Deep Dive
Explore the functionalities and installation process of the Intune Management Extension (IME). Learn how IME processes app policies, scripts, and handles failures. Delve into its role in deploying PowerShell scripts and Win32 applications on Windows devices enrolled in Intune. Discover the importanc
0 views • 68 slides
Understanding Malicious Attacks, Threats, and Vulnerabilities in IT Security
Malicious attacks, threats, and vulnerabilities in IT systems pose significant risks and damages. This chapter explores the types of attacks, tools used, security breaches, and measures to protect against cyber threats. Learn how security professionals safeguard organizations from malicious attacks
0 views • 24 slides
Understanding Typosquatting in Language-Based Package Ecosystems
Typosquatting in language-based package ecosystems refers to the malicious practice of registering domain names that are similar to popular packages or libraries with the intention of tricking developers into downloading malware or compromised software. This threat vector is a serious issue as it ca
0 views • 23 slides
Understanding Different Types of Scripts in HEC-ResSim
Explore the two main categories of scripts in HEC-ResSim - scripts executed outside simulations and scripts executed during simulations. Learn about the functions and properties of each type, including scripted rules and state variable scripts. Discover how these scripts compute flow limits, store m
6 views • 23 slides
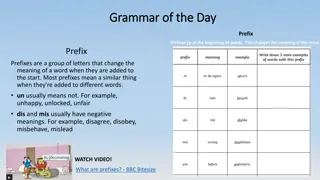
Understanding Play Scripts for Children
Explore the fundamentals of play scripts, including the role of prefixes in altering word meanings, the features of play scripts, and examples of popular plays. Dive into the significance of cast lists, scene descriptions, and stage directions in creating engaging scripts for young actors. Uncover t
0 views • 14 slides
Understanding Scripting in HEC-ResSim
Explore the two categories of scripts in HEC-ResSim - executed outside simulations and during simulations. Learn about static scripts for pre-processing, running simulations, and post-processing, along with the tools like Script Selector and Script Editor for script execution and editing.
0 views • 34 slides
Efficient Malicious URL Detection with Bloom Filters
Google's Chrome team faces the challenge of detecting malicious URLs without heavy memory usage. Universal hashing and Bloom Filters are discussed as innovative solutions to address this issue efficiently and effectively, illustrating how K-independent hash functions can improve detection accuracy w
0 views • 19 slides
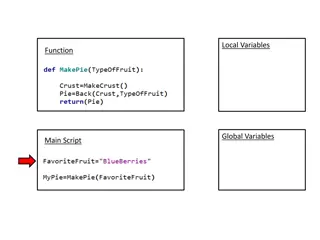
Understanding Local and Global Variables Functions in Scripts
Explore the concept of local and global variables in scripting through examples involving favorite fruits like blueberries and apples. Delve into the intricacies of defining types of fruit, crust, and pies while understanding the scope of variables within functions and scripts.
0 views • 12 slides
Understanding Python Essentials
Python is an interpreted language that is beginner-friendly and supports object-oriented programming. It excels at complex tasks and interactive script development. The setup process, running scripts, and editing can be done efficiently, and Jupyter notebooks provide an interactive environment for s
2 views • 15 slides
Exploring the Malicious Use of Artificial Intelligence and its Security Risks
Delve into the realm of artificial intelligence and uncover the potential risks associated with its malicious applications, including AI safety concerns and security vulnerabilities. Discover common threat factors and security domains that play a vital role in combating these challenges.
