Read⚡ebook✔[PDF] Linking the Space Shuttle and Space Stations: Early Docking Te
\"COPY LINK HERE ; https:\/\/getpdf.readbooks.link\/B073DZCNTR\n\n[READ DOWNLOAD] Linking the Space Shuttle and Space Stations: Early Docking Technologies from Concept to Implementation (Springer Praxis Books) | Linking the Space Shuttle and Space Stations: Early Docking Technologies from Concept t
1 views • 6 slides
READ⚡[PDF]✔ Emerging Space Powers: The New Space Programs of Asia, the Middle Ea
\"COPY LINK HERE ; https:\/\/getpdf.readbooks.link\/B004NNUV54\n\n[READ DOWNLOAD] Emerging Space Powers: The New Space Programs of Asia, the Middle East and South-America (Springer Praxis Books) | Emerging Space Powers: The New Space Programs of Asia, the Middle East and South-America (Springer Pra
1 views • 6 slides
Approaches in Studying Human-Environment Relationship
Explore different approaches to understanding the dynamic relationship between humans and their environment, including deterministic, teleological, possibilistic, and economic deterministic perspectives. These approaches shed light on how human actions and interactions with the environment have evol
1 views • 9 slides
Resolving QuickBooks Event ID Log Error 4
Learn how to resolve QuickBooks Event ID Log Error 4 with our comprehensive guide. This detailed resource provides step-by-step solutions to address this common issue, ensuring your QuickBooks functions smoothly. Discover how to identify the root causes of Event ID Log Error 4, from file corruption
1 views • 4 slides
How to Restore deleted Invoice in Quickbooks Online?
How to Restore deleted Invoices in Quickbooks Online?\nRestoring a deleted invoice in QuickBooks Online involves using the Audit Log to track and recreate it. First, access the Audit Log via the Gear icon under \"Tools\" and identify the deleted invoice details. Then, manually recreate the invoice b
1 views • 7 slides
Sustainable Development of Outer Space Activities and Planet Earth: UN/Austria Symposium Insights
Discussion on the long-term sustainability of outer space activities and its impact on Earth at the UN/Austria Symposium. Highlights COPUOS's role in promoting peaceful space use, international space law development, and space debris mitigation. It addresses key areas like space exploration, safety,
0 views • 9 slides
Understanding Deterministic Finite Automata (DFA) in Regular Language Theory
An exploration of Deterministic Finite Automata (DFA) in the context of Regular Languages, covering their definition, functioning, application in recognizing input strings, and building a DFA for a specific language. The Chomsky Hierarchy and the significance of Regular Languages are also briefly di
0 views • 41 slides
Understanding Pushdown Automata and Language Acceptance
Pushdown Automata (PDA) provide a theoretical framework for recognizing context-free languages. In PDA, the acceptance of a language depends on reaching a final state or having an empty stack. This concept is illustrated through examples and the distinction between deterministic and non-deterministi
0 views • 10 slides
Efficient Log Analysis and Data Reduction Using AWK
Learn how AWK and regex can streamline log analysis and data reduction tasks, saving you time and effort compared to manual methods like Excel. Discover how these tools excel at parsing columns of data, enabling advanced lexical analysis and efficient comparison of log files.
0 views • 15 slides
A Brief History of Space Exploration
Space exploration has seen significant milestones, from the German V2 rocket in 1942 to Yuri Gagarin becoming the first man in space in 1961 and the historic Apollo 11 moon landing in 1969. Animals like fruit flies and monkeys have ventured into space, contributing to scientific understanding. Russi
2 views • 14 slides
Workforce Ready (New Kronos) Log-in Instructions & Resources for Assistance
Comprehensive log-in instructions for Workforce Ready (New Kronos), including steps for web and mobile access, as well as resources for further assistance and training materials. Users can log in using their regular Doane credentials and follow the provided guidance. For additional help, resources,
0 views • 5 slides
Understanding Deterministic Turing Machines
Detailed explanation of Deterministic Turing Machines, their constituents, formal definition, determinism, and special statuses such as Start, Accept, Reject, and Loop. Includes visual representations and key concepts of deterministic Turing machines.
0 views • 14 slides
Exploring Space: Pioneers, Missions, and the Role of Animals
Humans have a rich history of space exploration, with notable milestones including Yuri Gagarin's orbit in 1961, the Apollo 8 moon mission, and Sally Ride becoming the first American woman in space. Before human space travel, animals played a crucial role in understanding the effects of space on liv
4 views • 21 slides
European Deep Space Surveillance and Tracking Collaboration
EU Space Surveillance and Tracking program involves five European nations collaborating to assess and reduce risks to European spacecraft, provide early warnings for re-entries and space debris, and prevent space debris proliferation. Available deep space sensors, such as optical telescopes, are uti
1 views • 8 slides
Concurrent Revisions: A Deterministic Concurrency Model
Exploring a deterministic concurrency model proposed by Daan Leijen and Sebastian Burckhardt, focusing on concurrent programming, threads, locks, futures, promises, transactions, and the resolution of conflicts in parallel performance.
