authentication, granting access to specific resources within the Procurement Integrated Enterprise En
1 views • 8 slides
Understanding ROC Curves and Operating Points in Model Evaluation
In this informative content, Geoff Hulten discusses the significance of ROC curves and operating points in model evaluation. It emphasizes the importance of choosing the right model based on the costs of mistakes like in disease screening and spam filtering. The content explains how logistical regre
7 views • 11 slides
Implementing Alert Messages and User Input Handling in Java
This tutorial guides you through creating alert messages, handling user input, defining functions, calling functions from the `onCreate` method, and creating an XML file for user data entry validation in Java. Learn how to display alerts for empty user credentials and process user actions accordingl
1 views • 6 slides
Unsupervised Clickstream Clustering for User Behavior Analysis
Understanding user behavior in online services is crucial for businesses. This research focuses on utilizing clickstream data to identify natural clusters of user behavior and extract meaningful insights at scale. By analyzing detailed user logs, the study aims to reveal hidden patterns in user inte
0 views • 19 slides
Domain-Specific Visual Analytics Systems: Exploring Expert User Insights
This presentation delves into domain-specific visual analytics systems focusing on political simulation, wire fraud detection, bridge maintenance, and more. It emphasizes leveraging user expertise for effective system design and evaluation, highlighting the importance of user insights in data analys
0 views • 27 slides
Efficient User Management System for Health Facilities
Record and manage user details effectively with the new Version 2.0 User Management feature. RNTCP has now registered over 35,000 PHIs, 140,000 Private Health Facilities, 15,000 Private Labs, 31,000 Private Chemists, across 700 Districts and 8,000 TUs in Nikshay. Enhance operations by editing TU pro
0 views • 26 slides
User Roles and Responsibilities Overview
The user roles within the application are categorized into Account Manager, Data Steward, and Common Functionality roles. Each role comes with specific responsibilities such as managing user accounts, database management, data stewardship, incident management, and more. Non-privileged roles provide
0 views • 11 slides
Reshaping Workplace Pensions - Defined Ambition Consultation Summary
The Defined Ambition Industry Working Group, set up by the Pensions Minister in 2012, aims to reshape workplace pensions for future generations. The consultation paper explores new forms of pension schemes, emphasizing shared risks between employers and workers. As defined benefit schemes decline, d
0 views • 25 slides
Optical SDN/NFV User Guide for Network Control & Management
Explore the comprehensive user guide for Optical Software-Defined Networking (SDN) and Network Functions Virtualization (NFV) at the University of Arizona. Learn about the SDN controller interfaces, network monitoring, traffic engineering databases, and more. Discover the capabilities of the Northbo
0 views • 13 slides
Understanding Agile User Stories in Software Development
Agile user stories play a crucial role in software development by providing short descriptions of features desired by customers in a language they understand. This method allows for agile planning, efficient documentation, and effective communication between development teams and clients. Extracting
0 views • 30 slides
Reforming Audit Requirements for Federal Awards
This presentation outlines the major policy changes in the government-wide requirements for auditing Federal awards under the Single Audit Act Amendments of 1996. It discusses the transition from OMB Circular A-133 to Subpart F-Audit Requirements in 2 CFR Part 200, focusing on targeting audit requir
1 views • 34 slides
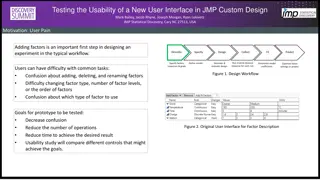
Exploring Usability Testing of New Interface in JMP Custom Design
In this study by Mark Bailey et al. from JMP Statistical Discovery in the USA, the focus lies on testing the usability of a new user interface using JMP Custom Design. The researchers highlight the significance of adding factors in the initial experiment design workflow to enhance user experience. U
0 views • 8 slides
Guide to Court Management System User Administration
Learn how to effectively manage user profiles, create sub-user accounts for legal assistants, update user information, and create associates' accounts in the Court Management System for the 17th Judicial Circuit Court of Florida. Detailed instructions provided for changing usernames, passwords, and
0 views • 15 slides
Understanding Object-Oriented Programming (OOP) Concepts in Chapter 8
Delve into the world of Object-Oriented Programming (OOP) through Chapter 8 of 'Essential Computational Thinking' by Dr. Ricky J. Sethi. Explore how classes and objects form the backbone of OOP, how messages are sent between objects, and the difference between regular and object reference variables.
0 views • 29 slides
Enhancing User Experience Through Data Trails and Metrics
Andrea Thompson, a Sr. User Experience Manager at The Home Depot, highlights the importance of measuring and analyzing user experience metrics to understand and improve customer interactions. By investigating data trails from various touchpoints, such as customer sign-ups, interactions with associat
0 views • 17 slides
Understanding User Identity and Access Tokens in Windows Security
Delve into the intricate world of user identity and access tokens in Windows security. Explore how user identities are represented, the structure of access tokens, and the significance of processes running under different user contexts. Gain insights into advanced Windows security principles and lea
0 views • 13 slides
Understanding User and Group Permissions in Linux Systems
Linux uses user and group permissions to control access to files, directories, and peripherals. Users are managed for security purposes by limiting access, with the root user having full system access. Grouping users into groups with specific access grants can enhance security. Each file is owned by
0 views • 23 slides
Automated Statistical Inference for Approximate Measurement Burdens
SketchLearn explores relieving user burdens in approximate measurement through automated statistical inference. The research delves into addressing challenges such as specifying errors, defining thresholds, handling network traffic, and optimizing measurement algorithms. By identifying and mitigatin
0 views • 35 slides
Understanding QuickScore Scoring Guide
QuickScore Scoring Guide explains how scoring is assigned based on user-defined thresholds and breakpoints. Users set values for goals, determine if higher or lower values are better, and establish scoring thresholds for different performance levels. The guide covers various scoring methods, includi
0 views • 10 slides
Comprehensive Guide to ZIMS for Studbooks User Defined Fields and Labels
Explore the functionalities of User Defined Fields (UDFs) and Labels in ZIMS for Studbooks, allowing users to define subsets of animals for analysis and assign tags or keywords to indicate specific characteristics. Learn how to create and manage UDFs, apply filters, and track unique information abou
0 views • 24 slides
Evolution of User Authentication Practices: Moving Beyond IP Filtering
The article explores the obsolescence of IP filtering in user authentication, highlighting the challenges posed by evolving technology and the limitations of IP-based authentication methods. It discusses the shift towards improving user experience and addressing security concerns by focusing on user
0 views • 22 slides