Understanding Malicious Attacks, Threats, and Vulnerabilities in IT Security
Malicious attacks, threats, and vulnerabilities in IT systems pose significant risks and damages. This chapter explores the types of attacks, tools used, security breaches, and measures to protect against cyber threats. Learn how security professionals safeguard organizations from malicious attacks
0 views • 24 slides
TEAM SWOT ANALYSIS
This comprehensive presentation template guides individuals or small groups through conducting a SWOT analysis to identify strengths, weaknesses, opportunities, and threats for a business. It includes questions to assess strengths, weaknesses, opportunities, and threats, a discussion section to dete
1 views • 8 slides
Artificial Intelligence in Cyber Security: Enhancing Threat Detection and Response
Artificial Intelligence (AI) is revolutionizing cyber security by enhancing threat detection, response, and prevention capabilities. By leveraging machine learning algorithms, AI enables organizations to identify cyber threats, analyze behavioral patterns, automate incident response, adapt to evolvi
1 views • 33 slides
Comprehensive Digital Risk Assessment Guide for Businesses
Conducting a digital risk assessment is vital for securing your business against threats like viruses, malware, hackers, and human errors. This guide outlines key areas to focus on, such as identifying critical assets, assessing potential impacts of breaches, prioritizing threats, utilizing tools li
3 views • 4 slides
Safeguarding Employee Data in Online Management Systems!
Online employee payroll management software streamlines payroll tasks such as calculating wages, deducting taxes, and processing employee payments within an organization. These software solutions are designed to automate repetitive tasks, reduce manual errors, and enhance efficiency in payroll proce
5 views • 7 slides
How to Change a Vendor to an Employee in QuickBooks
To change a vendor to an employee in QuickBooks, you need to navigate carefully to ensure accurate financial records. In this guide, we provide step-by-step instructions to help you transition vendor information to employee status seamlessly. We cover all the essential steps, from updating employee
3 views • 3 slides
Understanding Threats in Distribution Integrity Management Program
Distribution Integrity Management Program (DIMP) focuses on ensuring the integrity of pipelines by understanding and managing various threats. Operators are responsible for identifying, categorizing, and addressing potential threats such as corrosion, natural forces, excavation damage, and more to p
1 views • 39 slides
Healthcare Executive's Guide to Ransomware Threats
This comprehensive guide covers essential information on ransomware threats in healthcare, including the definition of ransomware, how it works, email and network threats, and statistics. Gain insights from Troy Ament, a seasoned CISO in the healthcare sector, to safeguard your organization against
0 views • 17 slides
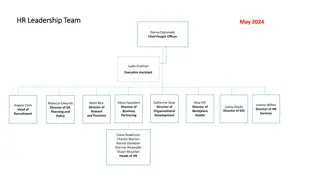
HR Leadership and Employee Relations Team Overview
Meet the dedicated leaders of the HR team, including the Chief People Officer, Directors, and Heads of various departments. Explore the Employment Policy and Strategy team responsible for employee relations and strategic projects. Learn about the Employee Relations team managing important aspects of
1 views • 9 slides
Enhancing Employee Experience in HR: A Next-Gen Approach
Explore the evolving landscape of HR through a focus on employee experience. Discover key areas like culture, leadership, training, and more to drive organizational health. Learn from case studies and models for a holistic understanding of employee engagement. Dive into the intersection of employee
1 views • 14 slides
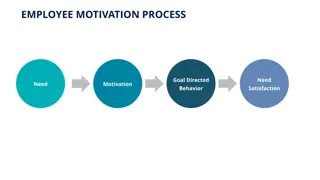
Understanding Employee Motivation and Engagement
Exploring the process of employee motivation, this content delves into goal-directed behavior, needs, satisfaction, and theories like Vroom's Expectancy Theory and Ulrich's Stages of Employee Connection. Ultimately aiming for commitment, this analysis provides valuable insights into enhancing employ
3 views • 51 slides
Cyber Threats and Security Controls Analysis for Urban Air Mobility Environments
The Urban Air Mobility (UAM) environment, with its service-oriented architecture, faces various cyber threats related to end-users, cyber-physical systems, cloud services, and on-premise computing. Threats include unauthorized interception of data, phishing attacks, and Denial of Service (DoS) incid
1 views • 9 slides
Understanding Hybrid Threats and Resilience through Civil Preparedness
Exploring the concept of hybrid threats that combine external threats and internal vulnerabilities, this academic viewpoint by Ramon Loik emphasizes the importance of civil preparedness in building resilience against crises. It delves into aspects such as target selection, active influencing, and th
0 views • 11 slides
Air Base Employee and Labor Relations Overview
