Good Laboratory Practices Study Protocols for Effective Research Management
Supplemental materials providing detailed protocols for implementing Good Laboratory Practices (GLP) in research settings. The protocols cover GLP requirements, experimental design, reading regulatory sections, approval processes, amendments, circulation lists, and study plans. These materials aim t
0 views • 22 slides
Update on SWAG Protocols and New NICE TA Progress Report
Kate Gregory leads the SWAG Protocols update for March 2024, with advancements in new protocols and NICE TA updates. A comparison of activities from Oct 2023 to Mar 2024 shows progress in issuing, reviewing, and drafting protocols. The latest NICE TA additions include treatments for advanced cancers
5 views • 13 slides
New Student Sessions 2023 - MCDB & MIMG Advising Information
The New Student Sessions 2023 offer valuable resources and advising information for Molecular, Cell, and Developmental Biology (MCDB) as well as Microbiology, Immunology, and Molecular Genetics (MIMG) undergraduate majors at UCLA. Learn about MCDB and MIMG major requirements, upper-division core cou
0 views • 21 slides
Understanding Consistency Protocols in Distributed Systems
Today's lecture covers consistency protocols in distributed systems, focusing on primary-based protocols and replicated-write protocols. These protocols play a crucial role in ensuring consistency across multiple replicas. One example discussed is the Remote-Write Protocol, which enforces strict con
0 views • 35 slides
Oklahoma School Safety Protocols Overview
Overview of the school safety protocols in Oklahoma, which define requirements based on COVID-19 alert levels per capita in each county. The protocols include instructions for different alert levels, mask recommendations, visitor limitations, and activity guidelines. Schools are expected to offer in
0 views • 9 slides
Work Protocols and Safety Measures for Employees Returning to Work
In the wake of the COVID-19 pandemic, these work protocols emphasize roles, responsibilities, and mental wellbeing of employees. Pre-work precautions at home, personal measures, testing procedures, increasing awareness, and safe travel guidelines are highlighted to ensure a secure work environment.
0 views • 16 slides
Understanding Emergency Conditions in ERCOT Protocols
ERCOT has defined various levels and communication protocols for Emergency Conditions within the electrical grid system. This includes Emergency Notices, Energy Emergency Alerts, operating plans, outage coordination, and requirements related to voltage support for ensuring system safety and reliabil
6 views • 18 slides
Understanding Lock-Based Protocols in Database Concurrency Control
Lock-based protocols are essential mechanisms for controlling concurrent access to data items in a database system. This involves granting locks in exclusive (X) or shared (S) modes to ensure data integrity and prevent conflicts. Lock compatibility matrices and locking protocols play a crucial role
2 views • 69 slides
Laboratory Safety Protocols and Pathogen Classification
Scientist must adhere to lab safety protocols including wearing safety gear, proper waste disposal, and handling chemicals carefully. The classification of pathogens varies by country based on WHO guidelines into four risk groups. Understanding these protocols and classifications is crucial for a sa
0 views • 17 slides
Open Access Publishing and EIS Programme at Pázmány University: Empowering Research and Scholarly Communication
Discover the advantages of Open Access (OA) publishing and how researchers benefit from immediate accessibility, increased discoverability, and global readership. Learn about the EIS Programme at Pázmány University, a member institution dedicated to providing essential electronic resources for hig
0 views • 12 slides
SRYA Clinic Soccer Fall 2021 Updates and Protocols
Stay updated on the latest news and protocols for the SRYA Clinic Soccer Fall 2021 season. Learn about volunteer positions, contacts, fun facts about the program, COVID-19 updates, and general protocols from Rec & Parks. Ensure the safety and well-being of players, coaches, and families while enjoyi
0 views • 23 slides
Secure Composition of Key Exchange Protocols
Explore the game-based composition approach for key exchange protocols, focusing on ensuring security in compositions with arbitrary tasks and the universal composability of protocols. Delve into the Bellare-Rogaway security model and the details of security games in protocol analysis. Understand ke
0 views • 25 slides
Taming Adaptivity in YOSO Protocols: The Modular Way
Explore the concept of taming adaptivity in YOSO protocols through a modular approach. The research delves into the efficiency, adversary adaptivity, role assignments, and compiler models in synchronous YOSO protocols. The visual presentations illustrate the framework, challenges, and strategies in
