Understanding Malicious Attacks, Threats, and Vulnerabilities in IT Security
Malicious attacks, threats, and vulnerabilities in IT systems pose significant risks and damages. This chapter explores the types of attacks, tools used, security breaches, and measures to protect against cyber threats. Learn how security professionals safeguard organizations from malicious attacks
0 views • 24 slides
Understanding Typosquatting in Language-Based Package Ecosystems
Typosquatting in language-based package ecosystems refers to the malicious practice of registering domain names that are similar to popular packages or libraries with the intention of tricking developers into downloading malware or compromised software. This threat vector is a serious issue as it ca
0 views • 23 slides
Understanding the Elements of Drama and Theater History
Drama, originating from the Greek verb "dran," involves acting and storytelling in front of an audience. Explore the key aspects, from the Globe Theater in London to dramatic structure, actors, and speech forms like dialogue and monologue. Learn about the crucial components such as playwrights, acto
4 views • 22 slides
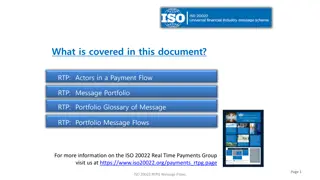
Real-Time Payments: Actors and Message Flows Overview
This document provides an overview of the actors involved in a payment flow and the message portfolio in Real-Time Payments (RTP). It includes details on various actors like Instructing agent, Forwarding agent, Ultimate Debtor, Reimbursement agents, and more. The provided message flows illustrate th
1 views • 12 slides
Efficient Malicious URL Detection with Bloom Filters
Google's Chrome team faces the challenge of detecting malicious URLs without heavy memory usage. Universal hashing and Bloom Filters are discussed as innovative solutions to address this issue efficiently and effectively, illustrating how K-independent hash functions can improve detection accuracy w
0 views • 19 slides
Exploring the Malicious Use of Artificial Intelligence and its Security Risks
Delve into the realm of artificial intelligence and uncover the potential risks associated with its malicious applications, including AI safety concerns and security vulnerabilities. Discover common threat factors and security domains that play a vital role in combating these challenges.
0 views • 30 slides
Financial Services Institutions Support Value Chain Actors
Financial services institutions play a vital role in supporting various actors within the value chain, including exporters, wholesalers, banks, processors, and non-bank financial institutions. This ecosystem also involves technical training, business support, local traders, private investors, specia
0 views • 30 slides
Understanding Typosquatting in Language-Based Package Ecosystems
Typosquatting in language-based package ecosystems involves malicious actors registering similar-sounding domain names to legitimate ones to deceive users into downloading malware or visiting malicious sites. This practice poses a significant threat as users may unknowingly install compromised packa
0 views • 23 slides
Understanding National Human Rights Protection Systems
Explore the essential elements of national human rights protection systems including actors, frameworks, and processes. Learn about the foundational role of the state, legal frameworks, institutions, and the involvement of non-state actors in upholding human rights. Reflect on the importance of dome
0 views • 35 slides
Understanding UML Use Cases for Software Requirements and Design
Use cases play a crucial role in defining software requirements and design. They outline interactions between actors and the system, describing functional requirements from the user's perspective. Identifying actors, their interactions, and goals are essential when writing a use case. This process h
0 views • 24 slides
Round-Efficient Byzantine Broadcast Under Strongly Adaptive and Majority Corruptions
This paper discusses a round-efficient Byzantine broadcast protocol that addresses strong adaptive adversaries and majority corruptions. The protocol involves unique and unbreakable peer signatures, committees for message verification, and time-locking mechanisms to prevent message tampering. By uti
1 views • 5 slides
Overview of US Foreign Policy Decision-Making Process
The US foreign policy decision-making process involves various actors and dynamics such as the President, Congress, interest groups, media, and public opinion. The Constitution outlines key provisions related to war powers, treaties, and appointments. The balance of power between the branches influe
2 views • 15 slides
Major Information Security Challenges Faced by Financial Services Firms
In today's digital age, large financial services firms encounter significant information security challenges such as exponential growth in malware threats, sophisticated cyber attacks, and frequent penetrations of information systems. The perfect storm of technological advancements and connectivity
0 views • 29 slides
Understanding Malicious Software and Its Impact on Computer Systems
