Scheme of Reservation and Delegation (SoRD)
The roles and responsibilities of the Chief Finance Officer and Director of Governance and Assurance at NHS Sussex Board, including their authority to approve applications and propose amendments to the organization's constitution and governance handbook. It also covers their involvement in decision-
20 views • 12 slides
Active Directory Delegation, cionsystems.com
The Active Directory Manager Pro features active directory delegation which can help organizations to reduce the number of high privilege accounts thereby reducing risk and enhancing security. https:\/\/shorturl.at\/uLNP7
2 views • 7 slides
Parsimoni – the European IoT/Edge OS. Secure, efficient, flexible.
Revolutionizing IoT/Edge computing with secure, efficient, and flexible technology, Parsimoni aims to set new standards in the industry. Led by CEO Miklos Tomka, the company leverages European open-source technology to create a secure-by-design OS for IoT/Edge applications. Seeking partners for cons
1 views • 5 slides
Understanding Secure Act 2.0 Key Provisions
In a detailed report by Dee Spivey and Angie Zouhar, key provisions of SECURE Act 2.0 are outlined, including changes in retirement plans like RMD age increase, employee certification of hardship withdrawals, and more. Secure 1.0 and Secure 2.0 differences, effective dates, and necessary actions for
5 views • 12 slides
Effective People Management Skills and Delegation in Business Administration
Successful people managers exhibit qualities such as autonomy, feedback, interpersonal skills, ethics, and effective delegation. Delegation involves giving scope, responsibility, and authority, supported by training and development, to increase efficiencies and flexibility in the workplace.
0 views • 12 slides
Understanding Delegation of Authority and Management by Objectives
The lesson on delegation of authority and management by objectives covers the process of delegating authority, implementing authorities, management by objectives, and the importance of preparedness plans and agreements. It discusses the authority having jurisdiction, scope of authority, and the dele
1 views • 31 slides
Introduction to SFTP & PGP Encryption for Secure Data Transfer
Discover how to ensure reliable data transfer, make informed decisions, and gain a strategic advantage through the use of Secure File Transfer Protocol (SFTP) and Pretty Good Privacy (PGP) encryption. The session includes demonstrations on PGP encryption and SFTP access, along with insights on setti
1 views • 22 slides
Understanding Delegation of Authority in Management
Delegation of authority in management is a crucial process where managers assign tasks to subordinates, allowing them to exercise authority on their behalf. Louis A. Allen defined authority as the rights entrusted to a position holder to enable task performance. Effective delegation involves element
0 views • 13 slides
Understanding Delegatus Non Potest Delegare in Legal Context
Delegatus non potest delegare, a Latin maxim, signifies that a person delegated with authority cannot further delegate it unless explicitly authorized. This principle is fundamental in administrative and agency law, ensuring trust and accountability in decision-making processes. The maxim was illust
1 views • 8 slides
Vanuatu Delegation Preparation for COP27 NAB Meeting
The Vanuatu delegation is gearing up for the COP27 NAB Meeting scheduled for April 20th, 2022. The COP is vital for reviewing the implementation of the Convention and making decisions to enhance its effectiveness. Resolutions were made to retain COP26 Delegates and engage in preparatory activities f
1 views • 7 slides
University Procurement Policies and Delegation Guidelines - October 2021
This presentation covers the definition of confirming orders, university and procurement policies regarding unauthorized commitments, delegation of procurement responsibilities, and the importance of following proper procedures to avoid personal liability for costs. It emphasizes the necessity of ob
4 views • 25 slides
Ensuring Secure Testing Environments in Oregon Education System
Oregon's Statewide Assessment System (OSAS) emphasizes the critical need for secure testing environments to maintain the validity and accuracy of assessment data. This includes handling secure printed test materials, identifying and preventing improprieties, and reporting any irregularities. From ma
2 views • 20 slides
Enhancing Nursing Delegation Through Technology: A Pilot Project
This presentation discusses the importance of delegation in nursing, introduces a pilot project involving a software-based delegation system, identifies the problem of lack of knowledge around RN delegation, outlines a change model, presents a PICO question on the impact of delegation tools on patie
0 views • 20 slides
Safe & Secure Gaming Platform Is Online Cricket ID In India