0 views • 30 slides
Understanding Typosquatting in Language-Based Package Ecosystems
Typosquatting in language-based package ecosystems involves malicious actors registering similar-sounding domain names to legitimate ones to deceive users into downloading malware or visiting malicious sites. This practice poses a significant threat as users may unknowingly install compromised packa
0 views • 23 slides
Understanding Malicious Software and Its Impact on Computer Systems
Malicious software, commonly known as malware, poses a serious threat to computer systems by exploiting vulnerabilities. This content covers various terminologies, categories, and types of malware, including viruses, worms, rootkits, spyware, and adware. It also delves into how malware can cause dam
0 views • 16 slides
InfiniBand Monitoring Methods at Los Alamos National Laboratory
Los Alamos National Laboratory utilizes InfiniBand monitoring methods to track fabric errors, optimize links, and analyze performance issues in clusters ranging from 8 to 1600 nodes. Developed by Susan Coulter, the IBMon2 suite of scripts identifies hardware errors and performance metrics, sending a
0 views • 16 slides
Revolutionizing Virtual Agent Management with The Dialer Console
Explore a new way to manage virtual agents with The Dialer Console. From starting and stopping campaigns to making dynamic changes to scripts and agents, this innovative tool provides comprehensive control and flexibility. Dive into managing campaigns, controlling agents, changing scripts, and more
1 views • 11 slides
Data Migration Case Study: DevInfo to DSD Using Python, R Scripts, and ArcGIS Online
Explore a case study on migrating data from DevInfo to DSD, involving Python, R scripts, and ArcGIS Online. Learn about the sub-regional workshop in Kigali focusing on data and metadata sharing for English-speaking African countries. Discover the evolution of ChildInfo and DevInfo versions, the upco
0 views • 18 slides
Detecting Drive-By Attacks: Analysis of Malicious Javascript in Big Data Environments
Cybersecurity researcher Andrei Bozeanu delves into the complex world of polymorphic viruses, heuristic analysis, and the similarities between polymorphic viruses and malicious Javascript. Discover how these threats operate and evade detection, highlighting the importance of understanding malware be
0 views • 48 slides
Understanding Malware: Types, Symptoms, and Countermeasures
Malware is malicious software that can alter computer settings, behavior, files, services, ports, and speed. Sources of malware include insufficient security, honeypot websites, free downloads, torrents, pop-ups, emails, and infected media. Symptoms of malware include unusual computer behavior, slow
0 views • 9 slides
Professional Voice Over for Documentary Scripts
Stevegouwsvo.com provides expert voice overs for documentary scripts, offering articulate and evocative narration that complements your storytelling. With a voice that conveys authenticity and depth, Steve enhances documentaries with compelling voice
3 views • 1 slides
Advances in Authenticated Garbling for Secure 2PC
The research discusses advancements in authenticated garbling for achieving constant-round malicious secure 2PC using garbled circuits. It emphasizes the utilization of correlated randomness setup and efficient LPN-style assumptions to enhance communication efficiency significantly. Various techniqu
0 views • 30 slides
Revolutionizing Data Analysis with R Notebooks: A Comprehensive Guide
Embrace the future of data analysis with R Notebooks, a game-changing alternative to conventional scripts. Learn how to effortlessly collate code, commentary, and output into a single document, export to various formats, and streamline your workflow. Say goodbye to the limitations of traditional scr
0 views • 44 slides
Understanding Malicious Software in Computer Security
In "Computer Security: Principles and Practice," the chapter on Malicious Software covers various types of malware such as viruses, adware, worms, and rootkits. It defines malware, Trojan horses, and other related terms like backdoors, keyloggers, and spyware. The chapter also discusses advanced thr
0 views • 49 slides
Understanding Malicious Software in Data Security
Malicious software, or malware, poses a threat to the confidentiality, integrity, and availability of data within systems. It can be parasitic or independent, with examples like viruses, worms, Trojan horses, and e-mail viruses. Understanding the different types of malware and their modes of operati
0 views • 5 slides
Exploring Bitcoin Scripts and Smart Contracts
Delve into the world of Bitcoin scripts, smart contracts, and their practical applications, including examples like escrow transactions and green addresses. Discover how Bitcoin offers clever solutions to complex conditions governing coin spending.