Malicious software, commonly known as malware, poses a serious threat to computer systems by exploiting vulnerabilities. This content covers various terminologies, categories, and types of malware, including viruses, worms, rootkits, spyware, and adware. It also delves into how malware can cause dam
0 views • 16 slides
Understanding Control Hijacking Attacks and Defenses
Control hijacking attacks pose a significant threat by allowing malicious actors to manipulate data and control flow within a system. This article explores common attack methods like stack smashing and heap spraying, along with defenses such as fixing bugs, implementing platform defenses, and markin
1 views • 36 slides
Best Actors Headshot Photography in New Cross
Are you looking for the Best Actors Headshot Photography in New Cross? Then contact Tom Trevatt Photography. They take artistic photos of your face that help you make a meaningful connection when you need it most. Their services include headshot phot
0 views • 6 slides
Collaboration for Durable Solutions in Humanitarian Settings
This workshop addresses challenges and opportunities in achieving durable solutions for refugees and internally displaced persons. It emphasizes the importance of collaboration among various stakeholders, including humanitarian and development actors, to ensure long-term recovery and sustainable pea
0 views • 21 slides
Understanding Heap Overflow Attacks
A heap is a collection of variable-size memory chunks managed by the program. Heap overflow attacks occur when malicious actors corrupt heap memory, potentially allowing them to overwrite data and execute arbitrary code. This poses a significant security risk. The process involves manipulating heap
2 views • 19 slides
Engaging Key Actors in Climate Information Value Chain Through Radio Discussions
In this discussion, the importance of engaging key actors along the climate information value chain through radio discussions is emphasized. The symbiotic relationship between radio journalists and meteorological authorities is highlighted, as well as the key actors involved such as Government Agenc
0 views • 22 slides
The Vital Role of Religious Institutions in Supporting Immigrants
Religions and immigration are interlinked in modern societies, where religions play a significant role in providing services, defending rights, and supporting the social cohesion of immigrants. Mainstream religious institutions serve as key actors in offering assistance, advocating for migrant right
2 views • 14 slides
Analysis of Media Coverage on the Brussels Process (Sep-Dec 2015)
This analysis delves into the media monitoring of the Brussels Process from September to December 2015. It focuses on the monitoring objective, airtime distribution among TV actors, duration dedicated to the Brussels Agreement, number of reports per media outlet, and reporting statistics. The resear
0 views • 37 slides
Modelling Workflows and Data Domain in System Requirements and User Experience
In this lecture, the focus is on modelling workflows and data domain in the context of system requirements and user experience. The topics covered include recap of use cases, use case diagrams, descriptions, events initiated by stakeholders, defining elements for each use case, use case diagrams, an
0 views • 56 slides
Main Actors Society and Regime Characteristics Analysis
Analysis reveals a society characterized by passivity, apathy, and patron-client relationships, with emigration as a major form of social protest. The regime exhibits consolidating authoritarianism, convergence of business and political elites, and systemic corruption. Oligarchic dominance, small an
0 views • 6 slides
Understanding Cyberwarfare: Actors, Targets, Cases
Cyberwarfare involves actions by nation-states to penetrate others' computers or networks for causing damage. It extends classic warfare and is characterized by its speed, global nature, and comprehensive impact. State and non-state actors play significant roles, engaging in cooperation for various
0 views • 10 slides
Detecting Drive-By Attacks: Analysis of Malicious Javascript in Big Data Environments
Cybersecurity researcher Andrei Bozeanu delves into the complex world of polymorphic viruses, heuristic analysis, and the similarities between polymorphic viruses and malicious Javascript. Discover how these threats operate and evade detection, highlighting the importance of understanding malware be
0 views • 48 slides
Understanding Malware: Types, Symptoms, and Countermeasures
Malware is malicious software that can alter computer settings, behavior, files, services, ports, and speed. Sources of malware include insufficient security, honeypot websites, free downloads, torrents, pop-ups, emails, and infected media. Symptoms of malware include unusual computer behavior, slow
0 views • 9 slides
Understanding Use Cases and Actors in System Design
Explore the concept of use cases in system design, including user goals versus interactions, system boundaries, actors, and how they all come together in use case diagrams. Learn how use cases capture user-visible functions, achieve discrete goals, and represent the interactions between actors and t
