Mern Stack Training Institute in - Hyderabad
Visualpath is one of the best MERN Stack Training Course in - Hyderabad institutes in Hyderabad. We are providing Live Instructor-Led Online Classes delivered by experts from Our Industry. We will provide live project training after course completion. Enroll Now!! Contact us 91-9989971070.\nwhatsAp
1 views • 13 slides
MERN Stack Online Training - Courses - MERN STACK Training - Ameerpet
Visualpath offers the Best MERN STACK Training - Ameerpet by real-time experts for hands-on learning. Our MERN Stack Online Training - Courses is available in Hyderabad and is provided to individuals globally in the USA, UK, Canada, Dubai, and Australia. Contact us at 91-9989971070.\nJoin us on wha
3 views • 13 slides
MERN Stack Training in Hyderabad - MERN Stack Training Course in Hyderabad
\nVisualpath offers the Best MERN Stack Training in Hyderabad by real-time experts for hands-on learning. Our MERN Stack Training Course in Hyderabad is available in Hyderabad and is provided to individuals globally in the USA, UK, Canada, Dubai, and Australia. Contact us at 91-9989971070.\nJoin us
1 views • 13 slides
Stack Based Attacks in Linux (an intro)
Explore the world of stack-based attacks in Linux through an introductory session presented by Bryce L. Meyer at the Saint Louis Linux Users Group. Covering topics from weaknesses to exploits, shellcode, and mitigations like stack canaries and address space randomization, this overview delves into c
7 views • 60 slides
Mastering Networking for Career Development
Learn about ethical networking, common myths, building networks, and connecting with others. Discover the art of reciprocal relationships to achieve professional goals. Join the Professional Services Careers Club to enhance your networking skills!
4 views • 31 slides
A Safety Expert’s Guide: How to Stack Pallets Safely
In the bustling world of warehouses, logistics, and manufacturing, the proper stacking of pallets is a critical aspect of maintaining a safe and organized workspace. As a safety expert, I\u2019ve seen firsthand the importance of implementing best practices to ensure the secure stacking of pallets. I
14 views • 2 slides
Important Networking Concepts Overview
Review essential networking concepts including protocol architecture, protocol layers, encapsulation, network abstractions, communication architecture, and TCP/IP protocol suite. Understand the functions of different layers in networking for reliable data transfer and communication efficiency.
3 views • 43 slides
Piezoelectric Stack Actuator Market Analysis, Size, Share, Growth, Trends Foreca
The Global Piezoelectric Stack Actuator market stands at the forefront of technological driving advancements in various industries through its dynamic applications. These actuator systems harness the unique properties of piezoelectric materials, providing precision and versatility in a range of mech
0 views • 8 slides
Efficient Stack Emission Monitoring Procedure for Air Quality Control
Stack emission monitoring is crucial for industries to assess and reduce pollutants in exhaust air. This procedure involves tasks like measurement, testing, and analysis of flue gases. Sampling sites are selected strategically for accurate readings, and molecular weight and gas velocity are determin
1 views • 11 slides
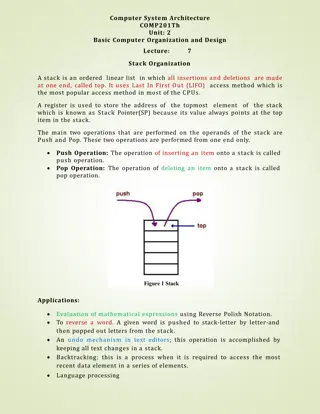
Stack Organization in Computer Systems
A stack is an ordered linear list where insertions and deletions occur at one end, known as the top. It follows the Last In First Out (LIFO) access method and is commonly used in CPUs. Key operations include Push (inserting) and Pop (deleting) items from the stack. Applications include evaluating ma
0 views • 5 slides
Understanding The Stack in Embedded Systems Design
The stack plays a crucial role in embedded systems design by providing a last-in, first-out storage structure for dynamic memory allocation. In this chapter, Dr. Brock J. Lameres explores the concept of the stack, its physical implementation in microcontrollers like the MSP430FR2355, and the operati
2 views • 27 slides
Understanding Networking Bridges and Transceivers
Bridges in networking play a crucial role in dividing logical bus networks into subnets, improving performance by managing traffic flow. Although network switches have largely replaced bridges today, the advantages of bridges in reducing unnecessary traffic and isolating busy networks remain signifi
0 views • 40 slides
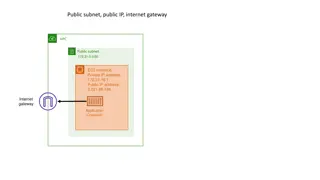
Networking Modes in AWS VPC Environments
Explore different networking modes such as Bridge mode with static mapping, Bridge mode with dynamic mapping, and AWS VPC networking mode in an AWS VPC environment with various configurations and scenarios.
