2022 Reach Codes Initiative. Advancing safer, healthier and more affordable buildings and vehicles
The 2022 Reach Codes Initiative focuses on advancing the adoption of safer, healthier, and more affordable buildings and vehicles through local enhancements to state building codes. This initiative addresses building electrification, reduced methane gas usage, and increased electric vehicle charging
0 views • 52 slides
Understanding Binary Codes and Their Applications
Binary coding is crucial for digital systems as they understand only 0s and 1s. This process converts information into binary language for processing by digital circuits. Different types of binary codes like weighted codes and BCD codes are used for error correction, digital communication, and compu
7 views • 20 slides
Understanding Activity, Pay, and Special Codes in API Terminology
Dive into the terminology surrounding Activity Codes, Pay Codes, and Special Codes within the realm of APIs. Explore how these codes represent different aspects of scheduling, productivity, and payroll management. Gain insights into the distinctions between Activity Codes and Pay Codes, their implic
5 views • 8 slides
Pseudo-Scientific Ideas About Race and Eugenics in the USA and Australia
The eugenics movement in the USA, under leaders like Charles Davenport, promoted the separation of "inferior" races to prevent genetic contamination of the "superior" groups. Laws like the Virginia Racial Integrity Act enforced racial segregation and punished interracial marriages. This era saw the
1 views • 20 slides
General Ledger Book Codes and Books Overview
Companies often need to report financial information in different ways for various purposes, such as management view, GAAP, and tax basis. Workday provides tools like Book Codes and Books to facilitate different types of reporting. Book Codes define transaction accounting locations, while Books grou
0 views • 5 slides
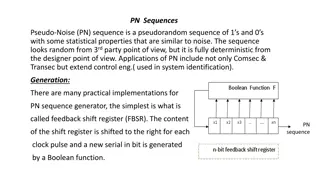
Understanding Pseudo-Noise Sequences and Applications
Pseudo-Noise (PN) sequences are deterministic yet appear random, with applications in various fields such as communication security, control engineering, and system identification. Generated using shift registers, they exhibit statistical properties akin to noise. Linear and nonlinear feedback shift
1 views • 19 slides
Understanding CB Codes in Curriculum Development
Delve into the world of CB codes, where CB stands for course basic, used by CCCCO for counting and funding various elements in curriculum development. Discover the purpose and significance of different CB codes ranging from course control numbers to special status indicators. Gain insights into the
0 views • 20 slides
Understanding Convolutional Codes in Digital Communication
Convolutional codes provide an efficient alternative to linear block coding by grouping data into smaller blocks and encoding them into output bits. These codes are defined by parameters (n, k, L) and realized using a convolutional structure. Generators play a key role in determining the connections
0 views • 19 slides
Understanding Binary Codes and Self-Complementing Codes
The concept of binary codes, including Binary Coded Decimal (BCD) codes, and self-complementing codes is explored in this informative content. Learn about how decimal numbers are represented in binary form, the structure of BCD codes, and the properties of self-complementing codes like 2421 and Exce
2 views • 34 slides
Understanding C Codes in Institutional Student Information Records (ISIRs)
C codes are indicators generated by CPS requiring resolution from the Financial Aid Administrator. This article explores the process of resolving C codes and highlights the seven common areas where C codes are generated, including Selective Service, Social Security, and Veterans Affairs matches. It
0 views • 32 slides
Updates on Oil & Gas NAICS Codes and Classification Guidelines
The National Oil and Gas Emissions Committee discusses the recent changes in NAICS codes for the oil and gas industry, including the breakdown of Crude Petroleum and Natural Gas Extraction codes. The U.S. Census Bureau provides guidance on assigning NAICS codes based on the primary economic activity
0 views • 12 slides
Understanding ICD-11 and Morbidity Coding Principles
ICD-11 is a classification system that groups entities based on statistical relevance and specificity of codes. Entities without specific codes are assigned to residual codes (Y for specified, Z for unspecified) based on hierarchy. Examples illustrate the differentiation between specified and unspec
0 views • 15 slides
Understanding Reasonable Arguments vs. Pseudo-Arguments
The provided content focuses on distinguishing between reasonable arguments and pseudo-arguments through thought-provoking questions such as the ethical treatment of animals, city subsidies for sports venues, and subjective opinions on aesthetics. It also explains the structure of an argument, highl
0 views • 18 slides
Understanding Cyclic Codes: Generation and Examples
