INTEGRITY: A FACTOR FOR EQUALITY THROUGH INCLUSIVE POLICIES
In a global context of growing income inequality, the importance of integrity in fostering equality through inclusive policies is emphasized. The OECD works with Mexico to address issues of inequality, corruption, and declining trust in government, highlighting the need for integrity and competence
0 views • 17 slides
Research Integrity 2.0 Australian Version: A Comprehensive Training Programme
Introducing the Research Integrity programme tailored for the Australian research community, focusing on principles, practices, and responsibilities outlined in the Australian Code for the Responsible Conduct of Research (2018). This interactive courseware aims to enhance integrity, boost confidence
5 views • 16 slides
The Impact of No Code-Low Code on Startup Innovation
In the vibrant world of startups, innovation is the cornerstone of success. As these businesses aim to carve out their niches, they often face a common hurdle: the extensive resources required for traditional software development. However, the emergence of low code no code (LCNC) platforms is revolu
2 views • 12 slides
Understanding Cryptographic Data Integrity Algorithms
Cryptographic data integrity algorithms ensure data integrity, verifying data received matches what was sent by authorized entities. Cryptographic hash functions play a crucial role in ensuring data integrity through hash values. Applications include message authentication, digital signatures, and v
3 views • 41 slides
Improving Code Analysis Workflow with Jenkins, Sonar, and Gerrit
Enhance code analysis processes by analyzing source code before merging, enabling analysis in branches, and triggering Jenkins jobs. Sonar.cloud provides options to analyze branches using Maven build, while the proposal suggests using Jenkins plugin for code review. Addressing challenges with Gerrit
1 views • 12 slides
Understanding Academic Integrity at the University of Manitoba
Explore the essential aspects of academic integrity, including its definition, importance for students, types of dishonesty, and expectations in a class setting. Discover why students should care about academic integrity, the various types of academic misconduct such as plagiarism and cheating, and
0 views • 28 slides
Understanding Integrity at Ok Tedi: Values and Practices
Ok Tedi's commitment to integrity is reflected in their values and operational practices. The organization emphasizes honesty, good moral principles, and accountability in all aspects of their work. Integrity is demonstrated through speaking the truth, maintaining safety, accurate reporting, and tre
0 views • 6 slides
Understanding Integrity Constraints in Relational Database Systems
Integrity constraints play a crucial role in maintaining the accuracy and integrity of data in a database. They include domain constraints, entity integrity, and referential integrity, each serving a specific purpose to ensure data consistency and reliability. Domain constraints ensure values in a c
1 views • 12 slides
Code of Professional Conduct and Ethics in Architectural Profession
The Code of Professional Conduct and Ethics in the architectural profession sets forth standards of honesty, integrity, and ethical behavior expected from registered architects. It outlines guidelines for professional conduct, practices, and ethics, emphasizing the need for transparency, disclosure
1 views • 29 slides
Understanding VB.NET: Features, Advantages, and Disadvantages
VB.NET is a popular object-oriented programming language developed by Microsoft as a successor to Visual Basic 6. It offers features like object-oriented programming, automatic code formatting, multithreading, and event management. Despite its advantages in code formatting and ease of web applicatio
2 views • 8 slides
Understanding Binary Coded Decimal (BCD) and Excess-3 Code
Binary Coded Decimal (BCD) is a binary code used to represent decimal numbers, with the popular 8421 BCD code and its conversion process explained. Additionally, Excess-3 Code, another BCD code, is detailed with an example of finding its code for a given decimal number. Different BCD codes like 4221
0 views • 11 slides
Exploring Public Integrity and Ethics in Civil Service
This module on public integrity and ethics delves into key instruments for strengthening ethical practices in public organizations, challenges faced, analyzing codes of ethics, and managing integrity risks. The agenda includes activities like structured ethical reflection, understanding public value
1 views • 13 slides
Understanding Integrity: A Biblical Perspective
Explore the concept of integrity through the lens of biblical teachings, focusing on examples from the story of Solomon and David. Discover the meaning of integrity in Hebrew and how it relates to being complete, whole, and consistent in actions and words. Learn about subconscious ways integrity can
0 views • 17 slides
A New Complaint Handling Code for the Sector - Webinar Highlights
This webinar discusses the introduction of a new Complaint Handling Code for the sector, aiming to address issues in social housing complaint processes. It covers key points, the background leading to the code's development, the Ombudsman's experience, and the code's aims and framework towards high-
0 views • 14 slides
The Significance of Integrity and Honesty in Personal Skills
Understanding the meaning of integrity and how it relates to honesty is crucial for individuals to live ethically. This article delves into the importance of honesty and integrity, evaluating one's own level of honesty, and practical scenarios showcasing integrity in action.
