Efficient Key Recovery Attack on SIDH
Efficient key recovery attack on Supersingular Isogeny Diffie-Hellman (SIDH) protocol. It explores the vulnerability of the protocol and proposes a concrete solution. The attack leverages auxiliary points to solve the isogeny problem and reveals instances of the common secret key.
5 views • 22 slides
Fernandes Thriving in United's Resurgent Attack^J Euro 2024 Success
Fernandes Thriving in United's Resurgent Attack, Euro 2024 Success\n\nhttps:\/\/blog.worldwideticketsandhospitality.com\/2024\/02\/15\/fernandes-thriving-in-uniteds-resurgent-attack-euro-2024-success\/\n\nUEFA Euro 2024 fans from all over the world can book European Championship 2024 Tickets on our
2 views • 5 slides
Basic Principles of MRI Imaging
MRI, or Magnetic Resonance Imaging, is a high-tech diagnostic imaging tool that uses magnetic fields, specific radio frequencies, and computer systems to produce cross-sectional images of the body. The components of an MRI system include the main magnet, gradient coils, radiofrequency coils, and the
2 views • 49 slides
Do Input Gradients Highlight Discriminative Features?
Instance-specific explanations of model predictions through input gradients are explored in this study. The key contributions include a novel evaluation framework, DiffROAR, to assess the impact of input gradient magnitudes on predictions. The study challenges Assumption (A) and delves into feature
0 views • 32 slides
Bayesian Estimation and Hypothesis Testing in Statistics for Engineers
In this course on Bayesian Estimation and Hypothesis Testing for Engineers, various concepts such as point estimation, conditional expectation, Maximum a posteriori estimator, hypothesis testing, and error analysis are covered. Topics include turning conditional PDF/PMF estimates into one number, es
1 views • 16 slides
Advanced Reinforcement Learning for Autonomous Robots
Cutting-edge research in the field of reinforcement learning for autonomous robots, focusing on Proximal Policy Optimization Algorithms, motivation for autonomous learning, scalability challenges, and policy gradient methods. The discussion delves into Markov Decision Processes, Actor-Critic Algorit
6 views • 26 slides
Estimation Clipboard 68 and New Esti-Mysteries Resources
Dive into Estimation Clipboard 68 and explore new Esti-Mysteries and Number Sense resources for everyday use in the classroom. Discover engaging activities and tools designed by Steve Wyborney to enhance mathematical learning experiences. Watch the instructional video, solve the bear estimation chal
0 views • 4 slides
Understanding Artificial Neural Networks From Scratch
Learn how to build artificial neural networks from scratch, focusing on multi-level feedforward networks like multi-level perceptrons. Discover how neural networks function, including training large networks in parallel and distributed systems, and grasp concepts such as learning non-linear function
1 views • 33 slides
Forces Affecting Air Movement: Pressure Gradient Force and Coriolis Force
The pressure gradient force (PGF) causes air to move from high pressure to low pressure, with characteristics including direction from high to low, perpendicular to isobars, and strength proportional to isobar spacing. The Coriolis force influences wind direction due to the Earth's rotation, making
0 views • 20 slides
Project Cost Estimation: Methods and Factors
Project cost estimation involves valuing all monetary aspects necessary for planning, implementing, and monitoring a project. This includes various entrants such as preliminary investigation costs, design fees, construction expenses, and more. The purpose of cost estimation is to determine work volu
1 views • 44 slides
Using the Estimation Clipboard in the Classroom
Explore tips for effectively using the Estimation Clipboard in the classroom to engage students in mathematical reasoning and estimation activities. The process involves inviting students to share estimates, encouraging written estimates and discussions, and revealing answers to promote engagement a
0 views • 5 slides
Understanding Slope, Gradient, and Intervisibility in Geography
Explore the concepts of slope, gradient, and intervisibility in geography through detailed descriptions and visual representations. Learn about positive, negative, zero, and undefined slopes, the calculation of gradient, and the significance of understanding these aspects in various engineering and
0 views • 12 slides
A Comprehensive Guide to Gradients
Gradients are versatile tools in design, allowing shapes to transition smoothly between colors. Learn about gradient types, preset options, creating your own metallic gradients, and applying gradients effectively in this detailed guide. Explore linear and radial gradient directions, understand gradi
0 views • 7 slides