Cyclic codes are a subclass of linear block codes where any cyclic shift of a codeword results in another valid codeword. This article explains the generation of nonsystematic cyclic codes through polynomial multiplication and provides examples and code tables for both nonsystematic and systematic c
0 views • 11 slides
Understanding Pseudo Code and Flow Charts for Algorithm Analysis
Explore the concepts of pseudo code and flow charts for analyzing algorithms, problem-solving, and understanding space and time complexity. Learn about basic elements of pseudo code, assigning operations, and writing effective pseudo code statements in a clear and structured manner. Discover the imp
0 views • 26 slides
Understanding Geographic Distribution Using 3-Digit ZIP Codes
Massachusetts has approximately 685 5-digit ZIP codes assigned by the USPS, which can be aggregated into 18 3-digit ZIP codes for geographic analysis. The distribution of Emergency Department visit volumes varies across these 3-digit ZIP code boundaries, reflecting different regional characteristics
1 views • 4 slides
Exploring Pseudo-Goodwin Cycles in a Minsky Model
This paper delves into the dynamics of Pseudo-Goodwin cycles within a Minsky model, examining the counter-clockwise movement of output and wage share. It distinguishes between true Goodwin cycles and pseudo variants, highlighting the role of income distribution, debt, and demand in shaping economic
0 views • 27 slides
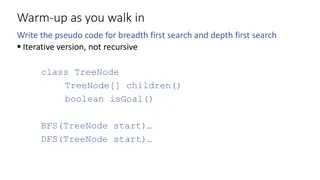
AI Search Algorithms: BFS and DFS Pseudo-code Iterative Version
Explore the iterative versions of Breadth First Search (BFS) and Depth First Search (DFS) with pseudo-code examples implemented for class TreeNode. Understand the concept of TreeNode, children() function, isGoal() method, and apply BFS and DFS starting from TreeNode start.
0 views • 53 slides
Understanding Professional Codes of Ethics
Explore the foundations and evolution of professional codes of ethics, examining values, ideals, and principles that shape ethical behavior. Learn about the roles and responsibilities of codes of ethics, concerns surrounding them, and how they influence policies in organizational settings. Delve int
0 views • 11 slides
Key Learnings from Exams: Algorithm Strategies & Representations
Exploring vital lessons from exams, including algorithm development tips, representation examples, and pseudo-code explanations. Understand the importance of reading questions carefully, creating precise steps, and terminating algorithms effectively. Dive into the world of algorithms, pseudo-code, a
0 views • 44 slides
Enhancing Spectrum Efficiency with Low Complexity Erasure Codes in IEEE 802.11 Document
This document delves into the implementation of erasure codes for content channels in IEEE 802.11 systems. By utilizing erasure codes, spectrum efficiency can be boosted without significantly increasing the complexity of encoding and decoding processes. The discussion also covers the duplication of
0 views • 20 slides
Enhancing Data Integrity Protection in Cloud Storage Using Regenerating Codes
This paper explores the importance of data integrity protection in cloud storage and presents a solution using regenerating codes to detect corrupted data chunks, provide fault tolerance, and enable efficient recovery. It compares regenerating codes with Reed-Solomon codes and discusses their implic
0 views • 36 slides
Understanding Secure PRFs and PRPs in Cryptography
Dive into the world of secure Pseudo-Random Functions (PRFs) and Pseudo-Random Permutations (PRPs) in cryptography. Learn about the definitions, security criteria, and examples of secure PRFs and PRPs such as 3DES and AES. Explore the concepts of secure block ciphers and key principles behind these
0 views • 54 slides
Lower Bounds on Sampling Good Codes in Bounded-Depth Circuits
Bounded-depth circuits are proven unable to sample or approximate good codes effectively. This work delves into lower bounds, showcasing that bounded families of circuits face limitations in computing specific functions or sampling distributions. The example of Parity in AC0 circuits illustrates the
0 views • 21 slides
Exploring Pseudo-Complex General Relativity for Gravitational Waves
Delve into the concept of pseudo-complex General Relativity (PC-GR) as an alternative theory to Einstein's General Relativity. The study considers algebraic extensions, weak field limits, and the extension of metrics in momentum-energy space. By analyzing predictions and implications, this research
0 views • 21 slides
DukeShift User Group and Special Codes Overview
Explore the DukeShift user group details featuring Julia Bambach, Tiffany McNeill, Bernard Rice, John Dale, and updates for February 2023. Learn about new special codes for virtual nursing, quick special code review, VA and SC special codes, and reporting on special codes. Dive into essential topics
0 views • 11 slides
Comprehensive Overview of Multi-delimiter Data Compression Codes and Key Features
This content showcases the concept of multi-delimiter data compression codes, their application in various algorithms such as arithmetic, finite state entropy, Huffman, and Fibonacci. Key features including compression rate, synchronization, search in compressed files, encoding/decoding speed, and c
