Best CRM for lead management
Workday CRM is easy to use CRM software that is designed for B2B. It include everything you need to run your businesses. like manage customers, projects, invoices, estimates, time logs
1 views • 1 slides
Best Customer Relationship Management CRM services Lead Project Management
Workday CRM is easy to use CRM software that is designed for B2B. It include everything you need to run your businesses. like manage customers, projects, invoices, estimates, time logs
0 views • 1 slides
Deep Dive
Explore the functionalities and installation process of the Intune Management Extension (IME). Learn how IME processes app policies, scripts, and handles failures. Delve into its role in deploying PowerShell scripts and Win32 applications on Windows devices enrolled in Intune. Discover the importanc
0 views • 68 slides
INVENTORY MANAGEMENT.
Managing inventory under ISO 15189 guidelines involves Quantity, Quality, and Process management. Key aspects include demand forecasting, inventory movement control, consumption planning, and ensuring fitness for purpose. Quantity management aims to balance demand and supply, manage supply economics
5 views • 13 slides
Importance of Logging and Traceability in Cybersecurity
Logging and traceability play a crucial role in cybersecurity, providing essential insights into system activities and aiding in incident response. This article explores the significance of logging, examples of log analysis, and the types of logs related to host and service activities.
1 views • 61 slides
United States Army Combatives Course Overview
Explore the comprehensive resources and materials related to the United States Army Combatives Course held at the 1/29 Infantry Regiment in Fort Moore, GA. This collection includes instructor books, risk assessment worksheets, visitor logs, course SOPs, training drills, graduation requirements, and
5 views • 13 slides
CHILDREN AT WORK DURING THE INDUSTRIAL REVOLUTION
Explore the types of work children did during the Industrial Revolution from 1851-1901. Learn about available sources for historians, such as census records, church registers, school logs, newspapers, photographs, poetry, and government reports. Discover how the 1851 census in England and Wales prov
2 views • 20 slides
ATH Export House
Athexporthouse.com is a renowned manufacturer of high-quality Gurjan face veneer in Indonesia. They use only the best quality Gurjan logs to produce veneers that are strong, durable, and resistant to moisture and insects. The veneers are carefully processed and graded to ensure consistency and unifo
0 views • 1 slides
Impact of Burning Firewood vs. Compressed Logs on PM2.5 Concentrations
Study comparing the effects of burning firewood and compressed logs on PM2.5 concentrations. Results show that compressed logs produce significantly lower particulate matter pollution. Recommendations include using compressed wood for reduced smoke emission. Various brands and types of compressed lo
0 views • 10 slides
Understanding Timber Production: Types, Classification, and Sustainability
Timber production involves the classification of timbers into hardwoods and softwoods based on the type of trees they come from. Hardwoods are from deciduous trees, while softwoods are from coniferous trees. Sustainable forestry practices, including managed logging activities, ensure the responsible
1 views • 11 slides
DWI Detection and SFST Training Session 1.3 - A Dry Lab
This training session focuses on properly administering SFSTs, observing and recording subject performances, interpreting subject performances, and maintaining SFST logs for DWI detection. Participants will work in teams, observe subjects performing tasks, record clues observed, and engage in discus
0 views • 5 slides
Understanding Sleep Problems in Older Adults
Sleep problems are common among older adults, especially those with chronic illnesses and mood disturbances. Primary sleep disorders that increase with age include sleep-related breathing disorders and restless legs syndrome. Changes in sleep patterns with aging involve decreases in total sleep time
0 views • 16 slides
Database Backup and Recovery Models Explained
Explore different database recovery models - Full Recovery, Bulk-Logged Recovery, and Simple Recovery. Learn about backup types like Full Backup, Differential Backup, and File/Filegroup Backup. Understand the importance of transaction logs in data recovery processes.
