Enhancing Access to Medicines and Health Products through Innovative Approaches
Global Health Centre experts discuss how building access into innovation can ensure better access to medicines, vaccines, and health products. Key ideas include planting seeds for access early in innovation, exploring alternative innovation models, and rethinking the relationship between innovation
4 views • 20 slides
2022 Thales Access Management Index
Thales Access Management Index highlights the current landscape of access security, revealing insights on multi-factor authentication adoption, remote and privileged user access management, VPN usage trends, challenges faced, and preferences towards third-party access management. The report emphasiz
2 views • 9 slides
Guidelines for Expanded Access to Investigational Drugs and Devices
Providing guidance on types of Expanded Access for drugs, biologics, and devices, this content explains the concept of Expanded Access and the criteria that must be met. It covers different types of Expanded Access for drugs and devices, emphasizing the importance of patient safety and benefit. The
0 views • 10 slides
Personnel Safety Systems and Access Control at CERN Facilities
Personnel Safety Systems at CERN include ODH detection, fire safety measures, and access control to protect personnel from hazards. Various access control layers are implemented to regulate entry to different parts of the facility, ensuring only trained personnel access underground areas. Biometric
0 views • 19 slides
Port of Stockton Restricted Area Access Control and ID Card Policy
Access to restricted areas at the Port of Stockton facilities requires possession of a TWIC (Transportation Worker Identification Credential). Only authorized personnel, such as employees, contractors, and those with regular access, may receive a Port Access Card after approval by the Facility Secur
0 views • 6 slides
Tower Hamlets Transport Network Overview
Tower Hamlets in London has a comprehensive transport network, including Overground, Underground, DLR stations, and bus routes. With low car access, the borough focuses on promoting walking, cycling, and public transport use. Significant growth in rail and tube station entries and exits reflects the
1 views • 7 slides
Introduction to Database Security and Countermeasures
Database security is essential to protect data integrity, availability, and confidentiality. Countermeasures such as access control, inference control, flow control, and encryption can safeguard databases against threats. Access control restricts user access, inference control manages statistical da
0 views • 26 slides
Advantages and Requirements of Underground Cables
Underground cables offer advantages like better protection from damage, fewer faults, and improved appearance. However, they come with higher installation costs and insulation challenges at high voltages. Requirements include using high-conductivity stranded copper or aluminum conductors, proper ins
0 views • 22 slides
O3 Access Control Solution Overview
O3 Access Control Solution offers unique selling points like single-seat management software, role-based permissions, customizable user information, and more. The system includes a compact controller with multi-format reader support and BACnet Access objects. It integrates with other O3 modules for
0 views • 10 slides
IGU Gas Storage Committee 2022-23 Meeting Highlights
The IGU Gas Storage Committee, Group 3, discussed key topics for 2022-23 including underground storage, evolving market conditions, decarbonized energy storage, and the role of underground hydrogen storage. The committee aims to advocate positions, cooperate with stakeholders, and enhance IGU's visi
0 views • 10 slides
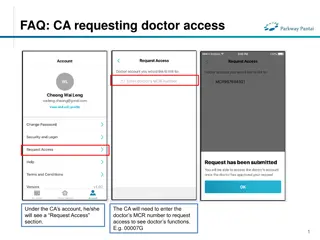
FAQs for Doctor and Clinical Assistant (CA) Account Access Management
Learn how CAs can request access to doctors' functions by entering the MCR number, how doctors can grant or remove CA access, and how CAs can manage access to multiple doctors. The process includes requesting, approving, and unlinking accounts, ensuring efficient and secure access management in a cl
0 views • 4 slides
Understanding the Underground Railroad Through Freedom Quilts
The Underground Railroad was not an actual railroad but a network of secret routes used by black slaves to escape to freedom. Freedom quilts played a crucial role as signals for the slaves, with specific patterns carrying hidden messages to guide their journey to safety. Seamstresses created sampler
2 views • 19 slides
Exploring Dark Matter in Southern Hemisphere with PAUL Project - A Scientific Journey
Join the PAUL project team as they delve into the search for dark matter in the Southern Hemisphere at L'Aquila, Italy. Discover operational underground labs, historical milestones, new developments, and future projects in South Africa. Explore the collaboration with world-class universities and the
