Understanding Secure Act 2.0 Key Provisions
In a detailed report by Dee Spivey and Angie Zouhar, key provisions of SECURE Act 2.0 are outlined, including changes in retirement plans like RMD age increase, employee certification of hardship withdrawals, and more. Secure 1.0 and Secure 2.0 differences, effective dates, and necessary actions for
5 views • 12 slides
Mastering Business Writing Skills: A Comprehensive Guide
Understanding the essence of business communication, types of communication, essentials of effective communication, smart communication tips, and communication across cultures is vital for professional success. Explore verbal, written, and non-verbal communication methods to enhance your communicati
0 views • 47 slides
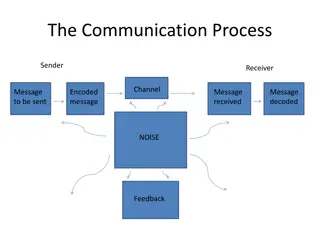
Understanding Communication and Sign Language
Communication is the vital process of exchanging information, ideas, and emotions through various channels such as speech, signals, and writing. This includes verbal and non-verbal communication, where sign language plays a crucial role. Effective communication depends on the sender, message, channe
1 views • 31 slides
Introduction to SFTP & PGP Encryption for Secure Data Transfer
Discover how to ensure reliable data transfer, make informed decisions, and gain a strategic advantage through the use of Secure File Transfer Protocol (SFTP) and Pretty Good Privacy (PGP) encryption. The session includes demonstrations on PGP encryption and SFTP access, along with insights on setti
1 views • 22 slides
Enhancing Zoonotic Disease Risk Communication in Public Health Emergencies
Explore the significance of adopting a One Health approach to zoonotic disease risk assessment and communication in the context of emergency health situations. The session emphasizes core capacities required by the International Health Regulations (IHR) 2005, effective risk communication processes,
2 views • 13 slides
Effective Communication Skills for Healthcare Professionals
Enhance your communication skills with the Accelerated Preceptorship Communication Session by Desiree Cox. Learn the importance of effective communication, different communication preferences, communication dynamics, non-verbal communication, listening skills, and more. Understand the communication
2 views • 28 slides
Ensuring Secure Testing Environments in Oregon Education System
Oregon's Statewide Assessment System (OSAS) emphasizes the critical need for secure testing environments to maintain the validity and accuracy of assessment data. This includes handling secure printed test materials, identifying and preventing improprieties, and reporting any irregularities. From ma
2 views • 20 slides
Secure Computation Techniques in RAM Models with Efficient Automation
Explore the automation of efficient RAM-model secure computation techniques, including examples such as secure binary search. Discover how traditional solutions using circuit abstractions can be improved for sub-linear time computation through methods like Oblivious RAM. Learn about techniques such
0 views • 37 slides
Enhancing Cybersecurity in University Research: Insights from SouthEast SECURE Program
The SouthEast SECURE program at universities like Clemson and University of Alabama focuses on improving cybersecurity for NSF-funded research projects. It provides metrics, communication facilitation, and practical assistance to enhance data security. The program aims to support researchers in util
0 views • 22 slides
Tamper-Evident Pairing (TEP) Protocol for Secure Wireless Pairing Without Passwords
This article discusses the challenges of traditional secure wireless pairing methods that rely on password validation and proposes the Tamper-Evident Pairing (TEP) protocol as a secure in-band solution to protect against Man-in-the-Middle (MITM) attacks. TEP eliminates the need for out-of-band chann
1 views • 40 slides
Evolution of Proofs in Cryptography
Cryptography has evolved from classical proofs to interactive and probabilistically checkable proofs, enabling the development of applications like Non-Malleable and Chosen-Ciphertext Secure Encryption Schemes. Non-Malleability protects against active attacks like malleability and chosen-ciphertext
0 views • 29 slides
Effective Communication Strategies in Business Environments
Explore the various aspects of communication processes within organizations, including sender-receiver dynamics, communication channels, small group networks, upward and downward communication methods, business communication tools, information richness of channels, email and voice mail etiquette, an
0 views • 21 slides
Actively Secure Arithmetic Computation and VOLE Study
Exploring actively secure arithmetic computation and VOLE with constant computational overhead at Tel Aviv University. Understanding how functions are represented in secure computation using arithmetic circuits over boolean circuits. Efficiently evaluating arithmetic circuits over large finite field
0 views • 36 slides
Cryptography and Information Security Fundamentals
