Cybersecurity and Supply Chain Risk Management: Best Practices for Procurement
The best practices for managing cybersecurity and supply chain risks in procurement. This book covers topics such as supply chain attacks, evaluating cybersecurity risks, vendor risk assessment, and implementing effective procurement strategies.
7 views • 23 slides
Types Cyber Attacks: Cyber Security Training Workshop
Join our Cyber Security Training Workshop to learn about different types of cyber attacks such as social engineering attacks, DDoS attacks, malware attacks, MitM attacks, APTs, and password attacks. Enhance your knowledge and skills in cyber security.
15 views • 45 slides
The Art and Science of Demand and Supply Chain Planning: Navigating Today's Global Economy
Explore the intricacies of demand and supply chain planning in the modern global economy through the insightful content provided in this book. From achieving supply and demand balance to adapting to uncertainties like navigating white water rapids, the text delves into strategies for improving accur
3 views • 201 slides
Understanding Supply Chain Management (SCM) in Business
Supply Chain Management (SCM) involves a network of companies collaborating to produce and deliver products or services to end consumers. It comprises elements such as suppliers, manufacturers, warehouses, distribution centers, transportation systems, retail outlets, and customers. SCM aims to enhan
2 views • 15 slides
Enhancing Supply Chain Performance Through Collaborative Planning and Decision Support
This case study highlights how collaborative planning, forecasting, and replenishment strategies were implemented to improve supply chain performance at Cedars-Sinai. By addressing challenges such as low fill rates and lengthy cycle times caused by the pandemic and global events, a joint mission was
1 views • 14 slides
Achieve Desired Score in APICS Transformation for Supply Chain (CTSC) Exam
Click Here---> \/\/bit.ly\/3VE038d <---Get complete detail on CTSC exam guide to crack Supply Chain Management. You can collect all information on CTSC tutorial, practice test, books, study material, exam questions, and syllabus. Firm your knowledge on Supply Chain Management and get ready to crack
0 views • 18 slides
Achieve Desired Score in APICS Transformation for Supply Chain (CTSC) Exam
Click Here---> \/\/bit.ly\/3VE038d <---Get complete detail on CTSC exam guide to crack Supply Chain Management. You can collect all information on CTSC tutorial, practice test, books, study material, exam questions, and syllabus. Firm your knowledge on Supply Chain Management and get ready to crack
0 views • 18 slides
How to Prepare for CTSC exam on Supply Chain Management
Click Here--- \/\/bit.ly\/3UZHo68 ---Get complete detail on CTSC exam guide to crack Supply Chain Management. You can collect all information on CTSC tutorial, practice test, books, study material, exam questions, and syllabus. Firm your knowledge on Supply Chain Management and get ready to crack CT
2 views • 15 slides
How Traceability Software Can Help Supply Chain Management
Traceability software improves supply chain management by providing real-time visibility into the flow of goods from source to destination. It helps track and document every step of the supply chain, ensure transparency, improve product quality, and reduce the risk of fraud or error on. This softwar
1 views • 12 slides
Developing a Teaching Portfolio for Online Doctoral Workshop on Supply Chain Analytics
In this workshop, distinguished panelists including Ananth Iyer, Apurva Jain, Subodha Kumar, and Yao Zhao share insights and expertise on supply chain analytics. Topics include program introductions, audience engagement, format, content criteria, and analytics applications. Participants will gain va
1 views • 7 slides
Managing Covid-19 Cyber and Data Protection Risks
Exploring the risks and challenges related to cyber attacks and data protection amidst the Covid-19 pandemic. The agenda covers an overview of cyber-attacks, recent developments, protections against cyber attacks, data protection concerns during lockdown, compliance steps, and employee rights issues
1 views • 35 slides
Mitigation of DMA-based Rowhammer Attacks on ARM
Practical strategies are presented in "GuardION: Practical Mitigation of DMA-based Rowhammer Attacks on ARM" to defend against Rowhammer attacks on ARM architecture. The paper discusses Rowhammer defenses, RAMPAGE attacks on Android OS, and introduces GuardION as a lightweight mitigation approach. I
0 views • 48 slides
Cybersecurity and Supply Chain Risk Management Best Practices
Supply chain attacks pose a significant threat to software developers and suppliers by targeting source codes and build processes to distribute malware. This article discusses the importance of supply chain risk management, the various attack vectors involved, the industries at risk, and the repercu
0 views • 23 slides
Rutgers Business School Supply Chain Management Curriculum Overview