0 views • 16 slides
Academic Integrity Policy at UIS - Guidelines and Procedures
The Academic Integrity Council at UIS ensures fair operation of hearing panels, reviews the policy implementation, and educates the community. It aims to protect the integrity of the academic environment and helps students develop integrity. Enforcement and effectiveness rely on faculty and departme
0 views • 14 slides
Understanding Frame Pointer Attacks and Exploit Development with pwntools
Explore the concepts of frame pointer attacks, LD_PRELOAD usage, and exploit development with pwntools library. Discover how to spawn a shell using LD_PRELOAD or a constructor, along with the limitations and challenges associated with command-line exploitation.
0 views • 30 slides
Investigating Performance Bottlenecks in Smart Pointer Management
Investigation into performance issues caused by smart pointer manipulation, focusing on the use of boost
0 views • 8 slides
Academic Integrity Board Game Overview
Academic Integrity Board Game offers a fun and educational approach to understanding academic integrity. The game revolves around values like honesty, trust, fairness, respect, responsibility, and courage, as defined by the International Center for Academic Integrity. Players set up the board, place
0 views • 4 slides
Understanding Durability and Integrity in Data Storage Systems
Durability and integrity are crucial aspects of data storage systems. Durability ensures data survives faults like crashes and power loss, while integrity ensures data correctness in the face of faults. Disk data is durable due to surviving power loss, and has integrity through explicit and complex
0 views • 24 slides
Understanding the .NET Architecture Components
The .NET architecture comprises various key components such as the Common Language Specification, Code Manager, Managed Code, Unmanaged Code, and Native Code. These components play crucial roles in the development and execution of applications within the .NET framework. Managed code is executed by t
0 views • 21 slides
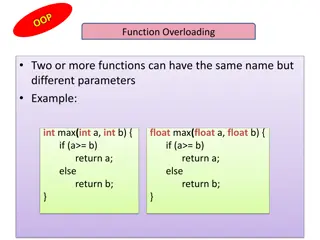
Understanding Function Overloading and this Pointer in C++
Explore the concept of function overloading in C++, allowing multiple functions with the same name but different parameters. Learn about the this pointer in object-oriented programming, which holds the memory address of the current object using a function. See examples of how to implement these conc
0 views • 13 slides
Exploring the Concept of Integrity through Art and Quotes
Delve into the multifaceted theme of integrity through thought-provoking quotes, artistic interpretations, and personal reflections. Witness how individuals from diverse backgrounds define and exemplify integrity in their own lives. Join the journey to understand the significance of integrity and it
0 views • 8 slides
Enhancing Data Integrity in IEEE 802.11 Networks
This document discusses proposals for improving data integrity in IEEE 802.11 networks, specifically focusing on header protection for individually addressed data and management frames. It explores the challenges and alternatives related to verifying Message Integrity Check (MIC) before sending ackn
0 views • 20 slides
Effective S106 Process Management in Local Authority: Insights from Stephen Pointer, Harborough District Council
Explore the expertise of Stephen Pointer, Strategic Planning and Housing Manager at Harborough District Council, in managing an effective Section 106 (S106) process. Discover his role, responsibilities, and experiences in navigating the complexities of national and district contexts, community inter
0 views • 19 slides
Understanding the Victorian Public Sector Code of Conduct
The Code of Conduct for Victorian Public Sector Employees outlines expected behaviors towards the government, community, and colleagues. It emphasizes values such as responsiveness, integrity, impartiality, accountability, respect, leadership, and human rights. A shared understanding of these values
0 views • 16 slides
Multi-Label Code Smell Detection with Hybrid Model based on Deep Learning
Code smells indicate code quality problems and the need for refactoring. This paper introduces a hybrid model for multi-label code smell detection using deep learning, achieving better results on Java projects from Github. The model extracts multi-level code representation and applies deep learning
0 views • 10 slides
Supervisor's Role in Guiding Students in Citizen Science and Business Projects
This module focuses on the critical role supervisors play in guiding students engaged in citizen science and business projects. It covers topics such as ethical challenges, academic integrity, and educational materials to support students and supervisors in their collaboration. The training plan inc