0 views • 15 slides
Understanding Web Security: Same-Origin Policy in Web Applications
In web development, the Same-Origin Policy plays a crucial role in ensuring the security of web applications by restricting how documents or scripts loaded from one origin can interact with resources from another origin. This policy helps prevent malicious attacks such as Cross-Origin Request Forger
0 views • 25 slides
Introduction to Shell Scripting in UNIX and Network Programming
Shell scripts in UNIX and network programming provide a powerful way to automate tasks, simplify recurring operations, and enhance system administration. They leverage variables, decision-making control, looping abilities, and function calls to streamline processes. With essential features like file
0 views • 32 slides
Buffer Overflow Attack and Vulnerable Programs
Understanding buffer overflow attacks and vulnerable programs, the consequences of such attacks, how to run malicious code, and the setup required for exploiting vulnerabilities in program memory stack layouts. Learn about creating malicious inputs (bad files), finding offsets, and addressing shellc
0 views • 36 slides
Exploring Java Sandbox Flexibility and Usage
The research delves into evaluating the flexibility and practical usage of the Java sandbox in dealing with Java applications. It highlights the importance of investigating how security tools are utilized, aiming to enhance security mechanisms and differentiate between malicious and benign code. The
0 views • 28 slides
Azure Monitoring Scripts Overview
Explore various Python scripts for monitoring Azure services including compute, storage, SQL, PaaS, and Active Directory. Each script is designed to check different aspects of Azure services using specific parameters and keys. Images depicting code snippets and sample outputs are provided for each s
0 views • 13 slides
Understanding Malware: Types, Risks, and Prevention
Malware, short for malicious software, is designed to disrupt, damage, or gain unauthorized access to computer systems. Malware includes viruses, worms, trojans, ransomware, adware, spyware, rootkits, keyloggers, and more. They can be spread through various means like malicious links, untrusted down
0 views • 15 slides
Understanding Malicious Software: Classification and Payload Actions
Malicious software, or malware, can be broadly classified based on how it spreads and the actions it performs once on a target system. This classification includes distinctions between viruses, worms, trojans, botnets, and blended attacks. The payload actions of malware can range from file corruptio
0 views • 44 slides
A Comprehensive Overview of Selenium IDE and Applitools Eyes Integration
The content discusses the seamless integration between Selenium IDE and Applitools Eyes for visual testing. It covers setting up visual tests, running test scripts, utilizing static and run-time options, simulating events, capturing images, viewing test progress, and more. The process involves creat
0 views • 4 slides
SmartSynth: Synthesizing Smartphone Automation Scripts from Natural Language
SmartSynth is a cutting-edge project by Vu Le, Sumit Gulwani, and Zhendong Su that aims to automate smartphone tasks by converting natural language instructions into executable scripts. The project involves programming in Java and C#, utilizing tools like Tasker and App Inventor to create automation
0 views • 31 slides
Introduction to Shell Arithmetic and Command.bc for Linguists
Today's lecture covers shell arithmetic, positional parameters for shell scripts, making shell scripts executable, and using command.bc for mathematical computations in the shell environment. Examples and demonstrations on shell arithmetic, utilizing the 'expr' command, and leveraging 'bc' command f
0 views • 21 slides
Tools and Techniques for Extracting Password Hashes and Credentials from Windows Systems
Explore various tools and scripts such as ESEDBXTRACT, GPPPFinder, and PowerShell scripts for extracting password hashes and credentials from Windows systems, including NTDS.dit and SYSTEM files, Group Policy Preferences, and more. Learn how to handle different Windows versions and access encrypted
0 views • 19 slides
Understanding Weak Points in Web Application Architecture
Information collected during the reconnaissance process can unveil critical aspects of a web application's architecture, including technologies used, API endpoints, functionality, domains, configurations, and authentication systems. Vulnerabilities in web applications often stem from poorly designed
4 views • 13 slides
Texas Instruments Latte Software Overview
Texas Instruments Latte software, commonly referred to as Latte, is a collection of Python scripts used to configure EVMs and create configuration scripts for application boards like FPGAs. It supports multiple devices, has Core and Library components, and is stored in a folder named "Latte" in the
0 views • 13 slides
Managing and Updating R2 Source Codes and Data Documentation
Set the home directory to prevent future directory changes before running real-time processes. Two versions of run_gdas scripts are provided along with instructions for setting up directories, updating scripts, and accessing necessary data files. Various resources and tools are mentioned, including
0 views • 62 slides
Understanding Cross-Site Scripting (XSS) Attacks and Prevention Measures
Cross-Site Scripting (XSS) is a prevalent security vulnerability in web applications that allows attackers to inject malicious scripts, potentially leading to unauthorized data access or manipulation. The content covers types of XSS attacks, finding vulnerable websites, testing exploits, and legal i
0 views • 10 slides
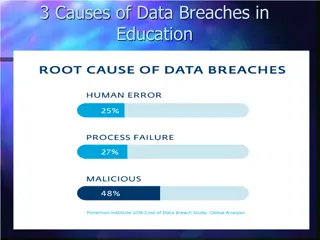
Understanding Data Breach Causes in Education
Data breaches in education are often caused by human errors, process failures, and malicious breaches. Human errors include leaving computers unlocked, sharing passwords, and carelessly discarding sensitive information. Process failures involve not keeping software up-to-date, lack of security polic
0 views • 15 slides
Smarter Betting, Bigger Wins_ The Power of Customizable CSGO Roulette Scripts
Explore customizable CSGO Roulette Scripts, csgo roulette, cs go roulette, csgo jackpot, and csgo script for smarter betting and bigger wins. Learn strategies, setup tips, and more!\n\nSource>>\/\/ \/csgo-roulette-script\n
0 views • 4 slides