Non Coronary Vascular Stents
Safe scanning of patients with non-coronary vascular stents (NCVS) in MRI settings in NHS Scotland. It covers key questions regarding the safety of patients with NCVS, including risks associated with MRI at different strengths, timing of MRI post-stent implantation, and the safety of various stent m
1 views • 9 slides
Evolution of CT Scan Technology and Terminology
The development of CT scanning technology revolutionized medical imaging. Godfrey Hounsfield introduced computerized axial transverse scanning in 1972, with Allan Cormack's mathematical contributions. Dr. Robert Ledley created the first whole-body CT scanner in 1974. Dr. Willi Kalender further advan
1 views • 121 slides
Understanding Investigations in Science
Investigating in science involves various approaches beyond fair tests, such as pattern-seeking, exploring, and modeling. Not all scientists rely on fair tests, as observational methods are also commonly used. The scientific method consists of steps like stating the aim, observing, forming hypothese
1 views • 20 slides
Enhancing Cybersecurity with Bluedog VAPT Services
Bluedog Security Monitoring offers essential cybersecurity services, including Vulnerability Assessment and Penetration Testing (VAPT). Their automated VAPT combines External Vulnerability Scanning and WebApp Scanning to provide comprehensive testing solutions that help businesses prioritize risks,
0 views • 16 slides
Environmental Scanning Techniques for Business Adaptation
Businesses are integral parts of society and must stay abreast of surrounding changes to thrive. Environmental scanning is crucial for businesses to adapt and evolve effectively.
0 views • 9 slides
Understanding Pattern Recognition in Data Science
Explore the concept of pattern recognition through chapters on pattern representation, learning objectives, KDD process, and classification. Dive into the Iris dataset and learn how patterns are represented and classified based on their attributes.
6 views • 66 slides
Improve Your Reading Skills: Scanning and Skimming Techniques
Enhance your reading skills by mastering the art of scanning and skimming. Learn how to efficiently search for specific information without reading every word. Discover tips for scanning different types of texts and practice answering questions based on scanned content.
8 views • 12 slides
CACFP Infant Feeding Meal Pattern Requirements Training Overview
The training material covers the Child and Adult Meal Pattern Requirements, emphasizing a wider variety of protein options, more fruits and vegetables, whole grains, and less added sugar and saturated fat. It details the Infant Meal Pattern Requirements, encouraging breastfeeding and promoting devel
2 views • 58 slides
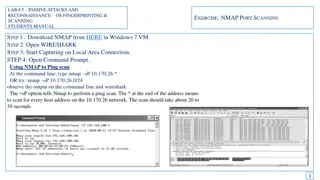
Passive Attacks and Reconnaissance using NMAP for Network Scanning
Learn how to use NMAP for passive attacks and reconnaissance through port scanning techniques like ping scan, TCP port scan, and stealth scan. Understand how to analyze the output in Wireshark to identify open ports and version numbers on target systems.
2 views • 7 slides
Passive Attacks and Reconnaissance in Network Security
Passive attacks involve monitoring target systems through port scanning or other means to locate vulnerabilities. Scanning is the first active action taken against a target network based on information gathered through footprinting, allowing deeper penetration. It includes scanning ports and service
0 views • 24 slides
Environmental Scanning Tool for Strategic Workforce Planning Cycle
In the Compare stage of strategic workforce planning, utilizing the Environmental Scanning Tool can assist in identifying work and workforce scenarios to achieve organizational goals. The tool consists of three templates including Choosing the Right Type of Data, Environmental Scanning Template, and
1 views • 9 slides
Effective Reading Strategies: Skimming and Scanning Techniques
Develop your reading skills with skimming and scanning techniques. Skimming helps you quickly grasp the main ideas of a text, while scanning allows you to find specific information efficiently. Learn how to differentiate between the two methods and when to use each effectively.
