Importance of literature review
A literature review is a critical component of any research endeavor, providing a comprehensive analysis of existing knowledge in a particular field. This review helps in clarifying conceptual issues, understanding research design, persuading examiners, and contributing new insights to the subject a
0 views • 28 slides
Understanding IRB Review Process for Expedited Research
Learn about the significance of IRB review, levels of review, and categories of expedited review. Discover the criteria for IRB review, including whether the study involves human subjects and contributes to generalizable knowledge. Explore the different levels of IRB review and the specific categori
4 views • 11 slides
Enhancing Access to Medicines and Health Products through Innovative Approaches
Global Health Centre experts discuss how building access into innovation can ensure better access to medicines, vaccines, and health products. Key ideas include planting seeds for access early in innovation, exploring alternative innovation models, and rethinking the relationship between innovation
4 views • 20 slides
Rapid Review of BSL Commissioning Arrangements by Dr. Michael Brady
NECS commissioned a Rapid Review of British Sign Language (BSL) service provision to identify areas for improvement in access and patient experience, especially during the Covid-19 pandemic. The review focused on stakeholder engagement, options appraisal for commissioning responsibility, and recomme
9 views • 19 slides
2022 Thales Access Management Index
Thales Access Management Index highlights the current landscape of access security, revealing insights on multi-factor authentication adoption, remote and privileged user access management, VPN usage trends, challenges faced, and preferences towards third-party access management. The report emphasiz
2 views • 9 slides
Guidelines for Expanded Access to Investigational Drugs and Devices
Providing guidance on types of Expanded Access for drugs, biologics, and devices, this content explains the concept of Expanded Access and the criteria that must be met. It covers different types of Expanded Access for drugs and devices, emphasizing the importance of patient safety and benefit. The
0 views • 10 slides
Personnel Safety Systems and Access Control at CERN Facilities
Personnel Safety Systems at CERN include ODH detection, fire safety measures, and access control to protect personnel from hazards. Various access control layers are implemented to regulate entry to different parts of the facility, ensuring only trained personnel access underground areas. Biometric
0 views • 19 slides
Port of Stockton Restricted Area Access Control and ID Card Policy
Access to restricted areas at the Port of Stockton facilities requires possession of a TWIC (Transportation Worker Identification Credential). Only authorized personnel, such as employees, contractors, and those with regular access, may receive a Port Access Card after approval by the Facility Secur
0 views • 6 slides
Introduction to Database Security and Countermeasures
Database security is essential to protect data integrity, availability, and confidentiality. Countermeasures such as access control, inference control, flow control, and encryption can safeguard databases against threats. Access control restricts user access, inference control manages statistical da
0 views • 26 slides
O3 Access Control Solution Overview
O3 Access Control Solution offers unique selling points like single-seat management software, role-based permissions, customizable user information, and more. The system includes a compact controller with multi-format reader support and BACnet Access objects. It integrates with other O3 modules for
0 views • 10 slides
Navigating Peer Review: A Comprehensive Guide for Authors and Reviewers
In academic publishing, peer review plays a crucial role in maintaining publication quality. This guide offers a detailed overview of the peer review process for both authors and reviewers, covering topics such as receiving review invitations, manuscript submission, writing effective reviews, and mo
0 views • 31 slides
Southern Illinois University Carbondale Office of Associate Provost for Academic Programs Review
The Program Review & Center/Institute Review at Southern Illinois University Carbondale aims to educate attendees on IBHE requirements, the review process, conflict of interest policies, self-study writing, on-site review involvement, financial support, and available resources. The IBHE mandates rev
0 views • 37 slides
Understanding EdPlan Connect for Parents
EdPlan Connect is a platform that allows parents to access and review their child's IEP documents, submit responses, and electronically sign documents online. Parents receive email notifications with access links to the parent portal, where they can authenticate their identity via an access code. On
6 views • 17 slides
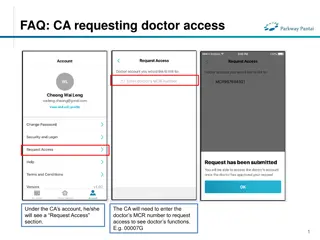
FAQs for Doctor and Clinical Assistant (CA) Account Access Management
