Rwanda HIE Patient Identity Management System Overview
The Rwanda Health Information Exchange (HIE) system focuses on patient identity management to uniquely identify individuals seeking healthcare across the country. By maintaining a set of identifiers in the client registry and avoiding duplication of patient records, the system ensures efficient and
12 views • 8 slides
Active Directory Self Service Password Reset Tool, cionsystems
It provides the feature of delegated web access administration, self-registration, self-service and password management. \/\/rb.gy\/1tjfv5
2 views • 2 slides
Unlocking Solutions: Addressing QuickBooks Company File Incorrect Password Issue
Unlocking Solutions: Addressing QuickBooks Company File Incorrect Password Issues\nQuickBooks, a vital tool for businesses, can encounter password-related hurdles, disrupting workflow. This guide explores causes and solutions to incorrect password issues. Forgotten passwords, user permission errors,
1 views • 5 slides
Amateur Radio Licensing Regulations and Call Signs in the UK
Learn about the licensing regulations, privileges, call sign formats, secondary identifiers, and addresses for amateur radio operators in the UK. Discover the differences between Foundation, Intermediate, and Full license classes, as well as the various call sign formats used in England. Explore the
0 views • 87 slides
IEEE 802.11-20-0745r0 Identifier Privacy Service
In IEEE 802.11-20-0745r0, the focus is on protecting identifiers to enhance privacy in wireless networks. The proposal suggests using ECIES for identifier protection, covering various identifiers like password identifiers and PMKIDs. By implementing a scheme similar to 3GPP and IETF standards, the s
4 views • 7 slides
Cybersecurity Best Practices for Password Protection and Incident Response
Enhance your cybersecurity knowledge with insights on password management, cybercriminal tactics, creating strong passwords, and password complexity. Learn how to safeguard your data and prevent cyber threats by implementing strong password rules, multi-factor authentication, and incident response s
2 views • 24 slides
Understanding Device Settings and Strong Passwords for Digital Citizenship
This lesson focuses on understanding device settings and the importance of creating strong passwords for digital citizenship. It covers topics such as changing backgrounds, locking screens, creating strong passwords, common password mistakes to avoid, and tips for password safety. The lesson also in
1 views • 11 slides
Federal Agencies Guidance on Ethics, Compliance, and Audit Services under NSPM-33
The White House OSTP released guidance for federal agencies to implement NSPM-33 focusing on disclosure requirements, digital identifiers, consequences for violations, information sharing, and research security programs. The guidance emphasizes supporting open scientific inquiry and nondiscriminator
0 views • 10 slides
Understanding Mode-S Radar Operations and Identifiers
This simplified explanation delves into the fundamental principles of radar operations, focusing on Primary and Secondary radar systems, including Mode A/C and Mode S functionalities. It covers radar interrogation, replies, and the significance of radar identifiers (II and SI codes) in managing over
0 views • 19 slides
Strengthen Your Digital Literacy with Strong Password Strategies
Enhance your digital literacy by learning about the importance of strong passwords, strategies for creating secure passwords, and the role of password managers. Explore various resources, videos, and tools to improve your password security and protect your online accounts effectively.
0 views • 5 slides
Promote Feature Adoption with Self-Service Password Reset Posters
Enhance feature adoption of self-service password reset among your employees with these ready-to-use posters. Simply customize and print them to encourage password security awareness in your workplace. Don't risk productivity downtime due to forgotten passwords – empower your team to reset their p
0 views • 13 slides
Distributed Algorithms for Leader Election in Anonymous Systems
Distributed algorithms play a crucial role in leader election within anonymous systems where nodes lack unique identifiers. The content discusses the challenges and impossibility results of deterministic leader election in such systems. It explains synchronous and asynchronous distributed algorithms
2 views • 11 slides
Streamlining Customer Service Management with Digital Identifiers
Revolutionize your customer service experience by leveraging cloud-based digital identifiers for unique customer identification, service validation, and access control. Seamlessly create, personalize, and send identifiers to customers via mobile and email, enabling automated service activation post-
0 views • 15 slides
Understanding Data Linkages for DaVINCI
Explore the intricacies of patient identifier linkages and linking methodologies for direct care data in the context of DaVINCI. Learn about different systems such as CHCS, AHLTA/CDR, MHS Genesis, and how they utilize identifiers like EDIPN, SSN, and more to establish unique patient records. Discove
0 views • 29 slides
Unveiling the Realities of Privacy in App Usage
Exploring the complexities of privacy policies, the disclosure of user data by apps, and the implications of mobile tracking. Learn how AppCensus assists parents in understanding app data collection practices and the risks associated with sharing persistent identifiers. Discover how third parties ut
0 views • 25 slides
Safely Logging Password-Derived Measurements for Web Login Systems
Design a secure measurement framework called Gossamer to assess risks associated with password-based measurements for web login systems. Explore ways to differentiate between benign and malicious traffic, and consider adding instrumentation to enhance security. Learn how attackers exploit password-d
0 views • 12 slides
Guide to Logging in and Setting Up Core-CT for the First Time
Accessing Core-CT for the first time involves using your State of Connecticut Employee ID and temporary password. Follow the steps to log in, set up a new password, and establish a forgotten password help feature. This guide provides clear instructions and visuals for each step.
