מנעולן בקרית מוצקין
The scourge of home and business burglaries is nothing new and surprising.\nAt every opportunity, burglars look for new and creative ways to overcome the security and locking mechanisms of homes and businesses throughout Nahariya, one of the most beautiful coastal cities in the country. In addition,
7 views • 3 slides
Buy Godrej 50mm Brass Finish Padlock with 3 Keys (Gold, Pack of 1)
Godrej Locks Brushed Finish 50mm Padlock Hardened Shackle Gold (Free Shipping UK)\n\nAbout this item\n\nSolid brass body provides sturdiness and MADE IN INDIA\n\nHardened steel shackle provides resistance to hacksaw cutting and crowbar attacks,\n\nElectroplated shackle ensures long life,\n\nDouble L
0 views • 3 slides
Classroom Security for Existing Educational Facilities: Ensuring Safety and Compliance
Explore the vital aspects of securing schools for life safety, focusing on classroom security within educational facilities. Learn about the importance of proper locking systems, acceptable types, NFPA 101 life safety code requirements, and ensuring unobstructed egress for occupants. Discover key re
0 views • 20 slides
Overview of Distributed Systems: Characteristics, Classification, Computation, Communication, and Fault Models
Characterizing Distributed Systems: Multiple autonomous computers with CPUs, memory, storage, and I/O paths, interconnected geographically, shared state, global invariants. Classifying Distributed Systems: Based on synchrony, communication medium, fault models like crash and Byzantine failures. Comp
9 views • 126 slides
Understanding Information Systems in Organizational Management
Management in organizations is divided into three levels: operational, tactical, and strategic. Each level requires different information systems to support various activities. Operational systems focus on routine transactions and control processes, while middle-level systems aid in semi-structured
9 views • 39 slides
Understanding Device Settings and Strong Passwords for Digital Citizenship
This lesson focuses on understanding device settings and the importance of creating strong passwords for digital citizenship. It covers topics such as changing backgrounds, locking screens, creating strong passwords, common password mistakes to avoid, and tips for password safety. The lesson also in
1 views • 11 slides
Understanding Transaction Management in DBMS
In this lecture, Mohammad Hammoud covers the key aspects of transaction management in database management systems (DBMS). Topics include locking protocols, anomaly avoidance, lock managers, and two-phase locking. The session delves into the rules, data structures, and processes involved in maintaini
1 views • 56 slides
Automotive Grade 10 Joining Methods: Locking Devices Overview
Automotive Grade 10 explores joining methods using locking devices to prevent nuts from loosening due to movement and vibration. Friction-locking devices include lock nuts, stiff nuts, and special washers. Positive-locking devices tighten nuts securely with slotted nuts, crowned nuts, tab washers, a
1 views • 7 slides
Comprehensive Guide to Acute Knee Examination in Urgent Care
This detailed guide covers the essential components of the acute knee exam conducted in an urgent care setting by Dr. Gregory Jones, including chief complaints, anatomy, examination techniques, ligament assessments, practical aspects, and more. The examination process involves assessing functional l
1 views • 27 slides
Introduction to Embedded Systems Design
Embedded Systems Design, Chapter 1 provides an insightful overview of embedded systems, distinguishing them from general-purpose computers. The chapter delves into the characteristics of embedded systems, their design considerations, and the various types of embedded computers such as general-purpos
1 views • 7 slides
Corrugated packaging box with flat pack and inner locking in style
Corrugated packaging boxes with flat packs and inner locking styles are popular for their durability, cost-effectiveness, and ease of assembly. They are widely used for shipping and storing products due to their protective qualities and customizable
1 views • 2 slides
Understanding Acute Knee Injuries: Meniscal Tears and Ligament Injuries
Acute knee injuries, such as meniscal tears and ligament injuries, are commonly caused by trauma or twisting motions. Meniscal tears can lead to pain, swelling, and locking of the knee joint, especially in young active individuals. Understanding the anatomy of the knee joint and meniscus, along with
0 views • 56 slides
Fainting Safety: Prevention and Recognition Strategies
Fainting, medically known as syncope, is a sudden loss of consciousness that can be caused by various factors like dehydration, heat, anxiety, or low blood pressure. This presentation debunks the myth of knee-locking causing fainting and focuses on prevention strategies such as proper hydration, nut
1 views • 14 slides
Self Lock in style Shoe packaging boxes
Creating self-locking style shoe packaging boxes is an excellent way to ensure secure and attractive packaging. Here's a step-by-step guide to designing and making these boxes using resources from a paper gallery.