0 views • 36 slides
Overview of Computational Complexity Theory: Savitch's Theorem, PSPACE, and NL-Completeness
This lecture delves into Savitch's theorem, the complexity classes PSPACE and NL, and their completeness. It explores the relationship between time and space complexity, configuration graphs of Turing machines, and how non-deterministic space relates to deterministic time. The concept of configurati
0 views • 67 slides
Advanced Techniques for Heavy Hitters Detection in Insertion Streams
Beating CountSketch algorithms, like those presented by David P. Woodruff and team, offer innovative solutions for identifying heavy hitters in insertion streams with minimal space complexity. Guarantees such as L1 and L2 outputs and the CountSketch approach are explored to achieve efficient heavy h
0 views • 18 slides
Understanding Issues in Context-Free Grammar: Ambiguity, Precedence, Associativity, and More
Delve into the complexities of context-free grammar, exploring concepts such as ambiguity, precedence, associativity, left recursion, and left factoring. Learn about the challenges posed by left recursion and the differences between ambiguous and unambiguous, as well as deterministic and non-determi
0 views • 7 slides
Central Log Service & IT Policies Overview
Central Log Service (CLS) is a university service for storing and analyzing log information, operated by the Division of IT Network Infrastructure and Services Monitoring team. The service provides a centralized location for log storage, analysis tools, and real-time indexing capabilities. IT Loggin
1 views • 7 slides
Testing in Space Simulation Facilities: A Comprehensive Analysis
This webinar delves into testing in space simulation facilities, comparing the requirements at different stages of space missions such as launch, cruise, and operations. Presented by Miracle Israel Nazarious, it covers topics including space qualification testing involving static load, vibration, th
0 views • 12 slides
Enhancing Replay Interface Efficiency in System Debugging
Efforts by researchers at Microsoft Research Asia and MIT focus on enhancing replay interface efficiency for system debugging. The motivation stems from the non-determinism challenges caused by time, user input, network I/O, and thread interleaving. The study observes that only certain parts of a pr
0 views • 26 slides
Development of GR740 Single Board Computer Reference Design by RUAG Space and Partners
RUAG Space collaborates with Gaisler and other partners in the development of a GR740-based single board computer reference design funded by ESA. The project aims to create an advanced technology platform for future space projects, leveraging RUAG's expertise in electronics and digital computers for
0 views • 12 slides
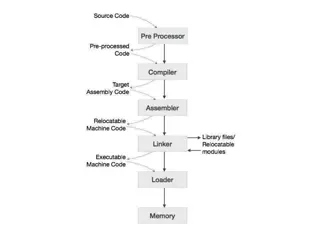
Compiler Data Structures and NFA to DFA Conversion
Compiler data structures play a crucial role in the compilation process, handling lexical analysis to code generation. Understanding the conversion from non-deterministic finite automata (NFA) to deterministic finite automata (DFA) is essential for efficient language processing and optimization.