0 views • 19 slides
Framework for Research Data Management and Persistent Identifiers at Waipapa Taumata Rau
This research delves into the integrated framework for Research Data Management (RDM) and the initiatives around Persistent Identifiers (PIDs) and ORCID implementation at Waipapa Taumata Rau. It explores the background, aims, and priorities of the RDM Programme for 2022-2024, focusing on improving R
0 views • 9 slides
Progress on IEEE 802.11-23/1576r0 Password Identifiers
Attempting to address the issue of supporting multiple PSKs per SSID in IEEE 802.11 networks, this document outlines the challenges with the existing approach, proposes encrypting STAs' identities in the AP's public key using HPKE, and discusses the opposition and alternative suggestions to improve
0 views • 10 slides
Challenges and Design Issues in MS-DOS Development
Windows faced difficulties in enabling multitasking while integrating with non-multitasking MS-DOS and device drivers. MS-DOS lacked multiprocessor synchronization capabilities, limiting shared resource access. Security features like unalterable password identifiers and command-based usage reduced v
0 views • 159 slides
Interactive Password Security Activity for Children
This presentation recaps the importance of strong passwords, techniques for creating them, and the significance of two-factor authentication. The lesson notes guide discussions on creating secure passwords using the "three random words" method and avoiding personal details. The interactive game "Gue
0 views • 4 slides
Best Practices for Secure Password Storage - OWASP Foundation Guidelines
Learn about secure password storage techniques recommended by OWASP Foundation, including adding salt, slowing down hashing functions, using HMAC isolation, and imposing difficult verification processes on attackers. Remember to use proper encoding, avoid limiting password types or lengths unreasona
0 views • 10 slides
Techniques and Tools for Offline Password Cracking
Explore the world of offline password cracking techniques using tools like John the Ripper. Learn about the motivation behind cracking user account passwords, gaining root privilege, and compromising vulnerable systems to obtain password hashes for further exploitation. Enhance your understanding of
0 views • 15 slides
Understanding Fine-Grained Password Policies in Active Directory
Explore the intricacies of Fine-Grained Password Policies (FGPP) in Active Directory, covering topics such as domain account policies, policy recovery methods, interpreting pwdProperties attribute, and implementing PSOs for granular password settings. Delve into the nuances of password complexity, h
0 views • 11 slides
Understanding Health Plan Identifiers: HPID vs. OEID
Health Plan Identifiers (HPIDs) play a crucial role in the healthcare industry by uniquely identifying health plans during electronic transactions. This article delves into the significance of HPIDs, the distinction between Controlling Health Plans (CHP) and Subhealth Plans (SHP), and the comparison
0 views • 17 slides
Understanding Naming Systems in Distributed Systems
Entities in distributed systems are uniquely identified using names, addresses, and identifiers. Naming systems assist in name resolution and can be categorized into flat, structured, and attribute-based naming. Flat naming uses random strings as identifiers, and various mechanisms such as broadcast
0 views • 21 slides
Key Concepts in AP Computer Science A Exam Review
Essential topics covered in AP Computer Science A Exam include identifiers, primitive data types, number representation, final variables, and arithmetic operators. Recognizing the basics, such as types, identifiers, operators, and control structures, is crucial for success in the exam. Understanding
0 views • 100 slides
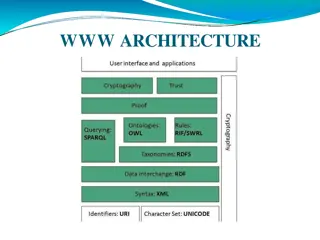
Understanding Web Technologies: From Identifiers to FTP
Explore the world of web technologies from identifiers and character sets to data interchange frameworks and ontologies like OWL. Learn about semantic web layers, cryptography, and FTP protocol objectives. Discover how these technologies work together to create a seamless online experience.
