Airport Security Market to be Worth $25.27 Billion by 2031
\u00ae, the airport security market is projected to reach $25.27 billion by 2031, at a CAGR of 8.6% from 2024 to 2031. Some of the major factors driving the growth of this market are stringent government regulations for airport security and the growing number of air passengers. In addition, increasi
7 views • 5 slides
KEERTHI SECURITY - Best Security Agencies In Bangalore
Keerthi Security is a security and facility management services provider in Bangalore. We are committed to offering top-notch security services for commercial and residential places. We aim to offer very secure and reliable security services to everyone. Our best-trained security guards are very sha
10 views • 11 slides
CAMPUS SECURITY AUTHORITY (CSA) TRAINING CAMPUS SECURITY AUTHORITY (CSA) TRAINING
This content provides detailed information on Campus Security Authority (CSA) Training for university staff, faculty, contractors, and students responsible for student activities in compliance with the Jeanne Clery Disclosure of Campus Security Policy and Campus Crime Statistics Act. It covers the o
0 views • 15 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
0 views • 6 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
1 views • 6 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
1 views • 6 slides
Understanding the Role of Security Champions in Organizations
Security Champions play a vital role in decision-making concerning security engagement, acting as a core element in security assurance processes within a team. They foster a security culture, reduce dependency on the CISO, and promote responsible autonomy and continuous security education in the org
3 views • 13 slides
Emergency Response Proposed Rule - Worker Safety and Health Conference
The Emergency Response Proposed Rule aims to update regulations for worker safety and health, expanding coverage to include technical search and rescue and emergency medical service entities. The rule proposes replacing the existing Fire Brigades standard with an Emergency Response standard. Federal
3 views • 23 slides
Pascal's Rule in NMR Spectroscopy ( n+1 )
Pascal's Rule in NMR spectroscopy, also known as the (N+1) rule, is an empirical rule used to predict the multiplicity and splitting pattern of peaks in 1H and 13C NMR spectra. It states that if a nucleus is coupled to N number of equivalent nuclei, the multiplicity of the peak is N+1. The rule help
1 views • 30 slides
TSA Updates on Security Training Rule for OTRB Companies
In the recent updates by TSA, the Security Training Rule for over-the-road bus (OTRB) companies has been highlighted. The rule mandates TSA-approved security training for employees in security-sensitive roles, emphasizing key requirements and elements of security training. Urban areas covered by the
1 views • 18 slides
Understanding the Roles of a Security Partner
Learn about the roles and responsibilities of a Security Partner, including requesting changes to security roles, approving security requests, and initiating access requests. Explore the overview of Workday Security, the security access request process, and the pre-request process flow. Discover how
2 views • 17 slides
Compliance Guide for Rule 205: Emission Offsets & Mobile Source Credits
Rule 205 outlines the process for generating emission offsets through voluntary mobile source emission reduction credits in Maricopa County. The rule-making process, state implementation plan submission, and permit conditions related to Rule 205 are discussed. The preparation for compliance includes
0 views • 7 slides
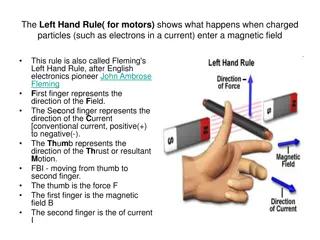
Understanding Fleming's Left Hand Rule and Electric Motors
Fleming's Left Hand Rule, also known as the Left Hand Rule for Motors, explains the interaction between charged particles and magnetic fields. Electric motors utilize this principle to convert electrical energy into mechanical energy through the interaction of magnetic fields and current-carrying co
2 views • 6 slides
Certification and Training in Information Security
This content covers various aspects of certification and training in the field of information security, including organizational information security outlines, positions in information security personnel, and professional certifications from renowned organizations. It also provides insights into dif
0 views • 18 slides
Understanding the Rule of Law and Legal Systems in Wales and England
The content discusses the nature of law, the Welsh and English legal systems, and the Rule of Law doctrine. It includes observations from the 2019 AS Law Unit 1 examination, emphasizing the importance of adhering to rubrics and answering questions clearly. Candidates faced challenges with timing and
0 views • 14 slides
Phase 2 Comprehensive Rule Update Legislative Rule Package Overview
Seven subdivision bills were adopted during the 2023 session, covering various topics such as independent reviewers, cut and fill systems, connection to public sewer systems, and more. The public comment period and hearing are scheduled, with the draft rule to respond to comments by August 25. A bil