0 views • 18 slides
Unlocking the Power of Networking and Developing Your LinkedIn Profile
Networking is a vital aspect of career growth. Learn the art of networking, both in-person and online. Discover the benefits of LinkedIn and how it can enhance your professional connections. Building a strong network opens up opportunities that may lead to career advancement. Utilize these strategie
0 views • 34 slides
Understanding Cabling Types and Specifications in Networking
Exploring various cabling options like Unshielded Twisted Pair, Shielded Twisted Pair, Coaxial Cable, and Fiber Optic Cable used in networking. Learn about different cable specifications, connectivity types, and cabling orders for efficient networking setups.
0 views • 11 slides
Understanding IMIX in Networking and Testing Tools
IMIX, or Internet Mix, refers to a mixture of packet sizes used to simulate real-world network conditions for testing networking devices. Various tools and methods, such as Genome Reporting, Moongen, T-Rex, and Spirent TestCenter, implement IMIX with specific packet size distributions and characteri
1 views • 8 slides
Growth of CA Firms through Networking & Merger
This document discusses the growth and trends of CA firms in India, focusing on networking, merger, and current practices. It highlights the total number of members, types of firm partnerships, guidelines for networking, current trends in practice, barriers to networking/merger, and the 2021 guideli
0 views • 32 slides
Diploma in Hardware & Networking: Upgrade Your IT Skills
This course provides comprehensive knowledge and practical experience in computer hardware and networking, essential for managing IT infrastructure. Gain expertise in PC hardware maintenance, customer and networking support, and more to pursue a career as a Hardware and Network Engineer. Learn to as
1 views • 8 slides
Understanding Activation Records and Stack in Assembly Programming
Explore the key concepts of activation records and the stack in assembly programming, including their roles in function calls, memory management, and variable storage. Gain insights into the low-level layout of variables, call conventions in MIPS and x86, and practical examples illustrating stack op
2 views • 66 slides
Networking and Partnership Formation for AECD at University of Gondar College of Education
Networking and partnership formation are vital for Adult Education and Community Development (AECD) at the University of Gondar, emphasizing the power of collaboration and interdependence. Various concepts such as interdependence, independence, and dependence underscore the importance of working tog
0 views • 120 slides
Networking: Mastering the Basics
Learn the principles and importance of networking, debunking myths and exploring real benefits. Discover networking goals, strategies, and conversation starters for effective networking. Enhance career opportunities, build relationships, and develop valuable connections in various settings.
0 views • 13 slides
Optimizing User-Space Network Services with F-Stack and FreeBSD TCP/IP Stack
F-Stack, a user-space network service using DPDK and FreeBSD TCP/IP stack, addresses challenges in handling service traffic like CDN and live streaming. By leveraging 25GbE, 40GbE, and 100GbE NICs, coupled with multi-core CPUs and kernel bypass techniques, F-Stack overcomes bottlenecks between user
1 views • 17 slides
Exploring Time-Sensitive Networking Horizons and Possibilities for Low Latency Solutions
Delve into the world of time-sensitive networking (TSN) as it offers bounded low-latency solutions for various applications. Discover TSN components, tools, and protocols such as frame replication, path control, per-stream filtering, time synchronization, and more. Gain insights from Jnos Farkas's p
2 views • 23 slides
Networking Fundamentals and Challenges in Data Centers
Today's lecture covers definitions of routing and switching in networking, focusing on data center challenges, traffic patterns, fabric management, and parallelism within networks. The session also explores the role of switches and routers in data center and Internet design, emphasizing the importan
0 views • 38 slides
Understanding Buffer Overflow Attacks at Carnegie Mellon
Learn about the Carnegie Mellon 15-213 Recitation Attack Lab, where you can hijack programs using buffer overflow attacks. Gain insights into stack discipline, stack frames, and defeating secure programs through return-oriented programming. Dive into topics like stack smashing attacks, buffer overfl
8 views • 24 slides
Understanding the OSI Model and Layered Tasks in Networking
The content highlights the OSI model and layered tasks in networking, explaining the functions of each layer in the OSI model such as Physical Layer, Data Link Layer, Network Layer, Transport Layer, Session Layer, Presentation Layer, and Application Layer. It also discusses the interaction between l
1 views • 41 slides
Understanding Web Security Fundamentals in Networking
This lecture delves into the intricate layers of web security, focusing on vulnerabilities by year, CSRF attacks, and defensive strategies. Topics covered include the application layer, networking stack, HTTP protocols, and common security threats like XSS and SQL injection. Various defense mechanis