0 views • 25 slides
Argon Recovery and Measurement in DArT Collaboration Meeting Overview
This document discusses the process of measuring and recovering underground argon in the context of a DArT Collaboration Meeting. It includes information about the underground argon in LSC, the DArT gas system presentation, the procedure to empty DArT, hardware issues related to the connection to ga
0 views • 11 slides
Lifecycle Analysis of Renewable Energy Facilities in Virginia
A comprehensive report presented at the Virginia Energy Summit discusses the analysis of renewable energy facilities' life cycle, legislative background, required analysis topics, key findings, and recommendations, emphasizing feasibility, costs, recycling opportunities, and potential impacts on und
0 views • 14 slides
EventsHQ Virtual Event Registration: User Access and Setup Guide
This comprehensive guide provides step-by-step instructions on setting up virtual event registration using EventsHQ. It covers how users can access event details, join the event, and includes best practices for sharing access links. Learn how to utilize the Virtual Event Details feature, send remind
1 views • 19 slides
Exploring Ghost Stories in the London Underground
Delve into the mysteries of ghost stories within the London Underground through a documentary that discusses monitoring stations, strange events, and unexplained phenomena. Witness accounts and expert analysis shed light on ghostly encounters, providing insight into the paranormal occurrences below
0 views • 24 slides
Underground Storage Tank Enforcement Update - February 2020
The update includes details of enforcement actions taken by the Division, such as orders issued, penalties imposed, and resolutions achieved in relation to underground storage tanks. Examples of resolved orders include violations like failure to monitor tanks regularly, lack of corrosion protection
0 views • 9 slides
Accessible Voting System for Californians with Disabilities
Learn about the Remote Accessible Vote-by-Mail System in California, designed to empower voters with disabilities to securely access, mark, and return their ballots from any computer with internet access. Find out who is eligible to use the system, how to access and return the ballot, and the steps
0 views • 23 slides
Dell Networking Solutions for BYOD and Guest Access Projects
Dell offers end-to-end solutions for Bring-Your-Own-Device (BYOD) and guest access projects, enabling secure employee access and controlled connectivity for visitors. The framework includes mobility business models, device security, network protection, and scalability. Dell supports customers in imp
0 views • 11 slides
Exploring the Daya Bay II: Jiangmen Underground Neutrino Observatory (JUNO)
Delve into the Daya Bay II project, encompassing the Jiangmen Underground Neutrino Observatory (JUNO), which secured a substantial funding commitment from the Chinese government. With construction slated to commence in 2015 and the first physics data expected by 2020, this ambitious venture has garn
0 views • 13 slides
Explore Underground Construction Technologies at UCT International Conference & Exhibition
UCT's Underground Construction Technology International Conference & Exhibition is a key industry event for connecting with customers and showcasing innovative solutions. Addressing challenges like budget constraints and limited customer visibility, UCT provides a cost-effective platform to engage w
0 views • 13 slides
Asian Americans in Underground Filmmaking: Punk, Anti-establishment, and DIY Mentality
Explore the world of Asian American filmmakers in underground cinema creating thought-provoking films with punk influences, anti-establishment themes, and a strong DIY mentality. Not confined by traditional norms, these filmmakers challenge the status quo and express creativity outside mainstream Ho
0 views • 22 slides
Regulatory Review of Underground Storage Tank Rules by Andria Merritt - Division of Waste Management
This regulatory review covers three key sections - 15A.NCAC.02N, 15A.NCAC.02O, and 15A.NCAC.02P - related to underground storage tank rules. The initial determinations highlight the rules necessary with substantive public interest and the actions required for approval. The schedule outlines the time
0 views • 7 slides
Harriet Tubman and the Underground Railroad Presentation
Explore Harriet Tubman's courageous efforts on the Underground Railroad through an interactive PowerPoint, fostering understanding of slavery, abolition, and Tubman's legacy. Engage students in discussions about Tubman's impact on U.S. history and her potential appearance on the $20 bill.
