Automated CT Perfusion Imaging in Acute Ischemic Stroke: Overview
This presentation delves into the significance of automated CT perfusion imaging in diagnosing and treating acute ischemic stroke. It covers essential information such as the burden of stroke in Ontario, the critical aspect of time in stroke treatment, hyperacute stroke treatment goals, and the impo
4 views • 41 slides
Impact of Fact-Checking on Credibility Among Older Adults
Analyzing the impact of fact-checking on news credibility among older adults reveals that age is a key factor in information credibility. Older adults tend to give more credibility to various kinds of information, leading to potential challenges in discerning between true facts and false news. Fact-
5 views • 31 slides
Exploring the impact of automated indexing on completeness of MeSH terms
This study delves into the effects of automated indexing on the thoroughness of MeSH terms. It addresses the novelty of automated indexing, its implications for teaching, questions raised by students, observed missing index terms, and the significance of MeSH in practice. The explanation of how auto
4 views • 33 slides
Task Force Automated Vehicles Regulation Screening Report
The Task Force Automated Vehicles Regulation Screening (TF-AVRS) conducted multiple meetings and screenings to evaluate regulations and terms related to automated vehicles. The report outlines the screening process, considered items, results, and future plans for regulation screening in the automoti
0 views • 9 slides
Task Force Report on Regulatory Fitness for Automated Driving Systems
The co-chairs of the Task Force on Regulatory Fitness for Automated Driving Systems presented an informal document at the 19th meeting of GRVA, outlining the context, purpose, and status of regulations related to automated vehicles. The report focuses on the need for a regulatory environment for aut
1 views • 10 slides
Exploring 'Checking Out Me History' - A Poem Analysis Quiz
Unravel the layers of "Checking Out Me History" through a 10-question quiz delving into themes of identity, historical figures, and the narrator's sentiments towards education and heritage. Discover the hidden messages and insights within this powerful poem.
0 views • 12 slides
Automated Workflow Forms Training & Implementation Overview
Learn about the automated workflow forms training and implementation presented by ANR Business Operations Center on August 5th. Understand the purpose, steps, and support available for the process involving various forms related to funding, purchases, and more. Get insights into the automated routin
2 views • 41 slides
Understanding Fact Finding Techniques in System Analysis and Design
Fact finding techniques play a crucial role in collecting essential data and information for system analysis and design. Techniques include sampling existing documentation, research, observation, questionnaires, interviews, prototyping, and joint requirements planning. Extracting facts accurately is
1 views • 8 slides
Automated Driving Systems Taxonomy & Definitions - SAE J3016 Overview
This overview discusses the alignment of international conventions regarding definitions of Automated Driving Systems (ADS) as outlined in SAE J3016. It covers the purpose, availability of SAE J3016, differences in regulations, the use of "autonomous" vs. "automated," and the concept of requesting h
4 views • 12 slides
Update on Categorization of Automated Vehicles by OICA and CLEPA
OICA and CLEPA are updating the categorization of automated vehicles, introducing new subcategories and refining definitions for driverless and dual-mode vehicles. The work aligns with ongoing efforts in related groups and aims to enhance clarity in classifying different types of automated vehicles
0 views • 12 slides
Overview of Subprograms in Software Development
Subprograms in software development provide a means for abstraction and modularity, with characteristics like single entry points, suspension of calling entities, and return of control upon termination. They encompass procedures and functions, raising design considerations such as parameter passing
4 views • 25 slides
Quality Improvement Cycle: Plan, Do, Check, Act (PDCA)
The Quality Improvement Cycle follows the PDCA framework, involving planning, implementing, checking, and acting to continuously enhance processes. It begins with defining customer requirements, implementing processes effectively, checking for issues, and taking action to resolve any problems. The c
1 views • 6 slides
Runtime Checking of Expressive Heap Assertions
Motivated by the unreliability of large software systems due to concurrency bugs and limitations of static analysis, the goal is to enable runtime analysis of deep semantic properties with low overhead. This involves checking expressive heap assertions at runtime with minimal impact on performance,
0 views • 15 slides
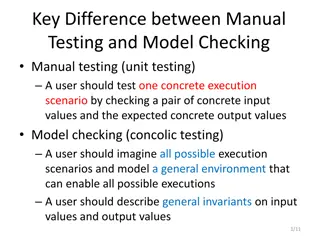
Difference Between Manual Testing and Model Checking