Explore Rutgers Business School's innovative Supply Chain Management Curriculum designed for high schools. The curriculum focuses on Project-Based Learning (PBL) and integrates essential elements such as significant content, 21st-century skills, in-depth inquiry, and more. The program is based on th
0 views • 15 slides
Understanding Denial-of-Service Attacks and Defense Strategies
Denial-of-Service attacks pose a serious threat where attackers flood networks with traffic, leading to system crashes and slowdowns. Explore the impact, expected results, and various categories of DoS attacks such as bandwidth attacks, protocol exceptions, and logic attacks. Learn how to defend aga
0 views • 61 slides
Understanding Network Denial of Service (DoS) Attacks
Network Denial of Service (DoS) attacks aim to disrupt services by overwhelming them with traffic. These attacks can occur at various layers of the network stack and exploit weaknesses to achieve their goal. Amplification attacks, such as the Smurf attack and DNS Amplification attack, can significan
2 views • 52 slides
Preventing Active Timing Attacks in Low-Latency Anonymous Communication
This research addresses the vulnerabilities of onion routing to timing attacks and proposes solutions to prevent active timing attacks, focusing on low-latency anonymous communication systems. Various problems related to timing attacks in onion routing are analyzed, including the role of adversaries
0 views • 52 slides
Managing Inventory in the Supply Chain: Tools, Techniques, and Strategies
This learning block delves into the crucial aspects of managing inventory in the supply chain, addressing demand variability, the bullwhip effect, and the role of third-party systems. Learners will explore the significance of inventory in supply chains, discuss tools for effective inventory manageme
0 views • 23 slides
Introduction to Supply Chain Management
Explore the key components of supply chains, the importance of supply chain management technology, and strategies to overcome challenges. Learn about supply chain visibility, the structure of supply chains, and the three segments - upstream, internal, and downstream. Discover how organizations acces
1 views • 29 slides
Strategies to Protect School Systems from Cyber Attacks
Schools are increasingly becoming targets of cyber attacks, making cybersecurity measures crucial. The article discusses the importance of responding to cyber attacks, creating incident response plans, and being vigilant against interception attacks. It outlines the steps to detect, document, and mi
0 views • 21 slides
Enhancing Supply Chain Insights Through Holistic Data Synthesis
Synthesizing economic data for comprehensive supply chain analysis, this talk by Krista Chan, Kevin Li, and Christian Moscardi from the U.S. Census Bureau discusses the goals, challenges, supply chain interests, data sources, and desired functionalities to present a holistic view of product supply c
0 views • 16 slides
Integrated Assessment and Modelling for Sustainable Biogas Supply Chains
The GroenGas sub-project I-AM focuses on integrating and synthesizing results from various sub-projects to assess innovations and improvements in biogas supply chains. The project aims to implement powerful options for sustainable supply chain management, including performance analysis, benchmarking
0 views • 14 slides
Decarbonising NRW's Supply Chain Emissions: Progress and Challenges
Dr. Anna Jones and her team are spearheading efforts in Wales to achieve net zero emissions by 2050, with a focus on decarbonising NRW's supply chain and the public sector. The Welsh public sector aims to collectively reach net zero by 2030, with a strong emphasis on reporting and reducing emissions
0 views • 10 slides
Understanding Supply in Economics
Explore the concept of supply in economics, including its definition, determinants, and graphical representation. Learn about the law of supply, non-price factors affecting supply, and key terms such as market supply and horizontal summation. Understand the difference between a change in quantity su
0 views • 30 slides
Utilizing Technology for Efficient Health Supply Chain Management in Pakistan During COVID-19
The USAID Global Health Supply Chain Program has supported Pakistan in leveraging its logistics management information system (LMIS) to efficiently plan and deliver critical COVID-19 supplies. Through coordination with government entities and use of various LMIS interfaces, Pakistan has enhanced dat
0 views • 12 slides
Understanding the Value Chain and Supply Chain Dynamics
The value chain involves adding value through a series of activities from producer to consumer, focusing on meeting consumer demands and gaining a competitive advantage. On the other hand, the supply chain focuses on efficient and cost-effective product distribution to meet consumer needs. The prima
0 views • 10 slides
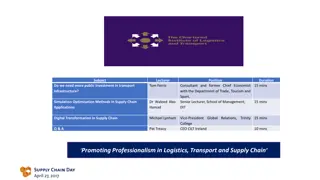
Digital Transformation in Supply Chain: Insights from Industry Experts
Explore the significance of digital transformation in supply chain management through expert insights from industry leaders like Michael Lynham and Dr. Waleed Abo-Hamad. Discover key components, drivers, and case studies showcasing the evolution and benefits of digital supply chains. Gain a deeper u