0 views • 72 slides
B2HANDLE: Managing Digital Object Identifiers for Data Persistence
B2HANDLE is a service for minting and managing persistent identifiers (PIDs) to facilitate common operations on digital objects across infrastructures. The system enables automated management of data objects and metadata, facilitates machine-driven workflows, and supports the construction of PID and
0 views • 17 slides
Understanding Persistent Identifiers (PIDs) and Handling Digital Objects
Explore the significance of Persistent Identifiers (PIDs) in assigning unique identifiers to digital objects, ensuring reproducibility, and facilitating reliable data management. Learn about versioning, PID binding, strategies for assigning PIDs, and the evolving role of repositories in managing dig
0 views • 6 slides
Understanding Persistent Identifiers (PIDs) in Research and Data Management
Persistent Identifiers (PIDs) play a crucial role in establishing long-lasting digital references for objects, contributors, and organizations in the realm of research and data management. This introduction delves into the significance of PIDs, focusing on their role in identifying and connecting di
0 views • 13 slides
Recommendations for Creating Identifiers in Data Catalogues
National data catalogues have specific requirements for identifiers, such as using HTTP URIs for open data datasets. While most INSPIRE datasets only have UUID identifiers, adhering to the DCAT-AP standard recommends using HTTP URIs. Recommendations for creating identifiers in the geodata sector are
0 views • 5 slides
Understanding Data Modeling: Key Concepts and Applications
Explore the fundamentals of data modeling through concepts like entities, attributes, identifiers, and their real-world applications, including examples related to Greta Garbo, modeling reality, and global legal entity identifiers. Discover how to design data models for diverse scenarios, such as re
0 views • 57 slides
Piloting Unique Identifiers for Geospatial Data - Nordic Forum Presentation
Presentation at the Nordic Forum for Geography and Statistics on piloting unique identifiers for geospatial data by Tuuli Pihlajamaa. The agenda included terms used, background for the pilot, aims, results, and future plans. Detailed discussions on terms like URI, RDF, JHS 193, INSPIRE guidelines, a
0 views • 15 slides
Understanding Password Security: Techniques and Best Practices
Delve into the world of password security with this comprehensive guide, covering topics such as password gathering, cracking strategies, tools, types of passwords, hashes, salting, better hashes, and hash identification. Learn how to enhance security measures and protect against malicious attacks.
0 views • 20 slides
Protecting Password Identifiers in IEEE 802.11-21
This submission addresses the need for safeguarding password identifiers in SAE to ensure privacy and prevent attackers from constructing personally identifiable information. The document presents two potential solutions, ultimately recommending the use of symmetric cryptography for efficient protec
0 views • 11 slides
Understanding Password Guessability Metrics in Real-World Security
Delve into the realm of password guessability metrics to enhance password security. Explore how measuring guessability aids in eliminating weak passwords, aiding users in creating stronger ones, and assessing security against various cracking algorithms. Uncover the significance of statistical and p
0 views • 27 slides
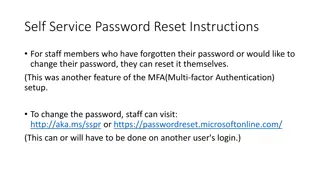
Self-Service Password Reset Instructions for Staff Members
Staff members can easily reset or change their password through self-service options using Multi-Factor Authentication. They can visit the provided links, verify their identity through email and phone number, and reset their password securely. Follow the step-by-step guide for a hassle-free password
0 views • 4 slides
Guide to Logging into Your Chromebook
This step-by-step guide provides instructions on how to log into your Chromebook using either your student ID and password or a QR code. Simply open the lid, press the power button, select "Next," and then proceed to log in with your credentials. For password login, enter your student ID and the def
0 views • 6 slides
Enhancing Wi-Fi Security with User-Friendly WPA3 Passwords
Proposal to enhance Wi-Fi security by incorporating password and password identifier hashes in the SAE commit exchange, enabling devices to hint to access points which password will be used. This approach aims to improve network efficiency and user experience while addressing privacy concerns associ
0 views • 8 slides