Gas meters market
A gas meter is driven by the force of the moving gas in the pipe. Each time the dial with the lower value complete one revolution, the pointer on the next higher value dial moves ahead one digit. These meters are essential for ensuring adequate gas pressure from the main supply of natural or liquefi
2 views • 6 slides
Understanding File Allocation Strategies in Operating Systems
Explore various file allocation schemes like extent-based systems, linked allocation, file allocation table (FAT), indexed allocation, and combined schemes used in operating systems. Learn about their pros and cons, including details on maximum file size calculations based on disk block sizes and po
0 views • 20 slides
Arrays as Pointers: Fundamentals of Computing
Explore the concept of using arrays as pointers in the context of computing. Learn how to create array of char pointers to store multiple strings, access elements in arrays of pointers, and understand the rules for accessing individual elements. Discover the nuances of pointer manipulation and array
1 views • 10 slides
Understanding VB.NET: Features, Advantages, and Disadvantages
VB.NET is a popular object-oriented programming language developed by Microsoft as a successor to Visual Basic 6. It offers features like object-oriented programming, automatic code formatting, multithreading, and event management. Despite its advantages in code formatting and ease of web applicatio
2 views • 8 slides
REGISTER ORGANIZATION OF 80386
Explore the organization of 80386 processors in the field of Information Technology, focusing on General Purpose Registers, Instruction Pointer, and Flags Control Registers. Learn about the categories, functions, and structure of these essential components in processor architecture.
0 views • 35 slides
LLVM Memory Review and Function Example
In this exercise, an LLVM IR function is created to extract the element at index 2 from a pointer to an array of integers. The concept of named memory in LLVM is reviewed, distinguishing between local, global, and constant memory declarations. Additionally, memory access operations like store, load,
2 views • 18 slides
Faster Postings Merges with Skip Pointers in Information Retrieval
Enhance the speed of postings merges in information retrieval by utilizing skip pointers and skip lists strategically. Learn how to augment postings with skip pointers, optimize query processing with skips, decide where to place skips, and adopt simple heuristics for skip pointer placement.
0 views • 7 slides
Evolution of Integer Sizes in C Programming
The evolution of integer sizes in C programming is explored, from early computers with 8-bit addresses to modern systems with 64-bit pointers. The variations in integer sizes, pointer sizes, and memory capacities over decades are highlighted, showcasing the advancements in computing technology.
0 views • 45 slides
Understanding Frame Pointer Attacks and Exploit Development with pwntools
Explore the concepts of frame pointer attacks, LD_PRELOAD usage, and exploit development with pwntools library. Discover how to spawn a shell using LD_PRELOAD or a constructor, along with the limitations and challenges associated with command-line exploitation.
0 views • 30 slides
Investigating Performance Bottlenecks in Smart Pointer Management
Investigation into performance issues caused by smart pointer manipulation, focusing on the use of boost
0 views • 8 slides
Comparison of C vs Rust Programming Languages
C and Rust are programming languages known for their efficiency in resource-constrained environments. While C offers direct control over hardware and is favored by advanced programmers for its performance, Rust provides memory safety features that prevent common errors like null pointer dereferences
0 views • 50 slides
Understanding ZFS: Structure and Operations
Explore the comprehensive structure and operations of ZFS, covering aspects like MOS layer, object-set layer, Dnode, Block Pointer, and TRIM operations. Learn about the meta-object set (MOS), dataset and snapshot layer (DSL), and storage pool allocator (SPA) modules within ZFS. Understand how ZVOLs,
0 views • 10 slides
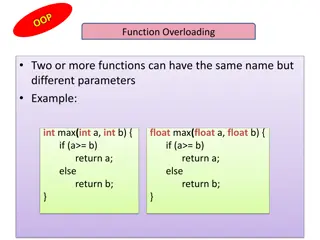
Understanding Function Overloading and this Pointer in C++
Explore the concept of function overloading in C++, allowing multiple functions with the same name but different parameters. Learn about the this pointer in object-oriented programming, which holds the memory address of the current object using a function. See examples of how to implement these conc
0 views • 13 slides
Understanding Pointers in Computing
Exploring the concept of pointers in computing, this content delves into the fundamentals of storing memory addresses, the size of variable types, managing memory, and utilizing pointers effectively. It discusses how pointers are used to store memory addresses and provides examples of pointer usage
0 views • 10 slides
Effective S106 Process Management in Local Authority: Insights from Stephen Pointer, Harborough District Council
Explore the expertise of Stephen Pointer, Strategic Planning and Housing Manager at Harborough District Council, in managing an effective Section 106 (S106) process. Discover his role, responsibilities, and experiences in navigating the complexities of national and district contexts, community inter
0 views • 19 slides
Understanding Computer Architecture Interrupts and Exceptions
Computer architecture interrupts and exceptions are essential for handling external events and unexpected conditions during program execution. Interrupts are caused by external events such as I/O requests, timers, or hardware failures, while exceptions occur due to specific instruction executions. W
0 views • 19 slides
Advanced Programming of Web Applications with Browser APIs
Explore advanced programming techniques for web applications using Browser APIs like navigation, history, web pages visibility, multiple windows/tabs, mouse and pointer interaction, and text selection. Learn how to leverage these APIs to create dynamic and interactive web experiences.