Learn how CAs can request access to doctors' functions by entering the MCR number, how doctors can grant or remove CA access, and how CAs can manage access to multiple doctors. The process includes requesting, approving, and unlinking accounts, ensuring efficient and secure access management in a cl
0 views • 4 slides
Slate Graduate School & International Admissions Review Forms Overview
Explore the process of submitting review forms and making admission recommendations in Slate Graduate School & International Admissions, including automatic assignment of applications to queues, review of Staff Review Forms, and recommending admission or denial through Faculty Review Forms. Learn ab
0 views • 8 slides
EventsHQ Virtual Event Registration: User Access and Setup Guide
This comprehensive guide provides step-by-step instructions on setting up virtual event registration using EventsHQ. It covers how users can access event details, join the event, and includes best practices for sharing access links. Learn how to utilize the Virtual Event Details feature, send remind
1 views • 19 slides
Phase 4 Progress Review Discussion Template Overview
This template guides a Progress Review discussion involving a Customer, Provider, and Key Stakeholders. It addresses the gaps in common business requirements, risk assessment confidence, deployment readiness, budget impacts, migration costs, and more. The template provides instructions for completin
0 views • 25 slides
Understanding Judicial Review in Administrative Law
In this chapter, the concept of judicial review in administrative law is explored, focusing on the scope of review set by Congress, including trial de novo and independent judgment on evidence. Different standards of review, such as clearly erroneous and substantial evidence, are discussed, highligh
0 views • 23 slides
Accessible Voting System for Californians with Disabilities
Learn about the Remote Accessible Vote-by-Mail System in California, designed to empower voters with disabilities to securely access, mark, and return their ballots from any computer with internet access. Find out who is eligible to use the system, how to access and return the ballot, and the steps
0 views • 23 slides
Dell Networking Solutions for BYOD and Guest Access Projects
Dell offers end-to-end solutions for Bring-Your-Own-Device (BYOD) and guest access projects, enabling secure employee access and controlled connectivity for visitors. The framework includes mobility business models, device security, network protection, and scalability. Dell supports customers in imp
0 views • 11 slides
UNCAC Implementation Review Mechanism: Moving Towards the Second Cycle
The UNCAC Implementation Review Mechanism is progressing into its second cycle, with a focus on evaluating challenges and terms of reference at the conclusion of each review cycle. The performance assessment has highlighted achievements in enhancing awareness and involvement of civil society/private
0 views • 7 slides
Understanding Arbitrary and Capricious Review in Administrative Law
Arbitrary and Capricious Review refers to a highly deferential standard applied to agency decisions, requiring agencies to demonstrate compliance with statutory requirements. The landmark case of Citizens to Preserve Overton Park v. Volpe set the precedent for a thorough judicial review based on the
0 views • 8 slides
Global Peer Review Activities and Future Plans Overview
This document highlights the recent peer review activities conducted by the Subcommittee on Peer Review, focusing on the accomplishments and upcoming plans for enhancing peer review processes. It includes insights from the Global Flyer Survey, training programs, and the development of guidelines, al
0 views • 3 slides
Understanding Full Committee Review (FCR) vs. Designated Member Review (DMR) for New IACUC Members
Explore the differences between Full Committee Review (FCR) and Designated Member Review (DMR) for new IACUC members. Learn the acceptable methods of protocol review, federal requirements, member responsibilities, risks, and best practices for protocol approval. Dive into the two valid methods of IA
1 views • 23 slides
Role-based Access Control Policies and Security Properties Overview
This content provides an overview of Role-based Access Control (RBAC) policies, Administrative RBAC (ARBAC) systems, and security properties in the context of access control in large organizations. It discusses the implementation of RBAC in various software systems, the assignment and revocation of
0 views • 18 slides
Program Review Annual Summary 2016 by PRC Committee
The Program Review Annual Summary 2016, prepared by the Program Review Committee (PRC), presents a detailed review of instructional programs and administrative units at the College. The report outlines the purpose of the annual review, the themes and issues identified, and recommendations for improv
0 views • 13 slides
Open Access at Charles University: Opportunities and Challenges
Charles University is navigating the landscape of open access following the implementation of the Czech National Open Access Strategy. The university is working towards making all research articles and proceeding papers open access, monitoring article processing charges, and promoting open access as