Manual testing focuses on testing specific scenarios with concrete inputs and outputs, while model checking involves imagining all possible scenarios to create a general environment for testing. In manual testing, users test specific execution scenarios, whereas in model checking, users envision and
2 views • 4 slides
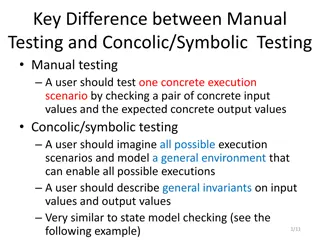
Difference Between Manual Testing and Concolic/Symbolic Testing in Software Development
Manual testing involves checking concrete input and output values for specific execution scenarios, while concolic/symbolic testing requires imagining all possible scenarios and modeling a general environment. General invariants on input and output values are described, similar to state model checki
0 views • 4 slides
Event Log Alignment for Conformance Checking
Approach based on ILP for aligning event logs and process models, ensuring multi-perspective conformance checking. Examples illustrate trace executions with and without problems, utilizing Petri Nets with data. Alignments between log and process traces are analyzed, showing the existence of multiple
0 views • 21 slides
Automated and Modular Refinement Reasoning for Concurrent Programs
This research explores automated modular refinement reasoning for concurrent programs, focusing on safety and correctness in operating systems and applications. Projects like Verve and Ironclad aim to achieve end-to-end security through formal verification tools and small trusted computing bases. Th
1 views • 12 slides
Context-Aware Identification of Check-worthy Claims in Political Discussions
This work explores the intersection of man and machine in countering malicious communication in social networks, focusing on fact-checking in political discussions. The research investigates the need for technology to verify the accuracy of public figures' statements, considering the thriving field
0 views • 21 slides
Exploring Architecture and Challenges of Proof Assistants
Explore the architecture of proof assistants, discussing the use of tactics, formal proofs, and the difficulty in utilizing these tools. Discover the contribution of a new architecture for proof assistants, addressing extensibility and error checking, with a focus on soundness guarantees. Delve into
0 views • 41 slides
Bounded Satisfiability Checking for Early Legal Compliance Verification
Early verification of legal compliance is crucial to avoid consequences such as violating regulations like GDPR. Through bounded satisfiability checking using Metric First-order Temporal Logic (MFOTL), this research focuses on system design verification for regulatory compliance. The study addresses
0 views • 29 slides
Automated Essay Evaluation Systems in ESL Education
Automated Essay Evaluation (AES) systems are increasingly utilized in ESL education to provide automated scores and feedback on writing assignments. These systems employ mathematical models to assess organizational, syntactic, and mechanical aspects of writing, offering a shift from traditional essa
0 views • 45 slides
Essential Guide to Opening and Managing a Checking Account
Learn the importance of opening a checking account, the process of choosing a bank, criteria to consider, and the steps to open an account. Understand the different services offered by banks and the key factors to keep in mind when selecting a financial institution. Discover the benefits and require
0 views • 39 slides
Impact of Shared Automated Vehicles on Transportation System Performance
This study by Dr. Louis A. Merlin and James Fischelson explores the potential impact of shared automated vehicles on transportation systems. By reviewing 39 papers and simulations, the research delves into the implications of new shared automated modes, such as automated taxis, shuttles, and shared
0 views • 38 slides
Differential Assertion Checking and Relative Correctness in Software Verification
Differential assertion checking compares two similar programs to identify errors, while relative correctness ensures all assertions pass, highlighting failed assertions. The content discusses the challenges and benefits of these techniques in software verification, with examples of correct and buggy
0 views • 17 slides
Divide & Conquer Approach to Model Checking
Addressing the state space explosion issue in model checking, this work by Canh Minh Do, Yati Phyo, and Kazuhiro Ogata introduces a divide & conquer approach focusing on until and until stable properties. The research extends techniques to handle these properties effectively, emphasizing mitigation
2 views • 17 slides
Understanding the Decision-Making Process of Checking Behaviors Among Doctors and Patients
Recent research by Ido Erev from Technion and University of Warwick, along with Alvin E. Roth and others, explores the coexistence of insufficient and over-checking behaviors among individuals, including doctors and patients. The study delves into the factors influencing checking decisions, highligh
0 views • 24 slides
Automated Signature Extraction for High Volume Attacks in Cybersecurity
This research delves into automated signature extraction for high-volume attacks in cybersecurity, specifically focusing on defending against Distributed Denial of Service (DDoS) attacks. The study discusses the challenges posed by sophisticated attackers using botnets and zero-day attacks, emphasiz