3D Human Pose Estimation Using HG-RCNN and Weak-Perspective Projection
This project focuses on multi-person 3D human pose estimation from monocular images using advanced techniques like HG-RCNN for 2D heatmaps estimation and a shallow 3D pose module for lifting keypoints to 3D space. The approach leverages weak-perspective projection assumptions for global pose approxi
0 views • 8 slides
Dealing with Range Anxiety in Mean Estimation
Dealing with range anxiety in mean estimation involves exploring methods to improve accuracy when estimating the mean value of a random variable based on sampled data. Various techniques such as quantile truncation, quantile estimation, and reducing dynamic range are discussed. The goal is to reduce
1 views • 12 slides
Mini-Batch Gradient Descent in Neural Networks
In this lecture by Geoffrey Hinton, Nitish Srivastava, and Kevin Swersky, an overview of mini-batch gradient descent is provided. The discussion includes the error surfaces for linear neurons, convergence speed in quadratic bowls, challenges with learning rates, comparison with stochastic gradient d
0 views • 31 slides
First Nations Attack on Fort Michilimackinac 1763: Causes, Tribes, and Aftermath
The First Nations' attack on Fort Michilimackinac in 1763 was triggered by British actions that disrupted their way of life. The Ojibwe, Odawa, Potawatomi, Ottawas, and Hurons were involved in the attack, led by Chief Pontiac. Following the attack, the British did not rebuild the fort but establishe
1 views • 7 slides
Efficient Gradient Boosting with LightGBM
Gradient Boosting Decision Tree (GBDT) is a powerful machine learning algorithm known for its efficiency and accuracy. However, handling big data poses challenges due to time-consuming computations. LightGBM introduces optimizations like Gradient-based One-Side Sampling (GOSS) and Exclusive Feature
0 views • 13 slides
Optimization Methods: Understanding Gradient Descent and Second Order Techniques
This content delves into the concepts of gradient descent and second-order methods in optimization. Gradient descent is a first-order method utilizing the first-order Taylor expansion, while second-order methods consider the first three terms of the multivariate Taylor series. Second-order methods l
0 views • 44 slides
Enhancing Cybersecurity for Windows Infrastructure: A Practical Guide
In this informative session, Vladimir Stefanovi, a seasoned System Engineer and Technical Trainer, sheds light on the vulnerabilities of Windows servers and provides valuable insights on how to protect and fortify your infrastructure against cyber threats. From traditional to modern attack vectors,
0 views • 21 slides
Estimation Puzzle: How Many Blue Rocks in the Vase?
A fun estimation challenge where clues are provided to narrow down the possibilities of the number of blue rocks in a vase. By using critical thinking and estimation skills, participants deduce that there are 65 blue rocks in the vase. Test your estimation abilities with engaging visual clues and de
0 views • 6 slides
Understanding Hessian-Free Optimization in Neural Networks
A detailed exploration of Hessian-Free (HF) optimization method in neural networks, delving into concepts such as error reduction, gradient-to-curvature ratio, Newton's method, curvature matrices, and strategies for avoiding inverting large matrices. The content emphasizes the importance of directio
0 views • 31 slides
Duane Wolf Attack Simulation Study: Insights for Law Enforcement Officers
Duane Wolf conducted an attack simulation study to test the speed at which an un-handcuffed suspect sitting on a curb can launch an attack on officers. The study involved volunteers in different leg positions to mimic real-life scenarios. Findings emphasized the importance of officers staying alert
0 views • 9 slides
Dual-Pol Observations in NW Environment OLYMPEX Planning Meeting
The OLYMPEX planning meeting in Seattle on January 22, 2015 discussed the contribution of polarimetric S-band radar in rain estimation systems targeted by OLYMPEX. The use of specific differential phase (Kdp) helps in minimizing assumptions about drop size distribution, convective/stratiform distinc
1 views • 15 slides
Fermi Problems and Estimation Techniques in Science
Understand Enrico Fermi's approach to problem-solving through estimation in science as demonstrated by Fermi Problems. These problems involve making educated guesses to reach approximate answers, fostering creativity, critical thinking, and estimation skills. Explore the application of Fermi Problem
0 views • 23 slides
Understanding Blending Attacks on Mixes by Meng Tang
Explore the effectiveness of blending attacks on mixes, including steps of a blending attack, attack models, factors affecting the attack, defense strategies, and insights from the attacker's viewpoint.
