CORE Organic Pleiades Network First Annual Workshop Roadmap 2030 - Event Recap
The CORE Organic Pleiades Network held its first annual workshop in Brussels, focusing on organic research and innovation in the European agri-food sector. The event discussed HEU partnerships, national/regional action plans, research funding, and more. CORE Organic aims to enhance knowledge and inn
0 views • 37 slides
Apache MINA: High-performance Network Applications Framework
Apache MINA is a robust framework for building high-performance network applications. With features like non-blocking I/O, event-driven architecture, and enhanced scalability, MINA provides a reliable platform for developing multipurpose infrastructure and networked applications. Its strengths lie i
3 views • 13 slides
Understanding Terrestrial Planets and Core Dynamics
Exploring the core-mantle interaction from the early Hadean period to present times reveals intriguing questions about the outer core's electrical conductivity, geodynamo sustainability, and inner core characteristics. Studies indicate challenges in maintaining the geodynamo, potential heat sources
9 views • 48 slides
Modeling and Generation of Realistic Network Activity Using Non-Negative Matrix Factorization
The GHOST project focuses on the challenges of modeling, analyzing, and generating patterns of network activity. By utilizing Non-Negative Matrix Factorization (NMF), realistic network activity patterns can be created and injected into live wireless networks. Understanding and predicting user behavi
4 views • 28 slides
Automated Anomaly Detection Tool for Network Performance Optimization
Anomaly Detection Tool (ADT) aims to automate the detection of network degradation in a mobile communications network, reducing the time and effort required significantly. By utilizing statistical and machine learning models, ADT can generate anomaly reports efficiently across a large circle network
8 views • 7 slides
Revolutionizing Network Management with Intent-Based Networking
Explore the concept and benefits of Intent-Based Networking (IBN) in simplifying network configuration and enhancing efficiency. Learn how IBN automates network operations, aligns with business objectives, improves security, and ensures scalability and reliability. Discover the potential of IBN tool
0 views • 14 slides
Network Compression Techniques: Overview and Practical Issues
Various network compression techniques such as network pruning, knowledge distillation, and parameter quantization are discussed in this content. The importance of pruning redundant weights and neurons in over-parameterized networks is highlighted. Practical issues like weight pruning and neuron pru
0 views • 37 slides
Network Slicing with OAI 5G CN Workshop Overview
Overview of Network Slicing with OAI 5G CN workshop focusing on the crucial role of network slicing in realizing the service-oriented 5G vision. This workshop covers topics like multiple logical networks creation on shared infrastructure, different types of network slices, preparation and instantiat
1 views • 6 slides
Network Design Challenges and Solutions in Business Data Communications
Issues in designing a Local Area Network (LAN) include needs analysis, technological design, and cost assessment. The traditional approach involves structured systems analysis, but faces challenges due to rapidly changing technology and increasing network traffic. The Building Blocks Approach recomm
1 views • 20 slides
Understanding 5G RAN Network Slicing and Architecture
Explore the intricate world of 5G Radio Access Network (RAN) and Network Slicing, delving into concepts such as SO Service Orchestrator, SDN-C Service Design, and Core Network Elements. Discover the significance of managing and designing mobile slice services, including eMBB, Massive IoT, and Missio
0 views • 26 slides
Understanding Snort: An Open-Source Network Intrusion Detection System
Snort is an open-source Network Intrusion Detection System (NIDS) developed by Cisco, capable of analyzing network packets to identify suspicious activities. It can function as a packet sniffer, packet logger, or a full-fledged intrusion prevention system. By monitoring and matching network activity
0 views • 23 slides
Overview of BRFSS Survey and its Core Components
The Behavioral Risk Factor Surveillance System (BRFSS) is a state-based telephone survey that monitors personal health behaviors in non-institutionalized adults. It collaborates with the CDC and all 50 U.S. states to gather data on various health topics. The survey includes fixed core questions on d
0 views • 18 slides
OAI 5G CN Workshop Fall 2021 Overview
Fall 2021 OpenAirInterface Workshop focused on developing a 5G Core Network stack, featuring sessions on 5GC basic procedures, different 5GC modes, deployment strategies, and roadmap discussions. The workshop agenda included labs on deploying the OAI Core Network, using VPP-based UPF, network slicin
0 views • 6 slides
Data Flows and Network Challenges in Particle Physics Infrastructure
