CS 404/504 Special Topics
Adversarial machine learning techniques in text and audio data involve generating manipulated samples to mislead models. Text attacks often involve word replacements or additions to alter the meaning while maintaining human readability. Various strategies are used to create adversarial text examples
1 views • 57 slides
Entry Requirements for Higher National Diploma & Bachelor Degree Programmes at UNISSA
Applications are open for admission to UNISSA's programmes, with applicants required to meet general and specific entry requirements. Equivalents like Higher National Diploma are considered, but meeting requirements does not guarantee entry. Various criteria apply, including qualifications, health s
2 views • 25 slides
Understanding Translation: Key Concepts and Definitions
Translation involves transferring written text from one language to another, while interpreting deals with oral communication. Etymologically, the term "translation" comes from Latin meaning "to carry over." It is a process of replacing an original text with another in a different language. Translat
11 views • 76 slides
Overcome Denied Entry to Canada
Experience the expertise of Northvistaimmigration.com and overcome the heartache of being Denied Entry to Canada. Let us help you navigate the immigration process with compassion and success.\n\n\n\/\/northvistaimmigration.com\/denied-entry-to-canada\/
4 views • 1 slides
Understanding Single Entry System in Financial Accounting
Single Entry System is a simplified method used by small businesses to track their financial transactions. It lacks the rigor of double-entry bookkeeping and focuses on recording cash transactions and personal accounts. This system presents challenges in accurately determining profits and financial
0 views • 14 slides
Understanding Coordinated Entry System (CES) in Homeless Services
Coordinated Entry is a strategic approach focusing on housing and service coordination to link individuals experiencing homelessness to appropriate resources. With a primary goal of quick identification and prevention of homelessness, the system assesses consumer needs and connects them to housing a
0 views • 12 slides
Understanding Entry-Level Driver Training (ELDT) Requirements
Entry-Level Driver Training (ELDT) is mandatory for entry-level commercial motor vehicle (CMV) operators in interstate and intrastate commerce who are obtaining a Class A or Class B CDL for the first time, upgrading their CDL, or adding specific endorsements. ELDT must be completed from a provider l
0 views • 9 slides
Understanding Double Entry Accounting System in Finance
There are two commonly known systems of accounting - single entry system and double entry system. Double entry system is the basis of modern day accounting and ensures accuracy by recording every transaction with dual aspects of debit and credit. By maintaining personal and impersonal accounts, it h
1 views • 7 slides
Understanding Entry and Exit Barriers in Industries
Entry and exit barriers play a significant role in shaping industry attractiveness and competitiveness. High entry barriers can deter new entrants, leading to stable returns but also higher risks. Conversely, low entry barriers may attract new players during economic upturns but result in intense ri
1 views • 15 slides
Comprehensive Confined Space Entry Training Guide
This training guide covers all aspects of confined space entry, including employee proficiency, safe performance, permit requirements, authorized entrants' duties, emergency services, and more. You'll learn about OSHA regulations, confined space definitions, examples, hazards, and general requiremen
0 views • 41 slides
Introduction to Structured Text in PLC Programming
Structured text is a high-level text language used in PLC programming to implement complex procedures not easily expressed with graphical languages. It involves logical operations, ladder diagrams, and efficient control logic for industrial automation. Concepts such as sensor input, logic operation
5 views • 23 slides
Understanding Globalization and the Evolving Entrepreneurial Environment
Globalization is the increasing economic interdependence among countries worldwide, leading to cross-border transactions, technology diffusion, and international capital flows. It facilitates business expansion, erases market differences, and encourages global strategic orientations. Factors influen
0 views • 9 slides
Understanding Functional Skills: Text Analysis and Application
This instructional text guides learners through the purpose of functional skills in analyzing different types of text, such as skimming and scanning, and understanding the features of various text genres. It includes activities to practice skimming, scanning, and detailed reading, with a focus on de
0 views • 13 slides
Enhancing Accessibility Through Alternate Text in Microsoft Documents