0 views • 10 slides
Understanding P vs. NP: A Comprehensive Overview
Delve into the complexities of computational problem-solving with insights on P, NP, NP-complete, determinism, and non-determinism. Explore the distinctions between deterministic and non-deterministic algorithms and the implications they have on problem-solving capabilities. Gain a deeper understand
0 views • 22 slides
Overview of Fundamental Principles of Space Law and Outer Space Treaties
The content discusses the fundamental principles of space law highlighted at the United Nations Space Law Conference 2020, focusing on key treaties such as the Outer Space Treaty of 1967 and associated rights, duties, and obligations of states in space exploration and use, including non-appropriatio
0 views • 16 slides
The Manfred Lachs International Conference on Conflicts in Space and the Rule of Law
The 4th Manfred Lachs International Conference held in Montreal in 2016 explored the intersection of conflicts in space and the rule of law, specifically focusing on the legal framework surrounding outer space weaponry. Discussions highlighted the importance of upholding humanitarian values, promoti
0 views • 7 slides
FY23 DoD Space Budget Overview and Investments
The FY23 Department of Defense (DoD) budget continues to prioritize investments in national security space capabilities, with a $1.6B increase in funding for DoD space programs. The United States Space Force receives significant appropriations exceeding the request, emphasizing oversight and managem
0 views • 16 slides
Systematic Testing of Reactive Software - A Case Study on LG Electric Oven
Overview of a case study conducted on LG Electric Oven using systematic testing of reactive software with non-deterministic events. The study focused on detecting concurrency bugs in the software controller of the oven through an automated testing framework that generates event timing sequences. It
0 views • 32 slides
Understanding Cross-Device Tracking for Better Engagement
Delve into the world of cross-device tracking with insights on probabilistic vs. deterministic matching models, limitations of third-party cookies, reasons to engage in cross-device tracking, and the distinctions between probabilistic and deterministic matching methods. Explore how tracking across m
0 views • 41 slides
Time Distribution System R&D Update for Hyper-Kamiokande Experiment
In the February 2020 update, Stefano Russo from LPNHE Paris presented the progress on the time distribution system R&D for the Hyper-Kamiokande experiment. The focus is on implementing a bidirectional data exchange link with a large bandwidth capacity for synchronous, phase-deterministic protocol. T
0 views • 17 slides
Concurrent Revisions: A Model for Deterministic Concurrency
This content discusses a deterministic concurrency model called Concurrent Revisions, focusing on interactive applications with large shared data structures. It covers the challenges of conflicting tasks, conventional concurrency control methods, and proposes a programming model based on revisions a
0 views • 41 slides
Overview of Nested Data Parallelism in Haskell
The paper by Simon Peyton Jones, Manuel Chakravarty, Gabriele Keller, and Roman Leshchinskiy explores nested data parallelism in Haskell, focusing on harnessing multicore processors. It discusses the challenges of parallel programming, comparing sequential and parallel computational fabrics. The evo
0 views • 55 slides
Personalized Celebrity Video Search: Cross-space Mining Approach
This study presents a novel approach for personalized celebrity video search based on cross-space mining, aiming to match user interests with celebrity popularity. By learning the interest space of users and the popularity space of celebrities, the framework correlates the two spaces to enhance sear
0 views • 23 slides
How to Synchronize EPPO Data with Log Shipping
EPPO provides multiple files in XML format, and it is challenging to update data in a SQLite database. Log shipping is a technique for replicating a database to another instance by copying transaction log files. Follow steps to set up log shipping on the EPPO Data services portal for efficient data
0 views • 8 slides
Ensuring Orthogonal Security in Data Encryption Processes
Addressing the challenge of data confidentiality in untrusted server environments through the use of encryption techniques such as deterministic and non-deterministic encryption. The goal is to achieve full functionality independently of data encryption, allowing for secure processing of data querie
0 views • 21 slides
Understanding 4-Log Virus Treatment and Groundwater Rule Compliance
This collection of images and information delves into the importance of 4-log virus treatment under the Groundwater Rule, regulatory requirements for groundwater systems, the basics of Ct calculations for disinfection, types of disinfectants used, and understanding log inactivation of viruses. The c
0 views • 24 slides
Utilizing Topic Modeling for Identifying Critical Log Lines in Research
By employing Topic Modeling, Vithor Bertalan, Robin Moine, and Prof. Daniel Aloise from Polytechnique Montréal's DORSAL Laboratory aim to extract essential log lines from a log parsing research. The process involves building a log parser, identifying important log lines and symptoms, and establishi
0 views • 18 slides
Shadow: Scalable and Deterministic Network Experimentation in Cybersecurity
The presentation discusses the concept of deterministic experimentation in cybersecurity, emphasizing the importance of experimental control and scalability in large distributed systems like Tor. It introduces Shadow, a network simulator designed to achieve repeatable and realistic experiments for r
0 views • 15 slides
Quantum Space-Bounded Complexity in Logarithmic Space: A Comprehensive Overview
Quantum space-bounded complexity explores the memory requirements for solving problems in log space. Examples include matrix multiplication, undirected graph connectivity, and problems like inverting matrices and determining connectivity. The significance of deterministic log space (NL) and nondeter
0 views • 49 slides
Space Debris Removal - Towards Sustainable Space Traffic Management
The 3rd Annual Manfred Lachs Conference in Montreal discussed the pressing issue of space debris removal and the need for a legal framework for space traffic management. With the increasing number of objects in Earth's orbit posing a risk, international collaboration and regulatory initiatives are e
0 views • 9 slides
![Read⚡ebook✔[PDF] Linking the Space Shuttle and Space Stations: Early Docking Te](/thumb/21519/read-ebook-pdf-linking-the-space-shuttle-and-space-stations-early-docking-te.jpg)
![READ⚡[PDF]✔ Emerging Space Powers: The New Space Programs of Asia, the Middle Ea](/thumb/21554/read-pdf-emerging-space-powers-the-new-space-programs-of-asia-the-middle-ea.jpg)