0 views • 27 slides
Protective Measures Against Stack Overflows
Host-based defenses such as Canaries, DEP, ASLR, and CFI play a crucial role in safeguarding systems against malicious attacks. Canaries act as early warning systems, alerting to stack overflows by monitoring changes in sensitive data. By implementing stack canaries, developers can prevent buffer ov
0 views • 51 slides
Understanding x86-64 Procedures and Data Structures
This content provides insights into x86-64 programming, covering topics such as procedures, integer registers, stack frames, locals in the red zone, interesting features of stack frames, arrays, multi-dimensional structures, and more. It dives into the usage conventions of integer registers, the all
0 views • 44 slides
Dell ProSupport Networking Support Capabilities Update Sales Training
This training session provides an overview of Dell ProSupport networking support capabilities, focusing on aligning with industry standards. Participants will learn to discuss networking support needs, understand ProSupport differences, and explore Dell's service portfolio. The session covers expert
0 views • 10 slides
Understanding the Importance of Networking for Community Growth
Networking plays a crucial role in fostering supportive relationships within a community, facilitating the exchange of talents, knowledge, and compassion. This article explores the concept of networking, its benefits, disadvantages, and practical steps to establish a structured network within the Os
0 views • 10 slides
Integrating OpenContrail into Neutron Stadium - Networking Advancements
Integrating OpenContrail into Neutron Stadium introduces Networking-OpenContrail, bridging OpenContrail with Neutron to enhance network functionality. The project aims to achieve full parity between the two platforms, with active contributors encouraged to join the development efforts. Deployment op
0 views • 7 slides
Understanding Memory Stack and Variable Scope in Computer Architecture
This content delves into the scope of variables, the stack in memory architecture, automatic and global variables, and the concept of constant types. It explains the functioning of the stack, how function calls are managed, and the allocation of variables within stack frames. The relationship betwee
0 views • 18 slides
Maximizing Networking Opportunities at Career Fairs and Conferences
Enhance your networking skills with practical tips on approaching strangers, asking insightful questions, and making lasting connections at career fairs and conferences. Understand the importance of networking for knowledge sharing, collaboration, and discovering hidden job opportunities. Learn the
0 views • 21 slides
Understanding x86-64 Stack and Register Usage at Carnegie Mellon
Explore the concepts of stack management, function invocation, and register usage in x86-64 architecture as taught in Carnegie Mellon's 15-213 recitation on Attack Lab. Learn about stack operations, caller vs. callee functions, and the conventions for using registers effectively. Gain insights into
0 views • 26 slides
Understanding Stack Protection and Exploitation Techniques
Delve into the world of stack protection and exploitation, covering topics like exploiting arbitrary write, issues with stack canaries, and shadow stack usage. Explore defense mechanisms like Stack Cookie and learn about the power of exploiting vulnerabilities to write arbitrary memory. Discover met
0 views • 23 slides
Understanding Stack Buffer Overflow Vulnerabilities
Stack buffer overflow is a critical security issue caused by writing more data to a buffer than allocated, leading to bugs, crashes, and potential attacks. This vulnerability, exemplified by the Twilight Hack, allows executing arbitrary code. Learn about its causes, implications, and mitigation stra
0 views • 7 slides
Understanding Buffer Overflow in Stack: SEED Workshop Lab
This content provides a comprehensive overview of buffer overflow in stack focusing on SEED Workshop Lab scenarios. It covers principles, practice, high-level pictures, program memory layout, function stack layout, function call chains, vulnerable program examples, and more. Through detailed images
0 views • 34 slides
Understanding Stack Overflow Vulnerabilities and Exploitation Techniques
Explore the history of stack overflow vulnerabilities, learn how to control a PC using stack overflow, place shellcode in memory, calculate shellcode addresses, and execute shellcode. Understand different types of overflows including stack overflow, heap overflow, and integer overflow. Delve into th
0 views • 33 slides
Evolving Computer Communication and Networks: P2P Networking, Media Streaming, CDN
Delve into the continuously evolving landscape of computer communication and networks, focusing on P2P networking, media streaming, and CDN technologies. Explore topics such as overlays, P2P applications, multimedia streaming advancements, and the interplay between internet, data processing, and dis
0 views • 63 slides