Explore the importance of alternate text in Microsoft documents for accessibility. Learn what alternate text is, why and when you should use it, and how to add it effectively. Discover the benefits of incorporating alternate text and the legal aspects related to accessibility under Section 508. Enha
0 views • 23 slides
New UCAS Tariff for Higher Education Entry Overview
UCAS has introduced a new Tariff for higher education entry starting from September 2017. This toolkit is designed to assist teachers and advisers in understanding the changes, timeline, points system, university examples, myth debunking, and available resources. The aim is to prepare educators and
0 views • 32 slides
Text Classification and Nave Bayes: The Power of Categorizing Documents
Text classification, also known as text categorization, involves assigning predefined categories to free-text documents. It plays a crucial role in organizing and extracting insights from vast amounts of unstructured data present in enterprise environments. With the exponential growth of unstructure
0 views • 28 slides
Understanding Audience and Purpose in Text Analysis
When analyzing written texts, identifying the purpose and audience is crucial. The purpose reflects the reason behind the text, while the audience indicates who the text is intended for. By recognizing these aspects, one can better understand the content, language, and overall impact of the text. Va
1 views • 50 slides
Essential Information on Text-to-911 System
Explore key details about the text-to-911 system, including capturing text conversations, handling abandoned calls, transferring text calls to queues, and managing text conversations effectively. Learn about system configurations, call release timings, and dispatcher capabilities in handling text me
0 views • 12 slides
Text-to-911 System Operations Quiz
Test your knowledge on Text-to-911 system operations with this quiz. Learn about capturing text conversations, handling abandoned calls, transferring calls to queues, text conversation timelines, and more. Enhance your understanding of the protocols and procedures involved in managing text-based eme
1 views • 12 slides
Impact of Rating-Based Platform Screening on New Complementor Entry
This study explores the effects of a platform design that ranks incumbent complementors based on review ratings on new complementor entry and overall complementor quality. The findings suggest that the rating-based platform screening reduces new complementor entry but enhances complementors' overall
0 views • 9 slides
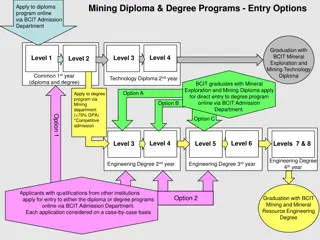
BCIT Mining Diploma & Degree Programs Entry Options
Explore the entry options for BCIT's Mining Diploma and Degree programs, including pathways for graduates to transition from the diploma to the degree program. Applicants can choose between diploma or degree programs based on their goals, with competitive admission criteria in place for direct entry
0 views • 10 slides
Understanding Entry and Exit Dynamics in Industries
Explore the fascinating world of entry and exit in industries, from the facts and barriers to Bain's typology of entry conditions and structural entry barriers. Learn about entry deterring strategies such as limit pricing, predatory pricing, and strategic bundling, and how they impact the market lan
0 views • 8 slides
Exploring Multi-Modal Text Entry and Selection on Mobile Devices
This study delves into the exploration of various input methods on mobile devices for text entry and selection. It compares traditional touch input with alternative methods such as tilt, speech recognition, and foot tapping. Through experiments, the study evaluates the performance benefits, expressi
0 views • 31 slides
Effective Strategies for Data Entry Integrity and Minimizing Errors
The chapter and subchapter discuss the importance of data integrity in the data management process, specifically focusing on data entry procedures, authenticity, and minimizing errors. It covers traditional manual data entry methods versus newer automated technologies, such as CAPI, and offers strat
0 views • 31 slides
Understanding Text Representation and Mining in Business Intelligence and Analytics
Text representation and mining play a crucial role in Business Intelligence and Analytics. Dealing with text data, understanding why text is difficult, and the importance of text preprocessing are key aspects covered in this session. Learn about the goals of text representation, the concept of Bag o
0 views • 27 slides
Effective Double-Entry Journaling for Deeper Reading Engagement
Double-Entry Journaling is a powerful method to engage actively with reading, promote deeper comprehension, and facilitate effective study guides. This technique involves dividing a document into two columns, where the left column contains quotes, main ideas, and confusing passages, while the right
0 views • 12 slides
Introduction to JMP Text Explorer Platform: Unveiling Text Exploration Tools
Discover the power of JMP tools for text exploration with examples of data curation steps, quantifying text comments, and modeling ratings data. Learn about data requirements, overall processing steps, key definitions, and the bag of words approach in text analysis using Amazon gourmet food review d