3 views • 17 slides
Michigan Revised Lead and Copper Rule Implementation Experience
The Michigan Department of Environment, Great Lakes, and Energy shares insights on the implementation of the Michigan Revised Lead and Copper Rule. Key topics include rule revisions, data outcomes, challenges, and development drivers. The rule aims to reduce lead levels, update sampling protocols, a
0 views • 26 slides
EPA Rule 40 CFR Part 63 Subpart HHHHHH Overview
EPA Rule 40 CFR Part 63 Subpart HHHHHH, also known as The Refinisher Rule, sets standards for hazardous air pollutants in paint stripping and surface coatings operations. The rule aims to control emissions of target hazardous air pollutants in collision centers and surrounding areas. It outlines req
0 views • 20 slides
Understanding the Mailbox Rule in Contract Law
The Mailbox Rule, a common law principle, stipulates that acceptance of an offer is valid when dispatched, providing certainty in contract formation. This rule is illustrated through scenarios involving delays in mail delivery and parties' need for assurance in contractual agreements. The examples h
0 views • 14 slides
Evolution of Theory and Knowledge Refinement in Machine Learning
Early work in the 1990s focused on combining machine learning and knowledge engineering to refine theories and enhance learning from limited data. Techniques included using human-engineered knowledge in rule bases, symbolic theory refinement, and probabilistic methods. Various rule refinement method
0 views • 12 slides
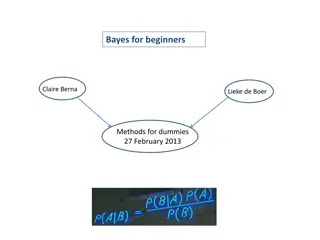
Understanding Bayes Rule and Its Historical Significance
Bayes Rule, a fundamental theorem in statistics, helps in updating probabilities based on new information. This rule involves reallocating credibility between possible states given prior knowledge and new data. The theorem was posthumously published by Thomas Bayes and has had a profound impact on s
0 views • 34 slides
Understanding Security in World Politics
Security studies delve into the intricate processes of defining and addressing security threats in global politics. It explores the contested nature of security definitions, emphasizes the political significance of security, and challenges the conventional boundaries of International Relations. The
0 views • 8 slides
History and Implementation of Military Munitions Rule
The history and implementation of the Military Munitions Rule, including its origins in regulations like RCRA and FFCA, the involvement of key stakeholders, identification of issues in rulemaking, and ensuring safe transportation and storage of hazardous waste. The process involved extensive consult
0 views • 26 slides
Comprehensive Course Review: Security Research Cornerstones at Carnegie Mellon University
Dive into the essential topics of software security, network security, OS security, and cryptography in the course offered by Vyas Sekar at Carnegie Mellon University. Explore control flow hijacks, cryptography terminology, and the importance of network security in protecting data transmissions. Lea
1 views • 41 slides
UIC Security Division Overview and International Activities
The UIC Security Division plays a crucial role in supporting the security platform of the International Union of Railways (UIC). Headed by Jacques Colliard, the division is based in Paris and consists of key personnel like Marie-Hélène Bonneau, Jos Pires, and Laetitia Granger. The division's activ
0 views • 12 slides
Introduction to Bayes' Rule: Understanding Probabilistic Inference
An overview of Bayes' rule, a fundamental concept in probabilistic inference, is presented in this text. It explains how to calculate conditional probabilities, likelihoods, priors, and posterior probabilities using Bayes' rule through examples like determining the likelihood of rain based on a wet
0 views • 21 slides
Understanding the New VA Pension Benefit Rule of October 11, 2018
VA Task Force members presented key changes in the VA pension benefit rule, focusing on net worth limits, transfer rules, exclusions, look-back periods, and penalties. The rule aims to uphold program integrity and align with GAO recommendations, impacting eligibility criteria for applicants. Key sec
11 views • 55 slides
U.S. EPA's Proposed Cross-State Air Pollution Rule Update for 2008 Ozone NAAQS
The U.S. Environmental Protection Agency (EPA) issued the Cross-State Air Pollution Rule (CSAPR) in 2011, aiming to improve air quality by reducing power plant emissions across state lines. Challenges and subsequent revisions led to the proposed CSAPR Update Rule in 2015, targeting interstate air po
0 views • 27 slides
Automating Security Operations Using Phantom
Isabella Minca, an intern for 4 months in the Security Team at Adobe, presents an overview of automating security operations using Phantom. The presentation covers goals, security alerts, Phantom playbooks, handling security data, and the capabilities of Phantom in orchestrating security responses.