1 views • 3 slides
Understanding Lock-Based Protocols in Database Concurrency Control
Lock-based protocols are essential mechanisms for controlling concurrent access to data items in a database system. This involves granting locks in exclusive (X) or shared (S) modes to ensure data integrity and prevent conflicts. Lock compatibility matrices and locking protocols play a crucial role
2 views • 69 slides
Efficient Cataloging and Record Management in Alma
Streamline your cataloging process in Alma by utilizing the Institution Zone (IZ) to link your inventory to the Network Zone (NZ) record. Remember to save and release records to avoid locking them and ensure smooth collaboration. Access training resources for detailed guidance.
0 views • 17 slides
Round-Efficient Byzantine Broadcast Under Strongly Adaptive and Majority Corruptions
This paper discusses a round-efficient Byzantine broadcast protocol that addresses strong adaptive adversaries and majority corruptions. The protocol involves unique and unbreakable peer signatures, committees for message verification, and time-locking mechanisms to prevent message tampering. By uti
1 views • 5 slides
Computer Lab Safety Training Guidelines
Ensure safe usage of computer labs in the College of Science, Technology, Engineering, and Mathematics with guidelines on Onity lock operation, loss of privilege/access, responsibility, emergency procedures, and electrical safety. The instructions cover aspects like door locking procedures, unauthor
0 views • 8 slides
YHI Account Locking: Reasons and Resolutions
Your YHI account could get locked due to multiple failed login attempts, inactivity, or accumulation of browsing data. Learn the common causes of locked accounts and their resolutions, including steps to reset your password or username, reactivate a dormant account, and clear browsing data. Contact
0 views • 7 slides
Compute and Storage Overview at JLab Facility
Compute nodes at JLab facility run CentOS Linux for data processing and simulations with access to various software libraries. File systems provide spaces like /group for group software, /home for user directories, and Cache for write-through caching. Additionally, there are 450TB of cache space on
0 views • 11 slides
Information Systems in Organizations: Overview and Implementation
Information systems play a crucial role in organizations, encompassing transaction processing systems, functional area information systems, and enterprise resource planning systems. This content delves into the purpose of transaction processing systems, the support provided by information systems ac
0 views • 30 slides
Carnegie Mellon Multithreaded Synchronization Recitation
Explore Carnegie Mellon's recitation on multithreaded synchronization, debugging tools, shared memory synchronization, critical sections, and locking. Dive into the Echo Server Sequential Handling code examples, finding weaknesses using telnet, and advanced debugging techniques with curl and binary
0 views • 34 slides
Challenges and Solutions in Win32 Multithreading
Tackling complex problems in Win32 multithreading involves dealing with locking issues, such as insufficient lock protection and lock order violation. Central to this are the essential locking disciplines that are difficult to enforce in practice. Tools like EspC Concurrency Toolset help analyze and
0 views • 16 slides
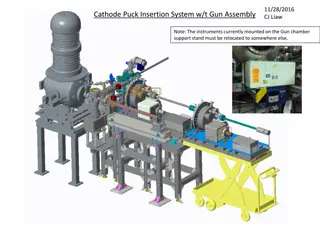
Development Status Update for Cathode Puck Insertion System
Update on the development status of the Cathode Puck Insertion System, including relocation of instruments, preparation table procurement, design and fabrication status of various components, stationary section details, welding requirements for manipulator and puck locking mechanism, mobile cart set
0 views • 14 slides
Innovative Approach to Magnetron Phase Locking for RF Applications
This document explores a novel method for phase locking magnetrons, essential for various high-power RF applications. Traditional methods involve injecting RF signals through additional components, leading to complexity and inefficiency. The proposed method utilizes varactor diodes and feedback loop
0 views • 16 slides
Understanding the Statistics Model in VPP for Enhanced Networking Performance
Dive into the world of VPP with a focus on the statistics consumption model, shared memory structures, and optimistic locking techniques. Learn how to leverage these concepts for optimal network performance at FOSDEM 2022.