0 views • 24 slides
Submitting and Accessing 5-Year Post-Tenure Review Materials in Vibe
The post-tenure review process in Vibe is essential for career development funding and compliance with NJ statutes and agreements. Users need to follow specific guidelines when submitting and accessing materials through Vibe, including retaining copies of all documents due to Vibe's limitations in s
0 views • 30 slides
Understanding Filesystem Security Principles and Access Control
Learn about filesystem security, general principles, discretionary access control (DAC), closed vs. open policy, closed policy with negative authorizations, and access control entries and lists. Discover how files and folders are managed, the role of access control lists (ACLs), and the different le
1 views • 56 slides
Understanding Ethernet and Multiple Access Protocols in Computer Networks
Exploring the fundamentals of Ethernet and multiple access protocols in computer networks, this content discusses the two primary categories of multiple access protocols - contention access and controlled access. It delves into topics such as CSMA/CD, LANs, performance of multiple access schemes, ad
0 views • 7 slides
Understanding Shared Memory, Distributed Memory, and Hybrid Distributed-Shared Memory
Shared memory systems allow multiple processors to access the same memory resources, with changes made by one processor visible to all others. This concept is categorized into Uniform Memory Access (UMA) and Non-Uniform Memory Access (NUMA) architectures. UMA provides equal access times to memory, w
0 views • 22 slides
Uncovering Fabricated Data in Stem Cell Research: The Haruko Obokata Scandal
Haruko Obokata, a promising stem cell researcher in Japan, faced allegations of data fabrication, leading to a significant research scandal. Post-publication peer review platforms like PubPeer, PubMed Commons, F1000 Research, and ResearchGate Open Review play vital roles in detecting and addressing
0 views • 11 slides
Understanding Access Changes and Community Relations at Fermilab
Access to Fermilab has become more complicated due to changing DOE guidance and security posture. Efforts are being made to streamline access while addressing security gaps. Public access to outdoor areas of the Fermilab campus is still encouraged, but communication regarding access changes needs im
0 views • 12 slides
Understanding Computer System Protection and Security
Mechanisms like protection and security ensure controlled access to a computer system's resources and prevent malicious activities. Protection involves defining access control levels through models, policies, and mechanisms. Security focuses on user authentication to safeguard stored information. Di
0 views • 25 slides
Harvard Chan School 2021 Yearly Access Review Process
The Harvard Chan School conducts its annual Yearly Access Review (YAR) process to review user access to various financial systems. The process involves assessing permissions, levels of access, and organizational details for each team member. Instructions are provided on reviewing worksheets, adding
0 views • 19 slides
Understanding Security Access in PeopleSoft Finance
Explore the various levels of security access in PeopleSoft Finance, from basic entry access to transaction entry, approvals, and procurement processes. Learn how to request individual and department security access and find relevant forms on the financial services website. Discover the different ty
0 views • 11 slides
Effective Strategies for Conducting a Literature Review in Research Methodology
Understanding the importance of literature review in research methodology, this chapter discusses the objectives, aims, and guidelines for writing a comprehensive literature review. It emphasizes the significance of identifying gaps in existing knowledge, structuring the review, and organizing infor
0 views • 33 slides
Understanding the Doctrine of Judicial Review in the United States
Judicial Review is a crucial power of the judiciary to review the constitutionality of laws and executive orders. This article explores the origin of Judicial Review in the United States, focusing on the landmark case of Marbury v. Madison. It delves into the concept, importance, and application of
0 views • 14 slides
Enhancing Online Teaching Through Self-Review: Challenges and Benefits
Explore the self-review process of online teaching, including identifying challenges, benefits, and different types of reviews. Learn about developing an effective review guide, promoting collegiality, and facilitating professional development in online teaching. Discover the components of a review
0 views • 23 slides
Peer Review Process in Academic Editing
Explore the importance of peer review in academic and professional development, focusing on improving writing skills and critical evaluation. Learn about the benefits of peer review, ways to effectively review work, and various modes of assessment. Understand the peer review process and how it enhan
0 views • 29 slides