0 views • 19 slides
Can You Afford a Data Breach? Understanding the Risks and Consequences
Explore the potential dangers and implications of a data breach through insightful presentations and visuals by Laura Middleton and James Hayward. Learn about the value of personal data, human errors, and organizational measures to mitigate risks. Stay informed and subscribe to the e-newsletter for
0 views • 10 slides
Sabbath Service Highlights and Vision of House of Israel
Today's Sabbath service at House of Israel included a message on the Last Supper and Passover, along with a focus on worship, evangelism, discipleship, and equipping for Yeshua's worldwide witness. Attendees were encouraged to subscribe for updates, engage in prayer, and participate in giving offeri
0 views • 58 slides
LiveTiles Limited Q1 FY20 Investor Update
LiveTiles Limited Q1 FY20 Investor Update for October 29, 2019, is a presentation in Australian Dollars (AUD). The presentation includes disclaimers, limitations, and risks associated with forward-looking statements. Recipients are advised to exercise caution and seek professional advice before maki
0 views • 9 slides
Guide to Accessing the RESP-FIT Member Forum
Welcome to the RESP-FIT Member Forum, a platform for Accredited Fit Testers, Approved Trainers, and Training Providers to enhance communication, share information, and discuss methodology and equipment related to fit testing and respiratory protection. Learn how to log in, access the forum for the f
1 views • 13 slides
Publish a Windows 10 Game with Unity 5: Step-by-Step Guide
Learn how to publish a Windows 10 game using Unity 5 with detailed instructions on enabling Developer Mode, entering game details, exporting to Windows 10 Universal Platform, building the solution in VS2015, associating with the Store app, adding required images, and running Windows App Cert Kit for
0 views • 14 slides
RAPID Meeting Insights and Schedule Updates
Join the Research Administration Platform for Innovation and Discussion (RAPID) meetings to engage with topics like Research Approval Workflow, Weill Research Gateway, EHS Safety, and E2RA Updates. Stay informed about upcoming meeting schedules and subscribe to meeting updates by sending a request t
0 views • 4 slides
Overview of Identification Protocols in CS255 by Dan Boneh
The lecture in CS255 covers various topics related to identification protocols, including signatures from trapdoor functions, certificates, revocation methods, certificate issuance problems, defense mechanisms like certificate transparency (CT), and moving on to protocols. The talk also explores the
0 views • 43 slides
Towards Practical Generic Zero-Knowledge Protocols
Exploring the evolution of zero-knowledge protocols, this presentation by Claudio Orlandi from Aarhus University delves into the concepts of Zero-Knowledge from Garbled Circuits, Privacy-Free Garbled Circuits, and more. The talk discusses efficient methods for proving statements and touches on relat
0 views • 29 slides
Understanding The Field Poll and Accessing Data Through CSU Campuses
The Field Poll, established in 1947 by Mervin Field, is an independent survey of California public opinion. CSU campuses subscribe to social science databases, granting access to Field Poll data. Access is IP authenticated, requiring access from CSU campuses. The UCDATA website allows users to searc
0 views • 43 slides
Wireless Sensor Networks: Medium Access Protocols Overview
This collection of images presents key concepts in wireless sensor networks, focusing on medium access protocols, the ISO/OSI reference model, types of conflict resolution, contention-free protocols, Bitmap protocol, ALOHA algorithm, and its analysis and efficiency. Various protocols and algorithms
0 views • 83 slides
Election of 1912 and Its Impact on APUSH Students
Explore the dynamic Election of 1912 in US history, featuring William Howard Taft, Theodore Roosevelt, Woodrow Wilson, and Eugene Debs. Learn about the split in the Republican Party, Wilson's victory, Debs' Socialist impact, and the rise of the Progressive Party. Subscribe for more educational conte
0 views • 5 slides
Neighborhood Boards: Oath of Office and Member Expectations
The presentation discusses the importance of the oath of office for neighborhood board members, emphasizing the requirement to subscribe within 60 days to avoid disqualification. It outlines the process for taking the oath and the consequences of not doing so timely. Through quiz questions scattered
0 views • 47 slides
Green Protocols for Greener Arbitrations
The Green Protocols introduced by AtLAS aim to guide the arbitration community in committing to environmentally sustainable practices. These protocols suggest ways to reduce carbon emissions, energy consumption, waste generation, and unnecessary travel by utilizing electronic communication, video co
