Group Policy Management for Active Directory, cionsystems
It allows IT admins to control a wide range of settings related to security and access permissions. A system requirement for this application is also mentioned here. https:\/\/rb.gy\/0cmjy6
3 views • 7 slides
Active Directory Group Policy Management, cionsystems.com
. It allows IT admins to control a wide range of settings related to security and access permissions. A system requirement for this application is also mentioned here. \/\/rb.gy\/gmxhsa
2 views • 7 slides
Safety Guidelines for Restricted Areas and Laboratories at Griffith Sciences
Griffith Sciences has strict protocols in place for accessing restricted areas, including obtaining necessary permissions and adhering to Access Risk Levels. The guidelines emphasize the importance of safety measures in laboratories, such as wearing appropriate PPE, following specific rules, and see
3 views • 11 slides
Active Directory Group Policy Management, cionsystems.com
It allows IT admins to control a wide range of settings related to security and access permissions. A system requirement for this application is also mentioned here. \/\/rb.gy\/6myl8r
2 views • 7 slides
Launchpad Operations and Security Enhancements
Explore the evolution of Launchpad, a key tool for managing SACR settings and user permissions within academic institutions. From its development by CIBER to modifications by SBCTC, learn how Launchpad facilitates secure copying of settings between users while ensuring data integrity and compliance.
1 views • 16 slides
Resolving QuickBooks Error 6176 - An Ultimate Guide
To resolve QuickBooks Error 6176, you need to adopt a systematic approach. Firstly, ensure that your QuickBooks software is updated to its latest version. Secondly, check if your system meets the software's requirements. You must also verify that there are no conflicting applications or antivirus so
1 views • 3 slides
Comprehensive Training Module for Test Information Distribution Engine (TIDE)
Detailed training module for TIDE covering account activation, logging in, password management, roles and permissions, and more. Get insights on preparing for testing, navigating the TIDE interface, managing user accounts, administering tests, and monitoring progress.
1 views • 93 slides
How to Fix QuickBooks Error 1603?
How to Fix QuickBooks Error 1603?\nQuickBooks Error 1603, occurring during installation or updates, impedes workflow. Causes include incomplete installations, system configuration issues, and antivirus interference. Diagnosis involves checking requirements, internet connection, and running diagnosti
0 views • 5 slides
How to Resolve QuickBooks Error 1321?
How to Resolve QuickBooks Error 1321?\nStuck with QuickBooks Error 1321? Don't sweat! This error signals a permission issue. Try a simple retry first. If that fails, consider granting temporary admin rights (use with caution!). For advanced users, editing permissions or using the QBInstall tool can
0 views • 3 slides
Troubleshooting “QuickBooks Already Has a Company File Open” Error
Troubleshooting \u201cQuickBooks Already Has a Company File Open\u201d Error\nEncountering the \"QuickBooks Already Has a Company File Open\" error? This common issue disrupts your workflow but can be fixed. Start by checking for multiple instances of QuickBooks and restarting your computer. Ensure
1 views • 6 slides
How to Restore deleted Invoice in Quickbooks Online?
How to Restore deleted Invoices in Quickbooks Online?\nRestoring a deleted invoice in QuickBooks Online involves using the Audit Log to track and recreate it. First, access the Audit Log via the Gear icon under \"Tools\" and identify the deleted invoice details. Then, manually recreate the invoice b
1 views • 7 slides
How to Resolve QuickBooks Error 1904
Struggling with QuickBooks Error 1904? This guide simplifies the resolution process. Error 1904 typically occurs due to damaged or missing files during software installation, causing inconvenience and delays. Common solutions include running the QuickBooks Install Diagnostic Tool, ensuring your oper
1 views • 5 slides
How to Resolve QuickBooks Update Error 12007
QuickBooks Update Error 12007? This error typically occurs due to misconfigured system files, internet connectivity issues, or problems with your firewall and security settings. When QuickBooks is unable to access the internet, it can't download updates, leading to Error 12007. To resolve this issue
0 views • 5 slides
How to Resolve QuickBooks Update Error 12007
QuickBooks Update Error 12007? This error typically occurs due to misconfigured system files, internet connectivity issues, or problems with your firewall and security settings. When QuickBooks is unable to access the internet, it can't download updates, leading to Error 12007. To resolve this issue
0 views • 5 slides
Overview of Housing Supply and Economic Impact in the UK
England experienced a significant increase in housing supply in 2022/23, with new build completions and conversions contributing to a record-breaking net supply of 320,000 homes per year. Despite challenges in planning permissions and government interventions, the home building industry supported th
2 views • 14 slides
Concurrent Interpretations of Authorization Logic
Explore the concepts of authorization logic through discussions on policy enforcement, permissions, logical implications, and security theorems in the context of a scenario involving Alice, UdS Students, and printing permissions.