0 views • 27 slides
Understanding Binary Codes and Character Coding Techniques
Binary codes, such as ASCII and EBCDIC, are crucial in representing data in computers and digital systems. They play a key role in error detection and data encoding. This article discusses the basics of binary coding, various types of binary codes, character coding techniques like ASCII and EBCDIC,
0 views • 22 slides
Pseudo-Tie Business Procedure Tariff Administration, August 2017
Pseudo-tie business procedure tariff administration from August 2017 outlines the purpose, implementation, and types of pseudo-ties in the energy industry. It covers dynamic transfers, pseudo-tie procedures, and various stakeholder involvements. The document details the process of implementing pseud
0 views • 11 slides
Understanding Pseudo-Tie Entry in Electric Industry Registry
Explore the requirements and measures of NERC Standard INT-004-3.1 for dynamic transfers in the electric industry. Learn about data fields required for pseudo-tie entry and approval methodology in the Electric Industry Registry. Discover the publishing schedule for EIR entries and the approval proce
0 views • 6 slides
Ordering of Pseudo Dispatch Instructions for QBOA
This document outlines the specific order in which Pseudo Dispatch Instructions (DIs) are to be arranged for QBOA in scenarios where multiple instructions are issued simultaneously. The order prioritizes certain instructions to maintain consistency and alignment with system implementation rules.
0 views • 11 slides
Quantum Error-Correcting Codes and Subsystem Codes
Quantum error-correcting codes (QECC) play a crucial role in protecting quantum information from errors. Stabilizer codes with fault-tolerant error-detecting circuits can lead to the construction of resilient subsystem codes. These codes involve encoding logical qubits into physical qubits and error
0 views • 26 slides
Overview of V*LIDORT and Other Radiative Transfer Models by Robert Spurr
The presentation provides an update on the status of V*LIDORT and other radiative transfer models as discussed at the Third TEMPO Science Team Meeting. It covers the LIDORT family overview, upgrades to the codes, new releases for RT models, and accelerated RT developments using PCA. The V*LIDORT cod
0 views • 12 slides
Understanding Pseudo Code: A Beginner's Guide to Organizing Programs
Pseudo code is a helpful way to organize your program logic before actual coding. It provides a structured outline from inputs to outputs, focusing on step-by-step guidelines that are not language-specific. This guide covers the basics of pseudo code, including general guidelines, steps to pseudo co
0 views • 29 slides
Understanding Tilde Codes for Custom Result Pictures
Tilde codes are utilized in the creation of custom result pictures from a mentometer system, offering flexibility in formats and colors. These codes are embedded within result pictures and replaced with numerical values by the mentometer system. Learn how to hide/unhide tilde codes, commonly used ti
0 views • 21 slides
Evolution of Communication Systems: From Bandwidth Division to Spread Spectrum
Third-generation communication systems utilize Pseudo-Noise (PN) codes to share bandwidth without interference, while first and second-generation systems divide bandwidth into smaller channels. PN codes are vectors with 1s and -1s, orthogonal to each other. Users transmit data using PN coding, combi
0 views • 14 slides
Managing Student Moves and Transfers in DLM 2022-2023
This content provides detailed guidance on managing student moves and transfers within the Dynamic Learning Maps (DLM) system for the 2022-2023 academic year. It covers the use of exit codes, special circumstance codes, key dates for assessments, required training materials, New Jersey specific guid
0 views • 22 slides
Current Policy Issues Regarding Three-Character Country Codes as Top-Level Domains
The GAC Agenda Item 10 discusses the possibility of using three-character country codes as top-level domains in the future rounds, addressing concerns of potential confusion with existing ccTLDs. The joint ccNSO and GNSO working group is exploring lifting restrictions on three-letter codes, with the
0 views • 6 slides
Handling Label Noise in Semi-Supervised Temporal Action Localization
The Abstract Semi-Supervised Temporal Action Localization (SS-TAL) framework aims to enhance the generalization capability of action detectors using large-scale unlabeled videos. Despite recent progress, a significant challenge persists due to noisy pseudo-labels hindering efficient learning from ab
0 views • 30 slides
Update on (V)LIDORT Radiative Transfer Models and Upgrades
The update discusses the (V)LIDORT radiative transfer models by Robert Spurr from RT Solutions Inc., highlighting features like pseudo-spherical approximation, Jacobians generation, and new releases. It covers upgrades to the codes, including thread-safe implementation and new capabilities like BRDF
0 views • 11 slides