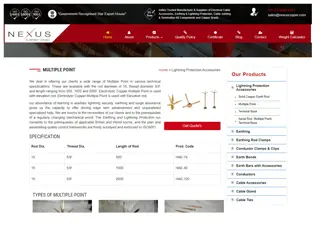
Multiple Point Lightning Protection Accessories, Multiple Point, Electrolytic Co
We are a leading manufacturer, exporter and supplier of a wide range of Multiple Point Lightning Protection Accessories, Multiple Point, Electrolytic Copper Multiple Point, Earthing and Lightning Protection at very cheap prices for our clients from Mumbai, India.
1 views • 3 slides
2022 Thales Access Management Index
Thales Access Management Index highlights the current landscape of access security, revealing insights on multi-factor authentication adoption, remote and privileged user access management, VPN usage trends, challenges faced, and preferences towards third-party access management. The report emphasiz
2 views • 9 slides
Understanding Multiple Linear Regression: An In-Depth Exploration
Explore the concept of multiple linear regression, extending the linear model to predict values of variable A given values of variables B and C. Learn about the necessity and advantages of multiple regression, the geometry of best fit when moving from one to two predictors, the full regression equat
4 views • 31 slides
Top 4 Eligibility Criteria for Multiple Entry Schengen Visa from Dubai (1)
Want to visit Europe multiple times? Learn the must-haves for a multiple-entry Schengen Visa from Dubai in our easy infographic. \n\nReady to jet-set? Contact Now! \n\/\/ \/product\/schengen-visa\/
2 views • 6 slides
Personnel Safety Systems and Access Control at CERN Facilities
Personnel Safety Systems at CERN include ODH detection, fire safety measures, and access control to protect personnel from hazards. Various access control layers are implemented to regulate entry to different parts of the facility, ensuring only trained personnel access underground areas. Biometric
0 views • 19 slides
Principles and Applications of Multiple Effect Evaporators in Chemical Engineering
This article discusses the operation and design principles of multiple effect evaporators in the context of chemical engineering. It covers the heat transfer mechanisms, efficiency considerations, and calculations involved in these systems, highlighting the benefits of utilizing multiple effects for
0 views • 11 slides
Understanding Analysis of Variance (ANOVA) for Testing Multiple Group Differences
Testing for differences among three or more groups can be effectively done using Analysis of Variance (ANOVA). By focusing on variance between means, ANOVA allows for comparison of multiple groups while avoiding issues of dependence and multiple comparisons. Sir Ronald Fisher's ANOVA method provides
0 views • 28 slides
Port of Stockton Restricted Area Access Control and ID Card Policy
Access to restricted areas at the Port of Stockton facilities requires possession of a TWIC (Transportation Worker Identification Credential). Only authorized personnel, such as employees, contractors, and those with regular access, may receive a Port Access Card after approval by the Facility Secur
0 views • 6 slides
Understanding Multiple Regression in Statistics
Introduction to multiple regression, including when to use it, how it extends simple linear regression, and practical applications. Explore the relationships between multiple independent variables and a dependent variable, with examples and motivations for using multiple regression models in data an
0 views • 19 slides
Discussion on Multi-RU Allocation in IEEE 802.11be Standard
In January 2020, a discussion took place on the allocation of multiple Resource Units (RUs) to a single Station (STA) in the IEEE 802.11be standard. The proposal suggested categorizing RUs into small and large types, avoiding aggregation across multiple 20MHz channels. It emphasized assigning a sing
2 views • 29 slides
Understanding Multiple Alleles in Genetics
Explore the concept of multiple alleles in genetics through examples like pea color inheritance and human blood types. Learn how multiple alleles create various phenotypes and genotypes, illustrating concepts of dominance, recessiveness, and co-dominance in genetic inheritance.
0 views • 15 slides
Understanding Multiple Implementation Inheritance and Roxy Code Generation
Exploring the concept of software building blocks and concerns in Object-Oriented Programming (OOP), highlighting the importance of managing multiple concerns within classes. Delve into the challenges and solutions of multi-concern implementation including the use of mixins and plugin-based imitatio
1 views • 9 slides
Understanding Multiple Disabilities in Special Education
Multiple disabilities refer to the presence of two or more impairments that significantly impact educational performance, leading to challenges in standard special education settings. This includes various combinations of disabilities such as mental retardation, blindness, orthopedic impairment, and
4 views • 35 slides
Multiple Objective Linear Programming: Decision Analysis and Optimization
Explore the complexities of multiple objective linear programming, decision-making with multiple objectives, goal programming, and evolutionary multi-objective optimization. Discover the trade-offs and conflicts between various objectives in optimization problems.
