Maximizing Impact: The Role of Rich Snippets in SERPs"User Intent
User intent, also known as search intent, refers to the underlying goal or purpose a user has when performing an online search. It goes beyond the literal interpretation of keywords and focuses on understanding why a person is searching. Recognizing and catering to user intent is crucial for creatin
3 views • 10 slides
Operating Systems
An operating system is a crucial program that manages all other programs on a computer. It handles tasks like input recognition, file management, and device control. There are different types of operating systems such as single-user, single-task systems, multi-user, multi-task systems, real-time ope
6 views • 11 slides
The Evolution of Graphical User Interfaces in Computing
Graphical User Interfaces (GUIs) have transformed computing into a more user-friendly and interactive experience, emphasizing the shift from technology-focused to human-centric living. This chapter delves into the various aspects of GUIs, including I/O alternatives, common GUI tasks, programming per
1 views • 32 slides
The Impact of Individualism on American Family Dynamics
Americans are shifting towards individualistic tendencies, prioritizing personal activities over shared family time. Evidence suggests a decline in family meals as people opt for eating on the go. This shift reflects a broader trend of self-centeredness over communal identity.
0 views • 8 slides
Understanding Linux User Capabilities and Namespace Management
Linux user namespaces and capabilities play a critical role in managing system security and permissions. Users and groups are assigned unique IDs, and processes are associated with the user's ID. The kernel enforces permission checks based on user IDs and group IDs, allowing root access to bypass ce
0 views • 14 slides
Insights Into 'An Inspector Calls' Characters
In "An Inspector Calls," the Inspector represents socialism, with an air of solidity and omniscience. He delivers a warning about mankind needing to change and accept responsibility. Mr. Birling, on the other hand, embodies capitalism, shown as unlikeable and out of touch. The play critiques Birling
0 views • 7 slides
Understanding Heuristic Evaluation in User Interface Design
Heuristic evaluation is an analytical method where experts evaluate interfaces based on usability principles. This evaluation helps in identifying potential design issues that may impact user satisfaction. The process involves a small group of evaluators reviewing the interface against a set of reco
5 views • 12 slides
Enhancing Bedside Teaching in Clinical Practice: Strategies and Challenges
Explore the importance of effective bedside teaching in clinical settings with a focus on maintaining patient and learner-centeredness. Dive into strategies, historical context, challenges, and tools for improving bedside teaching, addressing issues like time constraints and privacy concerns during
0 views • 36 slides
Understanding Different Types of Operating Systems
An operating system is the crucial program that manages a computer's resources and acts as an interface between the user and the machine. Various types of operating systems exist, including real-time, multi-user vs. single-user, multi-tasking vs. single-tasking, distributed, and embedded systems. Re
1 views • 11 slides
Exploring the Journey of Three Women in 'Vanities'
Vanities depicts the evolving lives of Kathy, Joanne, and Mary from high school through college and into their late twenties, highlighting themes of fear, vanity, and societal pressures. As the women navigate their ambitions and relationships, their individual struggles with self-centeredness and so
7 views • 17 slides
Implementing Alert Messages and User Input Handling in Java
This tutorial guides you through creating alert messages, handling user input, defining functions, calling functions from the `onCreate` method, and creating an XML file for user data entry validation in Java. Learn how to display alerts for empty user credentials and process user actions accordingl
1 views • 6 slides
Themes of Society and Psychology in Frankenstein
Society unfairly associates physical deformity with monstrosity in Mary Shelley's novel, Frankenstein. The abandonment and lack of proper nurture shape the monster's nature, while Victor and his creation struggle with gender identity. Frankenstein's self-centeredness leads to self-destruction, and t
0 views • 14 slides
Unsupervised Clickstream Clustering for User Behavior Analysis
Understanding user behavior in online services is crucial for businesses. This research focuses on utilizing clickstream data to identify natural clusters of user behavior and extract meaningful insights at scale. By analyzing detailed user logs, the study aims to reveal hidden patterns in user inte
0 views • 19 slides
Domain-Specific Visual Analytics Systems: Exploring Expert User Insights
This presentation delves into domain-specific visual analytics systems focusing on political simulation, wire fraud detection, bridge maintenance, and more. It emphasizes leveraging user expertise for effective system design and evaluation, highlighting the importance of user insights in data analys