0 views • 28 slides
Implications of ABA Model Rule 8.4(g) on Professional Conduct
The American Bar Association's Model Rule 8.4(g) addresses professional misconduct in legal practice related to discrimination and harassment based on various factors. The rule has been adopted by some states, sparking discussions on its implications and challenges within the legal community. Explor
0 views • 67 slides
Understanding HTTP Security Headers for Web Apps
Explore the importance of HTTP security headers on web applications through a detailed breakdown of headers like HSTS, XFO, XSS, CSP, CTO, RH, and FP. Learn how these headers enhance security by instructing browsers on handling website content, preventing various attacks. Gain insights on configurin
1 views • 68 slides
Ethics & Constitutional Limits on Attorney Expression Webinar
Join the live 90-minute webinar on Ethics: Model Rule 8.4(g) and Constitutional Limits on Regulating Attorney Expression of Unpopular Positions featuring expert faculty members. Explore regulations governing lawyer speech and the requirements for lawyer communication in various contexts. Learn about
0 views • 57 slides
Upholding the Rule of Law for Sustainable Economic Growth in Europe
Democracy and the rule of law are essential for sustained economic growth in Europe. The rule of law ensures stable and impartial enforcement of rules such as property rights and contract law, key for market economies. Upholding the rule of law is crucial for combating corruption and maintaining a f
0 views • 6 slides
Bayes’ Rule
Bayes Rule, a fundamental concept in statistics, explores how prior beliefs are updated based on new evidence. This rule, named after Thomas Bayes, has had a profound impact on statistical inference and has been further developed by mathematicians like Laplace. Exploring the probabilistic reasoning
0 views • 34 slides
Modular Security Analysis for Key Exchange and Authentication Protocols
Explore the modular security analysis approach used to examine the security of key exchange and authentication protocols, focusing on the universally composable authentication with a global Public Key Infrastructure. The analysis involves splitting the system into smaller components, separately anal
1 views • 15 slides
Revolutionizing Security Testing with BDD-Security
Explore the innovative approach of Continuous and Visible Security Testing with BDD-Security by Stephen de Vries. Gain insights into how security testing can be integrated seamlessly into modern development practices, shifting the focus from reactive to proactive measures. Learn about the importance
0 views • 33 slides
Comprehensive DevOps Security Training Overview
This Certified DevOps Security Practitioner course provides a deep dive into implementing DevSecOps, integrating security into the DevOps processes. Covering topics like security testing, Docker security, automation, and more, the training aims to equip participants with the necessary skills to embe
0 views • 5 slides
Office 365 Email & Security Workshop Highlights
Office 365 Email & Security workshop was held with presenters Jason Hetterle, Steve Garcia, and Joseph Andreason covering topics like security awareness, self-service password reset, Office 365 webmail features, and more. The agenda included discussions on security measures, a case study on an anato
0 views • 9 slides
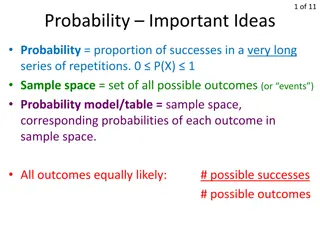
Understanding Probability: Key Concepts and Rules
Probability is the proportion of successes in a long series of repetitions. Important ideas include the 0-1 Rule, the 100% Rule, the Complement Rule, the Addition Rule, and the Multiplication Rule. These rules govern the calculation of probabilities in various scenarios. Learn the fundamental princi
0 views • 16 slides
Understanding Security Testing and Architecture
Explore the fundamentals of security testing, computer security goals, software security approach, and security architecture. Learn about securing computer assets, verifying trustworthiness of security mechanisms, and validating security architecture through threat modeling. Enhance your knowledge o
0 views • 57 slides