6 views • 84 slides
Framework for Advertising Multiple-Link Operations in IEEE 802.11
Proposed framework for advertising Multiple-Link Operations (MLO) capabilities in IEEE 802.11 networks classified into three categories: Common MLD Information, Per-Link Information, and Multiple BSSID features. Introduces a new element, Multiple Link Attribute (MLA) element, with profiles for each
0 views • 27 slides
Updates on Belamaf in Multiple Myeloma: ASH 2023 Highlights
Explore the latest findings from the American Society of Hematology (ASH) 2023 Hybrid Congress regarding Belamaf in multiple myeloma, including real-world outcomes, safety and efficacy analyses, long-term treatment impacts, infection risk, ocular toxicity prevention, and more. Key presentations cove
0 views • 35 slides
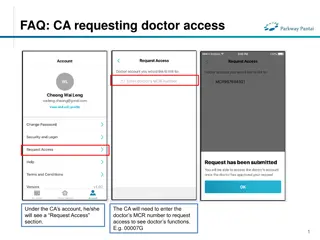
FAQs for Doctor and Clinical Assistant (CA) Account Access Management
Learn how CAs can request access to doctors' functions by entering the MCR number, how doctors can grant or remove CA access, and how CAs can manage access to multiple doctors. The process includes requesting, approving, and unlinking accounts, ensuring efficient and secure access management in a cl
0 views • 4 slides
Challenges and Techniques in Multiple Sequence Alignment
Multiple Sequence Alignment (MSA) poses a significant challenge due to NP-hard problems, large datasets, and the lack of accuracy in current methods. Novel techniques are needed to address scalability and accuracy issues in MSA, which serves multiple purposes like phylogeny estimation and structure
1 views • 52 slides
AMP Link Access Modes in IEEE 802.11-24 Presentation
Presented in the March 2024 document IEEE 802.11-24/0421r0, Solomon Trainin from Wiliot discusses three modes of AMP link access, including random access of multiple AMP STAs, access of a single AMP STA, and exemplary frame exchanges for each mode.
0 views • 10 slides
Guidelines for Multiple Primary & Histology Coding in Colon Cancer Abstractor Training
Utilize the Multiple Primary & Histology Coding Rules for accurate case abstraction. Understand equivalent terms, definitions, and instructions to determine multiple primaries for solid malignant tumors diagnosed after January 1, 2007. Avoid relying on physician statements and prioritize following t
0 views • 64 slides
Introduction to Pig Latin for Data Processing in Hadoop Stack
Pig Latin is a dataflow language and execution system that simplifies composing workflows of multiple Map-Reduce jobs. This system allows chaining together multiple Map-Reduce runs with compact statements akin to SQL, optimizing the order of operations for efficiency. Alongside Pig Latin, the Hadoop
0 views • 20 slides
Exploring Multiple Publishers and Subscribers in ROS Nodes
Understanding how to implement multiple publishers and subscribers in a single ROS node to control different turtles simultaneously, along with managing message variables efficiently. This tutorial walks through the process of defining and initializing publishers/subscribers and ensuring message del
0 views • 17 slides
Dealing with Multiple Related Conditions in Programming
When handling multiple related conditions in programming, using multiple `if` statements can become cumbersome. This guide explores how to efficiently manage such scenarios using branching techniques like `else-if` clauses. Learn about structuring your code to handle various conditions effectively w
0 views • 39 slides
Complex Case Study of Fever of Unknown Origin in a Patient with Multiple Sclerosis
A 42-year-old African American male with a history of Multiple Sclerosis presented with a fever of unknown origin, challenging the medical team to identify the underlying cause despite multiple investigations, treatments, and consultations. His complex medical history, including prior UTI treatment
0 views • 19 slides
Open Access at Charles University: Opportunities and Challenges
Charles University is navigating the landscape of open access following the implementation of the Czech National Open Access Strategy. The university is working towards making all research articles and proceeding papers open access, monitoring article processing charges, and promoting open access as
0 views • 24 slides
Understanding Multiple Inheritance in Object-Oriented Programming
Multiple inheritance in object-oriented programming allows a derived class to inherit from more than one base class, creating a unified derived class. This design structure is suitable when the base classes are orthogonal and have no common attributes or behaviors. The derived class logically combin
0 views • 14 slides
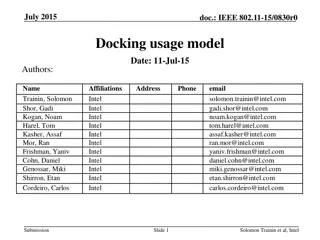
Wireless Office Docking Model for Multiple Devices
This document outlines a usage model for office docking involving wireless connections between mobile devices and various peripheral devices such as monitors, hard drives, printers, and more. It describes scenarios for single and multiple devices in both home and office settings, emphasizing the nee
0 views • 5 slides
Understanding Ethernet and Multiple Access Protocols in Computer Networks