0 views • 37 slides
Advancements in Automated Agents for Efficient Interaction with People
Explore the diverse applications of automated agents in various domains such as buyer-seller interactions, cultural studies, conflict resolution, medical applications, sustainability efforts, decision-making support, and training simulations. Discover how these automated agents are revolutionizing p
0 views • 20 slides
Inferential Statistics Solutions for Challenging Problems in Section B
The provided statistical problems in Section B involve calculating the expected number of shoppers spending specific durations at a furniture shop and reasons for not checking the weight of each packet when filling corn flakes. Solutions include determining the shoppers expected to spend more than 4
0 views • 25 slides
Input Elimination Transformations for Scalable Verification and Trace Reconstruction
This work introduces new input elimination techniques for scalable model checking in industrial applications, focusing on trace reconstruction. The transformations aim to make the netlist more tractable for solving, involving various algorithms such as retiming, phase abstraction, and bitwidth reduc
0 views • 27 slides
Conflict Checking Process in Heraldry: Armory 104 Overview
Delve into the intricacies of conflict checking using the ordinary in heraldry with Armory 104. Explore prerequisites, review key concepts, understand where SCA-registered armory is located, and learn the process of identifying and analyzing charge groups to ensure uniqueness in designs. Avoid commo
0 views • 28 slides
Utilizing the Family and Children's Trust Fund (FACT) Research Portal for Program Needs Identification and Targeting
Explore how the Family and Children's Trust Fund (FACT) in Virginia supports the prevention and treatment of family violence through data management and strategic goals. Learn about managing by data, FACT's initiatives, and the significance of prevention in addressing family violence issues.
0 views • 25 slides
Regional Automated Vehicle Program 2.0 Overview
Regional Automated Vehicle Program 2.0, led by the North Texas Regional Transportation Council, aims to facilitate the deployment of automated vehicles (AVs) in public entities. The program consists of various projects such as AV planning, cost coverage, and fund allocations for priority deployments
0 views • 10 slides
Automated Program Repair and Anti-Patterns in Search-Based Program Repair
Automated program repair aims to fix bugs in software through fault localization, patch generation, and patch validation using search-based techniques. This research discusses anti-patterns, previous work, repair patterns from human patches, and challenges such as weak oracles in automated program r
0 views • 20 slides
Understanding Automated Theorem Proving in Lean
Dive into the world of automated theorem proving in Lean with a focus on formal verification, history, and the use of logic and computational methods. Explore how programs can assist in finding and verifying proofs, as well as the significance of interactive theorem provers. Discover the evolution o
0 views • 35 slides
Subtyping and Type Checking in Programming Language Design
In the realm of programming language design, subtyping and type checking play crucial roles. This content delves into how syntax-directed rule systems evolve when dealing with subtyping, presenting the challenges and the solutions through a recursive algorithm approach. The discussion includes the t
0 views • 40 slides
Advances in Automated Mercury Speciation Measurement Methods
This content delves into the world of automated mercury speciation measurement methods, focusing on accuracy, calibration, and historical perspectives. It discusses challenges in measuring GEM, PBM2.5, and GOM with hourly resolution, highlighting the significance of continuous monitoring in various
0 views • 23 slides
Orthogonal Vectors Conjecture and Sparse Graph Properties Workshop
Exploring the computational complexity of low-polynomial-time problems, this workshop delves into the Orthogonal Vectors Problem and its conjectures. It introduces concepts like the Sparse OV Problem, first-order graph properties, and model checking in graphs. Discussing the hardness of problems rel
2 views • 22 slides
Streamlining Technical Processing for Library Services
In the technical processing workflow of a library, utilizing tools like copy cataloging macros can significantly improve efficiency and accuracy. This involves checking for copy cataloging status, running fix routines, and updating catalog records. While these macros offer benefits such as saving ti
0 views • 17 slides
Communication Complexity in Byzantine Agreement Research
The presentation discusses communication complexity in Byzantine Agreement, emphasizing a lower bound of (f/2) when After the Fact removal is considered. It explores two major contributions - the communication lower bound in randomized protocols and near-optimal subquadratic Byzantine Agreement. The
0 views • 9 slides