0 views • 7 slides
Disaster Recovery and Incident Response Concepts
This content covers the essential concepts of disaster recovery, incident response, penetration testing, vulnerability scanning, and business continuity planning in the context of cybersecurity. It explains the goals and steps involved in penetration testing, vulnerability scanning tasks, business c
2 views • 15 slides
Network Monitoring and Vulnerability Scanning Overview
Kashif Mohammad from the Department of Physics at the University of Oxford provides insights into their setup involving ZEEK, ELK Monitoring, and OpenVas for network monitoring and vulnerability scanning. The team aims to enhance network security through structured classification of nodes based on t
1 views • 10 slides
Understanding Scanning in Thin Clients, RDP, and Citrix Environments
Learn about the difference between Fat Clients and Thin Clients, various types of Thin Clients, reasons for using Thin Clients, how programs are accessed on servers, and issues with scanning in RDP connections in this informative guide. Discover why Thin Clients are preferred for centralized softwar
1 views • 16 slides
Understanding Functional Skills: Text Analysis and Application
This instructional text guides learners through the purpose of functional skills in analyzing different types of text, such as skimming and scanning, and understanding the features of various text genres. It includes activities to practice skimming, scanning, and detailed reading, with a focus on de
0 views • 13 slides
Implementing Barcode Scanning to Reduce Dispensing Errors in Pharmacy
Implementation of barcode scanning in pharmacy departments has been shown to significantly reduce dispensing errors, ensuring greater accuracy in medication dispensation. Despite the generally low error rate among pharmacists, high volumes of dispensing can still lead to a substantial number of erro
1 views • 20 slides
Understanding the Array Scanning Method in Electromagnetics
Exploring the Array Scanning Method (ASM) for analyzing the field of a single source near an infinite periodic structure. The notes cover the geometry, analysis, phasing, and field calculations involved in an infinite 2D periodic array of metal patches excited by dipole sources, providing insights i
0 views • 25 slides
Understanding the State Design Pattern in Software Development
The State Design Pattern is a Behavioral pattern similar to Strategy, allowing objects to change behavior based on internal state changes. This pattern involves defining different states and their implementations to control object behavior dynamically. Real-life examples like managing mood states an
0 views • 14 slides
What Are the 5 Benefits of Choosing an Advanced MRI Scanning Centre in Panchkula for Accurate Diagnosis
early diagnosis is equally important in treatment. If you are in Panchkula or the places nearby, it is a very wise decision to opt for a modern MRI scanning centre, for example, Kior Healthcare.
1 views • 3 slides
Understanding Breast Ultrasound: Anatomy, Patient Preparation, and Scanning Protocol
This informative content delves into breast ultrasound, covering topics such as breast anatomy, patient preparation and positioning, scanning protocol, required images, and normal sonographic appearances. It provides valuable insights into the structure and composition of the breast, guidelines for
0 views • 8 slides
Methods of Pattern Making in Fashion Design
Pattern making in fashion design involves three main methods: drafting, draping, and flat paper pattern making. Drafting consists of taking measurements and marking construction lines on paper to create patterns, while draping involves shaping fabric around a form to visualize the garment's design e
0 views • 13 slides
Understanding Sentence Patterns for Effective Writing
Enhance your writing skills by learning the seven basic sentence patterns. Recognizing sentence patterns helps improve your ability to construct sentences effectively and understand grammar functions. Explore different patterns, such as the Be Pattern with adverbials and subject complements, Linking
0 views • 27 slides
Mastering Reading Techniques: Skimming, Scanning, and Business Insights
Enhance your reading skills with a focus on skimming, scanning, and understanding business concepts such as commercial vs. retail, B2B vs. B2C, and online shopping trends. Dive into the specifics of general vs. specific information retrieval and learn about dual pricing strategies in the retail sect
0 views • 20 slides
Different Reading Techniques: Skimming and Scanning Explained
Reading involves the process of gaining meaning from text using eyes and brain. Skimming and scanning are two specific types of reading techniques that help readers to quickly grasp the main idea or find specific information in a text. Skimming is like gist reading, where you get a general idea of t
0 views • 17 slides
Understanding Façade Design Pattern in Structural Design Patterns
Façade design pattern simplifies the interface of a complex system by providing a unified and straightforward interface for clients to access the system's functionalities. It helps in isolating the clients from the complexities of underlying components, offering a more user-friendly experience. The
0 views • 48 slides