The most secure and safe gaming platform in India is Online Cricket ID. Faster withdrawals within 5 minutes with your online cricket ID. Secure and trusted online cricket and casino ID provider with 24x7 customer support.\nVisit for more information:
1 views • 3 slides
Understanding Directors' Duties and Responsibilities in Corporate Governance
This presentation explores the statutory duties of directors under the Companies Act 2014 and Irish common law, emphasizing best practices for fulfilling these responsibilities. It covers the role of directors as trustees of company assets, management delegation, and the authority of directors to bi
0 views • 31 slides
Secure Computation Techniques in RAM Models with Efficient Automation
Explore the automation of efficient RAM-model secure computation techniques, including examples such as secure binary search. Discover how traditional solutions using circuit abstractions can be improved for sub-linear time computation through methods like Oblivious RAM. Learn about techniques such
0 views • 37 slides
COIL4PURPOSE Southeast Asia Delegation Visit to Duy Tan University 8-9th March 2024
This document outlines the COIL4PURPOSE Southeast Asia Delegation Visit to Duy Tan University, including the purpose, projects, partners, and key takeaways. Projects discussed include psychology and district nursing with international collaboration and student engagement at the core. The visit focus
0 views • 5 slides
Tamper-Evident Pairing (TEP) Protocol for Secure Wireless Pairing Without Passwords
This article discusses the challenges of traditional secure wireless pairing methods that rely on password validation and proposes the Tamper-Evident Pairing (TEP) protocol as a secure in-band solution to protect against Man-in-the-Middle (MITM) attacks. TEP eliminates the need for out-of-band chann
1 views • 40 slides
RND Contractor Meeting: December 14, 2022
Agenda for the RND Contractor Meeting on December 14, 2022 includes welcoming participants, introductions, interpreter services, secure email information, meeting dates, and times for 2023. Instructions on using interpreter services and secure email systems are provided. Meeting notes will be posted
0 views • 6 slides
Actively Secure Arithmetic Computation and VOLE Study
Exploring actively secure arithmetic computation and VOLE with constant computational overhead at Tel Aviv University. Understanding how functions are represented in secure computation using arithmetic circuits over boolean circuits. Efficiently evaluating arithmetic circuits over large finite field
0 views • 36 slides
Accessing and Utilizing CPCSSN Secure Research Environment (SRE)
Learn how to access the CPCSSN Secure Research Environment (SRE) for secure data analysis. Follow steps such as setting up VPN, accessing SQL databases, and establishing ODBC connections for statistical analysis using tools like SAS, R, SPSS, or Stata. Enhance your research capabilities within a sec
0 views • 12 slides
Homomorphic Encryption Overview
Homomorphic encryption allows computation on encrypted data without revealing the underlying information. It enables secure delegation of data processing to a server while maintaining privacy. The process involves key generation, encryption, decryption, and evaluation of functions on encrypted data.
0 views • 40 slides
Enhancing Animal Telemetry Data Systems for Secure Collaboration
Wide spectrum of animal telemetry data collection protocols and platforms require enhanced data stewardship options for secure sharing before public release. The need for a more granular understanding of available data and structured systems integration is crucial. Initial workflow involves providin
0 views • 4 slides
STM32WB BLE Secure Connections Overview
This detailed content provides insights into the secure connections in STM32WB BLE devices, covering aspects such as BLE security methods, encryption techniques, pairing processes, key distribution, and security modes and levels. It emphasizes the use of Long Term Keys (LTK), Diffie-Hellman key exch
0 views • 12 slides
Understanding Secure Electronic Transactions (SET)
Secure Electronic Transactions (SET) is an encryption and security specification designed to protect credit card transactions on the Internet. SET provides a secure way to utilize existing credit card payment infrastructure on open networks, such as the Internet, involving participants like clients,
1 views • 6 slides
An Open-Source SPDM Implementation for Secure Device Communication
This article introduces an open-source SPDM (Secure Protocol and Data Model) implementation for secure device communication, developed by Jiewen Yao and Xiaoyu Ruan, Principal Engineers at Intel. SPDM aims to enhance device security through protocols for device authentication, session key establishm
0 views • 29 slides
Exploring Secure Care Services in Scotland
Delve into the world of secure care services in Scotland, focusing on achievements, challenges, and opportunities in providing youth justice. Learn about trends in secure care, reduction in costs, reasons for referrals, and evidence-based programs like DBT in Glasgow. Gain insights from industry lea