0 views • 28 slides
Enhancing Supply Chain Security and IT Governance: An Overview
This presentation delves into the critical aspects of supply chain security and IT governance, highlighting the synchronization of IT decisions across supply chains, global supply chain concerns, the cost implications of supply chain security lapses, and the need for more research and strategic alig
0 views • 28 slides
HUL Supply Chain Role Internship Insights 2021
Details about the Supply Chain Role Internship at Hindustan Unilever Limited (HUL), including duration, stipend, eligibility, internship program, selection process, resume tips, HR questions guidance, and companies offering similar internships. The internship talk, internship program details, intern
0 views • 9 slides
Understanding Supply Chain Management: Key Concepts and Processes
Supply chain management (SCM) involves the centralized management of goods and services flow, covering processes from raw materials to final products. By efficiently managing the supply chain, companies can reduce costs and improve product delivery. This seminar presentation explores the definition,
0 views • 24 slides
History of Software Supply Chain Attacks: A Comprehensive Overview
This content provides a detailed overview of the history of software supply chain attacks, highlighting significant incidents from various countries and industries. The narrative covers attacks dating back to 1982 and includes recent events such as the SolarWinds breach in 2020 and the novel depende
0 views • 21 slides
Automated Signature Extraction for High Volume Attacks in Cybersecurity
This research delves into automated signature extraction for high-volume attacks in cybersecurity, specifically focusing on defending against Distributed Denial of Service (DDoS) attacks. The study discusses the challenges posed by sophisticated attackers using botnets and zero-day attacks, emphasiz
0 views • 37 slides
Enhancing Supply Chain Efficiency with Quality Systems
Explore the best practices and methodologies for improving supply chain operations such as planning, sourcing, making, delivering, and returning. Discover key initiatives like E-procurement, bar coding, supplier quality assurance, and green supply chain to elevate functional excellence. Align supply
0 views • 28 slides
China-Africa Supply Chain Cooperation: Challenges and Opportunities
China-Africa Supply Chain Cooperation presents both challenges and opportunities for development. The growth of China-Africa supply chain is crucial, considering Africa's participation in the global supply chain mainly focused on providing primary products. The strategic importance of this relations
0 views • 19 slides
Clinical and Commercial Supply Chain Conference 2023
Annual conference on Clinical and Commercial Supply Chain Management featuring prominent industry leaders discussing the future state of supply chain strategies post-COVID-19. The event aims to educate, promote standardization, and improve connectivity among industry professionals. Work streams incl
0 views • 7 slides
Understanding Livestock Economics: The Law of Supply Explained
Exploring the concept of supply in livestock economics, this lecture covers theories, individual supply schedules, market supply schedules, and the law of supply. Dr. Puspendra Kumar Singh delves into the relationship between commodity prices and producer supply, offering insights into market dynami
0 views • 30 slides
Mattel's Toy Recalls and Supply Chain Management Crisis
Mattel faced a major crisis in 2007 with multiple toy recalls due to lead paint and design issues. The recalls mainly affected products manufactured in China, leading to a significant impact on the brand's reputation. While only 15% of the recalls were due to manufacturing errors, the incident shed
0 views • 30 slides
Targeted Deanonymization via the Cache Side Channel: Attacks and Defenses
This presentation by Abdusamatov Somon explores targeted deanonymization through cache side-channel attacks, focusing on leaky resource attacks and cache-based side-channel attacks. It discusses the motivation behind these attacks, methods employed, potential defenses, and the evaluation of such att
0 views • 16 slides
Understanding Network Security Vulnerabilities and Attacks
Explore the world of network security vulnerabilities and attacks, including Denial-of-Service (DoS) and Distributed-Denial-of-Service (D-DoS), security flaws in the TCP/IP protocol suite, ICMP attacks, routing attacks, and TCP attacks. Learn about common security vulnerabilities such as address spo
0 views • 36 slides
Enhancing Nepal's Agricultural Supply Chain for Sustainable Growth
Nepal's agricultural imports, dominated by staples, edible oil, vegetables, fruits, and more, indicate the need to strengthen the agricultural supply chain. Analyzing trade indicators reveals a trade deficit and the importance of optimizing supply chain management. The country's fragmented ASC manag
0 views • 12 slides