Basic Principles of MRI Imaging
MRI, or Magnetic Resonance Imaging, is a high-tech diagnostic imaging tool that uses magnetic fields, specific radio frequencies, and computer systems to produce cross-sectional images of the body. The components of an MRI system include the main magnet, gradient coils, radiofrequency coils, and the
2 views • 49 slides
BTR: Binary Token Representations for Efficient Retrieval Augmented Language Models
Retrieval-augmented language models like BTR address issues such as hallucination by providing efficient solutions for encoding input passages and queries. By utilizing cacheable binary token representations, BTR offers a unique approach to decomposing and binarizing passage encoding to improve runt
0 views • 9 slides
Understanding the Basics of Memory Functioning
Memory is the mental ability to store, retain, and recall information through encoding, storage, and retrieval processes. It involves sensory, short-term, and long-term memory stages, with encoding encompassing semantic, acoustic, and visual aspects. The retrieval process involves locating and recov
0 views • 20 slides
Understanding Positional Encoding in Transformers for Deep Learning in NLP
This presentation delves into the significance and methods of implementing positional encoding in Transformers for natural language processing tasks. It discusses the challenges faced by recurrent networks, introduces approaches like linear position assignment and sinusoidal/cosinusoidal positional
0 views • 15 slides
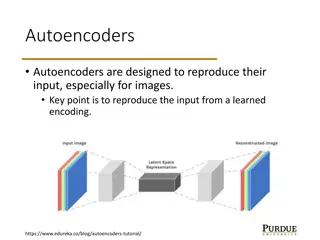
Understanding Variational Autoencoders (VAE) in Machine Learning
Autoencoders are neural networks designed to reproduce their input, with Variational Autoencoders (VAE) adding a probabilistic aspect to the encoding and decoding process. VAE makes use of encoder and decoder models that work together to learn probabilistic distributions for latent variables, enabli
6 views • 11 slides
Understanding Pulse Code Modulation (PCM) in Analog to Digital Conversion
This content delves into the realm of Pulse Code Modulation (PCM), outlining its significance in converting analog data to digital signals. It covers the process of Analog to Digital Conversion, emphasizing the advantages of digitizing analog signals for improved quality and reduced noise. The steps
0 views • 14 slides
Alternative Encodings for GIS Systems - Action 2017.2 Report
Define alternative encoding rules for various application schemas in mainstream GIS systems. The report outlines the process of proposing and endorsing encoding rules, with a focus on GeoJSON, GML, database formats, and linked data. It also details tasks of developing specific encoding rules and enh
0 views • 11 slides
Fundamentals of Communications and Networks in the Networks and Communication Department Tutorial
Exploring various encoding schemes and signal codes, such as Unipolar, NRZ-L, NRZ-I, Manchester, and Differential Manchester, along with practical exercises like extracting clock information and data sequences from Manchester-encoded streams. The tutorial covers topics like delta modulation, encodin
0 views • 18 slides
Financial and Eligibility Rules for EU Cooperation Programmes
Financial and eligibility rules for EU cooperation programmes include details on the first-level control unit, sources of information, hierarchy of rules, overarching eligibility rules, and reporting overview. These rules cover areas such as project activities, expenditure eligibility, procurement r
2 views • 27 slides
Signal Encoding Techniques in Networks and Communication
This chapter delves into signal encoding techniques used in digital data transmission, covering key concepts such as encoding schemes like NRZ-L and NRZI, multilevel binary encoding, and biphase encoding. It explores the fundamentals of digital signaling, modulation techniques, and the relationship
3 views • 34 slides
Rural Access Compliance Rules Proposal by Glenn Disher - PBM Investigator
Proposal by Glenn Disher, a PBM Compliance Investigator, outlines rules for rural access compliance. The proposal focuses on considering local conditions and enforcing rules for maximum impact. It includes recommendations for zip code rules, compliance mileage rules, and examples of non-compliant ru
0 views • 7 slides
Understanding Memory Encoding and Retention Processes
Memory is the persistence of learning over time, involving encoding, storage, and retrieval of information. Measures of memory retention include recall, recognition, and relearning. Ebbinghaus' retention curve illustrates the relationship between practice and relearning. Psychologists use memory mod
0 views • 22 slides
S-124 Navigational Warnings Data Capture and Encoding Guide Presentation
The S-124 Navigational Warnings Data Capture and Encoding Guide (DCEG) presentation was conducted by Timothy Ed Stacy, Deputy NAVAREA IV/XII Coordinator, at IHO, Monaco on September 4-8, 2023. It includes background information, examples, and the development process of the S-124 standard for maritim
0 views • 11 slides
SpatioTemporal Adaptive Resolution Encoding (STARE): A Versatile Data Store Leveraging HDF Virtual Object Layer
STARE-PODS is a proposal by a team of experts aiming to provide a unifying indexing scheme for combining diverse Earth Science data. Leveraging the SpatioTemporal Adaptive Resolution Encoding (STARE) and Parallel Optimized Data Store (PODS), the system enables efficient processing and analysis of ge
