Proposed Approach for MAC Address Assignment in IEEE 802.11
IEEE 802.1CQ is working on a mechanism to assign local MAC address blocks to end nodes specifically related to IEEE 802.11 standards. The current draft lacks a pre-association mechanism for IEEE 802.11 stations to obtain a local MAC address before association. The proposed remedy suggests specifying
6 views • 7 slides
Guiding Lights_ The Importance of Home Address Signs.docx
In the tapestry of neighborhood home address signs truly stand like a beacon of identity safety guiding you and other delivery drivers to the destinations. But the importance of the humble Home Address sign is often ignored. In this guide you can explore the importance of home address signs.\n
1 views • 2 slides
Implementing Address Spaces: Base + Limit Registers
Address spaces, base + limit registers, and contiguous allocation are essential concepts in operating systems. Real mode memory addresses lack isolation between processes and pose limitations on multitasking. Virtual memory introduces virtual address spaces, requiring translation to physical address
3 views • 11 slides
Understanding VSAM Logical Record Access Methods
VSAM utilizes three primary methods to find logical records - Relative Byte Address, Relative Record Number, and Key field. Relative Byte Address assigns a unique address to each record based on sequential ordering. Relative Record Number is used in RRDS datasets to access records by a numbered sequ
3 views • 35 slides
Understanding IPv4 Addresses and Classful Addressing in Computer Networks
Explore the basics of IPv4 addresses, address space, hierarchy in addressing, and classful addressing in computer networks. Learn about the unique 32-bit structure of IPv4 addresses, address space calculation, notation methods, and the hierarchical nature of network addressing. Dive into the concept
2 views • 14 slides
IEEE 802.11-20/0054r1 MLD MAC Address and WM Address
In the document IEEE 802.11-20/0054r1, the focus is on Multi-Link Framework for MLD address identification and differentiation. It explains the usage of MLD MAC address and STA WM medium address in wireless setups. The document also addresses the need for identifying different MLDs using MAC address
0 views • 16 slides
Creating a Shared Address Book in VSPS
Learn how to create a shared address book in VSPS by setting up a practice managed by the Practice Manager, who can add or remove users to access the address book. Follow step-by-step instructions to invite users and manage access to the shared address book efficiently.
0 views • 24 slides
Carnegie Mellon Secure Systems Verification Research
Carnegie Mellon University's research focuses on secure hypervisor systems, address space separation, and verification tasks to ensure security properties in the presence of adversaries. Challenges include scalability in model checking due to complex data structures in address translation. The aim i
3 views • 20 slides
Algorithms and Structured Programming - Introduction to CSCI 161
This document covers various topics related to algorithms, structured programming, comments in source code, and examples using println statements in Java programming. It provides insights into using escape sequences, generating specific outputs, and the importance of comments for code documentation
0 views • 21 slides
Understanding Segmentation in Operating Systems
Segmentation in operating systems involves dividing the address space into logical segments like code, stack, and heap, each with its base and bounds in physical memory. Address translation ensures proper mapping of virtual addresses to physical memory locations, preventing segmentation faults. Lear
0 views • 15 slides
Internet Number Resource Report June 2013
This report provides detailed information on the status of Internet number resources as of June 2013, including IPv4 address space allocations, available IPv4 /8s in each Regional Internet Registry (RIR), IPv4 address space issued by RIRs to customers, ASN assignments, 4-byte ASN assignments, and IP
0 views • 18 slides
Fundamentals of Computer Networks
Explore the essentials of computer networks, covering topics such as DHCP, NAT, IPv6, server operations, and IP address allocation. Understand how DHCP servers control IP address pools and provide network configurations to clients. Learn about address leases for dynamic allocation and how DHCP clien
0 views • 35 slides
Summary of MAC Address Policy Contribution to IEEE 802.11
This document outlines the contribution of MAC address policy to IEEE 802.11, focusing on defining ANQP and Beacon elements to convey information about addressing types supported by the network. It details how specific bits in the ANQP element represent support for various MAC address types includin
0 views • 5 slides
Tragic Tale of War and Grass in Carl Sandburg's Poem
Carl Sandburg's poem "Grass" reflects on the gruesome aftermath of wars like Austerlitz, Waterloo, Gettysburg, Ypres, and Verdun, with the grass personified as a silent witness covering the piled bodies. The poem hauntingly portrays the destruction and loss during the war, emphasizing the cyclical n
0 views • 4 slides
Major Battles and End of the Civil War Timeline
The timeline covers significant events during the American Civil War, including the Battle of Shiloh, Second Battle of Bull Run, Battle of Antietam, Gettysburg, and the Gettysburg Address. The battles were consequential, resulting in high casualties and strategic shifts in the war. The Gettysburg Ad
0 views • 17 slides
The Civil War: Causes, Battles, and Impact
The Civil War started in 1861 due to the issue of slavery in the United States. It lasted from 1861 to 1865 and resulted in significant bloodshed, with key battles like Gettysburg and Antietam. Despite the North's advantages in population and resources, the Confederates put up a stubborn resistance.
