Multiple Point Lightning Protection Accessories, Multiple Point, Electrolytic Co
We are a leading manufacturer, exporter and supplier of a wide range of Multiple Point Lightning Protection Accessories, Multiple Point, Electrolytic Copper Multiple Point, Earthing and Lightning Protection at very cheap prices for our clients from Mumbai, India.
1 views • 3 slides
Automated Anomaly Detection Tool for Network Performance Optimization
Anomaly Detection Tool (ADT) aims to automate the detection of network degradation in a mobile communications network, reducing the time and effort required significantly. By utilizing statistical and machine learning models, ADT can generate anomaly reports efficiently across a large circle network
8 views • 7 slides
Drone Detection Using mmWave Radar for Effective Surveillance
Utilizing mmWave radar technology for drone detection offers solutions to concerns such as surveillance, drug smuggling, hostile intent, and invasion of privacy. The compact and cost-effective mmWave radar systems enable efficient detection and classification of drones, including those with minimal
0 views • 8 slides
Understanding Floating Point Representation of Numbers
Floating point representation is crucial in computer arithmetic operations. It involves expressing real numbers as a mantissa and an exponent to preserve significant digits and increase the range of values stored. This normalized floating point mode allows for efficient storage and manipulation of r
0 views • 12 slides
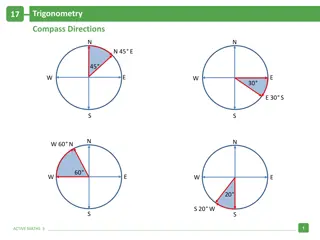
Trigonometry and Compass Directions Problem Solving
In this trigonometry problem, a ship travels from point A to point B and then to point C in specific directions. By applying the Pythagorean theorem, the distance from point C to A is calculated to be 7.2 km. The angle BCA is determined to be 34 degrees, and the direction of point C from A is found
0 views • 5 slides
Understanding Points of Inflection in Calculus
Points of inflection in calculus refer to points where the curve changes from convex to concave or vice versa. These points are identified by observing changes in the curve's concavity, and they are not always stationary points. A stationary point can be a point of inflection, but not all points of
0 views • 14 slides
Machine Learning Techniques for Intrusion Detection Systems
An Intrusion Detection System (IDS) is crucial for defending computer systems against attacks, with machine learning playing a key role in anomaly and misuse detection approaches. The 1998/1999 DARPA Intrusion Set and Anomaly Detection Systems are explored, alongside popular machine learning classif
0 views • 36 slides
NC22Plex STR Detection Kit: Advanced 5-Color Fluorescence Detection System
Explore the cutting-edge NC22Plex STR Detection Kit from Jiangsu Superbio Biomedical, offering a 5-color fluorescence detection system suitable for multiple applications. Enhance your research capabilities with this innovative product designed for precision and efficiency.
0 views • 20 slides
Automated Melanoma Detection Using Convolutional Neural Network
Melanoma, a type of skin cancer, can be life-threatening if not diagnosed early. This study presented at the IEEE EMBC conference focuses on using a convolutional neural network for automated detection of melanoma lesions in clinical images. The importance of early detection is highlighted, as exper
0 views • 34 slides
Colorimetric Detection of Hydrogen Peroxide Using Magnetic Rod-Based Metal-Organic Framework Composites
Nanomaterials, particularly magnetic rod-based metal-organic frameworks composites, are gaining attention for their exceptional properties and various applications in different fields. This study by Benjamin Edem Meteku focuses on using these composites for colorimetric detection of hydrogen peroxid
0 views • 16 slides
Understanding Floating Point Representation in Binary Systems
In computer systems, decimal numbers are represented in memory using scientific notation. This involves moving the decimal point and using mantissa and exponent to maintain precision and range. The transition to representing numbers in binary involves multiplying by 2 to the power instead of 10. Uti
2 views • 22 slides
Introduction to Floating Point Data Types and Operations
This content delves into the fundamentals of floating-point data types, focusing on single-precision floating-point formats like float, excess-127, and their characteristics. It also compares float and int32_t data types, detailing the representation and conversion of values between them. The materi
0 views • 46 slides
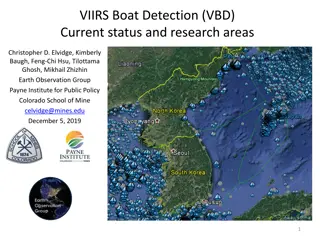
VIIRS Boat Detection (VBD) Research Overview
The Visible Infrared Imaging Radiometer Suite (VIIRS) program, a joint effort between NASA and NOAA, focuses on weather prediction and boat detection using low light imaging data collected at night. The VIIRS system provides global coverage with sensitive instruments and efficient data flow processe
1 views • 13 slides
Real-Time Cough and Sneeze Detection Project Overview