Explore the fundamental concepts of cryptography and information security, including Shannon's Coding Theorems, secure communication terminology, and information security concerns related to confidentiality, authenticity, and integrity. Dive into topics like compression for efficient communication,
0 views • 41 slides
Accessing and Utilizing CPCSSN Secure Research Environment (SRE)
Learn how to access the CPCSSN Secure Research Environment (SRE) for secure data analysis. Follow steps such as setting up VPN, accessing SQL databases, and establishing ODBC connections for statistical analysis using tools like SAS, R, SPSS, or Stata. Enhance your research capabilities within a sec
0 views • 12 slides
Understanding Classroom Communication and Management by Ramkrishna Chakraborty
Communication is a vital process of exchanging information, ideas, and opinions between individuals. In the educational context, effective communication is essential for achieving desired behavior patterns. This article explores the meaning, concept, and types of communication, emphasizing the impor
1 views • 19 slides
Effective Communication Strategies in Public Health Incident Leadership
Learn about the importance of effective communication within emergency operations centers during public health incidents. Explore communication tools, techniques, and case examples of communication failures. Discover key aspects such as team communication, situational awareness, shared mental models
0 views • 16 slides
Communication Protocols for System Integration
This technical document explores various communication protocols used for system integration, focusing on mailbox communication, interprocessor communication, system communication using IPCC, and BLE communication utilizing different IPCC channels. The document delves into the features, functions, a
1 views • 6 slides
Enhancing Animal Telemetry Data Systems for Secure Collaboration
Wide spectrum of animal telemetry data collection protocols and platforms require enhanced data stewardship options for secure sharing before public release. The need for a more granular understanding of available data and structured systems integration is crucial. Initial workflow involves providin
0 views • 4 slides
Understanding Secure Information Transmission in Cryptography
Explore the concepts of secure information confidentiality, integrity, and authenticity in the realm of cryptography, including digital signatures, signcryption, and the challenges faced in ensuring secure communication. Delve into the attempts to encrypt, authenticate, and solve issues like non-rep
0 views • 23 slides
Quantum Key Agreements and Random Oracles
This academic paper explores the impossibility of achieving key agreements using quantum random oracles, discussing the challenges and limitations in quantum communication, cryptographic protocols, quantum computation, and classical communication. The study delves into the implications of quantum ra
0 views • 29 slides
Secure Method of Information Exchange: Overview of Hub Concept & Prototype
This document presents an overview of the Hub Concept & Prototype for Secure Method of Information Exchange (SMIE) developed in April 2013 by New Zealand and the USA. It discusses drivers, ePhyto transmission options, Direct NPPO to NPPO ePhyto exchange, Hub/Cloud communication, security mechanisms,
0 views • 20 slides
Effective Communication Skills in Business Environment
Understand the importance of communication in organizations, learn about the process of communication, main objectives, types, and patterns of communication. Explore key points such as accuracy in conveying ideas, feedback, and communication channels. Enhance your knowledge on downward, upward, and
0 views • 24 slides
Mastering Effective Communication Skills in Daily Life
Enhance your communication skills with insights from Unit 5 Communication. Learn about different types of communication, speaking skills, effective communication strategies, assertiveness, and more. Understand the nuances of verbal, nonverbal, and paralanguage communication to convey your message cl
0 views • 52 slides
STM32WB BLE Secure Connections Overview
This detailed content provides insights into the secure connections in STM32WB BLE devices, covering aspects such as BLE security methods, encryption techniques, pairing processes, key distribution, and security modes and levels. It emphasizes the use of Long Term Keys (LTK), Diffie-Hellman key exch
0 views • 12 slides
Understanding Secure Electronic Transactions (SET)
Secure Electronic Transactions (SET) is an encryption and security specification designed to protect credit card transactions on the Internet. SET provides a secure way to utilize existing credit card payment infrastructure on open networks, such as the Internet, involving participants like clients,
1 views • 6 slides
Linear Communication in Secure Multiparty Computation for Efficient and Fast Processing
The research focuses on achieving perfectly secure multiparty computation (MPC) with linear communication and constant expected time. It explores efficient approaches using a broadcast-hybrid model and P2P communication, aiming to balance speed and efficiency in MPC. The study highlights the importa