This document provides a detailed overview of employee and labor relations at the 7.5 T.H.A.I.R.B.A.S.E.W.I.N.G facility, including governing directives, standards of conduct, employee work expectations, safety guidelines, and differences between bargaining unit and non-bargaining unit employees. It
0 views • 29 slides
Importance of Employee Orientation in Establishing Successful Working Relationships
Effectively orienting new employees is crucial for building successful working relationships within an organization. Employee orientation involves creating a positive first impression, guiding employees in adjusting to their new environment and roles, and providing necessary information and resource
0 views • 13 slides
Understanding Employee Benefits in the Workplace
Employee benefits play a crucial role in job satisfaction and employee well-being. Required benefits such as unemployment insurance and worker's compensation help protect employees in difficult situations. Other benefits like paid vacation time, health insurance, retirement plans, and more, can vary
0 views • 8 slides
Coastal Challenges: Threats and Uses Analysis
The Year 9 Geography homework booklet focuses on the topic of coasts, emphasizing grid references and mapping skills. Students are tasked with identifying grid references for shapes, drawing specific shapes on grids, and demonstrating understanding of 4 and 6 figure grid references. Additionally, in
0 views • 13 slides
Understanding Security Threats and Countermeasures
Explore the diverse threats posed by attackers in the information security landscape, ranging from employee sabotage to hacking incidents. Learn about fundamental security terminology, types of security compromises, and countermeasure strategies to prevent, detect, and correct security breaches. Gai
0 views • 32 slides
Understanding Employee Effort: Evidence from Absenteeism Analysis
This study examines the drivers of employee effort through analyzing patterns of absenteeism across firms. The research explores variations in absenteeism levels, investigates whether incentives or employee characteristics influence effort, and identifies firm characteristics that impact absenteeism
0 views • 39 slides
Understanding Employee Behavior and Motivation in Organizations
This chapter delves into the intricacies of employee behavior and motivation within organizations. It discusses various forms of employee behaviors, individual differences among employees, psychological contracts, and the person-job fit. Furthermore, it explores models and concepts of employee motiv
0 views • 44 slides
Understanding Security Threats and Vulnerabilities in Computer Systems
In computer security, threats exploit vulnerabilities to breach security and cause harm. Vulnerabilities arise from system weaknesses, attacker access, and capability. Threats include spoofing, data tampering, repudiation, information disclosure, denial of service, and elevation of privilege. Catego
0 views • 13 slides
Comprehensive Employee Benefits Manual
This Employee Benefits Manual covers Group Medical Benefits, Employee Medical Plans, Employee Base Plan, Employee Top-Up Plan, and Parents Base Plan. It includes details on coverage, policy periods, insurance companies, room rent limits, sum insured limits, members covered, age limits, co-payments,
0 views • 30 slides
Penn Foundation Employee Assistance Program - Supporting Employee Well-being
Penn Foundation Employee Assistance Program (EAP) is dedicated to promoting the well-being of employees by offering counseling, training, crisis intervention, and more. With over 40 years of experience, they provide support for a range of difficulties like anxiety, depression, career issues, and sub
0 views • 13 slides
Employee Layoffs, Separations, and Benefits Training Session
This training session on employee layoffs, separations, and benefits provides crucial information on employee classifications, civil service rules, seniority, layoff procedures, re-employment, and employee benefits. Topics covered include different employee classifications, civil service seniority,
0 views • 21 slides
Mobile Issues and Cyber Threats in Nigeria - Presentation by Dr. J.O. Atoyebi, NCC
Evolution of GSM in Nigeria, the impact of mobile phone deregulation, and the rise of cyber threats highlighted in a presentation by Dr. J.O. Atoyebi of the Nigerian Communications Commission. The report reveals Nigeria's position in global internet security threats and the challenges faced by the c
0 views • 7 slides
Recognizing and Preventing Insider Threats in National Security
Insider threats pose a significant risk to national security and industry, involving individuals using authorized access to carry out harmful actions. This content covers the definition of insider threats, indicators, consequences, and ways to recognize and report suspicious behaviors. It emphasizes
0 views • 15 slides
Understanding Threat Assessment in Conservation: Direct, Stress, and Indirect Threats