1 views • 50 slides
Filesystems: A Comprehensive Overview
File systems provide a structured approach to storing and organizing data on secondary storage devices. They involve logical organization of files, directories for grouping related files, sharing data between users, and managing permissions. Files contain data with attributes like size, ownership, a
4 views • 29 slides
Guidelines for Using Powered By CAST Logos for CAST Partners
Conditional use guidelines for partners of CAST in embedding, re-selling, or jointly selling CAST products, including permissions, requirements, and limitations to ensure the logos are used appropriately and do not harm the integrity or reputation of CAST trademarks.
0 views • 4 slides
Performance Overview of Standing Committee for Refugee Affairs (SCRA)
The presentation to Parliament highlights the mandate and functions of the Standing Committee for Refugee Affairs (SCRA) as per the Refugees Act. Established to make decisions independently, the SCRA oversees reviews, work permissions for asylum seekers, monitoring of decisions, and advice to the Mi
1 views • 15 slides
Enhancing Learning Through Field Trips: A Comprehensive Guide
Explore the benefits and best practices of conducting educational field trips, from planning and logistics to implementing effective teaching methods. Discover how field trips provide real-life experiences, supplement classroom learning, and develop important skills and attitudes in students. Learn
0 views • 16 slides
Efficient Road Cutting Management System for Service Providers
Efficiently manage road cutting permissions in BBMP through the BRCMS system, facilitating online requests and registrations for service providers. The system enables easy registration, activation, and application processes for road cutting services including OFC and MARCS. New service providers can
0 views • 21 slides
Gwendolyn Brooks Library Usage Statistics with Springshares LibInsight
Gwendolyn Brooks Library utilizes LibInsight's E-Journals/Databases Dataset to streamline the collection and analysis of usage statistics for reporting to ACRL, IPEDs, and university administration. The tool offers various features such as storing login information, different levels of permissions,
0 views • 7 slides
O3 Access Control Solution Overview
O3 Access Control Solution offers unique selling points like single-seat management software, role-based permissions, customizable user information, and more. The system includes a compact controller with multi-format reader support and BACnet Access objects. It integrates with other O3 modules for
0 views • 10 slides
Magento Go-Live Best Practices Checklist
Implementing a successful Magento go-live strategy requires careful attention to key settings and recommendations such as enabling page cache, optimizing performance, managing permissions, and applying necessary patches. This checklist covers essential steps to ensure a smooth transition to a live e
0 views • 9 slides
Enhancing GDPR Compliance with SIMS Reporting
Explore how SIMS Reporting supports GDPR compliance through the Person Data Output feature, enabling schools to efficiently handle Subject Access Requests. Learn about the Data Protection Act, permissions required for PDO, and running PDO for data portability.
0 views • 10 slides
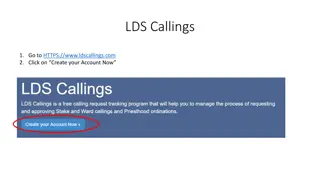
How to Manage LDS Callings and Administer Site Effectively
Detailed guide on creating an account, logging in, site administration, managing people, setting permissions, utilizing the dashboard, and submitting calling or Priesthood ordination requests for LDS members. Complete step-by-step instructions with images provided for each process.