1 views • 17 slides
Detailed Overview of Peripatus Structure and Anatomy
Peripatus, a small terrestrial nocturnal creature resembling a caterpillar, lives under stones and logs near water. Its body is cylindrical with indistinct segmentation and superficial ring-like annuli. The head features antennae, mandibles, and oral papillae, while the trunk bears walking legs with
2 views • 27 slides
Understanding Weird Logs in Zeek for Network Security Analysis
Dive deep into the world of "Weird" logs in Zeek with Fatema Bannat Wala, a Security Engineer from the University of Delaware. Discover the motivation behind analyzing over 200 types of Weirds triggered in network traffic, explore common types of Weirds, and learn how these logs can reveal crucial i
1 views • 29 slides
Performance of Post-Quantum Signatures: Analysis and Comparison
Explore the performance and characteristics of various post-quantum signature schemes including Lattice-based Dilithium, QTesla, Falcon, Symmetric Sphincs+, Picnic, Multivariate GEMSS, Rainbow, and more. Understand the implications of using these schemes in TLS, code signing, firmware updates, signe
0 views • 29 slides
Understanding Rock Correlation Through Facies and Biostratigraphy
Explore the correlation of rocks using facies and biostratigraphy in Activity 3 of EOSC 326. Learn about constructing biozones, correlating stratigraphic logs, and interpreting paleoenvironments. Discover the significance of fossils B and F in correlation and apply techniques like seriation in const
5 views • 19 slides
Guide to Setting Up a Computer Forensics Lab
Explore the essential aspects of creating a computer forensics lab, including where to establish it, tools needed, forensic software, storing evidence, access controls, chain of custody, and recording details about forensic images. Learn about the differences between criminal and civil investigation
0 views • 36 slides
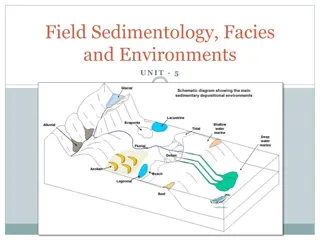
Field Sedimentology: Methods and Tools for Sedimentary Studies
Sedimentology involves interpreting sediments and rocks in terms of transport and deposition processes, distribution in space and time. Field studies require basic equipment like a notebook, hand lens, compass, clinometer, hammer, and GPS. Palaeocurrent indicators provide evidence of flow direction
0 views • 28 slides
Visualization of Process Behavior Using Structured Petri Nets
Explore the concept of mining structured Petri nets for visualizing process behavior, distinguishing between overfitting and underfitting models, and proposing a method to extract structured slices from event logs. The approach involves constructing LTS from logs, synthesizing Petri nets, and presen
0 views • 26 slides
Unsupervised Clickstream Clustering for User Behavior Analysis
Understanding user behavior in online services is crucial for businesses. This research focuses on utilizing clickstream data to identify natural clusters of user behavior and extract meaningful insights at scale. By analyzing detailed user logs, the study aims to reveal hidden patterns in user inte
0 views • 19 slides
Event Log Alignment for Conformance Checking
Approach based on ILP for aligning event logs and process models, ensuring multi-perspective conformance checking. Examples illustrate trace executions with and without problems, utilizing Petri Nets with data. Alignments between log and process traces are analyzed, showing the existence of multiple
0 views • 21 slides
Level 4 Diploma in Dance Teaching Unit 3 Overview
In Level 4 Diploma in Dance Teaching Unit 3, the focus is on dance teaching practice. The learner is observed teaching a class, supported by written evidence such as teaching logs and lesson planning. Continuous Professional Development activities are also emphasized. The examination involves teachi
0 views • 8 slides
AVID Journal Prompts for Critical Thinking and Goal Reflection
Engage in insightful journaling with AVID prompts to enhance writing skills and foster reflection on academic goals and challenges. Explore topics like AVID expectations, procrastination, subject difficulties, college aspirations, organization skills, learning logs, and memorable guest speakers.