0 views • 25 slides
Foundations of Parameter Estimation and Decision Theory in Machine Learning
Explore the foundations of parameter estimation and decision theory in machine learning through topics such as frequentist estimation, properties of estimators, Bayesian parameter estimation, and maximum likelihood estimator. Understand concepts like consistency, bias-variance trade-off, and the Bay
0 views • 15 slides
Software Development Cost Estimation Best Practices
Explore key principles and techniques for accurate cost estimation in software development projects. Discover the importance of the 5WHH principle, management spectrum, critical practices, resource estimation, estimation options, and decomposition techniques for improved project planning. Learn abou
0 views • 40 slides
Understanding Estimation and Statistical Inference in Data Analysis
Statistical inference involves acquiring information and drawing conclusions about populations from samples using estimation and hypothesis testing. Estimation determines population parameter values based on sample statistics, utilizing point and interval estimators. Interval estimates, known as con
0 views • 41 slides
Advances in Tropical Cyclone Radar Rainfall Estimation
Reviewing past methods and introducing new tools for radar rainfall estimation in tropical cyclones. Discusses advancements in Dual Polarization rainfall estimation and NSSL's National Mosaic & Multi-Sensor Quantitative Precipitation Estimation. Includes insights on reflectivity-to-rainfall relation
0 views • 28 slides
Volleyball Referee Hand Signals for Common Violations
Learn the essential hand signals used by volleyball referees to indicate common violations during a game. Signals include illegal alignment, line violation, illegal hit, delay of service, over the net, net foul, legal back row attack, illegal attack of serve back row attack, and illegal block/screen
0 views • 26 slides
Introduction to Statistical Estimation in Machine Learning
Explore the fundamental concepts of statistical estimation in machine learning, including Maximum Likelihood Estimation (MLE), Maximum A Posteriori (MAP), and Bayesian estimation. Learn about key topics such as probabilities, interpreting probabilities from different perspectives, marginal distribut
0 views • 23 slides
Mechanism of Br2 Attack on Trans-Cinnamic Acid
The detailed anti-attack and syn-attack mechanisms of Br2 on trans-cinnamic acid are presented, illustrating the intricate steps involved in preventing or facilitating the attack of bromine on the compound. The process involves initial attack, bridgehead formation, bond rupture, bond stabilization,
0 views • 11 slides
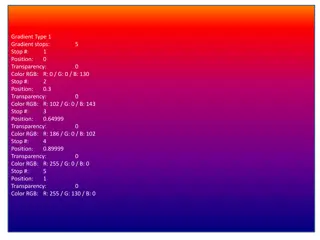
Gradient Types and Color Patterns
The content describes various gradient types and color patterns using RGB values and positioning to create visually appealing transitions. Each gradient type showcases a unique set of color stops and positions. The provided information includes detailed descriptions and links to visual representatio
0 views • 24 slides
Understanding Two-Stage Local Linear Least Squares Estimation
This presentation by Prof. Dr. Jos LT Blank delves into the application of two-stage local linear least squares estimation in Dutch secondary education. It discusses the pros and cons of stochastic frontier analysis (SFA) and data envelopment analysis (DEA), recent developments in local estimation t
0 views • 24 slides
Advanced Gaze Estimation Techniques: A Comprehensive Overview
Explore advanced gaze estimation techniques such as Cross-Ratio based trackers, Geometric Models of the Eye, Model-based Gaze Estimation, and more. Learn about their pros and cons, from accurate 3D gaze direction to head pose invariance. Discover the significance of Glint, Pupil, Iris, Sclera, and C
0 views • 40 slides
Unsteady Hydromagnetic Couette Flow with Oscillating Pressure Gradient
The study investigates unsteady Couette flow under an oscillating pressure gradient and uniform suction and injection, utilizing the Galerkin finite element method. The research focuses on the effect of suction, Hartmann number, Reynolds number, amplitude of pressure gradient, and frequency of oscil
0 views • 17 slides
Understanding the Black-Scholes Formula and Volatility Estimation
The Black-Scholes formula, developed by Dr. Fernando Diz, is a widely used model for pricing options. This formula calculates the theoretical price of an option based on various inputs, with volatility being a key factor. Volatility estimation can be done through historical or implied methods, each
0 views • 18 slides
Social Engineering Attack Framework (SEAF) - Understanding the Process
Social Engineering Attack Framework (SEAF) provides a structured approach to executing social engineering attacks. It defines the attack framework, assists in planning and execution, and helps in verifying the success of the attack. The process involves identifying the attack goal, assessing potenti
0 views • 16 slides
Essential Tips for Training Neural Networks from Scratch
Neural network training involves key considerations like optimization for finding optimal parameters and generalization for testing data. Initialization, learning rate selection, and gradient descent techniques play crucial roles in achieving efficient training. Understanding the nuances of stochast
0 views • 23 slides