This project focuses on real-time cough and sneeze detection for assessing disease likelihood and individual well-being. Deep learning, particularly CNN and CRNN models, is utilized for efficient detection and classification. The team conducted a literature survey on keyword spotting techniques and
1 views • 15 slides
Stop Hidden Water Damage: Your Ultimate Guide to Leak Detection in San Diego
Learn how San Diego leak detection services can help protect your home from water damage. Discover the signs of leaks, advanced detection technologies, and tips to prevent costly repairs. Stay ahead with proactive slab leak detection and expert solut
0 views • 6 slides
Understanding Colligative Properties in Solutions
Colligative properties in solutions depend on the total concentration of solute particles present, impacting properties such as boiling point elevation, freezing point depression, vapor pressure lowering, and osmotic pressure. Boiling point elevation is directly proportional to the number of solute
1 views • 19 slides
GOES-R ABI Aerosol Detection Product Validation Summary
The GOES-R ABI Aerosol Detection Product (ADP) Validation was conducted by Shobha Kondragunta and Pubu Ciren at the NOAA/NESDIS/STAR workshop in January 2014. The validation process involved testing and validating the ADP product using proxy data at various resolutions for detecting smoke, dust, and
1 views • 21 slides
Real-Time Cough and Sneeze Detection Using Deep Learning Models
Detection of coughs and sneezes plays a crucial role in assessing an individual's health condition. This project by Group 71 focuses on real-time detection using deep learning techniques to analyze audio data from various datasets. The use of deep learning models like CNN and CRNN showcases improved
0 views • 15 slides
Development of Satellite Passive Microwave Snowfall Detection Algorithm
This study focuses on the development of a satellite passive microwave snowfall detection algorithm, highlighting the challenges in accurately determining snowfall using satellite instruments. The algorithm uses data from AMSU/MHS, ATMS, and SSMIS sensors to generate snowfall rate estimates, overcom
0 views • 20 slides
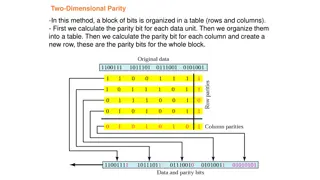
Data Error Detection Techniques Overview
Two-dimensional parity and Cyclic Redundancy Check (CRC) are data error detection methods used to ensure data integrity during transmission. Two-dimensional parity involves organizing bits in a table to calculate parity bits for data units and columns, while CRC appends a string of zeros to the data
0 views • 20 slides
Overview of GRANDproto Project Workshop on Autonomous Radio Detection
GRANDproto project workshop held in May 2017 focused on improving autonomous radio detection efficiency for the detection of extensive air showers (EAS). Issues such as detector stability and background rates were discussed, with the goal of establishing radio detection as a reliable method for EAS
1 views • 14 slides
Timely Leak Detection San Diego | Professional Leak Detection Services
Protect your home with expert leak detection services in San Diego. Avoid costly water damage and health risks with timely detection of hidden leaks. Schedule today!\n\nKnow more: \/\/ \/san-diego-slab-leak-detection\/
0 views • 7 slides
How Professional Leak Detection Can Save Your San Diego Home | Leak Detection Sa
Protect your home from costly damage with professional leak detection in San Diego. Learn about expert services like slab leak detection, non-invasive testing, and more. Save money and prevent water damage with top San Diego leak detection services.\
0 views • 8 slides
EPA Compliance Basics: Tank Leak Detection and Monitoring Methods
Learn about EPA requirements for tank leak detection, release detection methods, and compliance methods for monitoring tank systems. Understand the importance of implementing effective leak detection systems to prevent contamination and comply with federal regulations, including Automatic Tank Gaugi
0 views • 18 slides
Gas Detection of Hydrogen/Natural Gas Blends in the Gas Industry
Gas detection instruments play a crucial role in assessing the presence of hazardous atmospheres in the gas industry. This study focuses on the impact of adding hydrogen up to 20% in natural gas blends on gas detection instruments. The aim is to understand any potential inaccuracies in readings and
0 views • 30 slides
Timely San Diego Leak Detection | Protect Your Home from Water Damage
Discover the importance of timely leak detection in San Diego. Prevent costly water damage, reduce bills, and protect your home with professional leak detection services. Learn more about slab leak detection and prevention today!\n\nKnow more: \/\/m
0 views • 9 slides
Non-Isotopic Labeling for Molecular Detection
The use of non-radioactive probes in molecular detection involves synthetic DNA or RNA molecules with specific target sequences and reporter groups detectable via fluorescence spectroscopy. Direct and indirect labeling methods utilize fluorescent dyes or enzymes conjugated to modified nucleotides, a