0 views • 16 slides
The Siege of Petersburg and Richmond in the Civil War
Confederate forces faced major defeats at Gettysburg and Vicksburg, leading to a turning tide in favor of the Union. Ulysses S. Grant's Overland Campaign weakened Confederate forces, focusing on Petersburg as a critical supply line to Richmond. Despite initial failures, Union forces gradually extend
0 views • 9 slides
The Civil War: Key Events and Battles Overview
Explore the causes, events, and significant battles of the Civil War, from the disagreements over tariffs, slavery, sectionalism, and states' rights to pivotal moments like Lincoln's presidency, secession, the Emancipation Proclamation, and decisive battles at Gettysburg and Vicksburg. Witness the s
0 views • 9 slides
Understanding User-Level Memory Management in Operating Systems
Exploring user-level memory concepts such as virtual memory areas, address spaces, paging, forking, and copy-on-write in the context of Linux operating systems. Learn about virtual/physical memory relationships, virtual address translation, process address spaces, and the use of techniques like copy
0 views • 18 slides
Understanding Address Translation in Computer Systems
Explore the concept of address translation in computer systems, covering topics such as converting virtual addresses to physical addresses, different translation methods, goals of address translation, bonus features, and a preview of MIPS address translation. Learn about the benefits and limitations
0 views • 60 slides
Transforming Adolescent Health Outcomes: A Holistic Approach
Dr. Hayley Lofink Love, PhD, advocates for rethinking healthcare to address adolescent health challenges by leveraging school-based health centers. The current system is failing to meet adolescents' needs due to fragmented care and incomplete services. By providing convenient, culturally appropriate
0 views • 28 slides
Locally-Unique Address Assignment Protocols in IEEE 802 Networks
This content discusses the Local MAC Address Protocol for locally-unique assignment of 48-bit and 64-bit addresses in IEEE 802 networks. It specifies protocols, procedures, and management objects for address assignment in a structured manner. The document also covers peer-to-peer claiming, server mo
0 views • 11 slides
Local MAC Address Assignment Protocol (LAAP) and 802.1CQ
The Local MAC Address Assignment Protocol (LAAP) in conjunction with 802.1CQ specifies protocols and procedures for locally unique assignment of MAC addresses in IEEE 802 networks. LAAP operates in two modes - Server Mode and Peer-to-Peer Mode, ensuring efficient allocation of MAC addresses while av
0 views • 15 slides
Proper Addressing Guidelines for Mailing Envelopes
Learn how to correctly address envelopes for mailing purposes, including where to place the recipient's address, return address, and account number. Follow clear guidelines to ensure your mail is delivered efficiently without any issues.