Within threat assessment for conservation, different types of threats are identified and categorized, including direct threats which are human-induced actions directly affecting conservation targets, stressors which result from biophysical impacts of actions on targets, and indirect threats contribu
0 views • 24 slides
Employee Housing Solutions Implemented by Mammoth Community Water District
Mammoth Community Water District (MCWD) faced housing cost challenges affecting workforce recruitment and retention. To address this, they initiated strategies like an Employee Housing Program, Employee Home Loan Assistance Program, and a Van Pool Employee Transportation Association. These programs
0 views • 6 slides
Employee Experience Impact on Business Success
Explore three case studies showcasing the critical role of employee experience in shaping the success or downfall of businesses. From a cautionary tale of neglecting retention efforts to the discovery of employee appreciation driving consumer brand impact, delve into the importance of prioritizing a
0 views • 7 slides
Understanding Cyber Threats in Today's Digital Landscape
Cyberspace is a vast realm encompassing the Internet, where we engage in various activities ranging from communication to entertainment. With the majority of children exposed to the online world, cybersecurity awareness is crucial to tackle the rising cyber threats. These threats include job frauds,
0 views • 33 slides
Understanding Employee Rights and Responsibilities in Human Resources
This module delves into the laws and regulations governing employee rights and responsibilities in the workplace. Topics covered include laws related to employee information, behavior, and social media usage. Employee rights, such as those outlined in the Fair Credit Reporting Act and the Drug-Free
0 views • 24 slides
UAMS 2020 Employee Engagement Survey Overview and Feedback
In the UAMS 2020 Employee Engagement Survey, eligible employees will participate to help improve engagement. The survey, conducted in February 2020, aims to measure employee alignment within the organization. Past survey results led to positive changes such as increased salaries, more appreciation e
1 views • 7 slides
Enhancing Employee Engagement and Performance Management
Performance management is a collaborative process between supervisors and employees aimed at improving organizational effectiveness. This lesson explores the relationship between organizational success and employee engagement, emphasizing activities and strategies to enhance supervisor-employee rela
0 views • 22 slides
Strategies for Employee Retention and Engagement
Understanding the importance of employee retention, this content emphasizes the impact of high turnover rates, benefits of retention, ways to achieve good employee retention, top factors employees consider when choosing an employer, as well as essential strategies for effective leadership and manage
0 views • 13 slides
Understanding Employee Time and Labor Management in a Workplace Setting
This content covers various aspects of employee time and labor management, including the Fair Labor Standards Act (FLSA), timesheet management, leave balances, types of timesheets, exempt vs. nonexempt employee classification, and employee self-service options for time reporting. It emphasizes the i
0 views • 41 slides
Understanding Experiments and Threats to Validity
Explore the world of experimental research, internal and external validity, threats to validity, and the importance of proper study design in ensuring the credibility of research results. Learn about confounding variables, threats to internal validity such as environmental factors and group comparis
0 views • 15 slides
Navigating Current and Emerging Cyber Threats: Leadership Insights
Delve into the realm of current and emerging cyber threats with a focus on leadership considerations. Understand the evolving landscape of cyber risks, the importance of cyber expertise in leadership planning, and the essential role of cybersecurity in today's digital world. Explore the various thre
0 views • 16 slides
Understanding Threats and Attacks in Information Systems
Threats and attacks pose risks to information systems through vulnerabilities that can be exploited, leading to data loss, system unavailability, and compromised security. Four primary classes of threats include unstructured threats from inexperienced individuals, structured threats from skilled hac
0 views • 21 slides
Comparison of Traditional and Cyber Threat Assessment Methodologies
In the digital age, understanding cyber threats alongside traditional threats is crucial. Cyber adversaries operate globally and are hard to identify, posing challenges for intelligence agencies. The ease of acquiring cyber skills and resources makes cyber threats dynamic and dangerous. Classical cy
0 views • 17 slides
Employee Benefits and Cost Savings Analysis for Preschool Programs
Explore the employee discounts and cost savings associated with preschool programs in the community, including details on tuition rates, employee savings, and neighboring district discounts. Gain insights into the impact on employee finances and overall program costs.
0 views • 17 slides