Understanding Template Method Design Pattern in Software Design
Today's lecture covers the Template Method design pattern in software design, focusing on defining the pattern, its structure, and providing an example with Tea and Coffee recipes. The pattern allows subclasses to redefine certain algorithm steps without changing the overall structure, promoting cod
0 views • 40 slides
Graph Pattern Matching Challenges and Solutions
Graph pattern matching in social networks presents challenges such as costly queries, excessive results, and query focus issues. The complexity of top-k and diversified pattern matching problems requires heuristic algorithms for efficient solutions. Finding best candidates for project roles involves
0 views • 19 slides
Solving the Apple Tree and Conifer Tree Pattern Puzzle
In this mathematics unit, we explore a scenario where a farmer plants trees in a square pattern, with conifer trees surrounding the apple trees for protection against the wind. The task involves completing a table to understand the pattern for different numbers of rows of apple trees. Through this e
0 views • 15 slides
Understanding Virtual Functions and Visitor Pattern in C++
Virtual functions in C++ allow for dynamic polymorphism by defining a set of functions in base classes that can be overridden in derived classes. The visitor pattern is a design pattern that lets you define a new operation without changing the classes of the elements on which it operates. This patte
0 views • 12 slides
Cybersecurity Footprinting and Scanning Techniques
Learn about the techniques involved in cybersecurity footprinting and scanning to protect against information gathering, target acquisition, and unauthorized access. Explore topics such as network enumeration, DNS interrogation, and scanning methods to identify vulnerabilities and enhance security m
0 views • 8 slides
Understanding Pattern Recognition in Computer Science
Dive into the world of pattern recognition, where data is analyzed to make decisions and identify features. Explore statistical pattern recognition, classifiers, and the process of recognizing patterns in images. Learn how computers see and interpret visual data, and the challenges of representing k
0 views • 43 slides
Understanding the Strategy Design Pattern
The Strategy Design Pattern is a behavioral pattern that helps in encapsulating behaviors and varying them as attributes to avoid implementation inheritance and class explosions. By decoupling strategies from the main functionality, it allows for flexibility and ease in changing algorithms at runtim
0 views • 21 slides
Process of Launching an Enterprise: From Scanning Environment to Market Research
The process of launching an enterprise involves scanning the environment, locating business opportunities, converting opportunities into reality, conducting market research, developing a business plan, and managing the entrepreneur. It starts with analyzing the external and internal environment, fol
0 views • 8 slides
Understanding Scanning Electron Microscopes (SEM) and Electron Sources
Scanning Electron Microscopes (SEMs) utilize focused electron beams to produce high-resolution images by interacting with a sample's electrons. The electron source, such as the electron gun, plays a crucial role in forming fine electron beams for imaging purposes. Different types of electron sources
0 views • 12 slides
Exploring Atomic Dimensions: Scanning Probe Microscopy
Delve into the world of nanoscale imaging with Scanning Probe Microscopy (SPM) techniques like Scanning Tunneling Microscopy (STM) and Atomic Force Microscope (AFM). Unlike optical microscopes, SPM methods break the diffraction limit by relying on intermolecular forces and quantum tunneling for unpa
0 views • 26 slides
Exploring Confocal Microscopy: Adding the Third Dimension
Delve into the world of confocal microscopy with Lecture 07 of Principles of Modern Microscopy. Learn about optical sectioning, wide-field imaging, confocal laser scanning, and more to enhance fluorescence in microscopy. Understand the methods of optical sectioning such as deconvolution, multi-photo
0 views • 65 slides
Understanding the Observer Pattern in Software Engineering and Architecture
Dive into the Observer Pattern, a key design pattern in software engineering that establishes a one-to-many relationship between objects. When a state change occurs in one object, all its dependents are automatically notified and updated. Explore real-world examples and the role of the Observer Patt
0 views • 24 slides
Advantages of Scanning Lidars in Wind Resource Assessment
Scanning lidars offer a cost-effective and flexible solution for wind resource assessment compared to traditional met masts. They provide multi-point measurements without the need to relocate hardware, reducing uncertainties and risks in wind energy projects. This technology enhances the accuracy of
0 views • 10 slides
Effective Reading Techniques: Skimming, Scanning, and More
Explore different reading techniques like skimming, scanning, extensive reading, and intensive reading. Skimming helps to quickly grasp the main idea, while scanning is useful for finding specific information. Extensive reading is for pleasure, while intensive reading involves deep understanding and
0 views • 6 slides