0 views • 15 slides
Smart IoT Lock for Convenient Home Access
A detailed exploration of an Internet of Things (IoT) solution that revolutionizes home security by introducing a smart lock system. By implementing an IoT lock on your front door, you can effortlessly unlock the door as your phone comes in proximity and it locks automatically when you move out of r
0 views • 8 slides
Software Quality and Source Code Management Best Practices
Effective source code management is crucial for software quality assurance. This involves locking down code, baselining milestones, managing code variants, and ensuring traceability. Software Configuration Management (SCM) is key, encompassing configuration items and core concepts like creating base
0 views • 34 slides
Best Commercial Locksmith in Windsor
If you want the Best Commercial Locksmith in Windsor, visit NewGen Locksmith. They are fully licensed, insured, and highly skilled individuals possessing profound knowledge of residential and commercial locking systems. Whether the locks are contempo
1 views • 6 slides
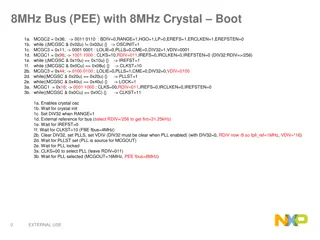
Configuring 8MHz Bus with 8MHz Crystal for PEE Mode
Configuring a system with an 8MHz bus using an 8MHz crystal for PEE (PLL Engaged External) mode involves a series of steps such as setting register values, waiting for specific conditions to be met, selecting clock sources, and ensuring PLL stability. The detailed configuration process ensures prope
0 views • 4 slides
Expert Key Cutting Precision for Your Safety Needs (1)
Commercial properties often have more complex locking systems, including master key systems. These keys require a high level of expertise to ensure they operate within these advanced systems without fail. Professional key cutters can handle these nee
0 views • 8 slides
Clock Synchronization Distribution For Data Taking Systems
The content details the clock synchronization distribution system for data taking systems requiring specific clock frequencies for various subsystems to ensure synchronous data processing. It covers the setup, external clock relationships, and generation specifics involving different clock frequenci
0 views • 10 slides
Performance Analysis of Synchronization Methods in Concurrent Data Structures
Explore the impact of synchronization methods on the performance and behavior of concurrent data structures in multithreaded applications. The study involves developing and implementing concurrent data structures, analyzing coarse-grain locking, fine-grain locking, lock-free mechanisms, and assessin
0 views • 25 slides
Understanding Database Transactions and Concurrency Control
This content delves into the world of database transactions, exploring concepts such as ACID properties, locking schedulers, anomalies in scheduling, and implementing transaction control mechanisms like Two Phase Locking. It covers the importance of maintaining atomicity, consistency, isolation, and
0 views • 36 slides
Comprehensive Guide to Reamed Intramedullary Nailing Techniques
This educational material covers the principles of intramedullary nailing, including indications and contraindications, patient positioning, reduction techniques, surgical approach, and the procedure using the ETN. It delves into technique details, positioning, approach/entry points, reaming, nail i
0 views • 5 slides
Comprehensive Examination Questions on Data Management Systems and Security Protocols
This content covers a range of topics related to data management systems, including two-phase locking and two-phase commit protocols, Bayou system with vector clocks and causality, digital signatures and certificates in protocols, and authentication protocols. Questions include scenarios and concept
0 views • 6 slides
Understanding Embedded Systems and Cyber-Physical Systems
Embedded systems are specialized computer systems embedded within larger systems, such as control systems and car controllers. This lecture covers real-time aspects, applications of Cyber-Physical Systems (CPS), and examples like the Boeing 777/Airbus A380 cockpit. It discusses the design process of
0 views • 22 slides
Understanding Locking and Synchronization in Multithreaded Environments
Exploring the concepts of locking and synchronization in the context of shared resources in multithreaded environments. Covering topics such as thread cooperation, coordination of access to shared variables, and the importance of synchronization mechanisms for controlling execution interleaving. Exa
0 views • 41 slides
Best Locking wheel nut Removal in Hafod
If you\u2019re looking for a Locking wheel nut Removal in Hafod, contact Fastest Fit Tyres LTD. Their skilled mobile tyre fitters are available 24 hours a day, ensuring you're never stranded due to a flat or damaged tyre. They specialise in puncture
0 views • 6 slides
Understanding Semantics and Locking Specifications in Concurrency
Exploring the importance of semantics and locking specifications in concurrent programming, this content delves into issues such as data races, unsafe code, and solutions like locking discipline to manage shared data effectively and prevent corruption.
0 views • 22 slides