0 views • 23 slides
An Open-Source SPDM Implementation for Secure Device Communication
This article introduces an open-source SPDM (Secure Protocol and Data Model) implementation for secure device communication, developed by Jiewen Yao and Xiaoyu Ruan, Principal Engineers at Intel. SPDM aims to enhance device security through protocols for device authentication, session key establishm
0 views • 29 slides
Exploring Secure Care Services in Scotland
Delve into the world of secure care services in Scotland, focusing on achievements, challenges, and opportunities in providing youth justice. Learn about trends in secure care, reduction in costs, reasons for referrals, and evidence-based programs like DBT in Glasgow. Gain insights from industry lea
0 views • 77 slides
Understanding Secure PRFs and PRPs in Cryptography
Dive into the world of secure Pseudo-Random Functions (PRFs) and Pseudo-Random Permutations (PRPs) in cryptography. Learn about the definitions, security criteria, and examples of secure PRFs and PRPs such as 3DES and AES. Explore the concepts of secure block ciphers and key principles behind these
0 views • 54 slides
Effective Communication in Workplace Safety Training
This presentation covers the importance of effective communication in workplace safety training, emphasizing the elements of a communication plan, communication processes, and the realities of communication. It explores the consequences of failure to communicate safety information effectively and di
0 views • 31 slides
Communication Costs in Distributed Sparse Tensor Factorization on Multi-GPU Systems
This research paper presented an evaluation of communication costs for distributed sparse tensor factorization on multi-GPU systems. It discussed the background of tensors, tensor factorization methods like CP-ALS, and communication requirements in RefacTo. The motivation highlighted the dominance o
0 views • 34 slides
Strategic Communication Goals and Objectives
Clearly defining goals and objectives is essential in strategic communication. This involves setting realistic and aligned targets, such as building communication capacity, influencing policy, and engaging public will. Communication plays a crucial role in achieving social change and programmatic su
0 views • 67 slides
Advances in Authenticated Garbling for Secure 2PC
The research discusses advancements in authenticated garbling for achieving constant-round malicious secure 2PC using garbled circuits. It emphasizes the utilization of correlated randomness setup and efficient LPN-style assumptions to enhance communication efficiency significantly. Various techniqu
0 views • 30 slides
Foundations of Cryptography: Secure Multiparty Computation
Explore the foundations of cryptography with insights into secure multiparty computation, including the Secure 2PC from OT Theorem and the Two-Party Impossibility Theorem. Delve into the impossibility of 2-Party Secure MPC, claims, and exercises on extending to statistical security. Learn about redu
0 views • 39 slides
Exploration of Cryptography and Secure Communication Methods
Delve into the concepts of cryptography, data hiding, and secure communication methods such as Diffie-Hellman key exchange. Discover how Bob safely sends a ring to Alice, the use of Caesar cipher method, and the importance of mathematical principles in ensuring secure communication protocols. Learn
0 views • 22 slides
Implementing VPN for Secure Corporate Communication
A Virtual Private Network (VPN) offers a secure method for corporations with multiple sites to transfer data over the Internet while maintaining confidentiality. By encrypting data and using tunneling techniques, VPN software ensures that communications remain private, making it a cost-effective and
0 views • 10 slides
Advanced Building Intercom Solution: Secure Communication for Property Developers
Explore the cutting-edge Building Intercom Solution for secure and feature-rich communication in residential colonies, housing complexes, and commercial spaces. This solution offers reliable and flexible PBX connectivity over IP, enhancing internal communication among residents while providing value
0 views • 17 slides
Specialization in International Business Communication (SIBC)
Specialization in International Business Communication (SIBC) offered by the Department of Business Communication focuses on the critical role of communication in various business settings, emphasizing skills in language usage, communicative competence, and strategic language application. The progra
0 views • 11 slides
Understanding Secure Messaging and Encryption Techniques
Explore the possibilities of sending secure messages through encryption without the need for advanced degrees in Computer Science or Math. Learn about symmetric and asymmetric key encryption methods, the use of PGP for secure messaging, and the concept of shared-key encryption. Discover the intricac
0 views • 16 slides