0 views • 27 slides
Efficient User Management System for Health Facilities
Record and manage user details effectively with the new Version 2.0 User Management feature. RNTCP has now registered over 35,000 PHIs, 140,000 Private Health Facilities, 15,000 Private Labs, 31,000 Private Chemists, across 700 Districts and 8,000 TUs in Nikshay. Enhance operations by editing TU pro
0 views • 26 slides
User Roles and Responsibilities Overview
The user roles within the application are categorized into Account Manager, Data Steward, and Common Functionality roles. Each role comes with specific responsibilities such as managing user accounts, database management, data stewardship, incident management, and more. Non-privileged roles provide
0 views • 11 slides
Understanding Agile User Stories in Software Development
Agile user stories play a crucial role in software development by providing short descriptions of features desired by customers in a language they understand. This method allows for agile planning, efficient documentation, and effective communication between development teams and clients. Extracting
0 views • 30 slides
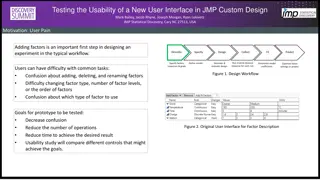
Exploring Usability Testing of New Interface in JMP Custom Design
In this study by Mark Bailey et al. from JMP Statistical Discovery in the USA, the focus lies on testing the usability of a new user interface using JMP Custom Design. The researchers highlight the significance of adding factors in the initial experiment design workflow to enhance user experience. U
0 views • 8 slides
Understanding Social and Emotional Development in Young Children
Explore the general emotional patterns and specific emotions in young children aged 4 to 6 years. Understand the positive and negative characteristics such as self-centeredness, independence, anxiety, and fear, and learn how to deal with common fears like imaginary dangers and separation anxiety. Re
1 views • 19 slides
Guide to Court Management System User Administration
Learn how to effectively manage user profiles, create sub-user accounts for legal assistants, update user information, and create associates' accounts in the Court Management System for the 17th Judicial Circuit Court of Florida. Detailed instructions provided for changing usernames, passwords, and
0 views • 15 slides
Understanding Curriculum and Principles of Curriculum Construction
Curriculum is the core of the school system, facilitating the transmission of knowledge from teachers to students. It encompasses the courses, activities, and learning environment provided to pupils. Principles of curriculum construction include child-centeredness, individual differences, co-relatio
0 views • 8 slides
Enhancing User Experience Through Data Trails and Metrics
Andrea Thompson, a Sr. User Experience Manager at The Home Depot, highlights the importance of measuring and analyzing user experience metrics to understand and improve customer interactions. By investigating data trails from various touchpoints, such as customer sign-ups, interactions with associat
0 views • 17 slides
God-Centeredness in Creation: Exploring Genesis and Its Impact on Life
Delve into the profound exploration of God-centeredness in creation through the lens of Genesis, revealing insights on life's purpose, prayer, scripture study, worship, and daily living. Uncover the significance of God's creative power, the reflection of His glory in nature, and the purpose of human
0 views • 12 slides
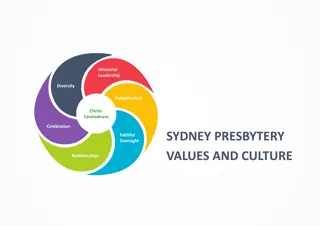
Sydney Presbytery Values and Culture: Missional Leadership and Collaboration
Sydney Presbytery values diversity, collaboration, and Christ-centeredness in its leadership approach. Embracing different perspectives, cultures, and experiences, they work together to serve the church and communities faithfully. The focus is on nurturing missional leaders who listen to the Spirit,
0 views • 11 slides
Understanding User Identity and Access Tokens in Windows Security
Delve into the intricate world of user identity and access tokens in Windows security. Explore how user identities are represented, the structure of access tokens, and the significance of processes running under different user contexts. Gain insights into advanced Windows security principles and lea
1 views • 13 slides
Understanding User and Group Permissions in Linux Systems
Linux uses user and group permissions to control access to files, directories, and peripherals. Users are managed for security purposes by limiting access, with the root user having full system access. Grouping users into groups with specific access grants can enhance security. Each file is owned by
0 views • 23 slides
Enhancing E-Learning in Higher Education: Quality and Learner-Centered Approach
Explore the theory, practices, and insights on developing high-quality, learner-centered e-learning in higher education. Discover how to support quality learning online, evolve e-learning practices, and adapt to changes post-pandemic. Learn about transitioning to deep-based learning, promoting stude