0 views • 16 slides
Funeral Arranging and Administration Diploma Course Overview
This Funeral Arranging and Administration Diploma course provides a comprehensive curriculum covering topics such as understanding bereavement, client care in the funeral service, communication skills, legislation, health and safety, and more. Led by experienced tutor Peter Linford, the course inclu
0 views • 25 slides
Text Analytics and Machine Learning System Overview
The course covers a range of topics including clustering, text summarization, named entity recognition, sentiment analysis, and recommender systems. The system architecture involves Kibana logs, user recommendations, storage, preprocessing, and various modules for processing text data. The clusterin
0 views • 54 slides
Fascinating World of Squirrels: Facts and Insights
Squirrels, with their diverse species and habitats, play a vital role in ecosystems. They are omnivores, living in trees, underground burrows, or old logs. Predators like wolves and humans threaten them, but their agility helps in survival. Discover more about these charming rodents and their intera
0 views • 13 slides
Provenance Analysis of Algorithms - Understanding Data Dependencies
Exploring the concept of provenance analysis in algorithms to understand how output items depend on input items. This analysis goes beyond traditional activity logs, focusing on structured collections of items and exploring various applications for causal and quantitative analysis. The critical test
1 views • 16 slides
VFC-400 Vaccine Monitoring Data Logger Kit Operations Overview
This presentation provides a detailed guide on operating the VFC-400 Vaccine Monitoring Data Logger Kit. It covers essential functions like entering review mode, starting and stopping recording, and monitoring temperature data. The step-by-step instructions ensure accurate temperature logging for va
0 views • 9 slides
Raft Consensus Algorithm Overview
Raft is a consensus algorithm designed for fault-tolerant replication of logs in distributed systems. It ensures that multiple servers maintain identical states for fault tolerance in various services like file systems, databases, and key-value stores. Raft employs a leader-based approach where one
0 views • 34 slides
Sketching Techniques for Efficient Numerical Linear Algebra on Massive Data Sets
Explore how sketching methods can be applied in numerical linear algebra to handle massive data sets efficiently. David Woodruff of IBM Almaden discusses using randomized approximations for algorithms aiming for nearly linear time complexity. Applications include analyzing internet traffic logs, fin
0 views • 95 slides
Understanding Speed Logs and Their Evolution in Maritime Navigation
Speed logs play a crucial role in measuring a vessel's speed and distance traveled through water. The evolution from primitive chip logs to modern RPM counters has significantly improved accuracy and efficiency in maritime navigation. Learn about the history, types, and working principles of speed l
0 views • 17 slides
Understanding Re-Finding Behavior in Yahoo Search Logs
Explore a study on re-finding behavior in Yahoo search logs, focusing on quantifying user re-finding actions, known patterns, methodology, and challenges in inferring re-finding intent. The research sheds light on the commonality and stability of re-finding, emphasizing the significance of identifyi
0 views • 22 slides
Overview of Large Scale Log Studies in HCI
This presentation from the CHI 2011 course delves into the design and analysis of large-scale log studies, highlighting the benefits and drawbacks of utilizing logs to understand user behaviors. It explores the insights logs provide, the challenges faced, and strategies to generate relevant logs for
0 views • 146 slides
Implementing Library Analytics at Lancaster University
Lancaster University Library, through the leadership of John Krug, Systems and Analytics Manager, has embraced analytics to enhance operations and decision-making. With the implementation of Alma and the development of analytics dashboards, the library is utilizing data from various sources such as
0 views • 17 slides
Analysis of Unique URLs Retrieval Patterns in Web Logs
This analysis delves into the retrieval patterns of unique URLs from web logs, revealing that a significant percentage of URLs are re-presented from different client IP addresses. The study identifies top repeaters and examines instances of potential proxy device usage based on AS locations.
0 views • 15 slides
Unsupervised Relation Detection Using Knowledge Graphs and Query Click Logs
This study presents an approach for unsupervised relation detection by aligning query patterns extracted from knowledge graphs and query click logs. The process involves automatic alignment of query patterns to determine relations in a knowledge graph, aiding in tasks like spoken language understand
0 views • 29 slides
Analyzing EZproxy Logs with ezPAARSE
This presentation delves into the analysis of EZproxy logs using ezPAARSE, a free and open-source software with a GPL-compatible license. It covers log formats, examples, benefits, and drawbacks of locally-created logs, offering insights and value for usage statistics. Explore other options like AWs
0 views • 10 slides
Big Data-Based Security Analytics for Protecting Virtualized Infrastructures in Cloud
This paper proposes a novel big data-based security analytics approach to detect advanced attacks in virtualized infrastructures in cloud computing. By utilizing network logs and user application logs collected from virtual machines, attack features are extracted through graph-based event correlatio
0 views • 54 slides
Application Log Processing Methodologies in Service-Oriented Architecture
Understanding the methodologies for processing application logs in a service-oriented architecture, including data collection, purpose, programming language toolkits, centralized log collection, non-discardable logs collection, event/enterprise bus integration, cloud platform data collection, and Ku
0 views • 13 slides