1 views • 32 slides
Understanding Numeric and Character Encoding in Programming
In the world of programming, numeric encoding is used to represent non-numeric data for various purposes. This includes encoding different entree options or characters in a natural language using fixed numeric values. Understanding how characters are represented numerically is crucial for efficient
0 views • 31 slides
Review of Quiz 2 Topics: Encoding in Python, Binary Representations, and Parsing Messages
Today's session covered a review of Quiz 2 topics focusing on Encoding in Python, Binary Representations, and Parsing Messages. Key points included understanding why different types of data cannot have unique types in Python, recognizing the significance of 0d0a in HTTP body, discussing exercises fr
0 views • 10 slides
Understanding Company Attribution Rules in Legal Proceedings
Company attribution rules in legal proceedings are outlined, focusing on primary rules found in a company's constitution, general principles of agency, and exceptions where traditional attribution methods may not apply. The interpretation of laws involving companies and the application of specific a
0 views • 7 slides
Line Encoding Lab 6 - 2019/1440: Polar NRZ-L, RZ, and MAN Techniques with Decoder
Explore the Line Encoding Lab 6 from 2019/1440, featuring Polar NRZ-L, RZ, and MAN techniques with decoders. Dive into Simulink settings and output results for each encoding method. Discover how to modify binary number generators and pulse generators to enhance encoding. Conclude with a thank you me
0 views • 14 slides
Optical Security with Double Random Fractional Fourier Domain Encoding
Utilizing double random fractional Fourier domain encoding for optical security involves encryption and decryption methods based on the fractional Fourier transform of various orders, involving specific mathematical operations and notations. The process includes transforming the input function, encr
0 views • 13 slides
Advanced Encoding Techniques in Randomized Algorithms
Explore innovative approaches in randomized algorithms through techniques such as perfect memory, efficient card guessing strategies, and polynomial encoding methods over finite fields. Learn how to optimize memory usage and enhance predictive capabilities in algorithmic processes.
0 views • 41 slides
Understanding Reed-Solomon Encoding: Basics and Applications
Messages consist of symbols from an alphabet and can face erasures and errors during transmission/storage. Redundancy is introduced in codewords to handle these faults, with schemes like 2x and 3x redundancy. Parity bits help detect/correct errors in binary messages efficiently, offering a cost-effe
0 views • 130 slides
Layout and Electrical Rules Check by KANTHARAJU P.K.
Layout rules check is essential in preparing masks for fabrication processes to ensure accuracy. Key design rules include minimum width, spacing, enclosure, and extension. Electrical rules checking (ERC) methodology is used to verify design robustness against electronic design rules at schematic and
0 views • 15 slides
Understanding Binary Codes and Character Coding Techniques
Binary codes, such as ASCII and EBCDIC, are crucial in representing data in computers and digital systems. They play a key role in error detection and data encoding. This article discusses the basics of binary coding, various types of binary codes, character coding techniques like ASCII and EBCDIC,
0 views • 22 slides
Practical Implementations of Arithmetic Coding
Explore the practical implementations, advantages, and disadvantages of arithmetic coding in this informative guide. Learn about the basic algorithm, dynamic interval expansion, integer arithmetic coding, and methods to improve the speed of arithmetic coding. Dive deep into encoding algorithms, exam
0 views • 78 slides
Overview of Computer Science: From Analog to Digital Computing
Explore the evolution of computing from analog devices like sundials and slide rules to mechanical digital computers by Charles Babbage, and the groundbreaking ENIAC - the first general-purpose digital computer. Delve into the concept of encoding information in digital computers using binary numbers
0 views • 42 slides
Understanding Procedural Rules in Company Proceedings
Procedural rules governing company proceedings can be found in the Companies Proceeding Rules, Companies Winding-Up Rules, and the Federal High Court (Civil Procedure) Rules. These rules dictate the process for applications, such as Originating Summons, Originating Motion, or Petition under CAMA. Th
0 views • 22 slides
Theory of Computation: Decidability and Encoding in CSE 105 Class
Explore the concepts of decidability, encoding, and computational problems in CSE 105 Theory of Computation class. Learn about decision problems, encodings for Turing Machines, framing problems as languages of strings, and examples of computational problems and their encodings. Gain insights into th
0 views • 26 slides
Scan and Fix: Indication and Normalization Rules in Alma
Introduction to indication rules and normalization rules in Alma Miriam C. Nauenburg's presentation on the scan and fix workflow. Learn about creating and applying indication and normalization rules, testing rules in the Metadata Editor, and organizing rules as private or shared.