0 views • 18 slides
Evolution of User Authentication Practices: Moving Beyond IP Filtering
The article explores the obsolescence of IP filtering in user authentication, highlighting the challenges posed by evolving technology and the limitations of IP-based authentication methods. It discusses the shift towards improving user experience and addressing security concerns by focusing on user
0 views • 22 slides
User Interface Design Principles in Human-Computer Interaction
User interface design principles are crucial in Human-Computer Interaction. This content highlights key principles such as aesthetics, anticipation, autonomy, and color consideration for users with color blindness. It emphasizes the importance of user testing, user autonomy, and providing essential
0 views • 24 slides
The Challenge of Humility in Christian Living
Embracing humility can be challenging, especially in a society that glorifies perfection and self-centeredness. Through passages from Philippians and reflections on joyful Christian living, we are reminded of the importance of humility, selflessness, and focusing on the well-being of others. These t
0 views • 36 slides
Understanding Interaction Design in Human-Computer Interaction
Interaction design focuses on creating interactive products that are easy, effective, and enjoyable to use. It aims to reduce negative user experiences while enhancing positive ones. Designing interactive products requires understanding user activities, interfaces, and device arrangements to support
0 views • 11 slides
Understanding Existential Counseling: Philosophy and Practice
Existential counseling is rooted in the philosophy of existentialism, focusing on concepts such as responsibility, freedom, and the unique subjective perspective of each individual. Rollo May's influence in this approach, along with the ontological and phenomenological underpinnings, shape the under
0 views • 24 slides
Themes of Society and Psychology in Frankenstein
Society unfairly associates physical deformity with monstrosity in Frankenstein, shaping the monster's nature through abandonment and lack of nurture. The struggles of Victor and his creation with gender identity and self-centeredness lead to self-destruction, illustrating themes of tampering in God
0 views • 14 slides
IEEE 802.11-20/1317r1 EHT-SIG Proposal Discussion
The document discusses EHT-SIG for single-user and sounding NDP in IEEE 802.11-20/1317r1, focusing on overflow bits, user fields, CRC, and tail formats. It covers the format details, subfields, and overhead compared to HE sounding, proposing specific bit allocations for different elements. The EHT-S
0 views • 16 slides
Roving Reference Service and User-Centeredness in Library Spaces
Examining the impact of roving reference service models on traditional library paradigms regarding user-centeredness and space design. The study explores how modern library practices challenge established relationships, utilizing a user-centric approach to redefine spatial interactions within librar
0 views • 14 slides
Innovations in Healthcare Delivery: Transforming Care Models for Better Outcomes
Explore the evolution of care delivery in healthcare through new models emphasizing primary care, non-physician providers, and patient-centered approaches. Discover integrated systems that coordinate services for improved patient outcomes driven by factors like prevention, quality care, and patient-
0 views • 25 slides
Administrator Deletes User - User Management System Storyboard
An administrator navigates through a user list, selects a user for deletion, confirms the action, and successfully removes the user from the system. The process involves interacting with user details, confirming the deletion, and updating the user list accordingly in a structured manner.
0 views • 4 slides
User Interface vs User Experience: Understanding the Essentials
Exploring the distinctions between User Interface (UI) and User Experience (UX) in human-computer interaction design. UI focuses on the space of interaction between humans and machines, while UX encompasses users' behavior, attitude, and emotions towards a product or service. The goal is to create i
0 views • 63 slides
Understanding Context Switching and User-Kernel Interaction in Operating Systems
Context switching in operating systems involves a seamless transition between user-level threads without the kernel's awareness. User-level code manages register state and stack pointers, while user-kernel mode switching requires changing processor privilege levels and agreement on information excha
0 views • 25 slides
Redefining Childhood: Breaking the Cycle of Violence through Human Dignity
The discussion delves into the concept of childhood as the last colony, exploring the dynamics of power, control, and respect in adult-child relationships. It questions how a revised understanding of childhood can potentially disrupt the cycle of violence rooted in humiliation and conflict. Through
0 views • 9 slides