0 views • 14 slides
Understanding Ethernet and Multiple Access Protocols in Computer Networks
Exploring the fundamentals of Ethernet and multiple access protocols in computer networks, this content discusses the two primary categories of multiple access protocols - contention access and controlled access. It delves into topics such as CSMA/CD, LANs, performance of multiple access schemes, ad
0 views • 7 slides
Efficient Ways to Stay Updated: Alerts & Journal TOCs
Learn how to set up search alerts for evidence/literature searches, subscribe to journal table of contents alerts, and utilize internet alert feeds to receive new published material relevant to your research or expertise. Explore various resources such as Cochrane Library, NHS Evidence, Dynamed, Goo
0 views • 25 slides
Scalable Identity and Key Management for Publish-Subscribe Protocols
This research by Prashant Anantharaman from Dartmouth College focuses on scalable identity and key management for publish-subscribe protocols in Energy Delivery Systems. It discusses the architecture, goals, assumptions, and implementation results in the context of PKI vs. Macaroons protocols. The w
0 views • 37 slides
Comprehensive Examination Questions on Data Management Systems and Security Protocols
This content covers a range of topics related to data management systems, including two-phase locking and two-phase commit protocols, Bayou system with vector clocks and causality, digital signatures and certificates in protocols, and authentication protocols. Questions include scenarios and concept
0 views • 6 slides
journal to publish research paper
The Journal of Research is an esteemed, peer-reviewed publication dedicated to advancing knowledge in [specific area of research, e.g., \"biomedical sciences\" or \"artificial intelligence\"]. Our mission is to publish high-quality, innovative resear
1 views • 12 slides
journal to publish research paper
The Journal of Research is an esteemed, peer-reviewed publication dedicated to advancing knowledge in [specific area of research, e.g., \"biomedical sciences\" or \"artificial intelligence\"]. Our mission is to publish high-quality, innovative resear
0 views • 6 slides
journal to publish research paper
The Journal of Research is an esteemed, peer-reviewed publication dedicated to advancing knowledge in [specific area of research, e.g., \"biomedical sciences\" or \"artificial intelligence\"]. Our mission is to publish high-quality, innovative resear
0 views • 9 slides
journal to publish research paper
The Journal of Research is an esteemed, peer-reviewed publication dedicated to advancing knowledge in [specific area of research, e.g., \"biomedical sciences\" or \"artificial intelligence\"]. Our mission is to publish high-quality, innovative resear
1 views • 15 slides
Improved Merlin-Arthur Protocols for Fine-Grained Complexity Problems
The text discusses Merlin-Arthur proof systems and protocols for central problems in fine-grained complexity, particularly focusing on the time complexity, completeness, and soundness of these protocols. It also touches on recent interest in these protocols and presents new results in areas such as
0 views • 16 slides
Quantum Distributed Proofs for Replicated Data
This research explores Quantum Distributed Computing protocols for tasks like leader election, Byzantine agreement, and more. It introduces Quantum dMA protocols for verifying equality of replicated data on a network without shared randomness. The study discusses the need for efficient protocols wit
0 views • 28 slides
Google Certification Module 16 Level 1 Overview
Jana Gerard, a Level 1 & Level 2 Google Certified Educator and Trainer, shares insights on subscribing to channels, creating and editing playlists, adding descriptions, and sharing playlists on YouTube. The practical tasks cover steps to access YouTube, subscribe, create playlists, and share videos
0 views • 12 slides
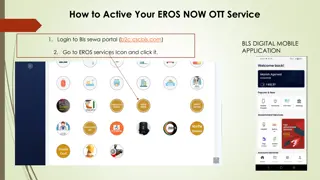
Step-by-Step Guide to Activating Your EROS NOW OTT Service
Follow these easy steps to activate your EROS NOW OTT service: Login to the Bls.sewa portal using the BLS Digital Mobile Application, fill in your details, receive a message on your registered mobile number, download and install the app, login with the received credentials, subscribe to a package, a
0 views • 7 slides
Terrestrial File Transfer Concept: Design Goals and Protocols
This document discusses the concept of terrestrial file transfer as presented in a series of slides from an ESA event in Noordwijkerhout, The Netherlands. It covers the purpose, design goals, protocols, and transport protocols involved in exchanging files between agencies for mission design, operati
0 views • 20 slides