0 views • 20 slides
Advances in Authenticated Garbling for Secure 2PC
The research discusses advancements in authenticated garbling for achieving constant-round malicious secure 2PC using garbled circuits. It emphasizes the utilization of correlated randomness setup and efficient LPN-style assumptions to enhance communication efficiency significantly. Various techniqu
0 views • 30 slides
Exploring Microsoft Orleans: A .NET Developer's Guide
Dive into the world of virtual actors and distributed system design with Microsoft Orleans, a powerful framework for building scalable and resilient applications in .NET. Learn about key concepts like grains, silos, and virtual actors, and discover how Orleans simplifies the development of complex d
0 views • 37 slides
Comprehensive Lesson on Distribution Planning and Setup
This detailed lesson plan covers essential aspects of distribution systems, planning, setups, layouts, and actors involved in the distribution cycle. Participants will learn about distribution types, considerations, and evaluation criteria to ensure successful distribution operations. The session in
0 views • 22 slides
Importance of Security in Web Development
Our perception of security has evolved to acknowledge the presence of malicious actors and potential vulnerabilities in web applications. To write secure code, developers must assume the worst-case scenario and adopt a security mindset that trusts no one. Attackers have various goals, such as steali
0 views • 18 slides
Understanding Malicious Software in Computer Security
In "Computer Security: Principles and Practice," the chapter on Malicious Software covers various types of malware such as viruses, adware, worms, and rootkits. It defines malware, Trojan horses, and other related terms like backdoors, keyloggers, and spyware. The chapter also discusses advanced thr
0 views • 49 slides
Understanding Malicious Software in Data Security
Malicious software, or malware, poses a threat to the confidentiality, integrity, and availability of data within systems. It can be parasitic or independent, with examples like viruses, worms, Trojan horses, and e-mail viruses. Understanding the different types of malware and their modes of operati
0 views • 5 slides
Understanding Botnets: Threats, Detection, and Control Techniques
Explore the world of botnets, learn about the creation, propagation, and command & control techniques used by malicious actors. Discover the security threats posed by botnets and methods to detect and mitigate them effectively. Images and detailed explanations provide insights into handling bot-rela
0 views • 31 slides
Impact of Non-State Actors on Civic Space: Interim Findings & Recommendations
Examining the impact of non-state actors on civic space in Bangladesh, Palestine, and Zimbabwe reveals the drastic effects of pro-government militias, GONGOs, and state-owned media restrictions on NGO activities. Recommendations include resolving conflicts, flexible long-term support, addressing act
0 views • 5 slides
Buffer Overflow Attack and Vulnerable Programs
Understanding buffer overflow attacks and vulnerable programs, the consequences of such attacks, how to run malicious code, and the setup required for exploiting vulnerabilities in program memory stack layouts. Learn about creating malicious inputs (bad files), finding offsets, and addressing shellc
0 views • 36 slides
Exploring Java Sandbox Flexibility and Usage
The research delves into evaluating the flexibility and practical usage of the Java sandbox in dealing with Java applications. It highlights the importance of investigating how security tools are utilized, aiming to enhance security mechanisms and differentiate between malicious and benign code. The
0 views • 28 slides
Understanding Malware: Types, Risks, and Prevention
Malware, short for malicious software, is designed to disrupt, damage, or gain unauthorized access to computer systems. Malware includes viruses, worms, trojans, ransomware, adware, spyware, rootkits, keyloggers, and more. They can be spread through various means like malicious links, untrusted down
0 views • 15 slides
Understanding Malicious Software: Classification and Payload Actions
Malicious software, or malware, can be broadly classified based on how it spreads and the actions it performs once on a target system. This classification includes distinctions between viruses, worms, trojans, botnets, and blended attacks. The payload actions of malware can range from file corruptio
0 views • 44 slides
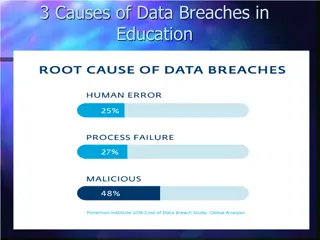
Understanding Data Breach Causes in Education
Data breaches in education are often caused by human errors, process failures, and malicious breaches. Human errors include leaving computers unlocked, sharing passwords, and carelessly discarding sensitive information. Process failures involve not keeping software up-to-date, lack of security polic
0 views • 15 slides