0 views • 22 slides
Code Pointer Integrity Team Overview
Code Pointer Integrity Team, consisting of Po-Jen Lai, Timmy Lin, Chun-Yu Hsiung, and Hung-Lin Wu, under the instruction of Scott Mahlke, is focused on understanding control flow hijack, memory control, and protection mechanisms. They explore new approaches to enhance code safety while minimizing ov
0 views • 25 slides
Automatic Generation of Research Highlights from Scientific Abstracts
Huge growth in scientific publications has made it challenging for researchers to keep up with new research. This project focuses on automatically constructing research highlights from paper abstracts using deep learning models. The system employs sequence-to-sequence models with attention and point
0 views • 9 slides
Understanding Pointers in C: A Beginner's Guide
Delve into the world of pointers in C with this comprehensive guide covering topics such as the address operator, pass by copy versus pass by reference, pointer usage, NULL pointers, pointer allocation, and practical experiments to enhance your understanding. Learn about the fundamentals of pointers
0 views • 22 slides
Introduction to Computer Graphics and Multimedia Applications
This lecture covers the fundamentals of computer graphics and multimedia applications, focusing on quadric surfaces, polygon meshes, and different mesh representations such as explicit mesh, vertex pointer representation, and edge list representation. It explains how quadric surfaces are defined imp
0 views • 8 slides
Understanding Smart Pointers in C++ - Bonus Lecture CSE390c Spring 2022
Explore the concept and benefits of smart pointers in C++ as a solution to managing heap-allocated memory more effectively. Learn about avoiding memory leaks and errors when handling pointers through smart pointer implementation. Dive into a Toy Smart Pointer example using a custom class template.
0 views • 36 slides
Overview of Static Bug Detection in Software Quality Assurance
Static bug detection is a less popular but effective approach for software quality assurance compared to traditional testing methods. It involves tools like Findbugs that help identify potential issues in code before deployment, such as bad coding styles, null pointer dereferences, and malicious cod
0 views • 36 slides
Memory Models: Enhancing Semantics for Programs with Data Races
This content delves into the importance of establishing stronger memory models to provide better semantics for programs experiencing data races. It highlights the challenges faced due to weak semantics in programming languages like C++ and Java, emphasizing the need for improved memory models to add
0 views • 61 slides
Advancements in ROOT Framework: Communication Strategies and Technical Updates
Explore the latest developments in the ROOT framework, including new compression algorithms, parallel processing enhancements, shared pointer support, and improvements in thread safety and performance. Learn how to effectively communicate project results and updates through workshops, conferences, r
0 views • 12 slides
Overview of 8085 Microprocessor Architecture
Intel 8085 microprocessor, introduced in 1977 as an 8-bit MP with 40-pin dual-in-line chip, operates on a single +5V supply at a clock speed of about 3MHz. It features 16-bit address bus capable of addressing up to 64KB memory, N-MOS technology, multiplexed data and address buses, interrupt support,
0 views • 52 slides
Understanding the 8085 Microprocessor Programming Model
The 8085 microprocessor, made by Intel, features general purpose registers, an accumulator, flag register, stack pointer, and program counter. The programming model includes ALU operation, flag flip-flops, and different instruction formats and operand types for executing tasks efficiently.
0 views • 13 slides
Understanding 8085 Microprocessor Architecture
The 8085 microprocessor architecture involves key components like register array, ALU, program counter, stack pointer, address latch, and more. Learn about the functionality and importance of each unit in data manipulation and communication. Dive into the details of general-purpose registers, data s
1 views • 17 slides
Understanding General Register Organization in Computer Architecture
In computer architecture, a common bus system is used to efficiently connect a large number of registers in the CPU. This enables communication between registers for data transfers and various microoperations. The setup includes multiple registers connected through a common bus, multiplexers for for
0 views • 40 slides
Pointer and Reference Conventions in C++ Programming
Understanding the conventions for passing pointers and references in C++ is crucial for safe and effective programming. Different forms allow various levels of control, from read-only access to modification rights, each signaling a specific intent. These conventions help prevent unexpected behavior
0 views • 21 slides
Overview of Exception Handling in C++ Programming
This content provides insights into exception handling in C++ programming, specifically comparing it to Java. It covers the differences in exception handling between C++ and Java, such as the absence of null pointer exceptions and divide-by-zero exceptions in C++. It explains how C++ deals with exce
0 views • 13 slides
Overview of COMP.520: Compilers with S. Ali
An overview of COMP.520: Compilers with S. Ali covering topics such as LLVM, JIT compilers, interesting ID errors, virtual address table vs VAT pointer, PA4 overview, local declarations, field declarations, method declarations, and variable access. The course includes important announcements and rec
0 views • 63 slides