Exploring the fundamentals of Ethernet and multiple access protocols in computer networks, this content discusses the two primary categories of multiple access protocols - contention access and controlled access. It delves into topics such as CSMA/CD, LANs, performance of multiple access schemes, ad
0 views • 7 slides
Understanding Shared Memory, Distributed Memory, and Hybrid Distributed-Shared Memory
Shared memory systems allow multiple processors to access the same memory resources, with changes made by one processor visible to all others. This concept is categorized into Uniform Memory Access (UMA) and Non-Uniform Memory Access (NUMA) architectures. UMA provides equal access times to memory, w
0 views • 22 slides
MATLAB Data Plotting Techniques for Multiple Functions
Explore advanced MATLAB techniques for plotting multiple functions in a single plot and across multiple subplots. Learn how to create visually appealing plots using functions like plot, subplot, title, and legend. Enhance your data visualization skills through hands-on examples and practical applica
0 views • 11 slides
Enhanced Algorithm for Internal Multiple Attenuation in Seismic Imaging
This research discusses the development of an improved algorithm for internal multiple attenuation in seismic imaging. The focus is on addressing the challenges in onshore and offshore regions close to a 1-D earth model. The algorithm aims to enhance the efficiency and accuracy of data processing in
0 views • 61 slides
Harvard Chan School 2021 Yearly Access Review Process
The Harvard Chan School conducts its annual Yearly Access Review (YAR) process to review user access to various financial systems. The process involves assessing permissions, levels of access, and organizational details for each team member. Instructions are provided on reviewing worksheets, adding
0 views • 19 slides
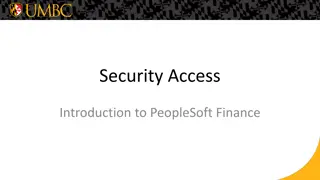
Understanding Security Access in PeopleSoft Finance
Explore the various levels of security access in PeopleSoft Finance, from basic entry access to transaction entry, approvals, and procurement processes. Learn how to request individual and department security access and find relevant forms on the financial services website. Discover the different ty
0 views • 11 slides
Advanced Networking with Multiple Distributed Gateway Ports in OVN
Explores the latest advancements in networking technology with OVN by allowing the creation of multiple Distributed Gateway Ports per logical router. This feature enables connectivity to multiple external networks, supporting scenarios like shared services, NAT configurations, and load balancing. Di
0 views • 7 slides
Desired Features of a Software Build System for DUNE DAQ
Discussion on the desired features of a software build system for DUNE DAQ, including creating C++ builds, supporting multiple languages, handling multiple software versions, efficient change management, easy installation processes, modularity, and more. The aim is to streamline the software develop
0 views • 9 slides
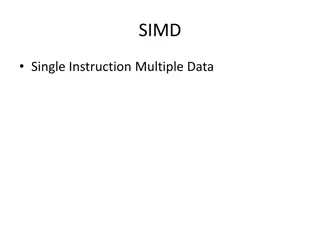
Understanding SIMD in Computer Architecture
SIMD (Single Instruction Multiple Data) architecture plays a crucial role in optimizing performance for parallel computing tasks. It allows for the simultaneous processing of multiple data elements, enhancing efficiency in various applications. The concept is rooted in executing the same operation a
0 views • 24 slides
CPA-Security and Multiple Message Security in Cryptography
Today's goal is to build a CPA-secure encryption scheme focusing on multiple message security. The concept of indistinguishable multiple encryptions against eavesdropping attackers is explored, highlighting the importance of secure encryption schemes in the presence of an eavesdropper. The experimen
0 views • 22 slides
Analysis of Proteasome Gene SNPs as Molecular Markers for Multiple Sclerosis in Latvian Population
This study by I. Trapina aims to investigate the prevalence and functionality of SNPs in proteasome genes to assess their potential as molecular markers for multiple sclerosis in the Latvian population. Multiple sclerosis is an autoimmune disease affecting the central nervous system, and the role of
0 views • 13 slides
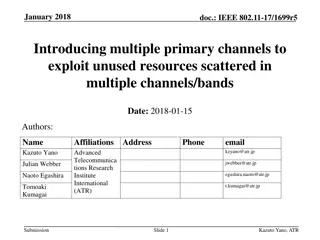
Enhancing Wireless LAN Throughput with Multiple Primary Channels
This document discusses the need for increasing system throughput in wireless LAN networks due to the growing demand for WLAN traffic. By introducing multiple primary channels, unused resources scattered across various channels can be exploited to improve quality of service and enhance transmission
0 views • 20 slides
Advancements in Non-Orthogonal Multiple Access (NOMA) Technology
Non-Orthogonal Multiple Access (NOMA) technology has revolutionized the way multiple users' messages are superimposed and transmitted over the same frequency simultaneously. NOMA offers enhanced spectral efficiency, massive connectivity, and increased throughput compared to traditional multiple acce
0 views • 5 slides