4 views • 27 slides
GASABO Service Procedures and Requests in GASABO District - Guidelines and Information
Providing guidelines and information on service procedures and requests in GASABO district. Learn about the process of seeking approvals, permissions, and services in the specified area. Understand the steps involved in requesting services in GASABO and the regulations governing these actions.
0 views • 91 slides
Android App Development Basics
Android apps operate within a secure, multi-user environment with each app having its own user identity and permissions. Components like Activities, Services, Receivers, and Providers handle various aspects of app functionality. Permissions safeguard user privacy by controlling access. Developers mu
3 views • 20 slides
Comprehensive Account Management Training Unit
This unit focuses on account management in the context of the National Enterprise Support Service (NESS) Application Portal (NAP) and the ROSS system. Trainees will learn how to request new NAP accounts, add ROSS users, assign user roles, manage access permissions, and more. The content covers diffe
0 views • 7 slides
Secure Management of IOOS GitHub Organization
Safeguarding the IOOS GitHub Organization involves ensuring proper permissions and access controls for members, teams, and collaborators. Risks include unauthorized deletion of repositories and potential security vulnerabilities. The path forward includes implementing security measures to protect th
0 views • 11 slides
Managing and Editing Staff Accounts in Your System
Explore the process of creating, managing, and editing staff accounts in your system. Learn about different staff account types, group permissions, creating staff accounts, defining course lists, assigning reason specialties, and managing certifications and work plans. Gain insights into how staff a
2 views • 12 slides
Software Installation and Management
Different types of software require various methods of installation and management such as interpreted scripts, pre-compiled binaries, and source code. It's important to comprehend users, roles, and permissions in software installation, including the significance of user privileges and file/director
1 views • 42 slides
Linux File Permissions and Security Practices
Explore how Linux file permissions work, including the concepts of read, write, and execute permissions for files and directories. Learn about changing permissions using the `chmod` command and how umask affects default permissions when creating files. Enhance your understanding of securing software
2 views • 9 slides
UNIX System Permissions and User Terminology
Explore the concept of UNIX system permissions, including discretionary access control (DAC) model, user terminology, file/directory access, access permission modes, categories of users, and checking permissions using examples. Learn about user IDs, groups, superuser privileges, ownership, access mo
1 views • 24 slides
File Permissions and Ownership in Linux
This content discusses the concept of file permissions and ownership in Linux, covering the three levels of ownership (owner, group, everybody), the usage of the 'ls -l' and 'id' commands to check identity information, changing file permissions using the 'chmod' command with octal notation, and meth
1 views • 5 slides
User and Group Permissions in Linux Systems
Linux uses user and group permissions to control access to files, directories, and peripherals. Users are managed for security purposes by limiting access, with the root user having full system access. Grouping users into groups with specific access grants can enhance security. Each file is owned by
1 views • 23 slides
User Permissions in Database Management Systems
Database Management Systems (DBMS) offer security measures to control user accesses and permissions. Users can be assigned specific access rights and commands. This guide explains concepts like creating users, granting privileges, managing roles, and using GRANT commands effectively in DBMS.
0 views • 12 slides
Government Agenda for Brownfield Land Development
Unpacking the government agenda for brownfield land development involves key elements such as the Brownfield Register, Permissions in Principle, Local Plan Changes, and the push to convert office spaces to residential units. The government is committed to utilizing brownfield land efficiently, setti
0 views • 47 slides
Android Permissions Overview
This detailed overview provides insights into the various permissions categories in Android, including location, hardware, services, Bluetooth, accounts, text messaging, user information, phone calls, and miscellaneous permissions like voicemail access and system functionalities. Each section highli
1 views • 24 slides
Standards Balloting and Commenting System (SBS) Overview
Learn about the roles and permissions in the Standards Balloting and Commenting System (SBS), including registration, validation, and accessing the ERO Platform. Find out who needs an ERO Platform account, additional permissions required for various roles, and how to navigate the SBS for casting vot
0 views • 24 slides