0 views • 11 slides
Polymer Physics for Route Optimization on the London Underground
Aston University's research on polymer physics applied to route optimization on the London Underground addresses the challenges of routing algorithms, interaction among communications, and the need for choices-sensitive optimization. The study explores models to minimize congestion and optimize traf
0 views • 35 slides
Role-based Access Control Policies and Security Properties Overview
This content provides an overview of Role-based Access Control (RBAC) policies, Administrative RBAC (ARBAC) systems, and security properties in the context of access control in large organizations. It discusses the implementation of RBAC in various software systems, the assignment and revocation of
0 views • 18 slides
Open Access at Charles University: Opportunities and Challenges
Charles University is navigating the landscape of open access following the implementation of the Czech National Open Access Strategy. The university is working towards making all research articles and proceeding papers open access, monitoring article processing charges, and promoting open access as
0 views • 24 slides
Kentucky Public Service Commission - Underground Facilities Protection Law Overview
Kentucky Public Service Commission enforces the Underground Facility Damage Prevention Act, which sets requirements for excavators and operators to prevent damage to underground facilities such as telecommunications, electricity, natural gas, and more. The law defines key terms like damage, excavato
0 views • 40 slides
Understanding Filesystem Security Principles and Access Control
Learn about filesystem security, general principles, discretionary access control (DAC), closed vs. open policy, closed policy with negative authorizations, and access control entries and lists. Discover how files and folders are managed, the role of access control lists (ACLs), and the different le
1 views • 56 slides
Understanding Ethernet and Multiple Access Protocols in Computer Networks
Exploring the fundamentals of Ethernet and multiple access protocols in computer networks, this content discusses the two primary categories of multiple access protocols - contention access and controlled access. It delves into topics such as CSMA/CD, LANs, performance of multiple access schemes, ad
0 views • 7 slides
Evolution of Underground Science at Laboratoire Souterrain de Modane
Explore the evolution of underground science at Laboratoire Souterrain de Modane, from its inception to becoming a national facility for fundamental physics research. Through mergers and advancements, the facility now hosts a wide range of interdisciplinary topics, including astroparticles, nuclear
0 views • 25 slides
Harvard Chan School 2021 Yearly Access Review Process
The Harvard Chan School conducts its annual Yearly Access Review (YAR) process to review user access to various financial systems. The process involves assessing permissions, levels of access, and organizational details for each team member. Instructions are provided on reviewing worksheets, adding
0 views • 19 slides
Understanding Security Access in PeopleSoft Finance
Explore the various levels of security access in PeopleSoft Finance, from basic entry access to transaction entry, approvals, and procurement processes. Learn how to request individual and department security access and find relevant forms on the financial services website. Discover the different ty
0 views • 11 slides
Georgia Underground Marking Standards and Guidelines
Comprehensive guidelines and standards for underground utility marking in Georgia, including GUFPA laws and PSC rules enforcement, utility markings, tolerance zones, locating nonconductive lines, marking duct structures, joint trenching, and other important considerations.
0 views • 32 slides
Progress in Closing Leaking Underground Storage Tank Sites Over 20 Years
Contamination from leaking underground storage tank (UST) sites poses a threat to groundwater, which is a crucial source of drinking water for many Americans. The EPA, along with various partners, has significantly reduced the backlog of such sites from around 168,400 in 1999 to 64,800 in 2019. Prog
0 views • 8 slides
Access Rights Workshop and Procedures in Oil & Gas Industry
Detailed information on access rights workshop and existing procedures in the oil and gas industry. Covering topics such as conventional vs. unconventional drilling techniques, geothermal schemes, legal positions regarding mineral rights, and the current process for underground access. Also discusse
0 views • 14 slides
Simulation Scenarios for Underground Mining in IEEE 802.11-18
This document discusses the motivation and proposed simulation scenarios for reliable communication in underground mining environments using Li-Fi technology. It addresses the shortcomings of Wi-Fi, IrDA, and BLE in such specialized settings and presents detailed scenarios for mining roadway and wor
0 views • 7 slides
Underground Storage Tank Enforcement Update - October 2, 2019
The Underground Storage Tank Enforcement Update provides information on current enforcement cases, types of enforcement cases, and status definitions for Enforcement Action Requests (EARs) and Orders. It includes details on the number of EARs received, active EARs, and status definitions for EARs an
0 views • 9 slides
Recent Updates in Underground Facility Damage Prevention Regulations
Recent law changes in the field of underground facility damage prevention, including updates on incident reporting responsibilities for excavators and operators, propane inclusion, and notifying 911. The amendments aim to enhance safety measures and streamline communication processes in excavation a
0 views • 16 slides