0 views • 23 slides
How to Fill Out the Junior Duck Stamp Program Entry Form
Properly fill out your child's Junior Duck Stamp Program entry form by providing group and student information, entry details, conservation message, supervising adult/teacher information, authenticity statement, submission guidelines, and deadline. Ensure original artwork, signatures, and mailing in
0 views • 7 slides
Exploring the Features and Structure of a Diary Entry
Dive into the features and structure of a diary entry, understand key elements such as past tense, writer's feelings, and informal language. Discover when to use different text styles and embark on a task to analyze a diary entry by highlighting grammatical and structural features. Plus, explore the
0 views • 6 slides
Understanding Threats and Responses in the Mobile App Market
The study explores the impact of platform-owner entry on complementors in the mobile app market, examining evidence from platforms like Facebook, Uber, Android, Alibaba, iOS, and WeChat. Concerns from complementors about imitation by platform owners are discussed, along with views from platform owne
1 views • 19 slides
Single Firefighter Forcible Entry through Inward Swinging Door
Follow these steps for a single firefighter forcible entry through an inward swinging door: assess the door size and shock the door jamb, insert the adz end for mechanical advantage, use an axe as a wedge, create a gap using the butt of the axe, advance the halligan tool to force entry efficiently.
0 views • 6 slides
Understanding the Role of V3 Region in HIV Entry to CD4 T-Cells
The V3 region of gp120 plays a crucial role in HIV entry to CD4 T-cells by determining the coreceptor usage. Studies focus on the structural aspects of V3, its conservation, coreceptor binding, and antibody accessibility. The HIV envelope structure, including trimeric spikes with gp120 and gp41 glyc
0 views • 24 slides
Understanding Bigrams and Generating Random Text with NLTK
Today's lecture in the Computational Techniques for Linguists course covered the concept of bigrams using NLTK. Bigrams are pairs of words found in text, which are essential for tasks like random text generation. The lecture demonstrated how to work with bigrams, including examples from the NLTK boo
0 views • 19 slides
Evolution of Educational Background for Entry into the Therapeutic Recreation Profession
This presentation by Teresa M. Beck provides an overview of the historical progression in educational requirements for entry-level professionals in therapeutic recreation. It delves into the shift from bachelor's to master's degree programs, challenges and advantages of pursuing a master's degree, a
1 views • 33 slides
Understanding Security Access in PeopleSoft Finance
Explore the various levels of security access in PeopleSoft Finance, from basic entry access to transaction entry, approvals, and procurement processes. Learn how to request individual and department security access and find relevant forms on the financial services website. Discover the different ty
0 views • 11 slides
Insights on Entry and Exit Dynamics in Industries
Exploration of the entry and exit dynamics in industries, covering factors influencing the establishment of new firms, barriers to entry, Bain's typology of entry conditions, structural entry barriers, and entry-deterring strategies employed by incumbents. Insights include the impact on the market l
0 views • 7 slides
Enhancing Reading Comprehension Through Text-Dependent Questions
This resource delves into the significance of text-dependent questions in improving students' reading comprehension skills by emphasizing the importance of evidence from the text, building knowledge through nonfiction, and developing critical thinking abilities. It highlights key advances in educati
0 views • 16 slides
TCIC Conditions of Bond - Implementation Overview
The TCIC Conditions of Bond outline the procedures and requirements for entry into TCIC for cases involving violent and family violence-related offenses in Texas. HB 766 and SB 6 impact the Texas Code of Criminal Procedure, defining duties for Magistrates, Sheriffs, and DPS. Magistrates must notify
0 views • 34 slides
BioLock Biometric Home Entry System Overview
BioLock is a biometric home entry system developed by Mavis Chan, Brent Erickson, and Sydney Bitner of Group 9. It features a fingerprint-enabled lock for secure home access, allowing homeowners to check access history remotely and receive alerts for unauthorized entry attempts. The system utilizes
0 views • 12 slides
Data Entry and Management Procedures for Clinical Trials
Detailed instructions on how to enter and manage data for clinical trials are provided in this content. It covers steps such as screening, randomization, data entry, use of electronic case report forms, and various forms to be completed throughout the trial period. The process involves both unblinde
0 views • 4 slides