0 views • 54 slides
Exploring Word Embeddings and Syntax Encoding
Word embeddings play a crucial role in natural language processing, offering insights into syntax encoding. Jacob Andreas and Dan Klein from UC Berkeley delve into the impact of embeddings on various linguistic aspects like vocabulary expansion and statistic pooling. Through different hypotheses, th
0 views • 26 slides
Understanding Word Vector Models for Natural Language Processing
Word vector models play a crucial role in representing words as vectors in NLP tasks. Subrata Chattopadhyay's Word Vector Model introduces concepts like word representation, one-hot encoding, limitations, and Word2Vec models. It explains the shift from one-hot encoding to distributed representations
0 views • 25 slides
Understanding Information Encoding in Computer Organization and Design
Discussions in this lecture delve into the importance and methodology of representing operands in computer systems, covering topics such as encoding characters, integers, positive and negative numbers, fixed-point and floating-point numbers. The motivation behind using binary representation is explo
0 views • 35 slides
Understanding Image Compression Techniques
Image compression is essential for reducing file sizes without significant loss of quality. This article explores three common techniques: Run-Length Encoding, Arithmetic Encoding, and their applications in data compression. Learn about encoding intervals, probability ranges, and decoding processes
0 views • 33 slides
Simple and Robust Rules for Monetary Policy Overview
This document discusses the historical background, empirical experience, characteristics of simple rules, robustness, and the comparison between optimal control and simple rules in monetary policy. It explores the evolution of policy rules from Smith and Ricardo to modern approaches, emphasizing the
0 views • 22 slides
January 2016 IEEE 802.11-16/0104r0: Rate Matching for HE-SIG-B
The document from January 2016 focuses on rate matching for HE-SIG-B in IEEE 802.11-16/0104r0 standard. It delves into the encoding/decoding structure, example of SIG-B with code-rate, MCS table, proposed encoding method for HE-SIG-B, and the structure of HE-SIG-B per-STA information field. The cont
0 views • 10 slides
Understanding Encoding and Decoding Data Principles
Data encoding involves converting information into a different form using specific rules, which is then decoded back to its original state. This process is crucial for secure communication, as seen in examples like Morse Code. Through encoding, messages can be kept confidential and accessed only by
0 views • 7 slides
High-Speed Hit Decoder Development for RD53B Chip
Development of a high-speed hit decoder for the RD53B chip by Donavan Erickson from MSEE ACME Lab, focusing on data streams, hitmap encoding, ROM splitting, decode engine building, and more. The process involves encoding methods, ROM setup with borrowed software look-up tables, and buffer systems fo
0 views • 33 slides
Unraveling the Complexities of Hex Game Encoding Paradigms
Hex, a strategic two-player game invented by John Nash and Piet Hein, poses intriguing challenges for mathematicians and computer scientists. This article delves into different paradigms for encoding Hex game rules, exploring the performance of each. From basic observations to advanced approaches li
0 views • 20 slides
Introduction to Data Engineering and Information Theory
This content delves into the fundamentals of data engineering and information theory, focusing on topics such as data communication, sharing, storage, and archiving. It explores key concepts like data representation, corruption prevention, historical milestones in communication technology, Shannon's
0 views • 24 slides
Understanding the Three Stages of Human Memory Process
The human memory process is conceptualized as encoding, storage, and retrieval stages. Encoding involves registering new information, storage retains it for future use, and retrieval brings stored data to awareness. Explore how our memory system functions through these crucial stages.
0 views • 36 slides
Jamming-Resistant Encoding for Non-Uniformly Distributed Information
Protect systems against jamming with efficient encoding methods based on keystroke frequency distribution. Attacker profiles and assumptions analyzed. Approaches considered include algebraic manipulation detection codes and level-out codes. Initial results show promise in reducing error masking prob
0 views • 4 slides