0 views • 20 slides
Understanding Intrusion Detection Systems (IDS) and Snort in Network Security
Intrusion Detection Systems (IDS) play a crucial role in network security by analyzing traffic patterns and detecting anomalous behavior to send alerts. This summary covers the basics of IDS, differences between IDS and IPS, types of IDS (host-based and network-based), and the capabilities of Snort,
0 views • 34 slides
Anomaly-Based Network Intrusion Detection in Cyber Security
An overview of the importance of network intrusion detection, its relevance to anomaly detection and data mining, the concept of anomaly-based network intrusion detection, and the economic impact of cybercrime. The content also touches on different types of computer attacks and references related to
0 views • 32 slides
LD-Sketch: Distributed Sketching Design for Anomaly Detection in Network Data Streams
LD-Sketch is a novel distributed sketching design for accurate and scalable anomaly detection in network data streams, addressing challenges such as tracking heavy keys in real-time across a vast key space. By combining high accuracy, speed, and low space complexity, LD-Sketch enables efficient heav
0 views • 25 slides
Understanding Freezing Point Depression and Molality for Solutions
Introduction to molality and freezing point depression in solutions. Molality is a way to measure solution concentration, calculated using moles of solute and kilograms of solvent. By calculating the moles of NaCl in a salt solution and the mass of the solvent (ice/water), the molality can be determ
0 views • 9 slides
Understanding Anomaly Detection in Data Mining
Anomaly detection is a crucial aspect of data mining, involving the identification of data points significantly different from the rest. This process is essential in various fields, as anomalies can indicate important insights or errors in the data. The content covers the characteristics of anomaly
0 views • 50 slides
Impact of Tx EVM on MIMO Detection Follow-Up
This document discusses the impact of Tx EVM on MIMO detection, highlighting that improving Tx EVM can achieve theoretical gains in nonlinear detection. It addresses questions raised during discussions and presents an optimal detector scenario in the presence of colored noise from Tx EVM. Simulation
0 views • 14 slides
Object-Oriented Python Code for WIMP Direct Detection Signals
Calculating signals for Weakly Interacting Massive Particle (WIMP) direct detection using an object-oriented Python code called WimPyDD. WimPyDD provides accurate predictions for expected rates in WIMP direct detection experiments within the framework of Galilean invariant non-relativistic effective
0 views • 24 slides
Nonparametric Tolerance Interval Approach to Immunogenicity Assay Cut Point Determination
This content discusses the importance of determining the cut point for immunogenicity assays to detect anti-drug antibodies (ADA) in large-molecule therapeutics. It highlights the need for well-developed and validated assays to ensure drug efficacy and safety. The approach involves multiple-tiered v
0 views • 26 slides
Prevent Water Damage_ Why Slab Leak Detection Matters in San Diego
Protect your home from costly water damage with professional slab leak detection services in San Diego. Learn how early detection can safeguard your foundation and avoid expensive repairs.\n\nKnow more: \/\/ \/san-diego-slab-leak-detection\/
0 views • 9 slides
Detection Methods for GMOs and LMOs in Molecular Biology
Techniques in Molecular Biology lecture discusses GMOs and LMOs, transgenic plants, examples like Bt cotton and Golden rice, detection methods, purpose of detection, and how transgenic plants are created. The content emphasizes the need to differentiate GM crops from non-GM crops and the importance
2 views • 40 slides
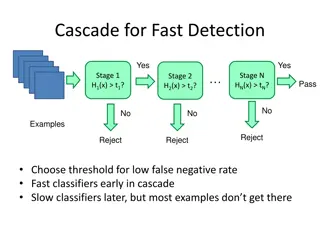
Object Detection Techniques Overview
Object detection techniques employ cascades, Haar-like features, integral images, feature selection with Adaboost, and statistical modeling for efficient and accurate detection. The Viola-Jones algorithm, Dalal-Triggs method, deformable models, and deep learning approaches are prominent in this fiel
0 views • 21 slides
Understanding Floating Point Numbers in Computer Science
Exploring the concepts of floating point format, normalization, conversion processes, and IEEE 754 standard for representing floating point numbers in computer systems. Learn about two's complement, excessive notation, and the components that make up a floating point number. Dive into examples of co
0 views • 18 slides
Understanding Point-to-Point Protocol (PPP) and Serial Communications in WANs
This content explores the Point-to-Point Protocol (PPP), outlining its components, establishment of sessions, authentication protocols, and configuration. It also delves into WAN connection options, serial and parallel ports communication, and serial communication standards for LAN-to-WAN connection
0 views • 31 slides