0 views • 77 slides
Understanding Secure PRFs and PRPs in Cryptography
Dive into the world of secure Pseudo-Random Functions (PRFs) and Pseudo-Random Permutations (PRPs) in cryptography. Learn about the definitions, security criteria, and examples of secure PRFs and PRPs such as 3DES and AES. Explore the concepts of secure block ciphers and key principles behind these
0 views • 54 slides
Best Practices for Testing Domain Delegation
Develop a comprehensive approach to testing domain delegation, focusing on creating explicit requirements and a modular tool like Zonemaster. Emphasize the importance of setting specific, measurable, realistic, and time-bound requirements for correct delegation. Discuss the need for tools to detect
0 views • 20 slides
Understanding Unidirectional Updatable Encryption and Proxy Re-Encryption
Unidirectional updatable encryption and proxy re-encryption are key concepts in secure cryptography deployments. Key management and rotation are essential for secure encryption schemes such as Proxy Re-Encryption (PRE) and Updatable Encryption (UE). PRE allows delegation of decryption abilities, whi
0 views • 16 slides
APNIC Internet Resource Analyst Update
Anna Mulingbayan, Senior Internet Resource Analyst and Liaison Officer at APNIC, provides updates on IP address and ASN delegation in the Asia-Pacific region. The content covers IPv4 exhaustion, delegation policies, last /8 delegations, and key policies implemented in 2011. Additionally, it discusse
0 views • 18 slides
Foundations of Cryptography: Secure Multiparty Computation
Explore the foundations of cryptography with insights into secure multiparty computation, including the Secure 2PC from OT Theorem and the Two-Party Impossibility Theorem. Delve into the impossibility of 2-Party Secure MPC, claims, and exercises on extending to statistical security. Learn about redu
0 views • 39 slides
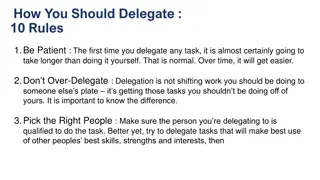
Effective Delegation: 10 Rules to Master the Skill
Developing successful delegation skills is crucial for effective leadership. Follow these 10 rules to delegate tasks efficiently: Be patient, avoid over-delegating, choose the right people, explain the reason for delegation, provide specific instructions, offer training, check in regularly, avoid mi
0 views • 4 slides
Mastering Delegation for Organizational Simplification
Dive into the world of delegation with insights on what to keep and what to give away, the importance of delegation, how it simplifies life, and why it is crucial for personal and team growth. Uncover the key points, beliefs, and actions that drive effective delegation strategies to enhance producti
0 views • 30 slides
Effective Delegation Strategies in USCG Auxiliary Leadership
Delegation is vital in the USCG Auxiliary, requiring careful consideration of individuals' skills, workload, and goals. Successful delegation involves clearly articulating outcomes, providing support, maintaining control through timelines and reviews. By following these steps, delegation can be done
0 views • 5 slides
Island Health Nursing Support Services (NSS) Delegation Overview
Island Health Nursing Support Services (NSS) provides delegation in schools to support children's complex health needs. Delegation involves two parts: the individual nurse decision to delegate and adherence to organizational policies, professional standards, and regulations. Referrals to NSS must be
0 views • 13 slides
U.S. Constitutional Law I(T) Fall 2023: Non-Delegation Doctrine Overview
Exploring the Non-Delegation Doctrine in U.S. Constitutional Law, this content delves into the background, current doctrine, historical cases, and contextual considerations related to congressional delegation of regulatory powers. It addresses the constitutionality of Congress authorizing bodies suc
0 views • 46 slides
Role of Effective Delegation in Personnel Management in Education
Delegation plays a crucial role in management within the educational system by empowering individuals to carry out specific tasks. This process involves assigning responsibility and authority to others while remaining accountable for the outcome. Understanding the benefits, process, reasons for relu
0 views • 23 slides
Efficient Delegation in Financial Decision Making
Analyzing the life cycle of financial advice reveals that most individuals lack the time, interest, or knowledge to manage their finances effectively. Delegating financial decision-making early can be beneficial, with customized advice outperforming simple target date funds. However, delegation opti
0 views • 19 slides
Understanding Secure Messaging and Encryption Techniques
Explore the possibilities of sending secure messages through encryption without the need for advanced degrees in Computer Science or Math. Learn about symmetric and asymmetric key encryption methods, the use of PGP for secure messaging, and the concept of shared-key encryption. Discover the intricac
0 views • 16 slides