0 views • 6 slides
Code Pointer Integrity Team Overview
Code Pointer Integrity Team, consisting of Po-Jen Lai, Timmy Lin, Chun-Yu Hsiung, and Hung-Lin Wu, under the instruction of Scott Mahlke, is focused on understanding control flow hijack, memory control, and protection mechanisms. They explore new approaches to enhance code safety while minimizing ov
0 views • 25 slides
Automatic Generation of Research Highlights from Scientific Abstracts
Huge growth in scientific publications has made it challenging for researchers to keep up with new research. This project focuses on automatically constructing research highlights from paper abstracts using deep learning models. The system employs sequence-to-sequence models with attention and point
0 views • 9 slides
Role of Integrity Commissioner in Ethics and Accountability Framework for City of Winnipeg
The presentation highlights the importance of ethics and accountability in a democracy, emphasizing the role of Integrity Commissioners in ensuring fair conduct by elected officials. It discusses the need for a formal framework to address ethical issues, complaints, and adherence to a Code of Conduc
0 views • 44 slides
Understanding Pointers in C: A Beginner's Guide
Delve into the world of pointers in C with this comprehensive guide covering topics such as the address operator, pass by copy versus pass by reference, pointer usage, NULL pointers, pointer allocation, and practical experiments to enhance your understanding. Learn about the fundamentals of pointers
0 views • 22 slides
Understanding Smart Pointers in C++ - Bonus Lecture CSE390c Spring 2022
Explore the concept and benefits of smart pointers in C++ as a solution to managing heap-allocated memory more effectively. Learn about avoiding memory leaks and errors when handling pointers through smart pointer implementation. Dive into a Toy Smart Pointer example using a custom class template.
0 views • 36 slides
Software Integrity Case Studies and Verification Methods
Explore case studies and methods for verifying property preservation, system-to-software integrity, and transitioning from AADL to Simulink and SPARK. Learn about peer review, testing, code generation, and more to ensure software integrity and meet system properties.
0 views • 13 slides
Overview of Static Bug Detection in Software Quality Assurance
Static bug detection is a less popular but effective approach for software quality assurance compared to traditional testing methods. It involves tools like Findbugs that help identify potential issues in code before deployment, such as bad coding styles, null pointer dereferences, and malicious cod
0 views • 36 slides
Medicaid Integrity Institute 2012 Training Conference Overview
The Medicaid Integrity Institute (MII) provides training and technical assistance to state Medicaid program integrity employees at no cost. The institute, established in 2007 by CMS and the US Dept. of Justice, aims to enhance national program integrity standards. Located at the National Advocacy Ce
0 views • 8 slides
Plumbing Code Appeals and Interpretations Overview
This document provides information on the agenda, upcoming professional development events, Building Code Appeal Board, Appeal Board decisions, Code Interpretation Committee, code interpretations, and final thoughts related to plumbing code appeals and interpretations. It covers the appeal process,
0 views • 8 slides
Reflections on Research Integrity and Responsible Behavior in Academic Communities
Discussion on the importance of addressing research integrity and ethical behavior within the academic community, emphasizing the need for a code of conduct, guidelines for responsible research practice, and regular updates to ensure good research behavior is taught and practiced throughout research
0 views • 23 slides
Practice Test for Developing Integrity in 4th Grade
This practice test by Renee Cook from Brownsburg, IN, focuses on developing integrity in 4th-grade students. The test includes scenarios where students have to choose the best action reflecting integrity. The test is designed like a dartboard, aiming to find the "bull's-eye" answer that aligns most
0 views • 18 slides
Pointer and Reference Conventions in C++ Programming
Understanding the conventions for passing pointers and references in C++ is crucial for safe and effective programming. Different forms allow various levels of control, from read-only access to modification rights, each signaling a specific intent. These conventions help prevent unexpected behavior
0 views • 21 slides