This overview delves into the data flows and network challenges faced in particle physics infrastructure, focusing on the JUNO project. It discusses the process of data reception, storage, and replication across various data centers, highlighting the bidirectional nature of data flows. Additionally,
0 views • 24 slides
Overview of CUPE Local 3550's Response to Anti-Union Legislation
A detailed overview of Bill 32, an anti-union legislation affecting Canadian Union of Public Employees (CUPE) Local 3550, which requires categorization of dues into core and non-core, with members opting in for non-core spending. The local has reviewed its budget, confirming it is 100% core, and emp
0 views • 14 slides
Progress of Network Architecture Work in FG IMT-2020
In the Network Architecture Group led by Namseok Ko, significant progress has been made in defining the IMT-2020 architecture. The work has involved gap analysis, draft recommendations, and setting framework and requirements. Phase 1 focused on identifying 19 architectural gaps, such as demands for
1 views • 11 slides
Recertification and Assessment of Core Curriculum Courses
The Core Curriculum Council of the Faculty Senate presents a process for recertification and assessment of core curriculum courses to maintain integrity and quality. Courses must be recertified every four years to ensure consistency amidst changes in instructors, content, and teaching methods. State
0 views • 33 slides
Enhancing Alignment Between Introductory Biology and Core Courses
Explore the alignment of the Biology core curriculum, focusing on the structure, goals, and rationale behind flipping portions of the curriculum. Evaluate the preparedness of students for core courses, identify gaps, redundancies, and essential knowledge transfer. Study design involves categorizing
0 views • 25 slides
Understanding Interconnection Networks Topology
Exploring the topology of interconnection networks helps determine the arrangement of channels and nodes, impacting network cost, performance, latency, energy consumption, and complexity of implementation. Abstract metrics such as degree, hop count, and network diameter play crucial roles in evaluat
1 views • 56 slides
Transportation Network Modeling and Analysis with C.Coupled SE Platform
This content outlines the features and functionalities of the C.Coupled SE Platform (CSET Platform) developed by the Connetics Transportation Group. It covers aspects such as interface design, inputs merging, purposes, platform development using Cube, TAZs merging, and network attributes. The platfo
0 views • 11 slides
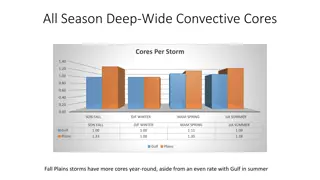
Analysis of Seasonal Variations in Gulf Plains Convective Cores
The analysis reveals fascinating insights into Gulf Plains convective cores, showcasing variations in core numbers, average pixels per storm, pixels per core, and core sizes across different seasons. Deep-Wide cores dominate in the summer, while Gulf cores are larger in the fall. The study sheds lig
1 views • 4 slides
Human Disease Symptom Network: Understanding Disease Relationships Through Symptoms and Genes
The Human Disease Symptom Network (HSDN) is constructed using a large-scale medical bibliographic records database to form a network of human diseases based on symptom similarities. By integrating disease-gene associations and protein-protein interaction data, correlations between symptom similarity
0 views • 37 slides
Introduction to Network Analysis Using .NET
This presentation introduces the concept of network analysis using .NET in the humanities classroom. It provides a template for teaching and adapting network analysis tools for educational purposes. The guide explains the relevance of networks in processing and visualizing data, emphasizing the coll
0 views • 20 slides
Achieving Mission Fulfillment Through Core Themes: An Update
In 2016, our college established four core themes to represent its mission at the core. These themes - Academic Transfer, Career & Technical Education, Essential Skills, and Lifelong Learning - serve as indicators to gauge our progress towards fulfilling our mission. Currently, we are performing abo
0 views • 18 slides
Semantic Data Model of Electronic Invoicing Core Elements
Presentation by Fred van Blommestein on the EN16931-1 semantic data model of core elements in electronic invoicing, covering invoice processes, core invoice design, semantic model details, business rules, and invoicing principles. The model includes 160 elements in 33 groups, with mandatory elements
0 views • 13 slides
Meridian: An SDN Platform for Cloud Network Services
Meridian is an SDN platform developed by Mohammad Banikazemi, David Olshefski, Anees Shaikh, John Tracey, and GuohuiWang at IBM T. J. Watson Research Center. The platform focuses on providing cloud network services efficiently. It encompasses an architecture that enables faster and more convenient n
0 views • 21 slides
Enhancing Network Security with Software-Defined Snort and OpenFlow
Explore the implementation of Snort, Barnyard, and PulledPork within a Software-Defined Network framework using OpenFlow technology. Learn how these tools enhance network security through intrusion detection engines, rule management, and network traffic control mechanisms. Dive into the architecture