0 views • 6 slides
Understanding Processes in Computer Science at Carnegie Mellon University
Processes in computer science at Carnegie Mellon University are explored, defining a process as an instance of a running program. The illusions of logical control flow and private virtual address spaces are maintained for each program. Components of a process include address space, processor state,
0 views • 50 slides
Introduction to IEEE 802c SLAP
IEEE 802c defines Local Medium Access Control (MAC) Address Usage, providing structured approaches through the Structured Local Address Plan (SLAP) in different regions of the local MAC address space. Local MAC addresses are not globally unique, and the assignment is within local administration's sc
0 views • 9 slides
Mint: Cost-Effective Network-Address Translation Architecture
Mint (Multiple Inexpensive Network-address Translation) presents a cost-effective, scalable, fault-tolerant, and flexible approach to handling IP address depletion by utilizing multiple NAT servers. The system architecture includes NAT servers and a Mint-NAT gateway to enhance packet handling effici
0 views • 18 slides
Hardware-Assisted Page Walks for Virtualized Systems
Virtualization in cloud computing and server consolidation relies on hardware-assisted page walks for address translation in virtualized systems. This involves two-level address translations to ensure isolated address spaces for each virtual machine, utilizing multi-level page tables to manage memor
0 views • 32 slides
Understanding Standard Combinational Modules in Digital Design
Introduction to standard combinational modules such as decoders, encoders, multiplexers (Mux), demultiplexers (DeMux), shifters, adders, and multipliers. Exploring their behaviors, logic, and applications in signal transport, data processing, and address manipulation. Detailed explanation of how dec
0 views • 26 slides
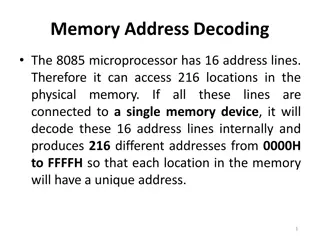
Memory Address Decoding in 8085 Microprocessor
The 8085 microprocessor with 16 address lines can access 216 locations in physical memory. Utilizing a 74LS138 address decoder, chip select signals are generated for memory block selection. The interfacing involves decoding address lines to enable memory access, with distinctions between RAM and ROM
0 views • 18 slides
Understanding Addressing in Computer Networks
Addressing in computer networks plays a crucial role in efficient communication. Classful addressing, which led to address depletion, has made way for classless addressing and CIDR strategy. In classless addressing, the address space is divided into variable length blocks, allowing for more flexibil
0 views • 17 slides
IPv6 Addressing and Coexistence: Overview and Challenges
This lecture covers essential topics on IPv6 addressing, including IPv4 issues, the need for IPv6, address representation, types, testing, and verification. It explains how IPv6 is designed to overcome the limitations of IPv4, particularly the depletion of the IPv4 address space. The discussion also
0 views • 44 slides
The Turning Point: Gettysburg and Vicksburg in the Civil War
President Lincoln issues the Emancipation Proclamation after the Battle of Antietam, setting the stage for significant events in the Civil War. The Union faces leadership changes and Confederate advances, leading to the pivotal Battle of Gettysburg in June 1863. The battle becomes the largest ever f
0 views • 12 slides
Removal of FILS IP Address Configuration in IEEE 802.11-14/0093r2
This document details the rationale behind the proposal to remove FILS IP Address Configuration in IEEE 802.11-14/0093r2. The author, Hitoshi Morioka, explains that the need for this configuration is redundant due to the HLP encapsulation's ability to support all required functions. By eliminating c
0 views • 18 slides
IEEE 802.11-23/0421r1: Understanding the IRM Scheme for MAC Address Privacy
The document discusses the use of the Same MAC Address (SMA) scheme in IEEE 802.11-23/0421r1 and introduces the Improved Randomized MAC (IRM) scheme as a privacy-enhancing solution. It explores the implementation and benefits of IRM over SMA, addressing issues like privacy requirements, device ident
0 views • 7 slides
Understanding the Significance of Beginnings and Endings in Writing
Beginnings and endings play vital roles in capturing and maintaining reader interest. The opening sentences set the tone and purpose, offering a glimpse into the content, while conclusions provide closure. Academic introductions typically present context and a thesis statement, appealing to specific
0 views • 25 slides
Understanding Address Information Accuracy in Health Card Registrations: A Study from Northern Ireland
Address information from health card registrations plays a crucial role in health programs, interventions, and migration estimates. The study utilizing the Northern Ireland Longitudinal Study (NILS) explores non-response and lagged response issues in reporting address changes, shedding light on the
0 views • 22 slides
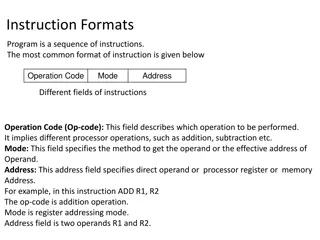
Understanding Different Instruction Formats in Computing
Instruction formats in computing include one-address, two-address, three-address, and zero-address instructions, each with specific ways of specifying operations and operands. One-address instructions utilize an implied accumulator register, while two-address and three-address instructions allow for
0 views • 18 slides
Understanding Instruction Formats in Computer Architecture
Explore different types of instruction formats in computer architecture, including one-address, two-address, and zero-address instructions. Learn how instructions are structured and executed, such as specifying operands and memory addresses. Dive into examples like evaluating expressions and organiz
0 views • 20 slides
Geographic Support System Initiative (GSS-I) Overview
The Geographic Support System Initiative (GSS-I) aims to enhance address data quality through partnerships with tribal, state, county, and local governments. This program involves acquiring, verifying, and geocoding address data, with a focus on improving address coverage and spatial accuracy. Reeng
0 views • 20 slides