0 views • 15 slides
Enhancing Network Security Through Multi-Core Packet Scattering and Deep Packet Inspection
Explore the use of multi-core systems to tackle performance bottlenecks in network intrusion detection systems, specifically focusing on deep packet inspection. Techniques such as load balancing and pattern subset scanning are discussed to optimize DPI processes and improve overall network security
0 views • 43 slides
Understanding ASP.NET Core: Features, Ecosystem, and Differences
ASP.NET Core is a modern framework for building web applications with cross-platform capabilities. It offers a leaner and modular approach compared to ASP.NET Framework. With support for both .NET Core and full .NET Framework, ASP.NET Core enables developers to create applications that can run on Wi
0 views • 9 slides
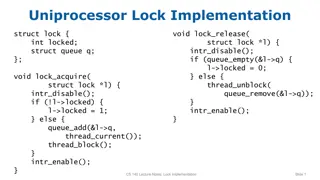
Lock Implementation Strategies for Single-Core and Multi-Core Systems
The provided content outlines several lock implementation strategies for both single-core and multi-core systems. It covers the structures, functions, and techniques used to manage locks efficiently, including releasing locks, acquiring locks, and handling synchronization. Different versions of lock
0 views • 6 slides
Understanding Network Analysis: Whole Networks vs. Ego Networks
Explore the differences between Whole Networks and Ego Networks in social network analysis. Whole Networks provide comprehensive information about all nodes and links, enabling the computation of network-level statistics. On the other hand, Ego Networks focus on a sample of nodes, limiting the abili
0 views • 31 slides
Network Function Virtualization (NFV) Overview
Network Function Virtualization (NFV) focuses on virtualizing network functions to improve efficiency and reduce costs in network infrastructure. The lecture discusses key readings, devices that compose a network, specialization of devices, benefits of one-device-does-anything approach, and the goal
0 views • 21 slides
Enhancing Network Stability with Network Monitoring Systems
Network monitoring is crucial for efficient management and proactive issue detection in a network environment. Factors influencing an effective network system include choosing the best OEM, SLA agreements, and selecting a reliable System Integrator. Reactive monitoring can lead to financial losses a
0 views • 12 slides
Journey to the Earth's Layers
The Earth's structure consists of four main layers: the crust, mantle, outer core, and inner core. The crust is the thin, rocky layer we see on the surface, while the mantle is a solid layer that flows like a viscous liquid. The outer core is a hot, melted layer of iron and nickel, and the inner cor
0 views • 10 slides
Core Review and Alignment Committee Updates
The Core Review and Alignment Committee established in 2021 at WSU is diligently evaluating the existing core requirements, aligning them with learning outcomes, and addressing issues such as student transfers, distinctiveness of the core, and student recruitment and retention efforts.
0 views • 13 slides
ACORN Core Outcomes Research Network Overview
ACORN (ACNE CORE OUTCOMES RESEARCH NETWORK) was established in July 2013 with the aim of creating a standardized set of core outcome measures for use in acne clinical trials. Led by key individuals such as Diane Thiboutot, Jerry Tan, and Alison Layton, ACORN focuses on global representation, stakeho
0 views • 10 slides
System of Environmental-Economic Accounting Core Tables for Water
System of Environmental-Economic Accounting (SEEA) provides core tables and accounts focusing on water accounting and other environmental aspects. The core tables offer concise and relevant information essential for deriving indicators and formulating evidence-based public policies. These tables aim
0 views • 15 slides
Accelerating Systemic Change Network Inaugural Workshop Summary
The Accelerating Systemic Change Network held its inaugural workshop at Howard Hughes Medical Institute in July 2016 to address the lack of coordination in improving higher education. With a vision to become a professional hub for change researchers in STEM education, the network aims to enhance ind
0 views • 5 slides
Exploring Networks in Rutland's Community Health Network Study
This study focuses on describing the networks of organizations that have emerged in each Blueprint Health Service Area (HSA) to support population and individual health. It examines the role of Community Health Teams, the connections between participating organizations, characteristics of successful
0 views • 17 slides
University Network Section Overview July 2015 - March 2016
The presentation covers the network team structure, team members, objectives, goals, report outline, network statistics, accomplishments, and future plans of the university network section from July 2015 to March 2016. It highlights efforts to provide stable internet and intranet services, restructu
0 views • 16 slides